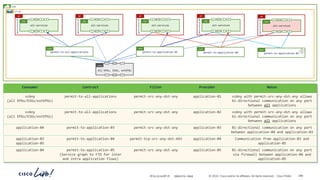
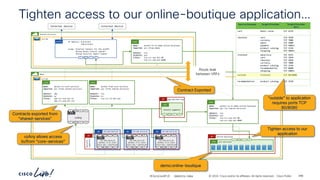
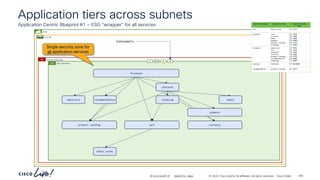
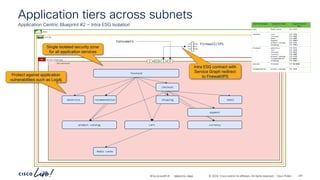
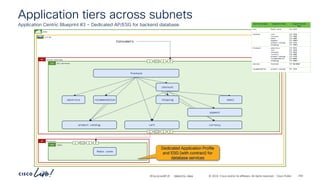
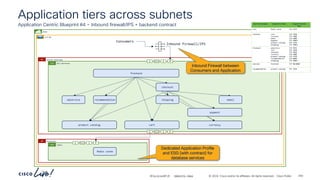
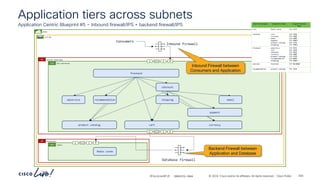
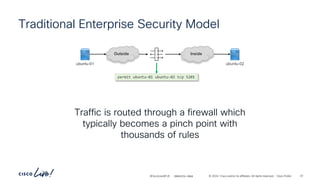
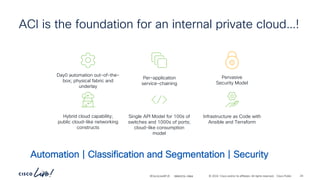
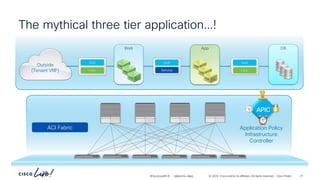
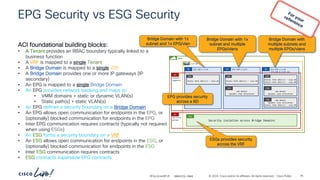
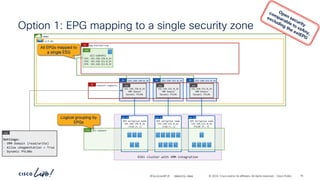
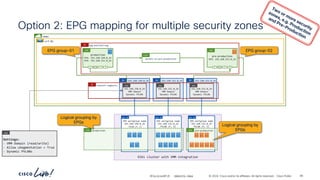
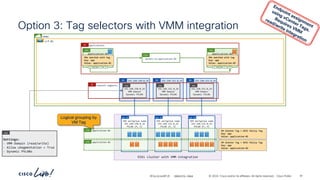
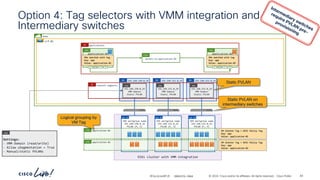
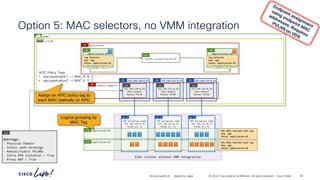
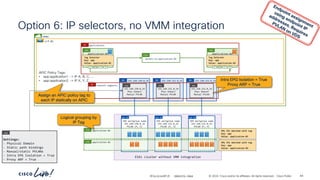
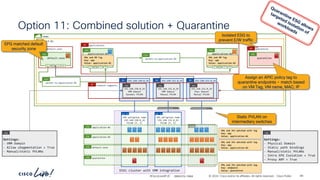
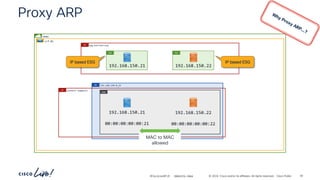
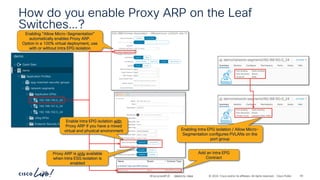
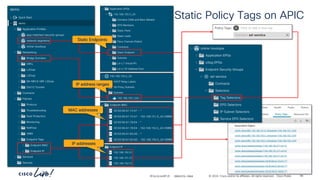
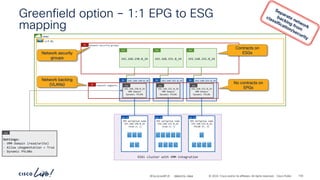
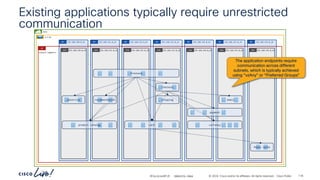
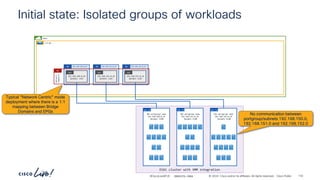
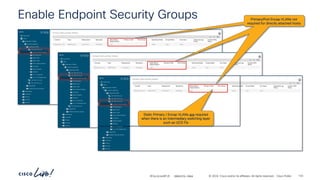
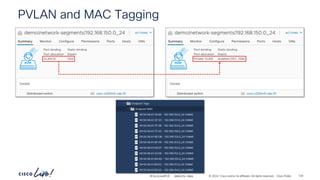
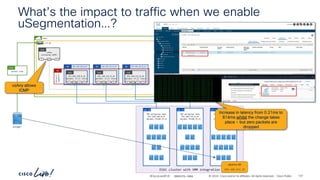
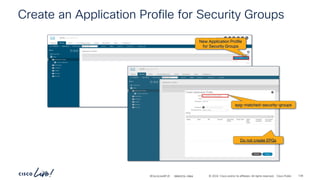
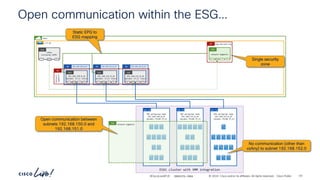
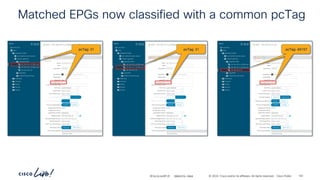
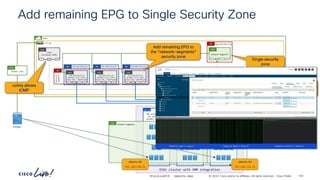
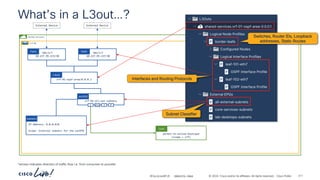
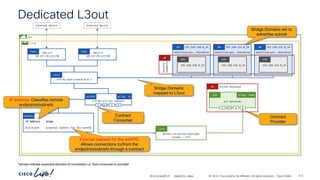
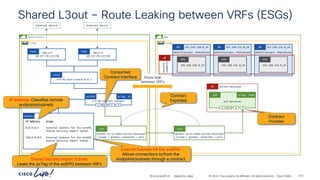
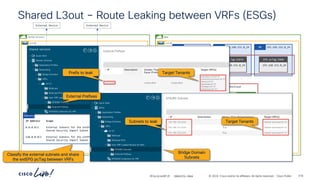
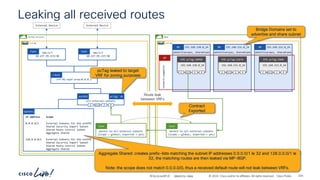
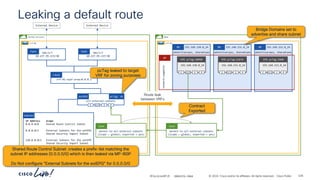
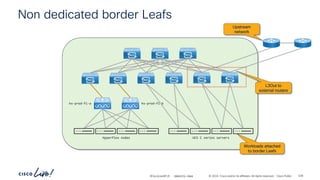
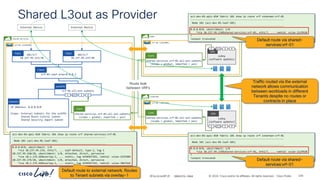
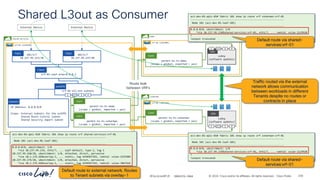
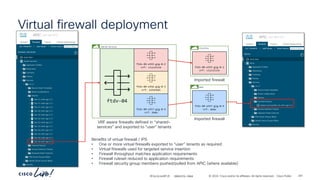
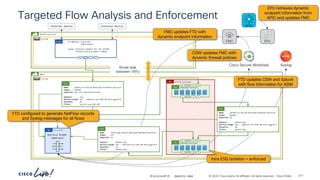
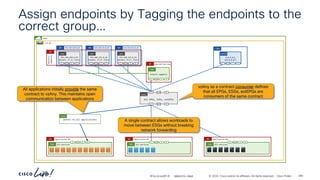
