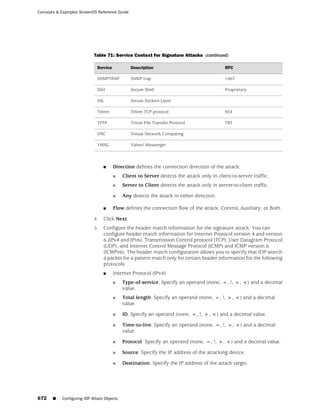
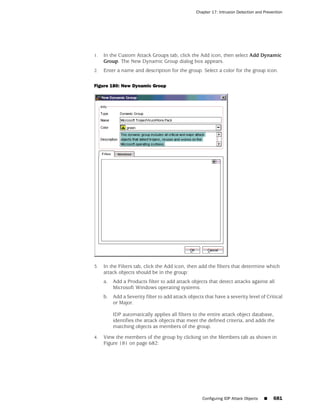
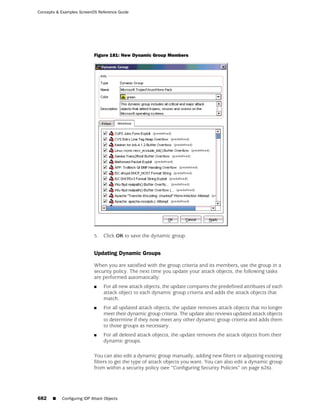
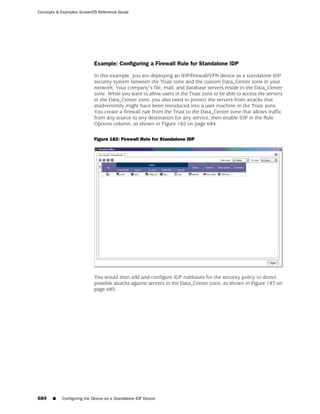
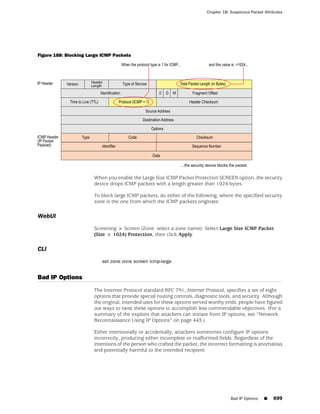
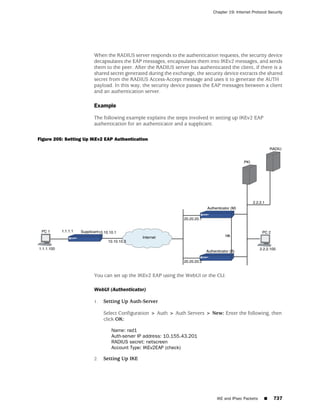
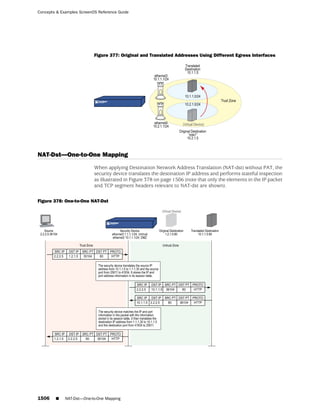
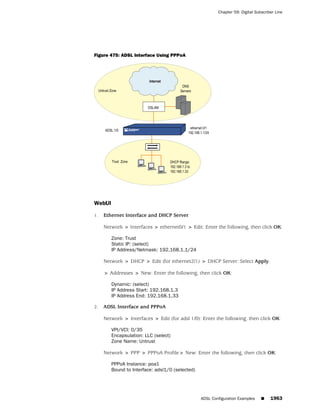
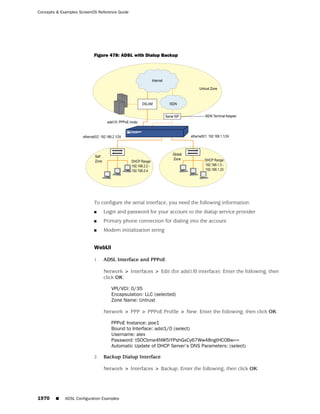
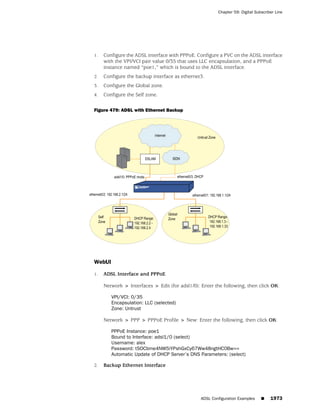
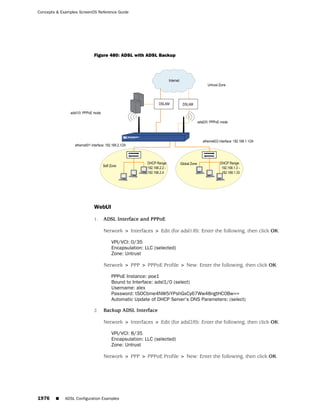
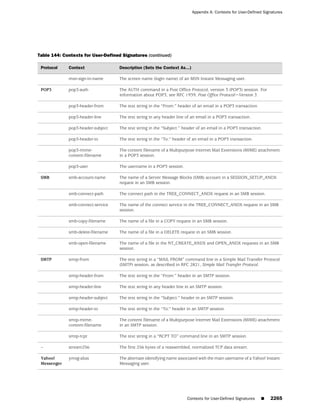
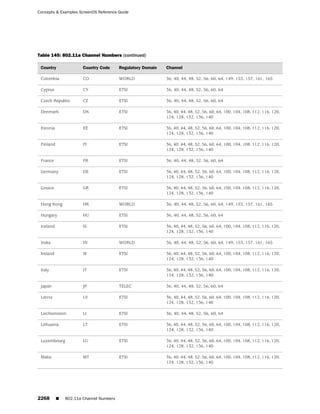
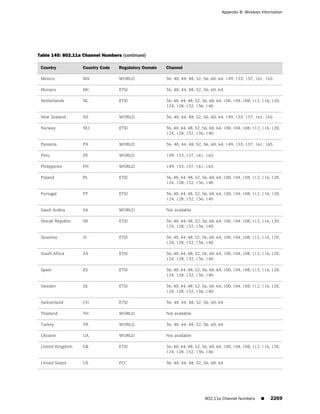
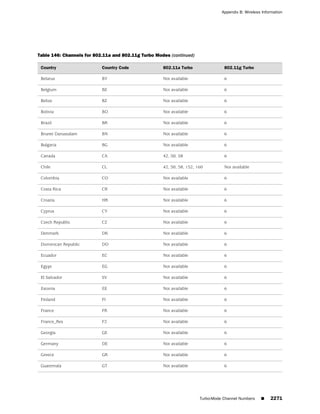
This document is the Concepts & Examples ScreenOS Reference Guide for Juniper Networks, Release 6.3.0, detailing software licensing, use restrictions, and revision history. It outlines the license agreement terms, prohibitions, and customer responsibilities, including confidentiality and compliance with export laws. Additionally, the document includes a table of contents for various technical topics related to ScreenOS architecture, policies, and security mechanisms.















































































































