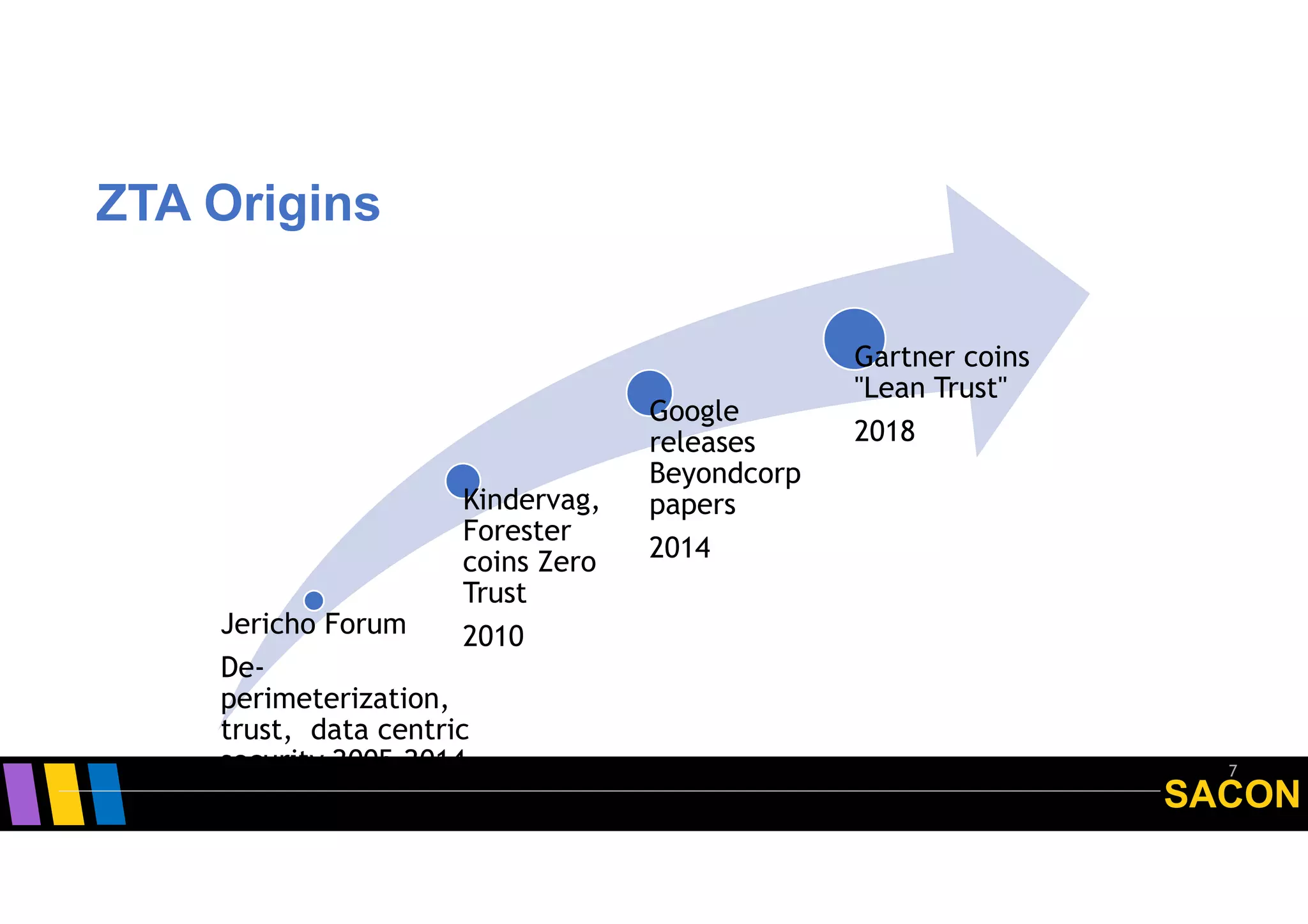
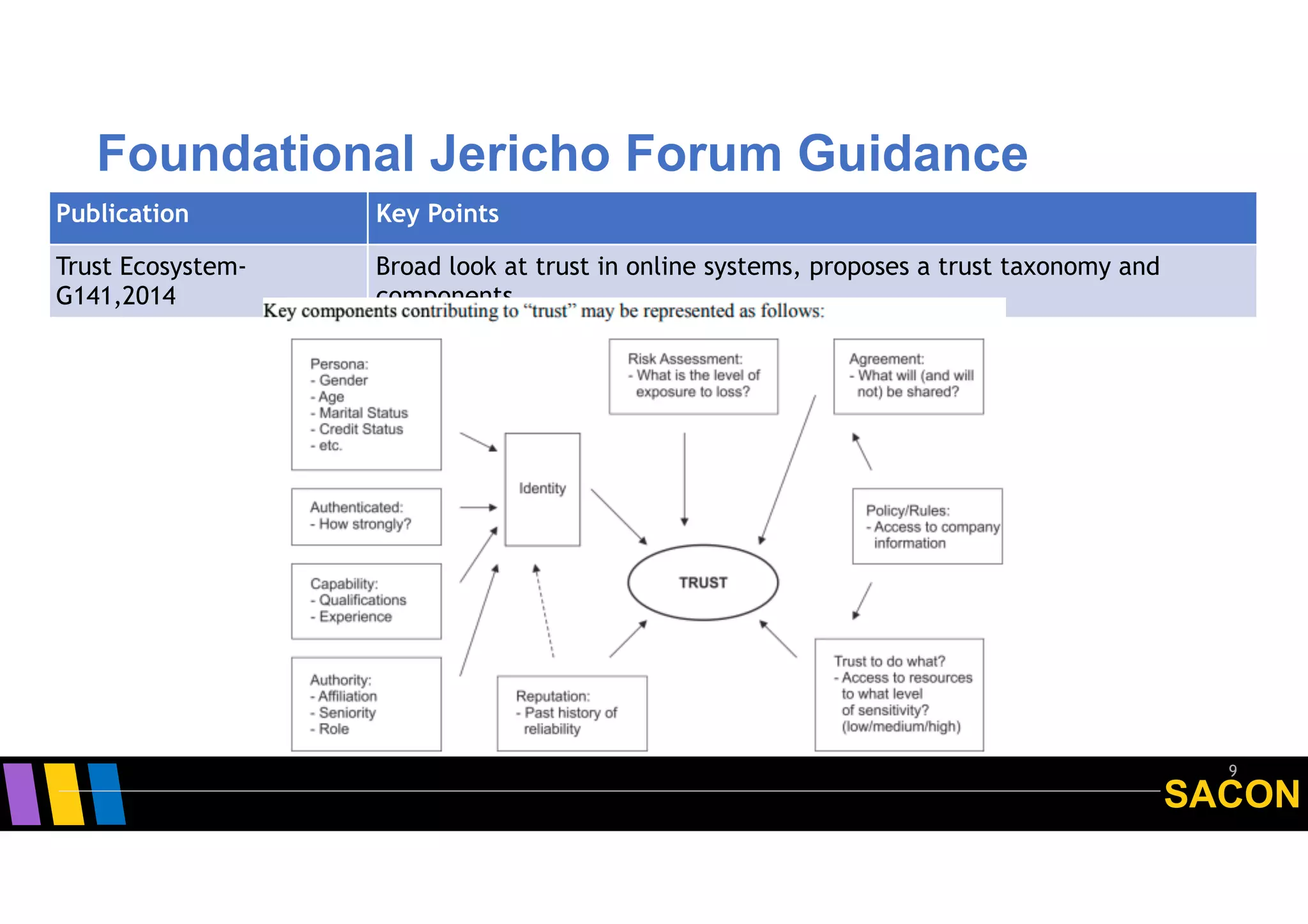
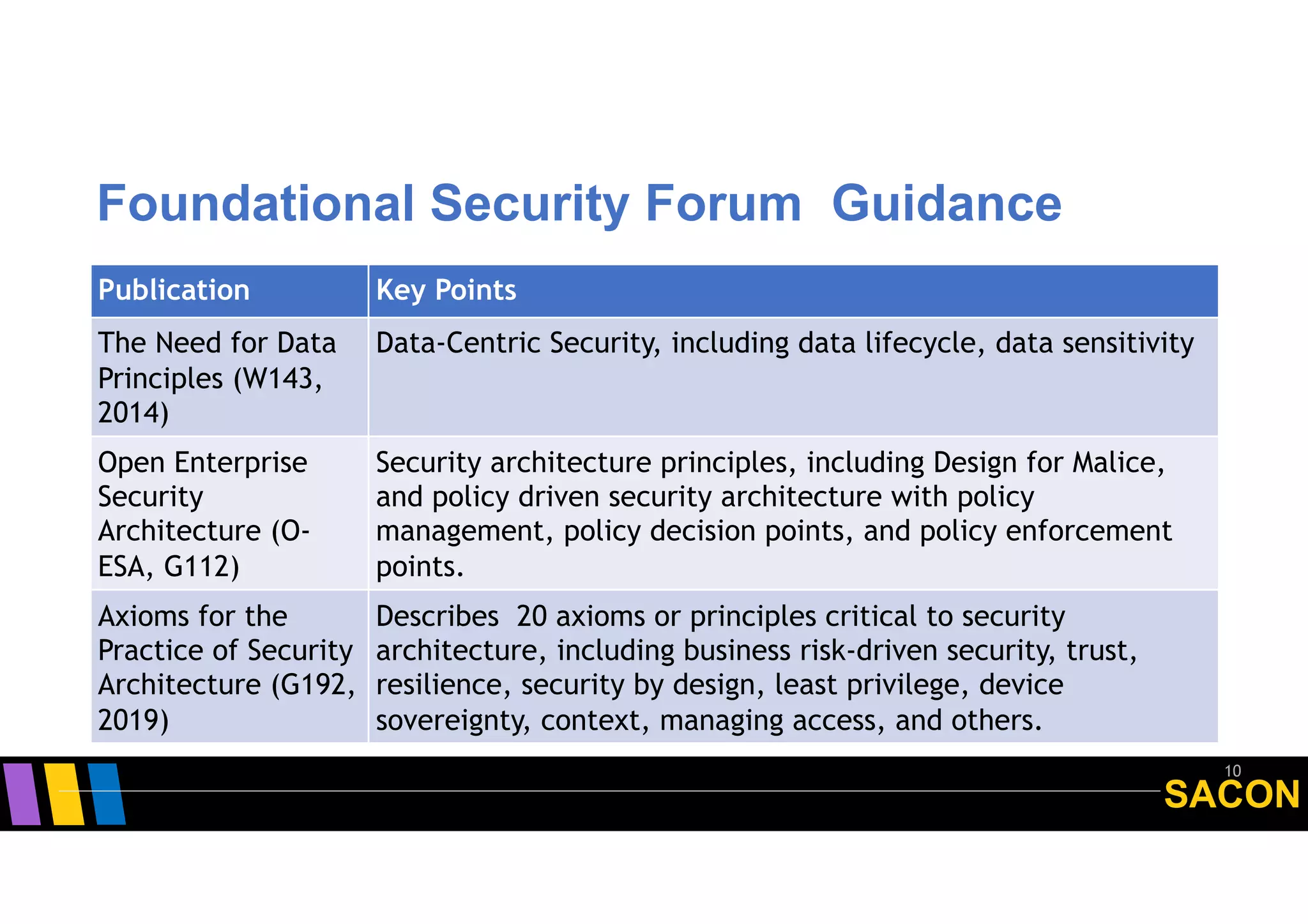
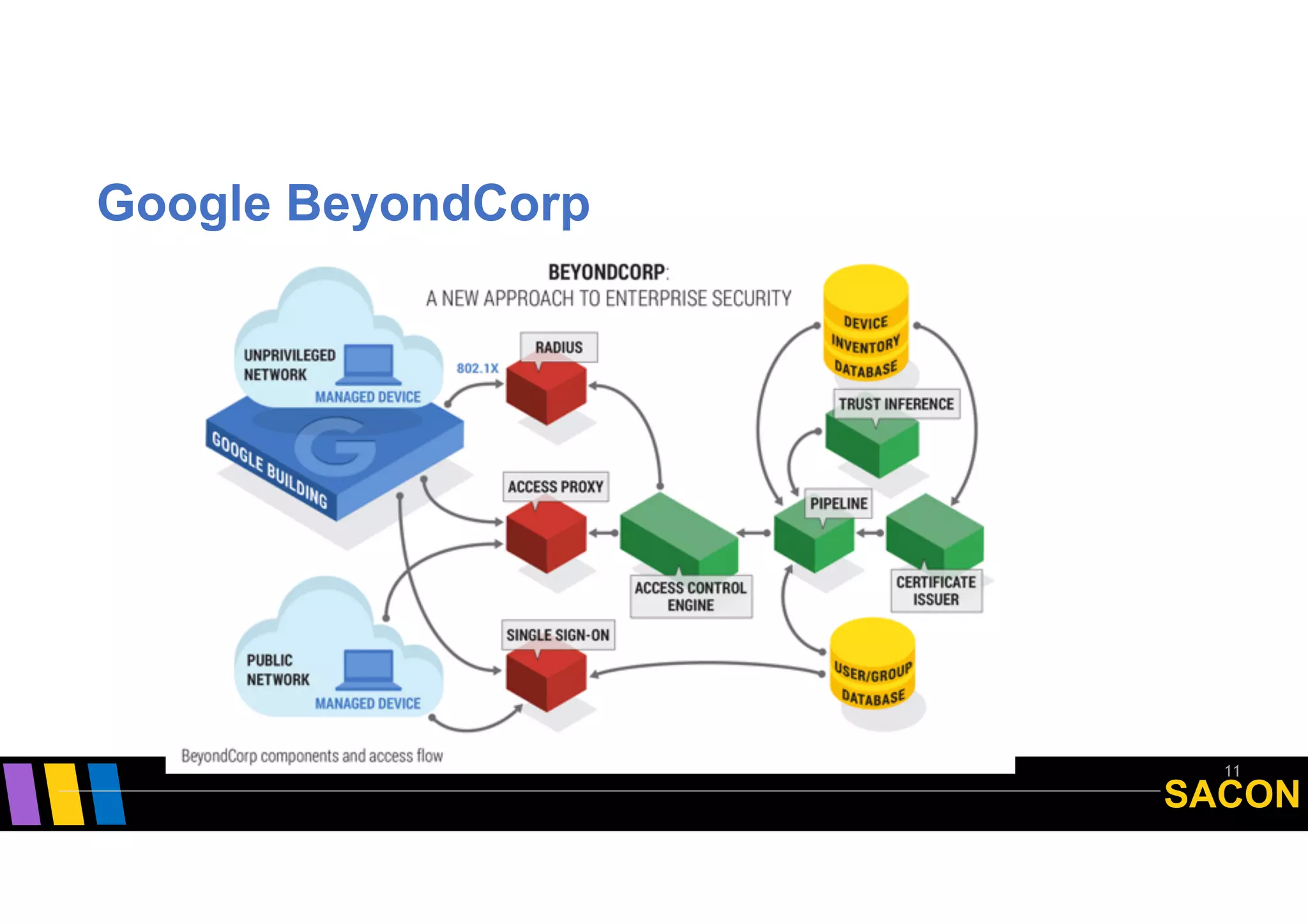
The document discusses the origins and principles of Zero Trust Architecture (ZTA), emphasizing the need to eliminate traditional perimeter security due to its limitations in modern computing environments. It highlights ZTA's guiding principles such as explicit verification, least privileged access, and dynamic user authentication, proposing a proactive approach to security as opposed to reactive measures. Additionally, it addresses the challenges and opportunities in standardizing ZTA and encourages engagement with the Open Group's initiatives for developing security standards.


![SACON
!3
Full de-perimeterised working
Full Internet-based Collaboration
Consumerisation
[Cheap IP based devices]
Limited Internet-based Collaboration
External Working
VPN based
External collaboration
[Private connections]
Internet Connectivity
Web, e-Mail, Telnet, FTP
Connectivity for
Internet e-Mail
Connected LANs
interoperating protocols
Local Area Networks
Islands by technology
Stand-alone Computing
[Mainframe, Mini, PC’s]
Time
Connectivity
Drivers: Low cost and
feature rich devices
Drivers: B2B & B2C integration,
flexibility, M&A
Drivers: Cost, flexibility,
faster working
Today
(2008)
Drivers: Outsourcing and
off-shoring
Effective breakdown of
perimeter
Zero Trust Origins…De-perimeterization Timeline](https://image.slidesharecdn.com/hietalasaconztafeb2020final-200226072511/75/SACON-Jim-Hietala-Zero-Trust-Architecture-From-Hype-to-Reality-3-2048.jpg)