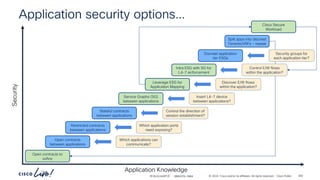
The document discusses Cisco's approach to implementing an Application Centric Infrastructure (ACI) as a foundation for internal private cloud systems. It covers key topics such as network design considerations, security models, application-centric modes, and automation blueprints. Additionally, it emphasizes the importance of network connectivity and security in cloud environments, along with various diagrams for reference.































































![-
#CiscoLiveAPJC © 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
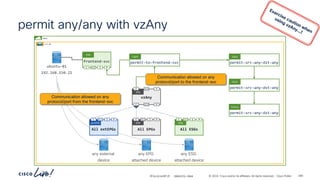
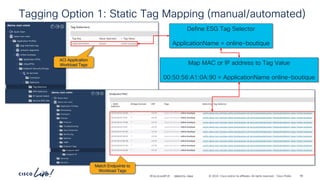
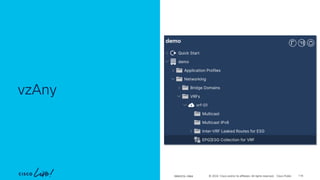
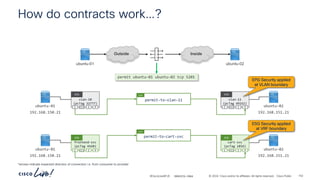
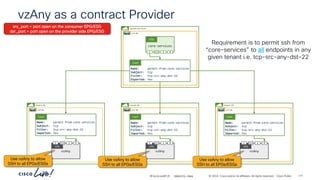
permit-any
Cont
permit-any
Subj
permit-any
Filt
unspecified
Entry
ubuntu-01
192.168.150.21
ubuntu-02
192.168.151.21
frontend-svc
P
C I
CCI
ESG
cart-svc
P
C I
CCI
ESG
permit any/any
# netcat –l [any]
# netcat –p [any] ubuntu-02 [any]
ubuntu-01
192.168.150.21
ubuntu-02
192.168.151.21
# netcat –l [any] # netcat –p [any] ubuntu-01 [any]
BRKDCN-2984 157](https://image.slidesharecdn.com/cdnaciforciscoprivatecloud-241204133727-a9a38665/85/Sdn-aci-for-cisco-private-cloud-building-onprem-pdf-129-320.jpg)

![-
#CiscoLiveAPJC © 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
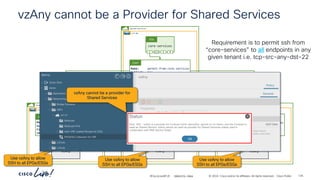
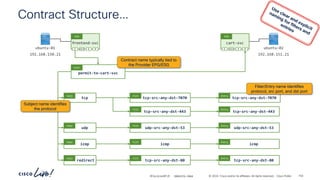
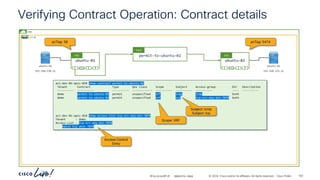
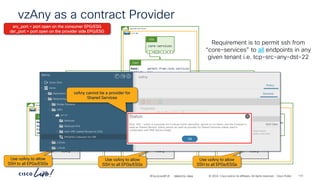
Verifying Contract operation with netcat – Stateful = No
demo
vrf-01
ubuntu-02
P
C I
CCI
ESG
ubuntu-01
P
C I
CCI
ESG permit-to-ubuntu-02
Cont
tcp
Subj
tcp-src-any-dst-7070
Filt
tcp-src-any-dst-7070
