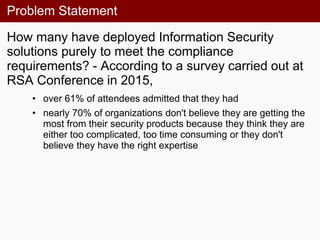
The document discusses security beyond compliance. It summarizes a presentation about moving past a compliance-focused approach to security. The presentation addresses how the majority of organizations deploy security solutions only to meet compliance requirements. Additionally, most organizations do not feel they are getting full value from their security products due to complexity, time consumption, or lack of expertise. The presentation argues that to improve security, organizations need to focus on increasing expert knowledge, improving user behavior, and advancing their security technology rather than just seeking compliance. It promotes taking a more holistic approach to security beyond just compliance.