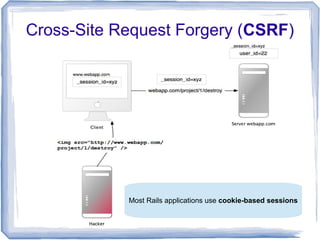
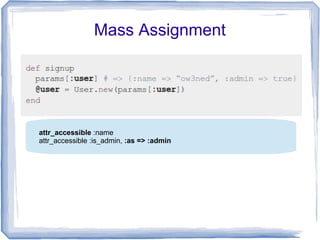
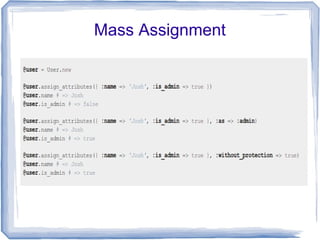
This document discusses various security vulnerabilities in Ruby on Rails applications including session hijacking, CSRF, mass assignment, and SQL injection. It provides recommendations to address these issues such as using SSL, adding session expiration, sanitizing user input, and using parameterized queries. The key takeaway is that security must be an ongoing process as new vulnerabilities emerge, and failing to address issues can enable catastrophic attacks on applications and user data.













![Header Injection
redirect_to params[:referer]
http://www.yourapplication.com/controller/action?
referer=http://www.malicious.tld
Make sure you do it yourself when you
build other header fields with user input.](https://image.slidesharecdn.com/securityonrails-121007203413-phpapp01/85/Security-on-Rails-14-320.jpg)


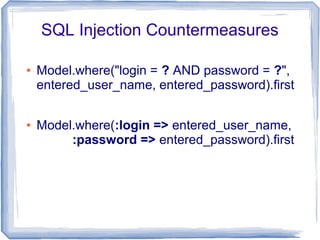
![SQL Injection
● Project.where("name = '#{params[:name]}'")
SELECT * FROM projects WHERE name = '' OR 1'
● User.first("login = '#{params[:name]}' AND
password = '#{params[:password]}'")
SELECT * FROM users WHERE login = '' OR '1'='1' AND
password = '' OR '2'>'1' LIMIT 1](https://image.slidesharecdn.com/securityonrails-121007203413-phpapp01/85/Security-on-Rails-20-320.jpg)