(Stateful: No)
Entry
# netcat –l 7071
# netcat –p [any] ubuntu-02 7070
# netcat –l 5000 # netcat –p 7070 ubuntu-01 5000
# netcat –l 7070
# netcat –p [any] ubuntu-02 7070
# netcat –l 5000 # netcat –p 7071 ubuntu-01 5000
ubuntu-01
192.168.150.21
ubuntu-02
192.168.151.21
ubuntu-01
192.168.150.21
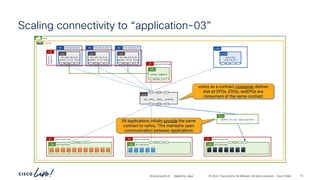
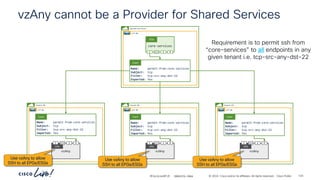
Communication to and from
port “7070” is allowed
Stateful: No
Provider to Consumer connections
are allowed when the Provider side
port is specified as the source port
Incorrect Provider side port
ubuntu-02
192.168.151.21
Communication to and from
“any” port is allowed
BRKDCN-2984 160](https://image.slidesharecdn.com/cdnaciforciscoprivatecloud-241204133727-a9a38665/85/Sdn-aci-for-cisco-private-cloud-building-onprem-pdf-132-320.jpg)
![-
#CiscoLiveAPJC © 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
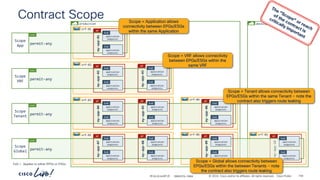
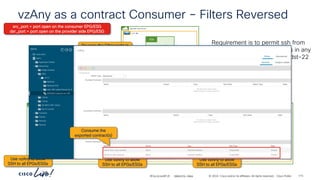
Verifying Contract operation with netcat – Stateful = Yes
demo
vrf-01
ubuntu-02
P
C I
CCI
ESG
ubuntu-01
P
C I
CCI
ESG permit-to-ubuntu-02
Cont
tcp
Subj
tcp-src-any-dst-7070
Filt
tcp-src-any-dst-7070
(Stateful: Yes)
Entry
# netcat –l 7071
# netcat –p [any] ubuntu-02 7070
# netcat –l 5000 # netcat –p 7070 ubuntu-01 5000
# netcat –l 7070
# netcat –p [any] ubuntu-02 7070
# netcat –l 5000 # netcat –p 7071 ubuntu-01 5000
ubuntu-01
192.168.150.21
ubuntu-02
192.168.151.21
ubuntu-01
192.168.150.21
Communication to and from
port “7070” is allowed
Stateful: Yes
Provider to Consumer connections
are blocked as the contract is a
“stateful” contract
Incorrect Provider side port
ubuntu-02
192.168.151.21
Communication to and from
“any” port is allowed
