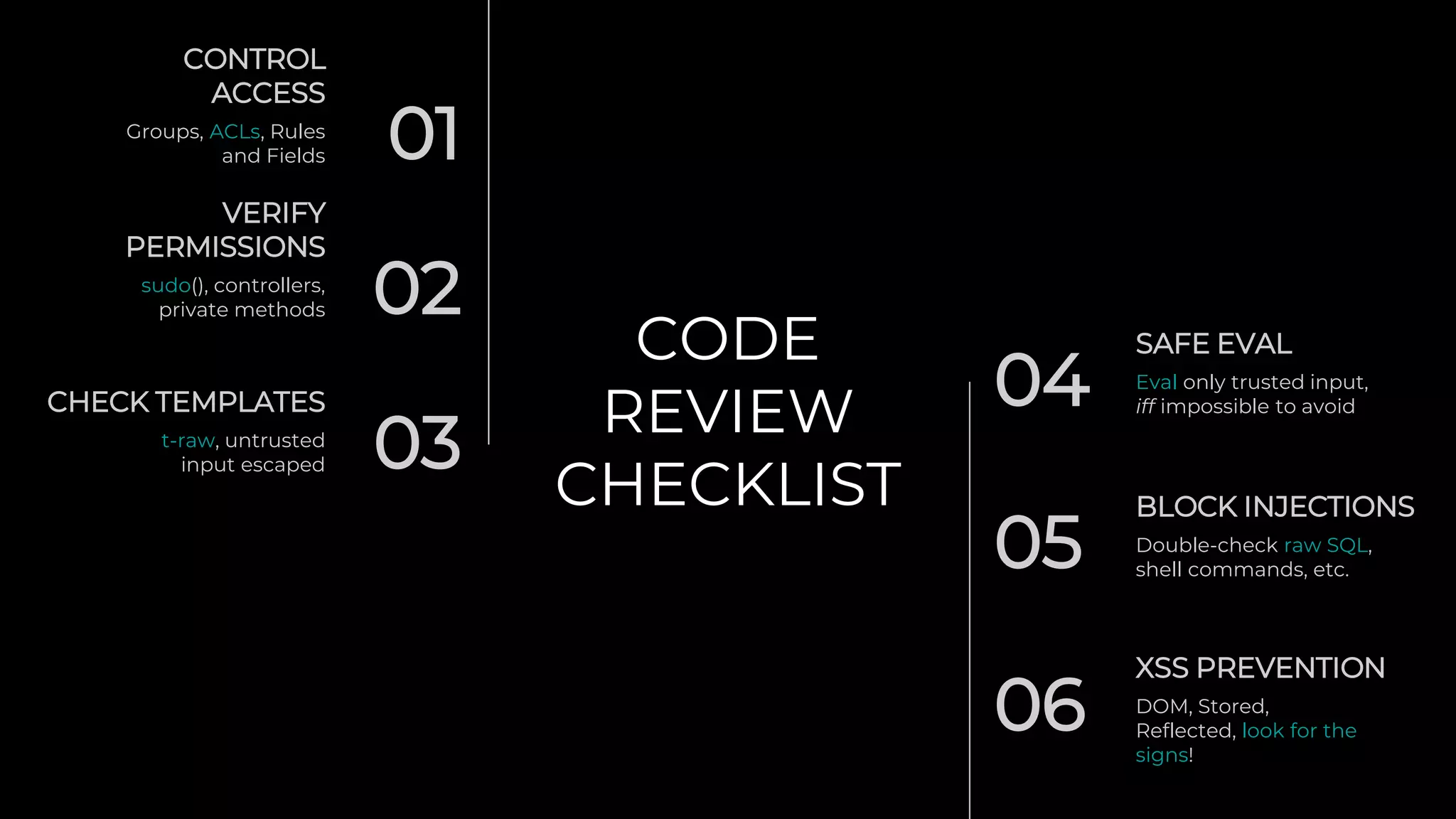
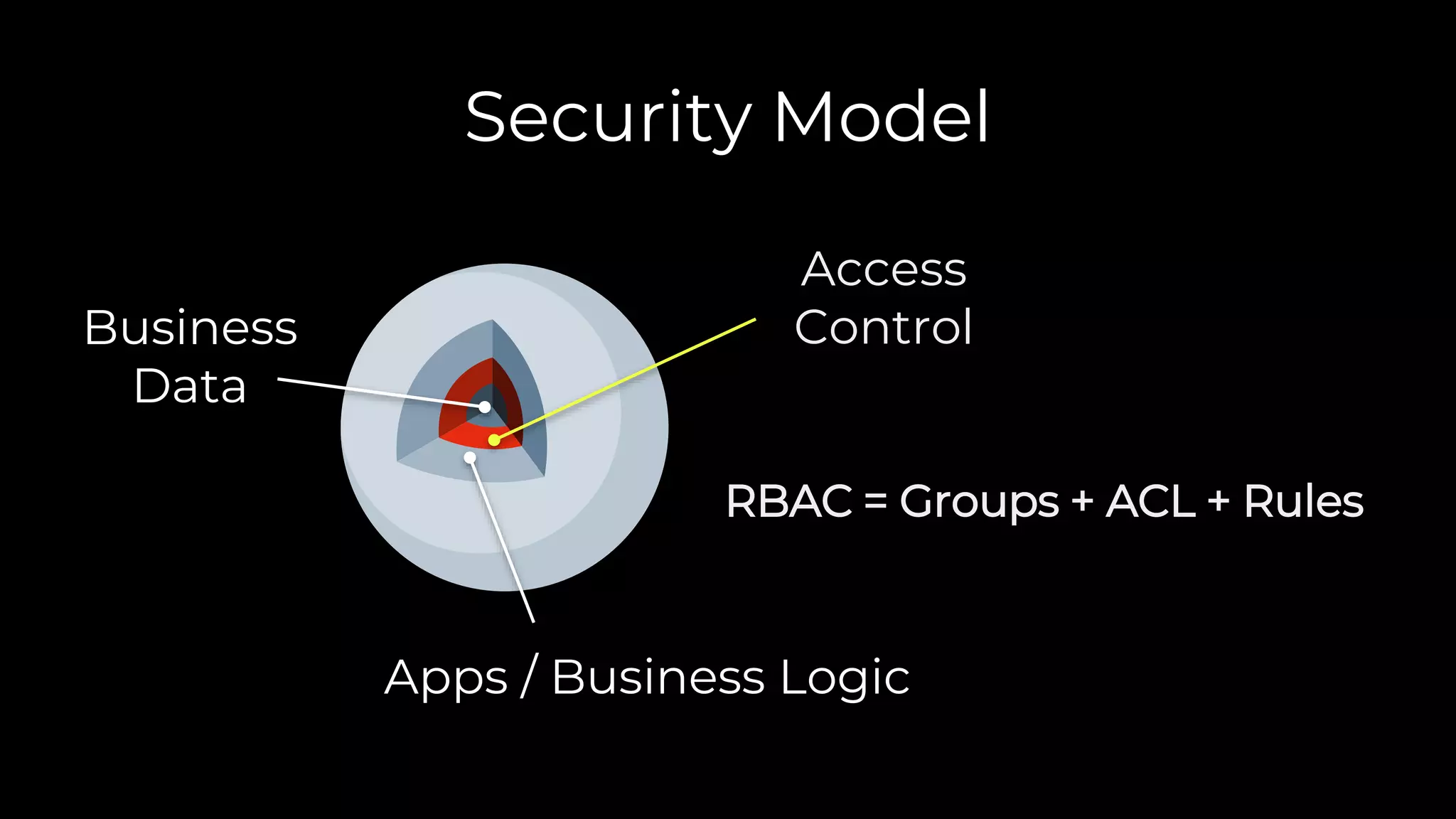
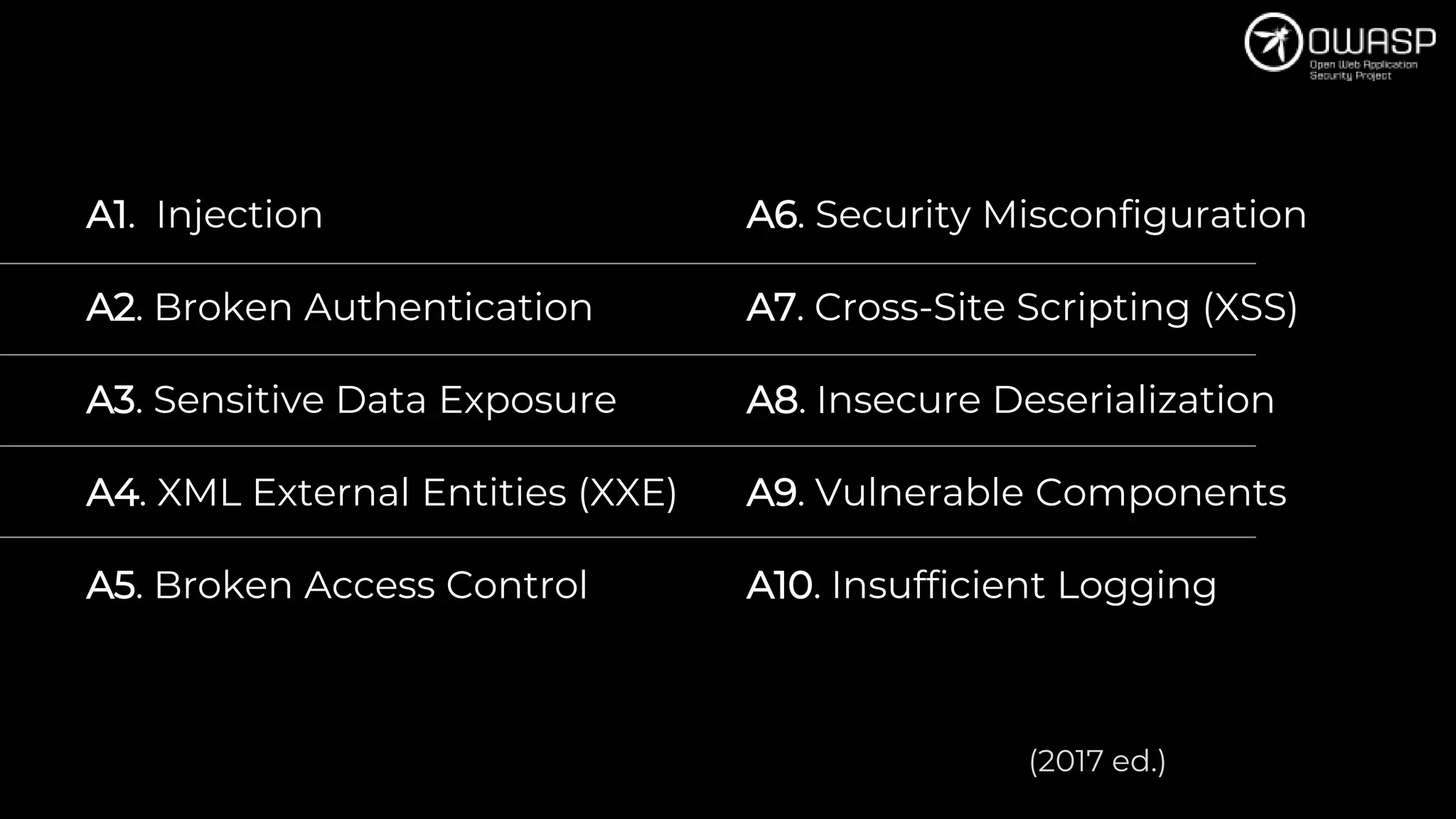
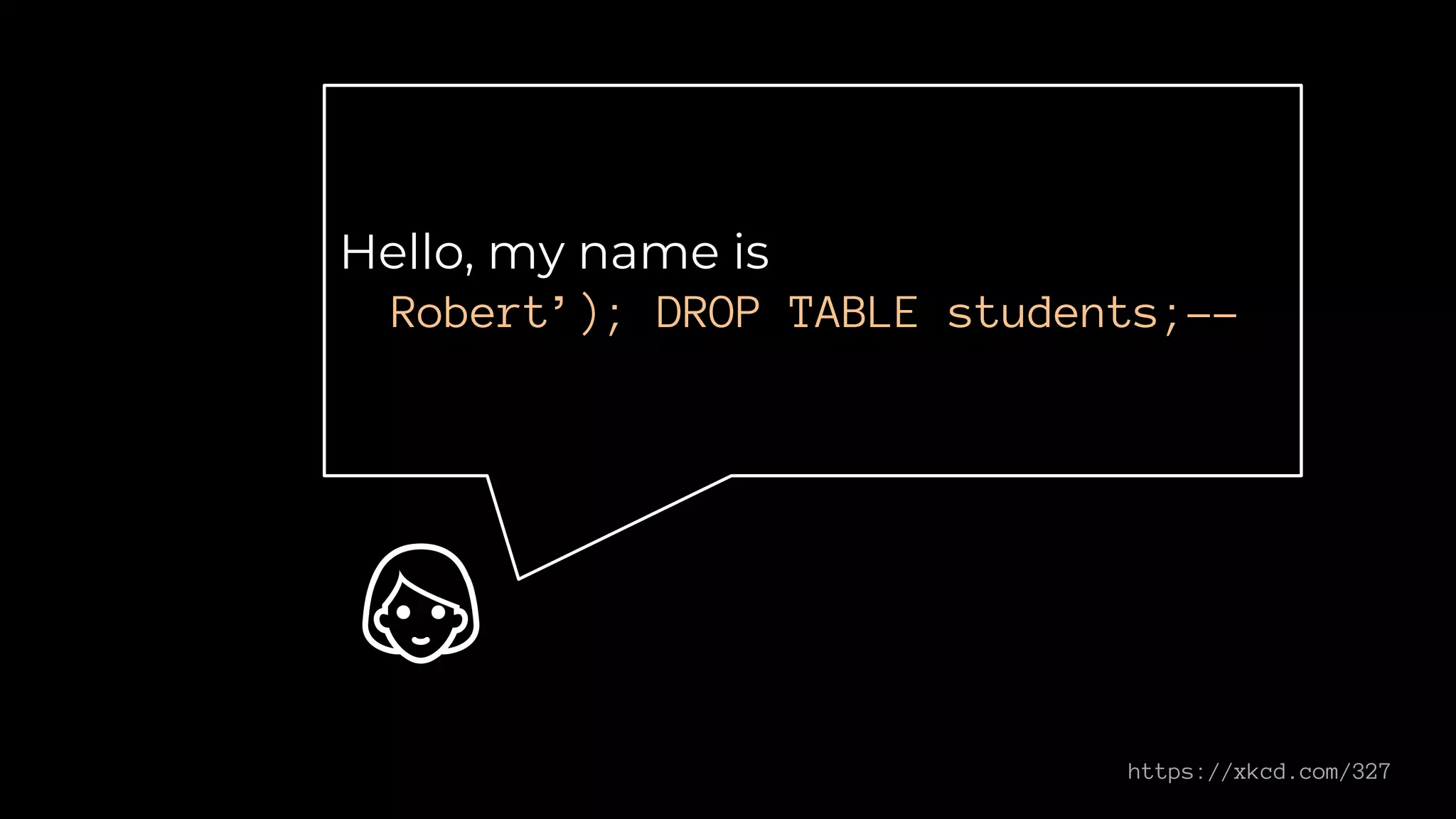
This document provides an overview of software security best practices and common vulnerabilities for Odoo code. It discusses the top 10 risks including injection, broken authentication, sensitive data exposure, XML external entities, broken access control, security misconfiguration, cross-site scripting, insecure deserialization, vulnerable components, and insufficient logging. For each risk, it provides examples of vulnerable code and recommendations for more secure implementations. It emphasizes that the Odoo