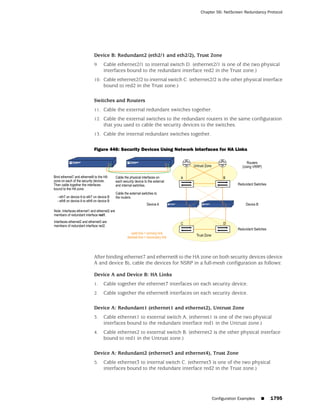
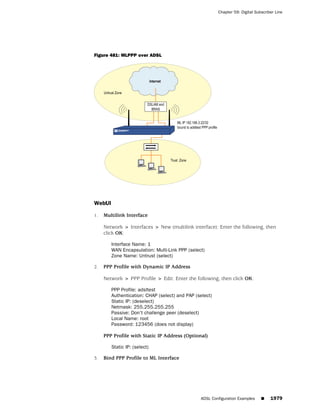
![Chapter 1: About the Concepts & Examples ScreenOS Reference Guide
from the list, and follow the instructions on the page. Click the ? character in the
upper right for Online Help on the Config Guide.
Command Line Interface Conventions
The following conventions are used to present the syntax of command line interface
(CLI) commands in text and examples.
In text, commands are in boldface type and variables are in italic type.
In examples:
■ Variables are in italic type.
■ Anything inside square brackets [ ] is optional.
■ Anything inside braces { } is required.
■ If there is more than one choice, each choice is separated by a pipe ( | ). For
example, the following command means “set the management options for the
ethernet1, the ethernet2, or the ethernet3 interface” :
NOTE: When entering a keyword, you only have to type enough letters to identify
the word uniquely. Typing set adm u whee j12fmt54 will enter the command set
admin user wheezer j12fmt54. However, all the commands documented in this
guide are presented in their entirety.
Naming Conventions and Character Types
ScreenOS employs the following conventions regarding the names of objects—such
as addresses, admin users, auth servers, IKE gateways, virtual systems, VPN tunnels,
and zones—defined in ScreenOS configurations:
■ If a name string includes one or more spaces, the entire string must be enclosed
within double quotes; for example:
set address trust “local LAN” 10.1.1.0/24
■ Any leading spaces or trailing text within a set of double quotes are trimmed;
for example, “ local LAN ” becomes “local LAN” .
■ Multiple consecutive spaces are treated as a single space.
■ Name strings are case-sensitive, although many CLI keywords are case-insensitive.
For example, “local LAN” is different from “local lan” .
ScreenOS supports the following character types:
■ Single-byte character sets (SBCS) and multiple-byte character sets (MBCS).
Examples of SBCS are ASCII, European, and Hebrew. Examples of MBCS—also
referred to as double-byte character sets (DBCS)—are Chinese, Korean, and
Japanese.
Document Conventions ■ 11](https://image.slidesharecdn.com/630ceall-120330145020-phpapp02/85/ScreenOS-6-1-Concepts-Examples-115-320.jpg)







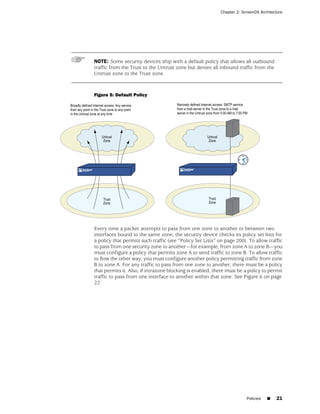


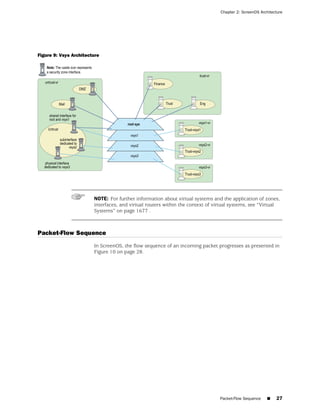






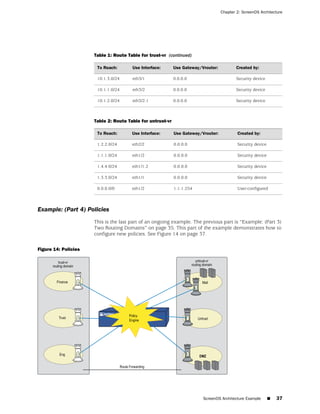









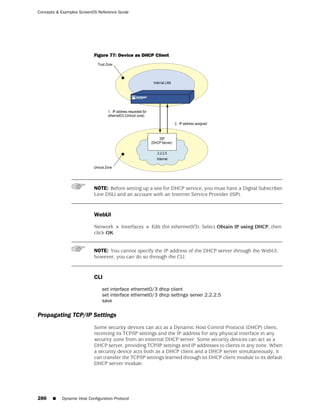