BRKDCN-2984 165](https://image.slidesharecdn.com/cdnaciforciscoprivatecloud-241204133727-a9a38665/85/Sdn-aci-for-cisco-private-cloud-building-onprem-pdf-136-320.jpg)

![-
#CiscoLiveAPJC © 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
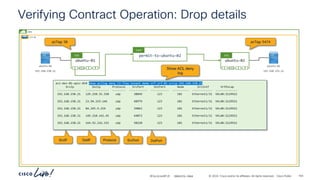
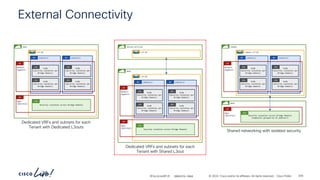
Reversing the Filter ports – Stateful = No
demo
vrf-01
ubuntu-02
P
C I
CCI
ESG
ubuntu-01
P
C I
CCI
ESG permit-to-ubuntu-02
Cont
tcp
Subj
# netcat –p [any] ubuntu-01 22
# netcat –l 22
# netcat –l 5000 # netcat –p [any] ubuntu-01 5000
# netcat –l 5000
# netcat –p 22 ubuntu-02 5000
ubuntu-01
192.168.150.21
ubuntu-02
192.168.151.21
ubuntu-01
192.168.150.21
Communication to and from
“any” port is allowed
Stateful: No
Provider to Consumer connections
are allowed when the Provider side
port is specified as the source port
Incorrect Consumer side port
ubuntu-02
192.168.151.21
Communication to and from
port “22” is allowed
Source port must be
“22”
BRKDCN-2984 169
tcp-src-22-dst-any
Filt
tcp-src-22-dst-any
(Stateful: No)
Entry](https://image.slidesharecdn.com/cdnaciforciscoprivatecloud-241204133727-a9a38665/85/Sdn-aci-for-cisco-private-cloud-building-onprem-pdf-140-320.jpg)










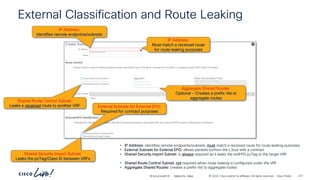






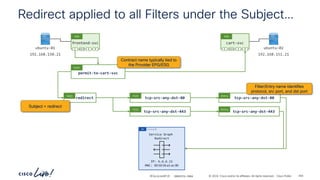


![-
#CiscoLiveAPJC © 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
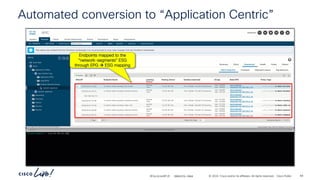
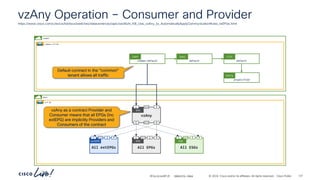
192.168.152.0_24
BD 192.168.152.0_24
BD
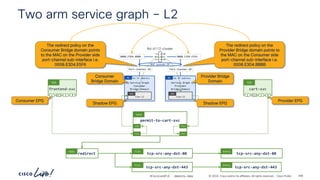
Two arm service graph – L3 Cons to Prov
6.6.6.0_24
BD
Service Graph
Consumer
Bridge Domain
7.7.7.0_24
BD
Service Graph
Provider
Bridge Domain
vlan-12
EPG
vlan-13
EPG
ftd-4112-cluster
Port-channel-10 Port-channel-30
Shadow EPG
Shadow EPG
Consumer