framework includes mechanisms to prevent many mistakes but knowledge and mindset are also key. The document concludes with recommendations for code reviews to check access control, permissions, templates, evaluations, injections, and cross-site scripting prevention.










![# Best option when possible: use the ORM
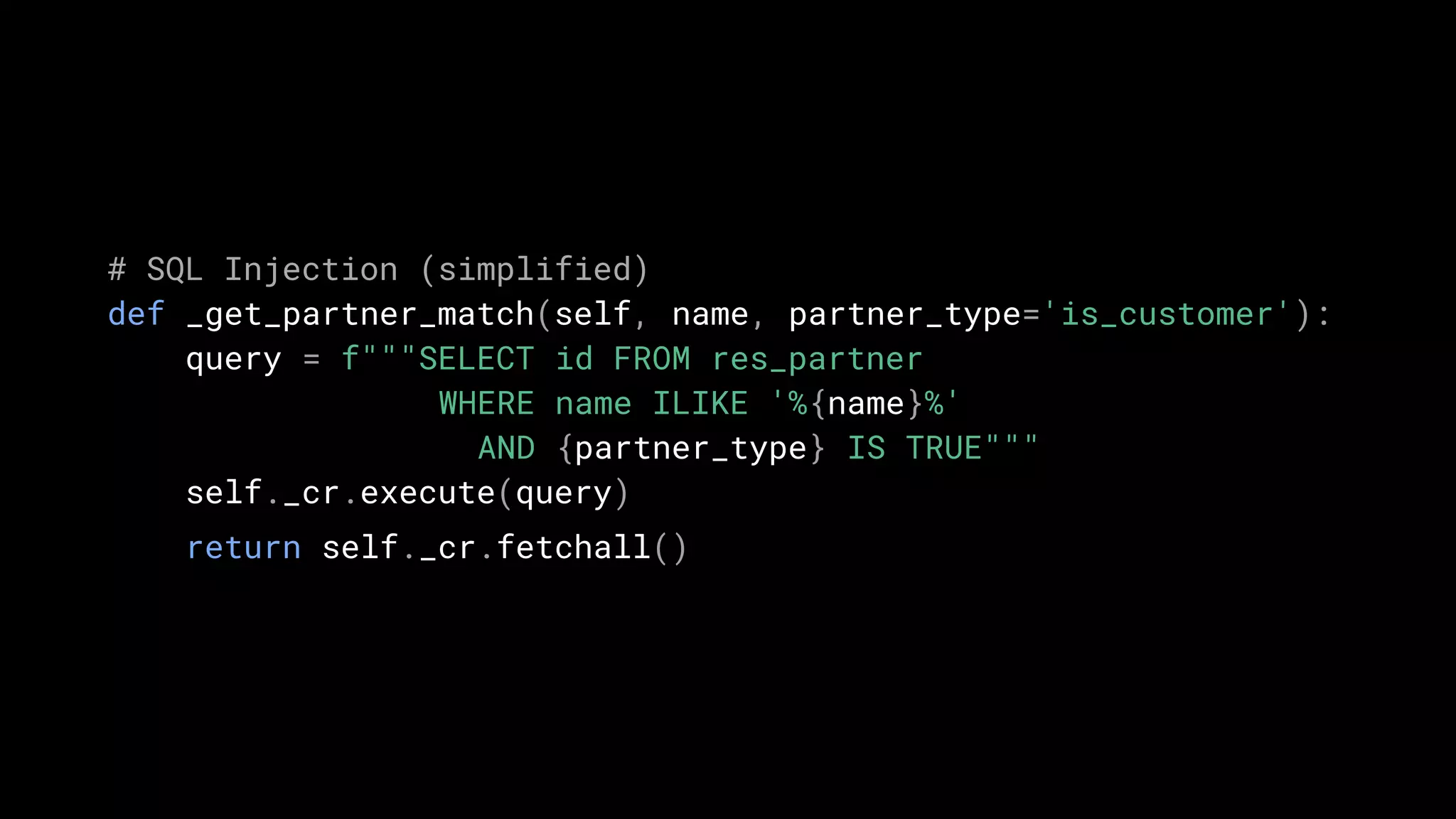
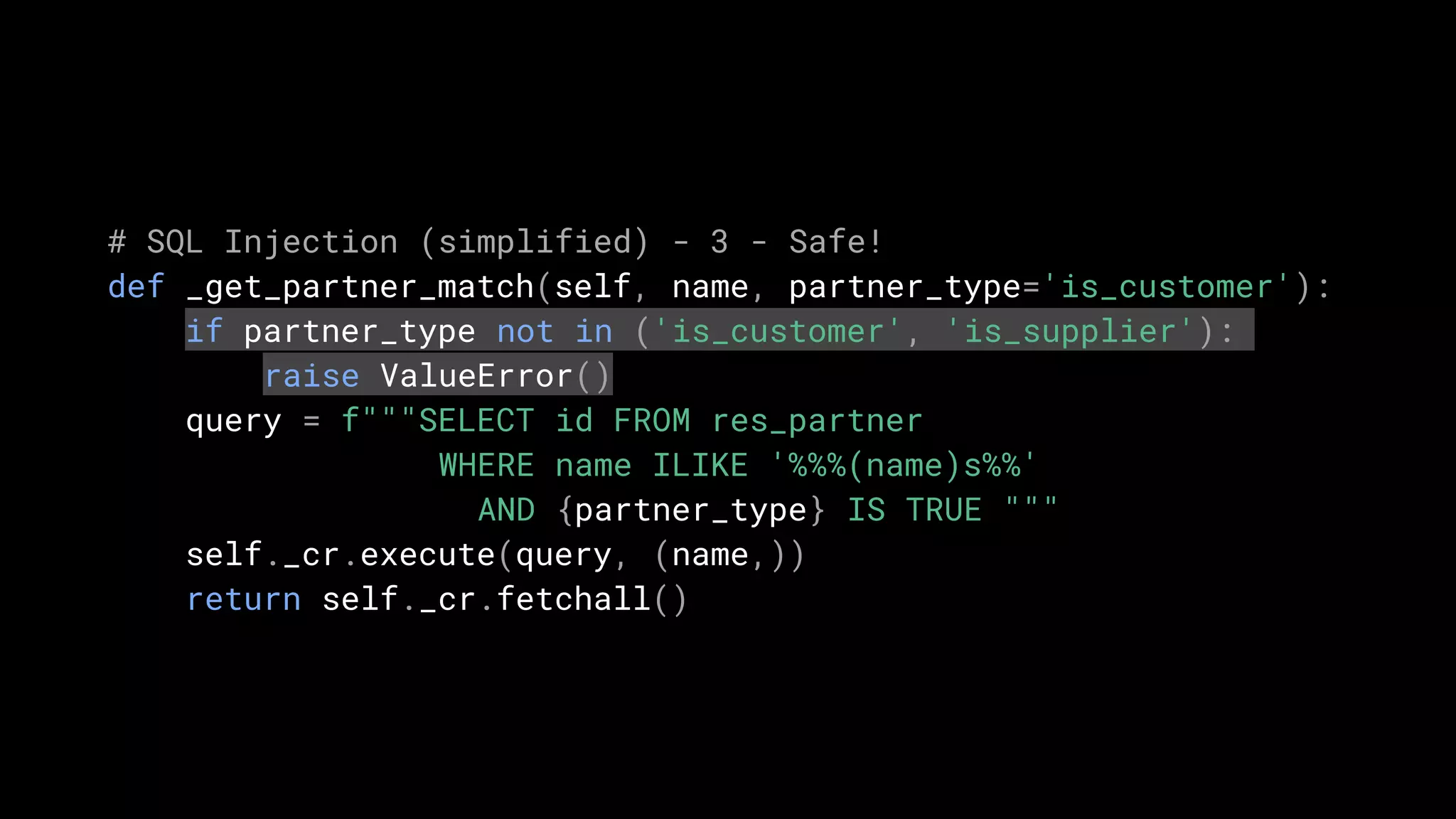
def _get_partner_match(self, name, partner_type='is_customer'):
return self.search([('name', 'ilike', name),
(partner_type, '=', True)])](https://image.slidesharecdn.com/security-odoocodehardening-201103093920/75/Security-Odoo-Code-Hardening-16-2048.jpg)



![XXE: use safe XML parsers