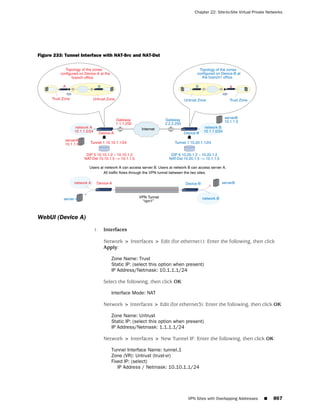
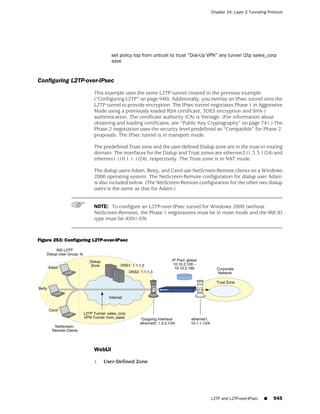
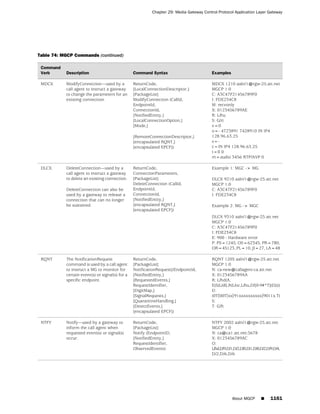
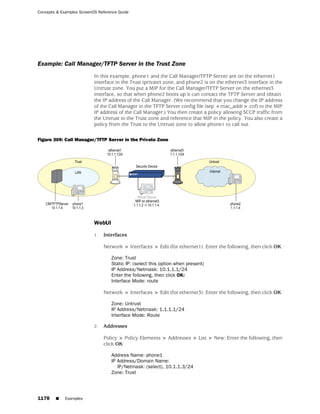
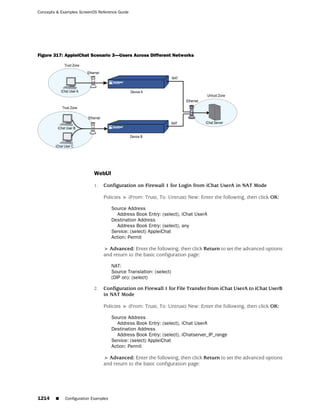
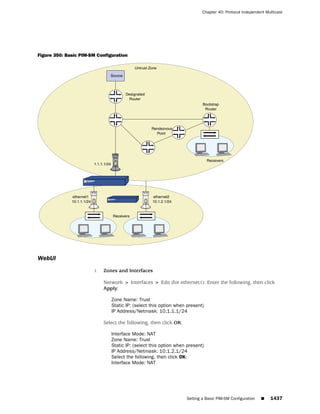
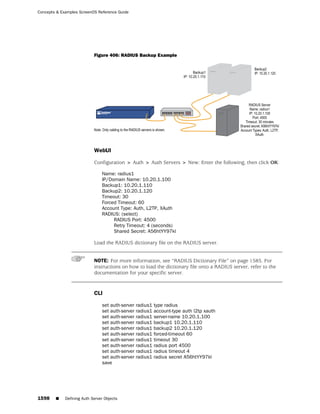
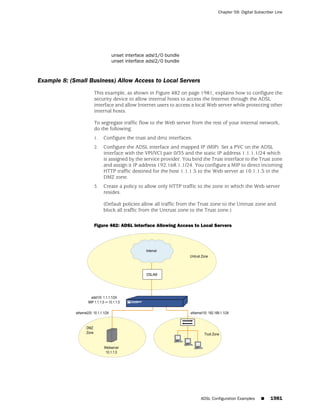
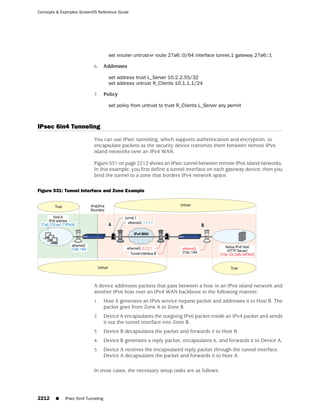
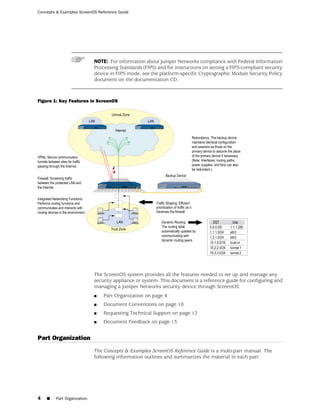
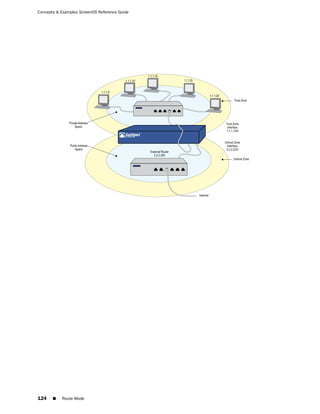
![Concepts & Examples ScreenOS Reference Guide
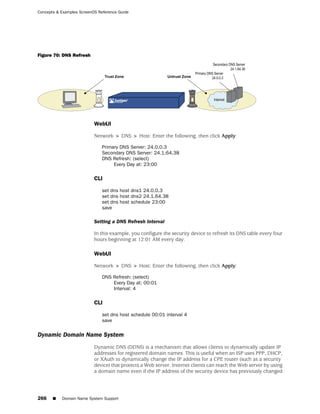
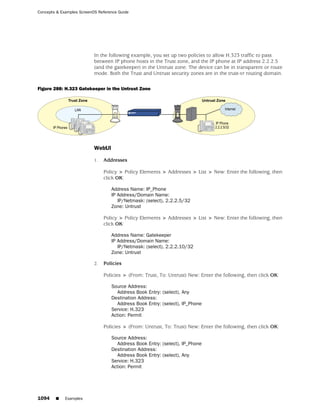
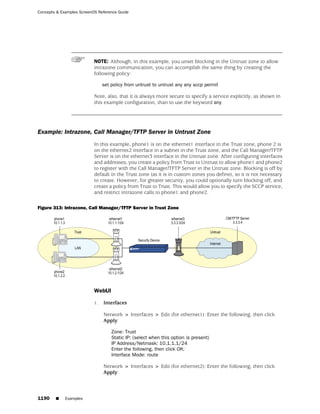
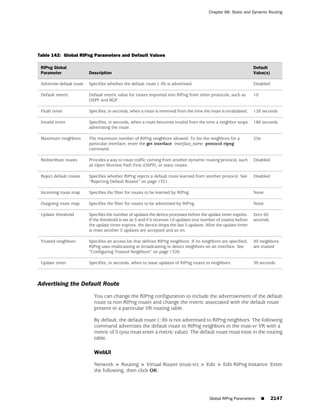
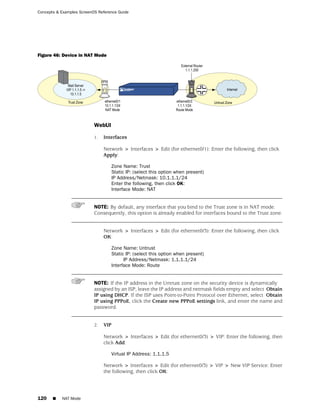
WebUI
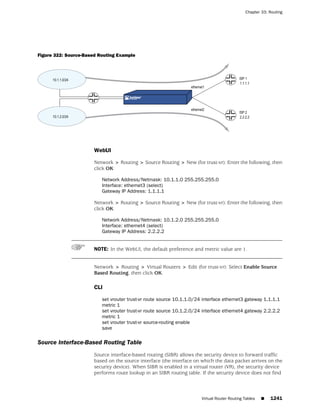
Network > Zones > New: Enter the following, then click OK:
Zone Name: Type a name for the zone.
Virtual Router Name: Select the virtual router in whose routing domain you want
to place the zone.
Zone Type:
Select Layer 3 to create a zone to which you can bind interfaces in NAT or route
mode.
Select Layer 2 to create a zone to which you can bind interfaces in transparent mode.
Select Tunnel Out Zone when creating a tunnel zone and binding it to a carrier zone,
then select a specific carrier zone from the drop-down list.
Block Intra-Zone Traffic: Select this option to block traffic between hosts within the
same security zone. By default, intra-zone blocking is disabled.
NOTE: The name of a Layer 2 security zone must begin with “L2-” ; for example, “
L2-Corp” or “ L2-XNet.”
CLI
set zone name zone [ l2 vlan_id_num | tunnel sec_zone ]
set zone zone block
set zone zone vrouter name_str
save
NOTE: When creating a Layer 2 security zone, the VLAN ID number must be 1 (for
VLAN1).
Modifying a Zone
To modify the name of a security zone or tunnel zone, or to change the carrier zone
for a tunnel zone, you must first delete the zone and then create it again with the
changes. You can change the intra-zone blocking option and the virtual router on an
existing zone.
NOTE: Before you can remove a zone, you must first unbind all interfaces bound to
it.
Before you can change the virtual router for a zone, you must first remove any
interfaces bound to it.
48 ■ Configuring Security Zones and Tunnel Zones](https://image.slidesharecdn.com/630ceall-120330145020-phpapp02/85/ScreenOS-6-1-Concepts-Examples-152-320.jpg)
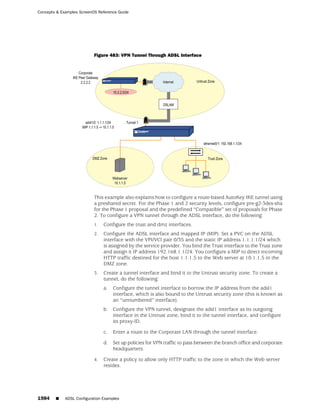
![Chapter 3: Zones
WebUI
1. Modifying the Zone Name
Network > Zones: Click Remove (for the security zone or tunnel zone whose
name you want to change or for the tunnel zone whose carrier zone you want
to change).