Bridge Domain
Consumer EPG Provider EPG
frontend-svc
P
C I
CCI
ESG
cart-svc
P
C I
CCI
ESG
redirect
Subj
tcp-src-any-dst-80
Filt
tcp-src-any-dst-80
Entry
tcp-src-any-dst-443
Filt
tcp-src-any-dst-443
Entry
BRKDCN-2984 268
permit-to-cart-svc
Cont
Cons
Cons
Prov
Prov
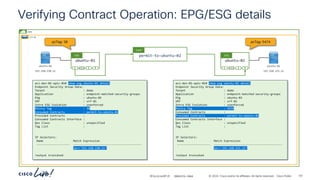
> show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
<output truncated>
Gateway of last resort is not set
C 6.6.6.0 255.255.255.0 is directly connected, Port-channel10-vlan-12
L 6.6.6.10 255.255.255.255
is directly connected, Port-channel10-vlan-12
C 7.7.7.0 255.255.255.0 is directly connected, Port-Cannel30-vlan-13
L 7.7.7.10 255.255.255.255 is directly connected, Port-Cannel30-vlan-13
S 192.168.151.0 255.255.255.0 [1/0] via 6.6.6.1, Port-channel10-vlan-12
S 192.168.152.0 255.255.255.0 [1/0] via 7.7.7.1, Port-channel30-vlan-13
Firewall static
routes
Provider Bridge
Domain](https://image.slidesharecdn.com/cdnaciforciscoprivatecloud-241204133727-a9a38665/85/Sdn-aci-for-cisco-private-cloud-building-onprem-pdf-180-320.jpg)
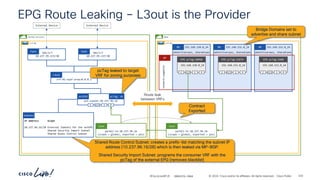
![-
#CiscoLiveAPJC © 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
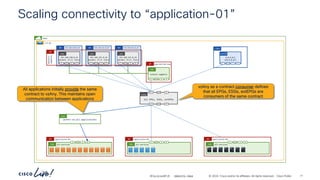
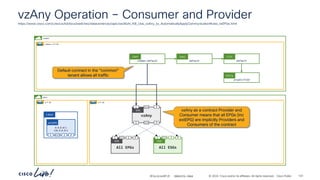
192.168.151.0_24
BD 192.168.152.0_24
BD
Two arm service graph – L3 Prov to Cons
6.6.6.0_24
BD
Service Graph
Consumer
Bridge Domain
7.7.7.0_24
BD
Service Graph
Provider
Bridge Domain
vlan-12
EPG
vlan-13
EPG
ftd-4112-cluster
Port-channel-10 Port-channel-30
Shadow EPG
Shadow EPG
Consumer
Bridge Domain
Consumer EPG Provider EPG
frontend-svc
P
C I
CCI
ESG
cart-svc
P
C I
CCI
ESG
redirect
Subj
tcp-src-any-dst-80
Filt
tcp-src-any-dst-80
Entry
tcp-src-any-dst-443
Filt
tcp-src-any-dst-443
Entry
BRKDCN-2984 269
permit-to-cart-svc