Recursion bombs
<!DOCTYPE xmlbomb [
<!ENTITY a "1234567890" >
<!ENTITY b "&a;&a;&a;&a;&a;&a;&a;&a;">
<!ENTITY c "&b;&b;&b;&b;&b;&b;&b;&b;">
<!ENTITY d "&c;&c;&c;&c;&c;&c;&c;&c;">
]>
<bomb>&d;</bomb>
Local File Inclusion
<!DOCTYPE external [
<!ENTITY ee SYSTEM "file:///etc/password">
]>
<root>ⅇ</root>
The framework protects you.
Use lxml.etree:
etree.fromstring(xml_data)
lxml.etree is configured to reject:
+ recursive entities
+ network resolution
+ local entity resolution
Or have a look at defusedxml.](https://image.slidesharecdn.com/security-odoocodehardening-201103093920/75/Security-Odoo-Code-Hardening-23-2048.jpg)

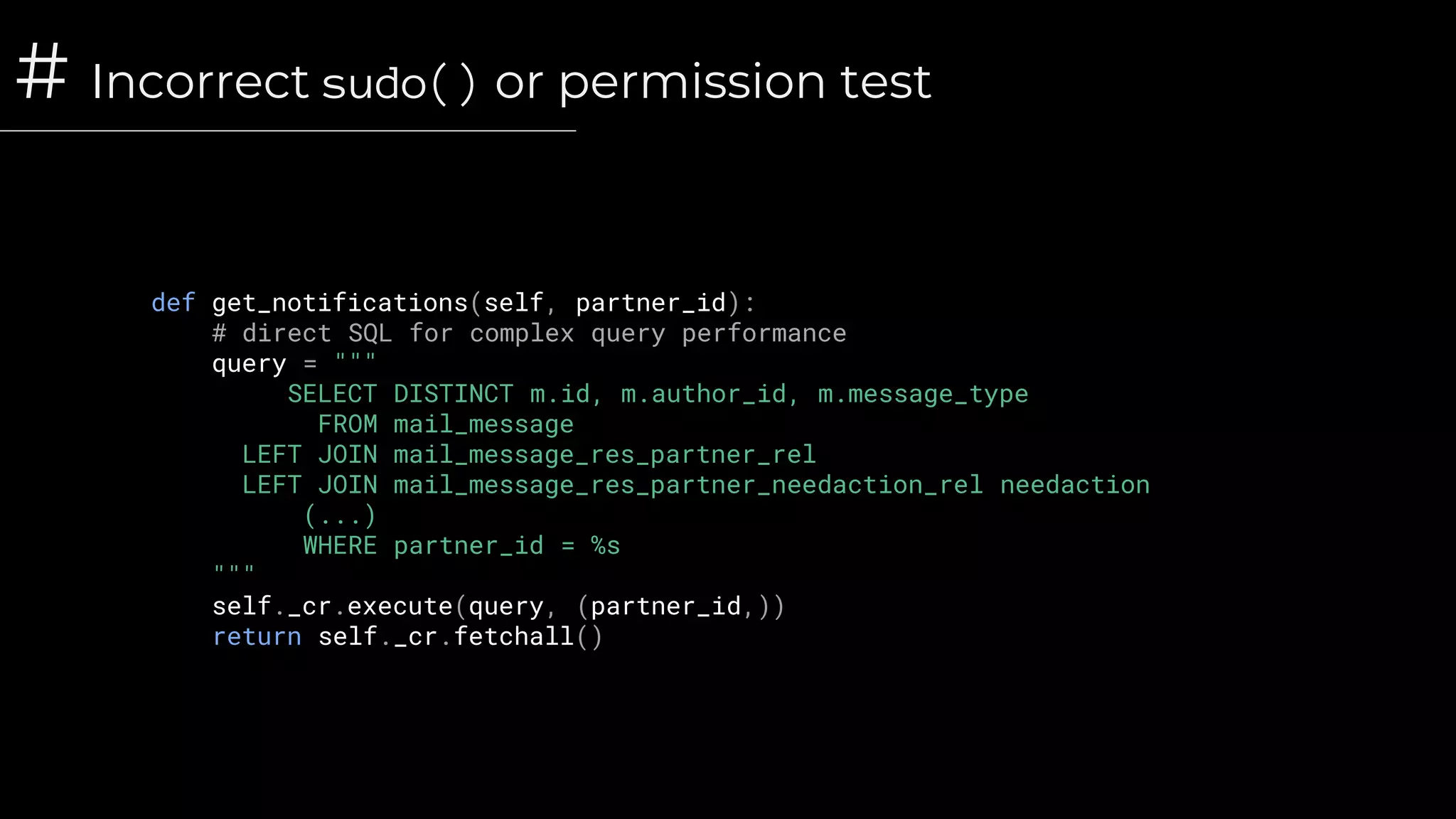