When the prompt appears, asking for confirmation of the removal, click Yes.
Network > Zones > New: Enter the zone settings with your changes, then click
OK.
2. Changing the Intra-Zone Blocking Option or Virtual Router
Network > Zones > Edit (for the zone that you want to modify): Enter the
following, then click OK:
Virtual Router Name: From the drop-down list, select the virtual router into whose
routing domain you want to move the zone.
Block Intra-Zone Traffic: To enable, select the check box. To disable, clear it.
CLI
1. Modifying the Zone Name
unset zone zone
set zone name zone [ l2 vlan_id_num | tunnel sec_zone ]
2. Changing the Intra-Zone Blocking Option or Virtual Router
{ set | unset } zone zone block
set zone zone vrouter name_str
save
Deleting a Zone
For best performance, always save your changes and reboot after deleting a zone.
To delete a security zone or tunnel zone, do either of the following:
WebUI
Network > Zones: Click Remove (for the zone you want to delete).
When the prompt appears, asking for confirmation of the removal, click Yes.
CLI
unset zone zone
Configuring Security Zones and Tunnel Zones ■ 49](https://image.slidesharecdn.com/630ceall-120330145020-phpapp02/85/ScreenOS-6-1-Concepts-Examples-153-320.jpg)


































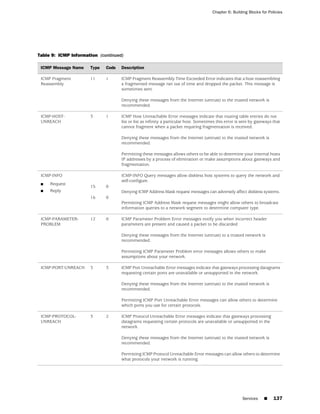
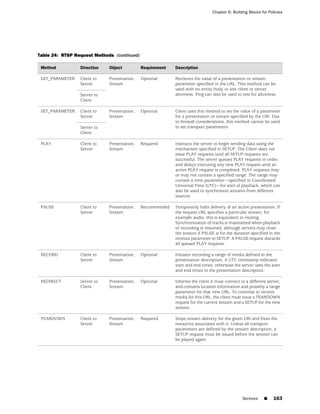
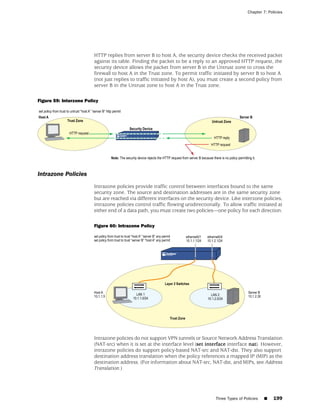
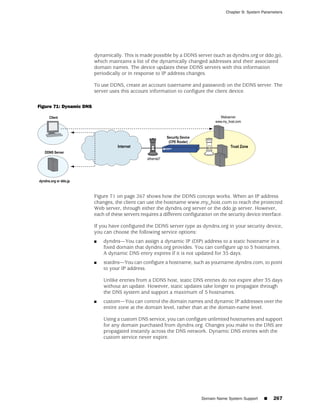
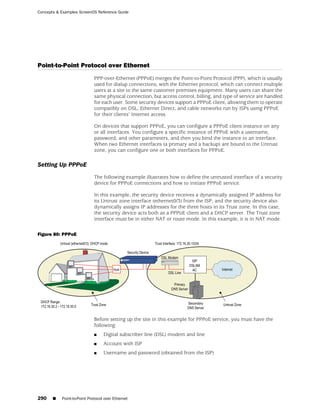
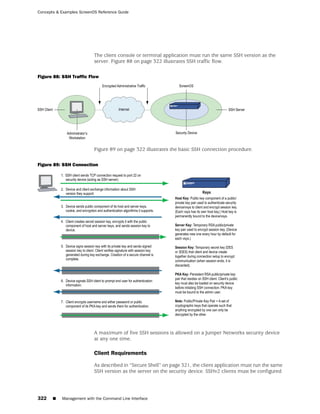
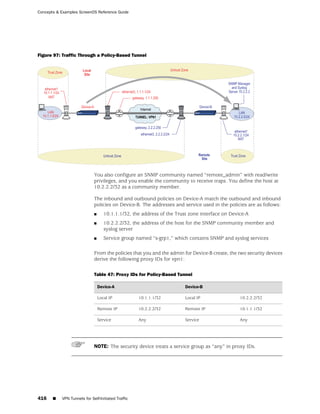
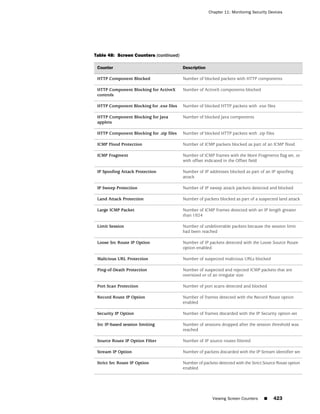
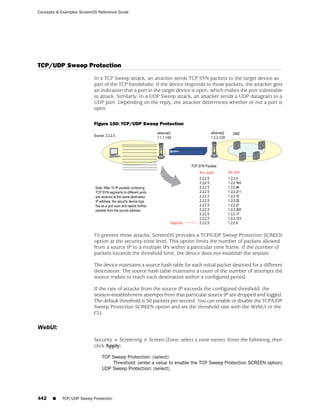
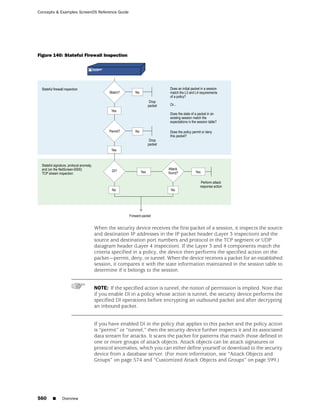
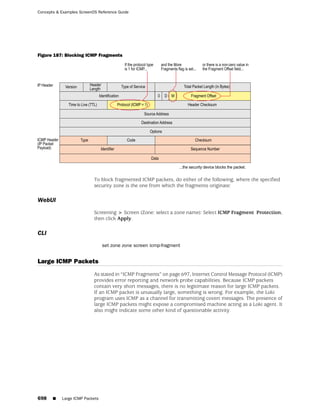
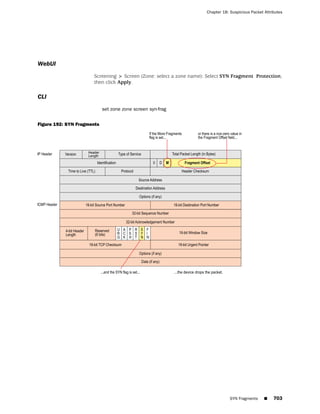
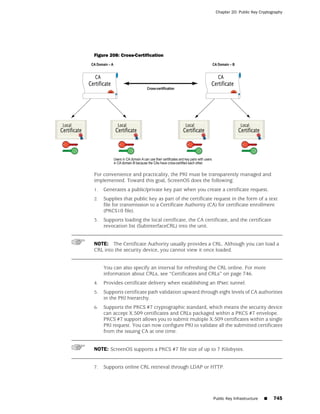
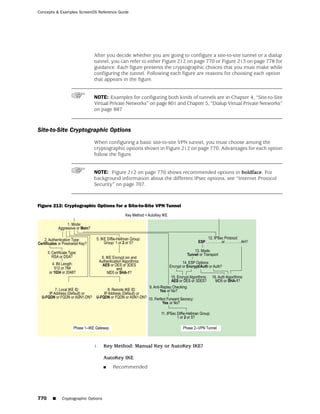
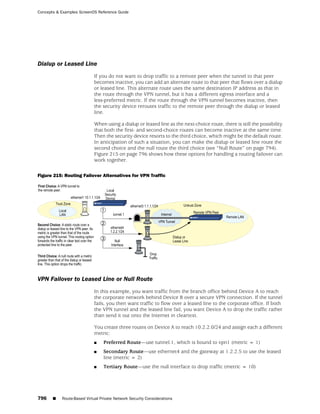
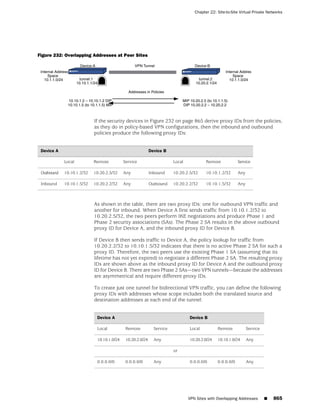
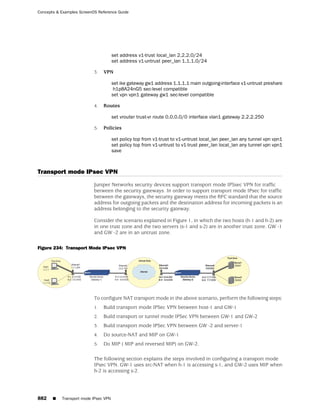
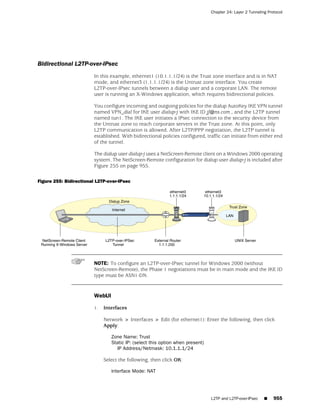
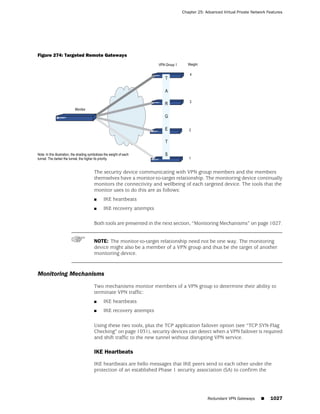
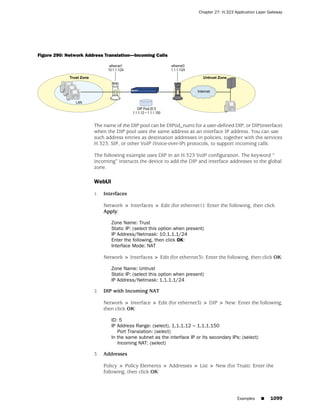
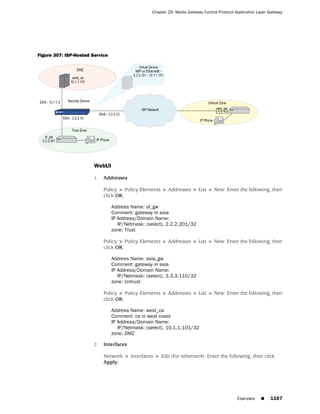
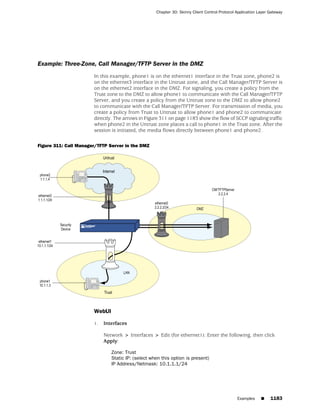
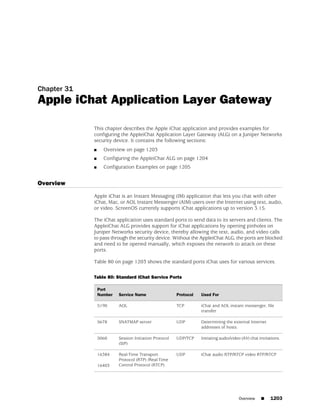
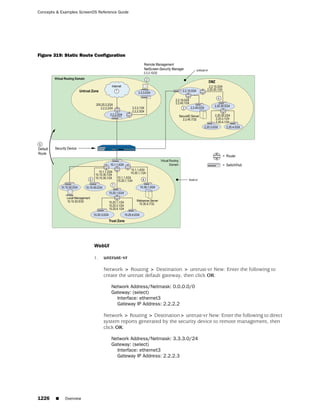
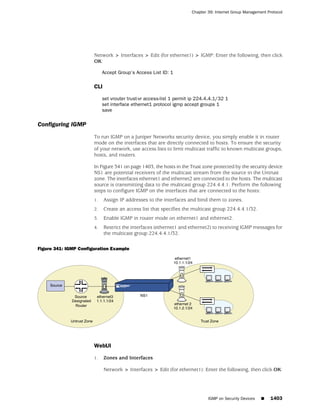