Cont
Cons
Cons
Prov
Prov
> show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
<output truncated>
Gateway of last resort is not set
C 6.6.6.0 255.255.255.0 is directly connected, Port-channel10-vlan-12
L 6.6.6.10 255.255.255.255
is directly connected, Port-channel10-vlan-12
C 7.7.7.0 255.255.255.0 is directly connected, Port-Cannel30-vlan-13
L 7.7.7.10 255.255.255.255 is directly connected, Port-Cannel30-vlan-13
S 192.168.151.0 255.255.255.0 [1/0] via 6.6.6.1, Port-channel10-vlan-12
S 192.168.152.0 255.255.255.0 [1/0] via 7.7.7.1, Port-channel30-vlan-13
Firewall static
routes
Provider Bridge
Domain
Traffic received on the Firewall consumer interface.
The Firewall has a static route pointing back out of the
incoming interface, therefore traffic does not traverse
the consumer/provider interfaces.](https://image.slidesharecdn.com/cdnaciforciscoprivatecloud-241204133727-a9a38665/85/Sdn-aci-for-cisco-private-cloud-building-onprem-pdf-181-320.jpg)

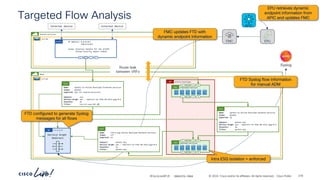




![-
#CiscoLiveAPJC © 2024 Cisco and/or its affiliates. All rights reserved. Cisco Public
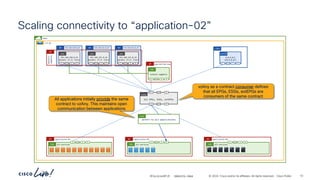
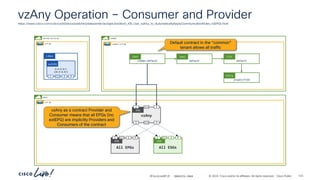
permit-any
Cont
permit-any
Subj
permit-any
Filt
unspecified
Entry
ubuntu-01
192.168.150.21
ubuntu-02
192.168.151.21
frontend-svc
P
C I
CCI
ESG
cart-svc
P
C I
CCI
ESG
permit any/any
# netcat –l [any]
# netcat –p [any] ubuntu-02 [any]
ubuntu-01
192.168.150.21
ubuntu-02
192.168.151.21
# netcat –l [any] # netcat –p [any] ubuntu-01 [any]
Communication allowed to/from any
protocol/port in both directions
BRKDCN-2984 284](https://image.slidesharecdn.com/cdnaciforciscoprivatecloud-241204133727-a9a38665/85/Sdn-aci-for-cisco-private-cloud-building-onprem-pdf-193-320.jpg)