![# Incorrect sudo() or permission test
# Portal controller route
@route(['/sale/<int:order_id>/approve'], type='json', methods=['POST'], auth='public')
def order_approve(self, order_id, **post):
order = self.env['sale.order'].sudo().browse(order_id)
order.action_approve()
user
public
none
converters type methods
auth](https://image.slidesharecdn.com/security-odoocodehardening-201103093920/75/Security-Odoo-Code-Hardening-26-2048.jpg)
![# Incorrect sudo() or permission test
# Portal controller route - bad!
@route(['/sale/<int:order_id>/approve'], type='json', methods=['POST'], auth='public')
def order_approve(self, order_id, **post):
order = self.env['sale.order'].sudo().browse(order_id)
order.action_approve()](https://image.slidesharecdn.com/security-odoocodehardening-201103093920/75/Security-Odoo-Code-Hardening-27-2048.jpg)
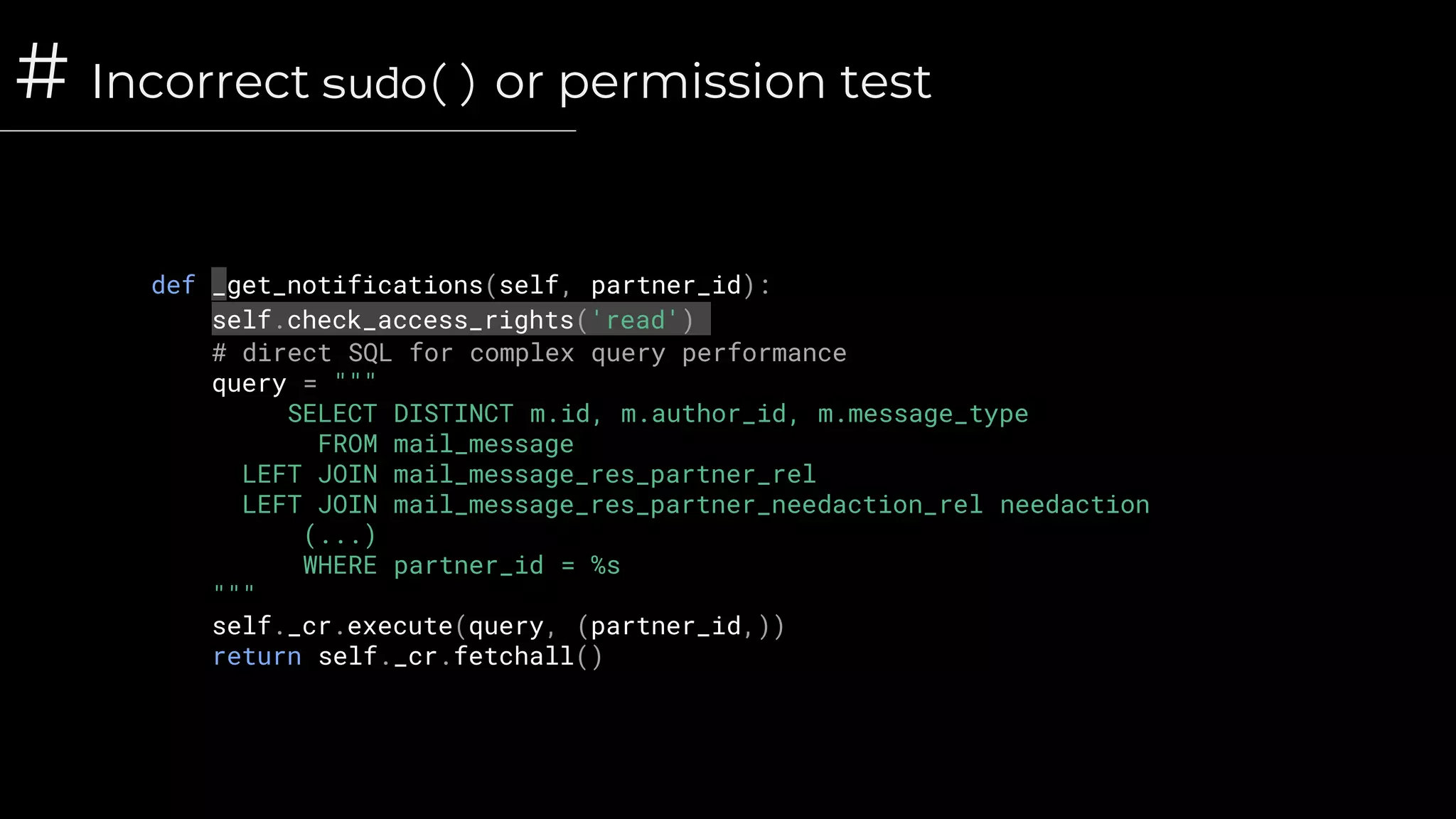
![# Incorrect sudo() or permission test
# Portal controller route - corrected
@route(['/sale/<int:order_id>/approve'], type='http', methods=['POST'], auth='public')
def order_approve(self, order_id, token, **post):
order = self.env['sale.order'].sudo().browse(order_id)
if not tools.consteq(order.access_token, token):
raise AccessDenied()
order.action_approve()](https://image.slidesharecdn.com/security-odoocodehardening-201103093920/75/Security-Odoo-Code-Hardening-28-2048.jpg)







![@classmethod