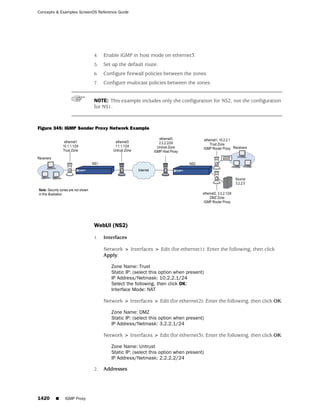
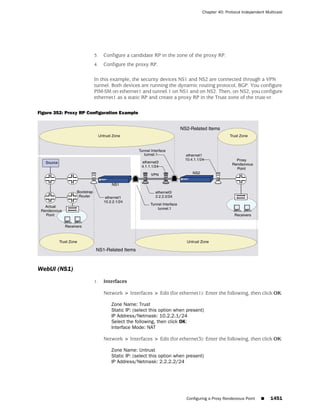
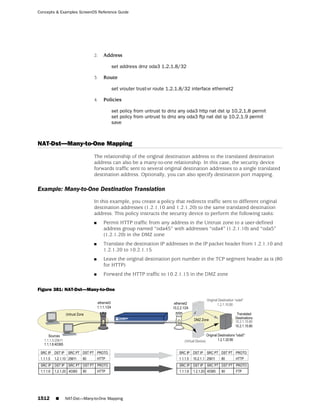
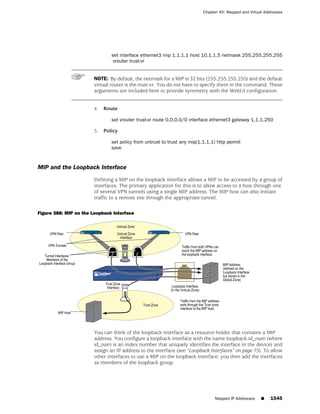
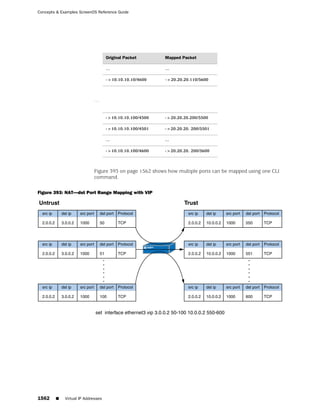
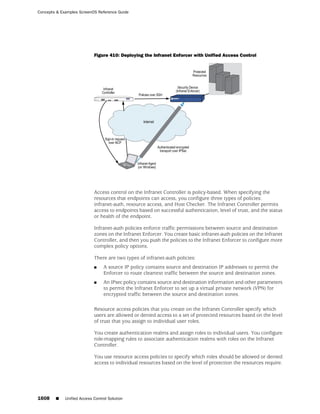
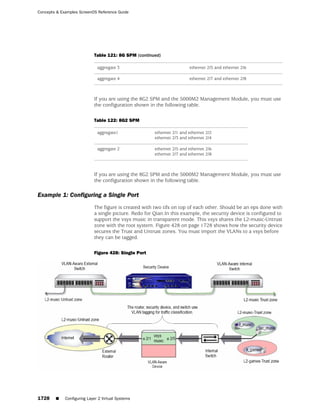
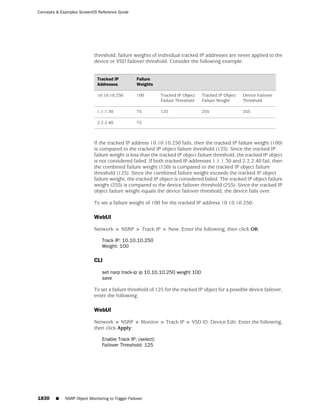
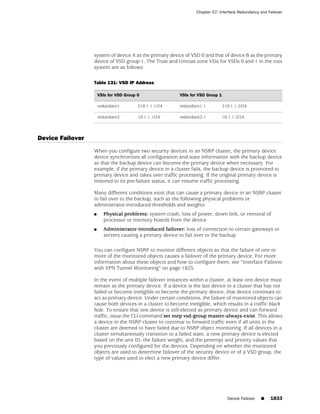
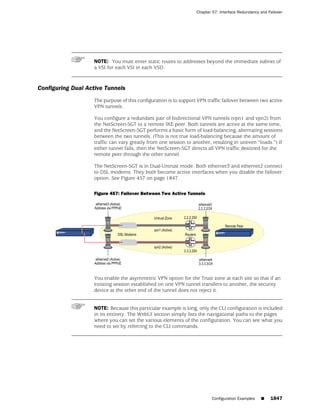
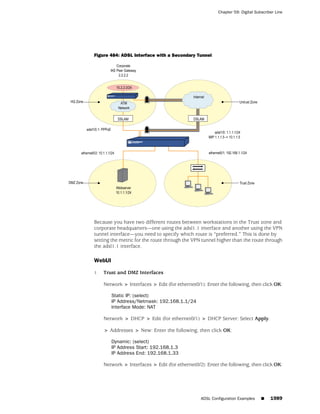
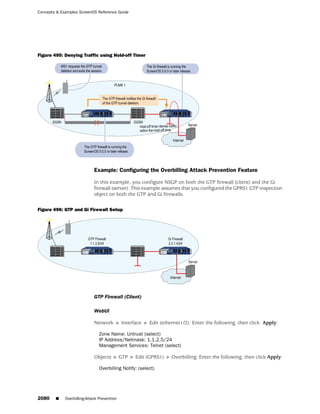
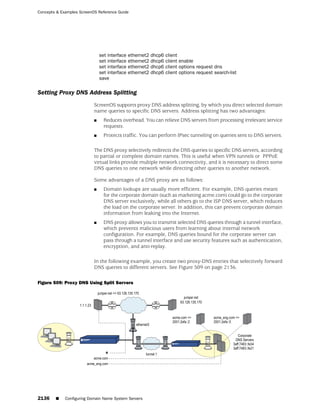
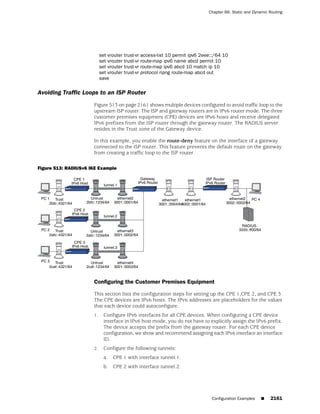
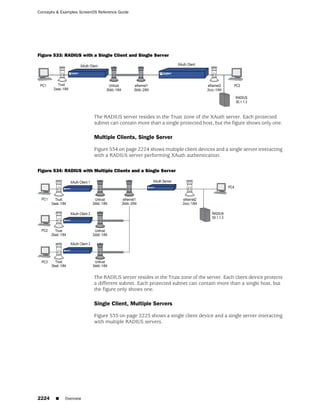
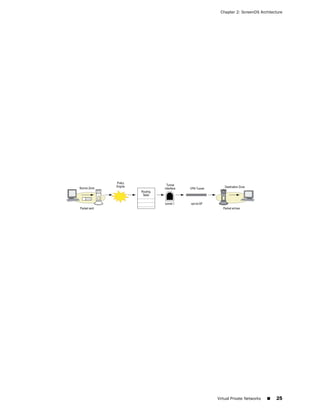
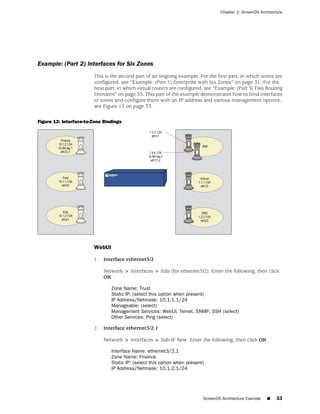
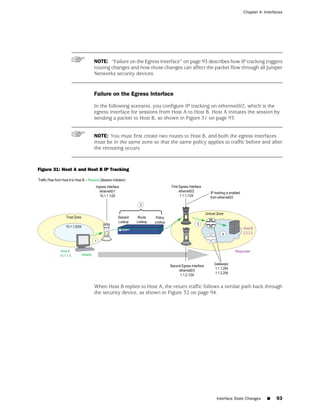
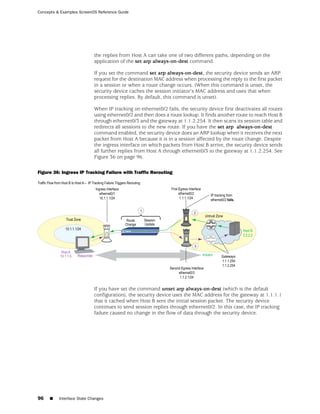
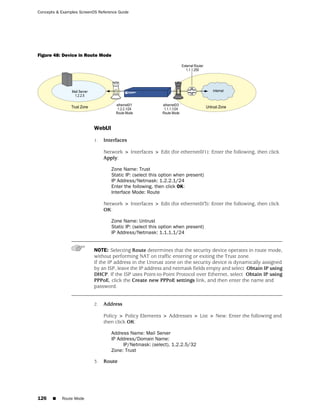
![Concepts & Examples ScreenOS Reference Guide
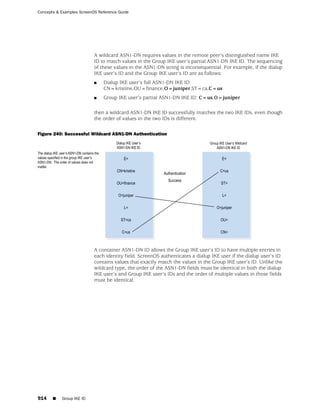
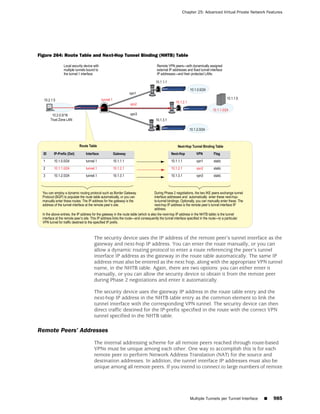
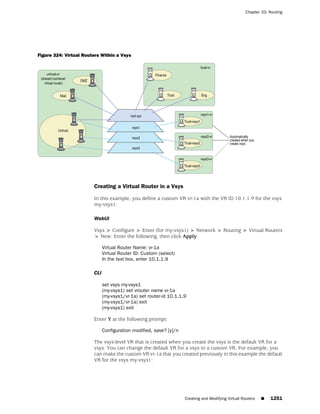
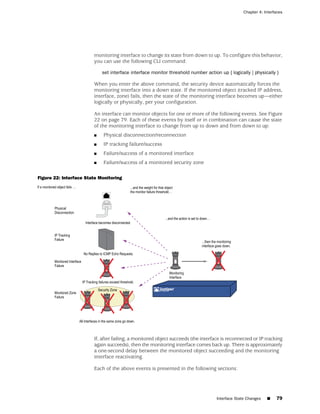
the state of a monitored interface changes from up to down, the following can occur,
as shown in Table 6 on page 86.