def _login(cls, db, login, password, user_agent_env):
ip = request.httprequest.environ['REMOTE_ADDR'] if request else 'n/a'
try:
# do login ...
except AccessDenied:
_logger.info("Login failed for db:%s login:%s from %s", db, login, ip)
raise
_logger.info("Login successful for db:%s login:%s from %s", db, login, ip)
_logger.info(
"Password reset attempt for <%s> by user <%s> from %s",
login, request.env.user.login, request.httprequest.remote_addr)
odoo.addons.base.models.res_users: Login failed for db:production login:mike@ex.com from 16.12.19.27
odoo.addons.base.models.res_users: Login successful for db:production login:mike@ex.com from 14.16.23.56
odoo.addons.auth_signup...main: Password reset attempt for <lenny@ex.com> by user <public> from 85.133.187.167](https://image.slidesharecdn.com/security-odoocodehardening-201103093920/75/Security-Odoo-Code-Hardening-45-2048.jpg)
![def assert_log_admin_access(method):
"""Decorator checking that the calling user is an administrator, and logging the call.
Raise an AccessDenied error if the user does not have administrator privileges
"""
def check_and_log(method, self, *args, **kwargs):
user = self.env.user
origin = request.httprequest.remote_addr if request else 'n/a'
log_data = (method.__name__, self.sudo().mapped('name'), user.login, user.id, origin)
if not self.env.is_admin():
_logger.warning('DENY access to module.%s on %s to user %s ID #%s via %s', *log_data)
raise AccessDenied()
_logger.info('ALLOW access to module.%s on %s to user %s #%s via %s', *log_data)
return method(self, *args, **kwargs)
return decorator(check_and_log, method)
odoo...ir_module: ALLOW access to module.button_immediate_uninstall on ['crm'] to user bart@ex.com #2 via 2.5.15.214
odoo...ir_module: ALLOW access to module.button_uninstall on ['crm'] to user bart@ex.com #2 via 2.5.15.214
odoo...ir_module: ALLOW access to module.module_uninstall on ['sale_crm', 'crm'] to user __system__ #1 via 2.5.15.214](https://image.slidesharecdn.com/security-odoocodehardening-201103093920/75/Security-Odoo-Code-Hardening-46-2048.jpg)