Table 6: Monitored Interface
If: Then:
The physical state of an The state change might trigger another interface that is monitoring
interface changes from the one that just went down to also go down. You can specify whether
up to down you want the second interface to be physically or logically down.
The state change of either interface going physically down, or the
combined weight of both going physically down together, might
trigger an NSRP failover. An NSRP device or a VSD group failover can
only occur as a result of a change to the physical state of an interface.
The logical state of an The state change might trigger another interface that is monitoring
interface changes from the one that just went down to also go down. Although the first
up to down as the result interface is down logically, you can specify whether you want the
of an IP tracking failure down state of the second interface to be logical or physical.
Figure 27: Ethernet0/3 and Ethernet0/2 Interface Monitoring
To set interface monitoring, do either of the following:
WebUI
Network > Interfaces > Edit (for the interface you want to do the monitoring) >
Monitor > Edit Interface: Enter the following, then click Apply:
Interface Name: Select the interface that you want to be monitored.
Weight: Enter a weight between 1 and 255.
CLI
set interface interface1 monitor interface interface2 [ weight number ]
save
If you do not set a weight, the security device applies the default value, 255.
86 ■ Interface State Changes](https://image.slidesharecdn.com/630ceall-120330145020-phpapp02/85/ScreenOS-6-1-Concepts-Examples-190-320.jpg)




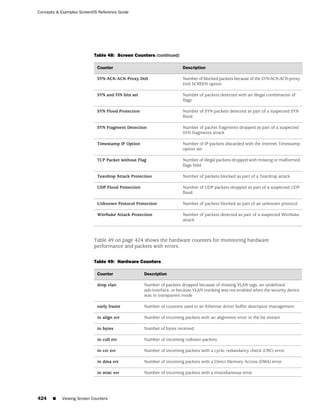
![Concepts & Examples ScreenOS Reference Guide
Weight: Enter a weight between 1 and 255.
CLI
set interface interface monitor zone zone [ weight number ]
If you do not set a weight, the security device applies the default value, 255.
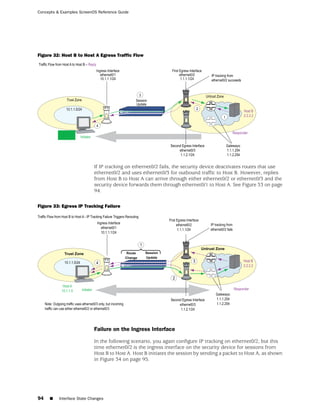
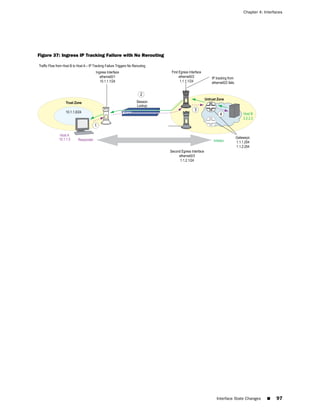
Down Interfaces and Traffic Flow
Configuring IP tracking on an interface allows the security device to reroute outgoing
traffic through a different interface if certain IP addresses become unreachable
through the first interface. However, while the security device might deactivate routes
associated with an interface because of an IP tracking failure, the interface can remain
physically active and still send and receive traffic. For example, the security device
continues to process incoming traffic for an existing session that might arrive on the
original interface on which IP tracking failed. Also, the security device continues to
use the interface to send ping requests to target IP addresses to determine if the
targets again become reachable. In these situations, traffic still passes through an
interface on which IP tracking has failed and for which the security device has
deactivated routes.
How the security device handles session traffic on such an interface depends upon
the following:
■ If the interface on which you configure IP tracking functions as an egress interface
for a session, session replies might continue to arrive at the interface and the
security device still processes them.
■ If the interface on which you configure IP tracking functions as an ingress
interface for a session, applying the set arp always-on-dest command causes
the security device to reroute session replies to another interface. If you do not
set this command, the security device forwards session replies through the
interface on which IP tracking failed even though the security device has
deactivated routes using that interface. (By default, this command is unset.)
By default, a security device caches a session initiator’s MAC address when it
receives the initial packet for a new session. If you enter the CLI command set
arp always-on-dest, the security device does not cache a session initiator’s MAC
address. Instead, the security device performs an ARP lookup when processing
the reply to that initial packet. If the initiator’s MAC address is in the ARP table,
the security device uses that. If the MAC address is not in the ARP table, the
security device sends an ARP request for the destination MAC address and then
adds the MAC address it receives to its ARP table. The security device performs
another ARP lookup whenever a route change occurs.
“Failure on the Egress Interface” on page 93 describes separate scenarios in which
IP tracking fails on the egress interface and on the ingress interface; and, in the case
of the latter, what occurs when you use the command set arp always-on-dest.
92 ■ Interface State Changes](https://image.slidesharecdn.com/630ceall-120330145020-phpapp02/85/ScreenOS-6-1-Concepts-Examples-196-320.jpg)






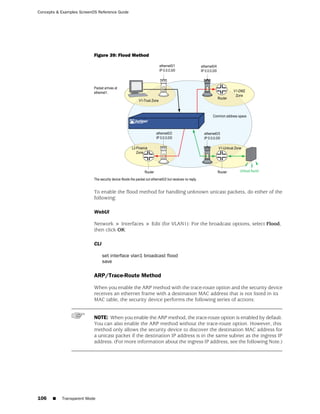

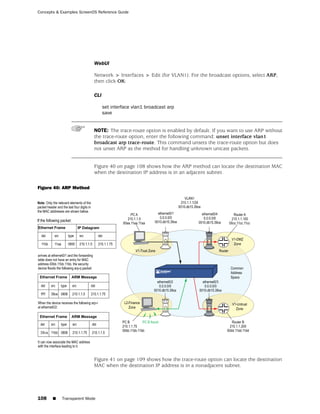
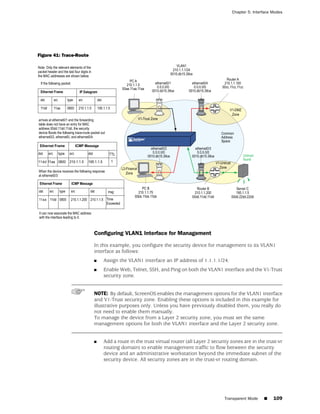

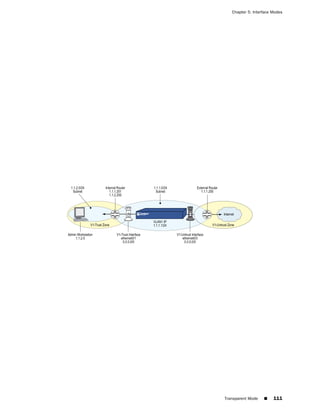
















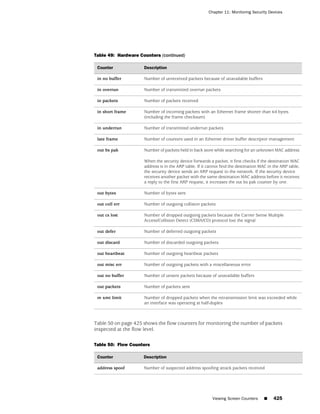
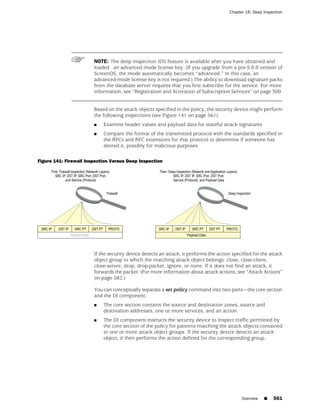
![Chapter 6: Building Blocks for Policies
■ Policy > Policy Elements > Services > Predefined
■ Policy > Policy Elements > Services > Custom
■ Policy > Policy Elements > Services > Groups
■ Using the CLI:
get service [ group | predefined | user ]
NOTE: Each predefined service has a source port range of 1-65535, which includes
the entire set of valid port numbers. This prevents potential attackers from gaining
access by using a source port outside of the range. If you need to use a different
source port range for any predefined service, create a custom service. For information,
see “Custom Services” on page 149.
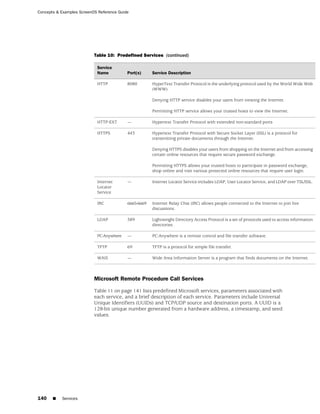
This section contains information about the following predefined services:
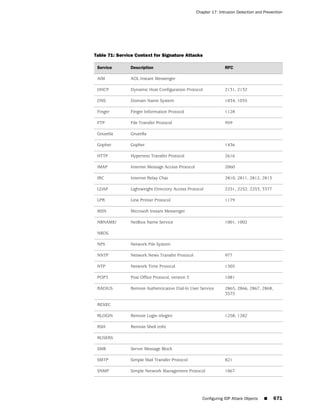
■ Internet Control Messaging Protocol on page 136
■ Internet-Related Predefined Services on page 139
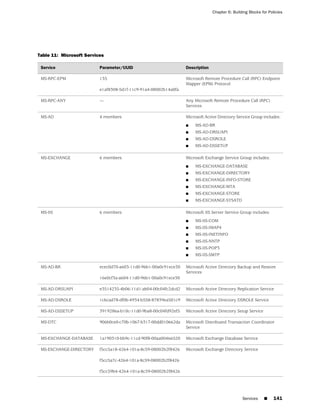
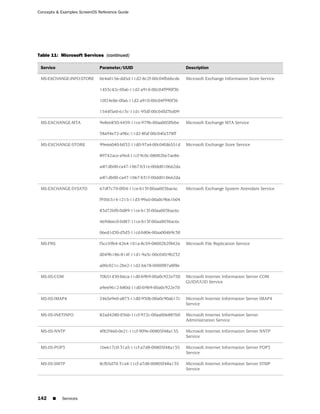
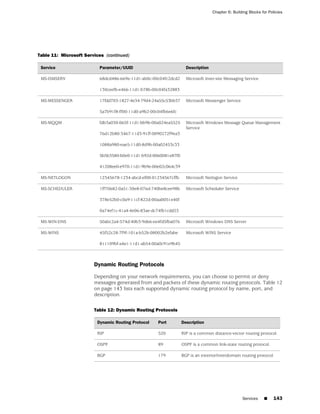
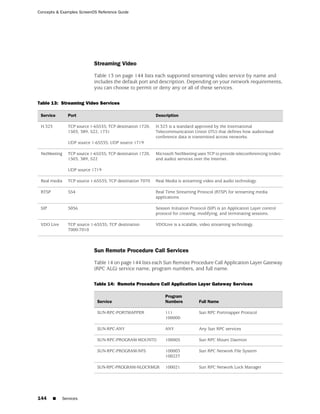
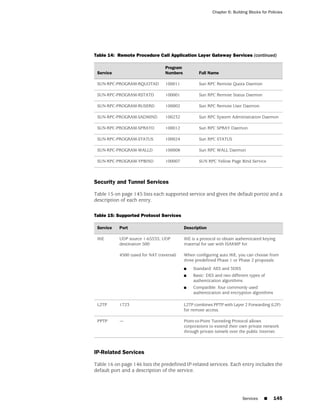
■ Microsoft Remote Procedure Call Services on page 140
■ Dynamic Routing Protocols on page 143
■ Streaming Video on page 144
■ Sun Remote Procedure Call Services on page 144
■ Security and Tunnel Services on page 145
■ IP-Related Services on page 145
■ Instant Messaging Services on page 146
■ Management Services on page 146
■ Mail Services on page 147
■ UNIX Services on page 148
■ Miscellaneous Services on page 148
You can find more detailed information about some of these listed on the following
pages:
■ Defining a Custom Internet Control Message Protocol Service on page 154
■ Remote Shell Application Layer Gateway on page 155
■ Sun Remote Procedure Call Application Layer Gateway on page 155
■ Customizing Microsoft Remote Procedure Call Application Layer Gateway on
page 157
■ Real-Time Streaming Protocol Application Layer Gateway on page 158
■ Stream Control Transmission Protocol Application Layer Gateway on page 171
■ Point-to-Point Tunneling Protocol Application Layer Gateway on page 172
Services ■ 135](https://image.slidesharecdn.com/630ceall-120330145020-phpapp02/85/ScreenOS-6-1-Concepts-Examples-239-320.jpg)