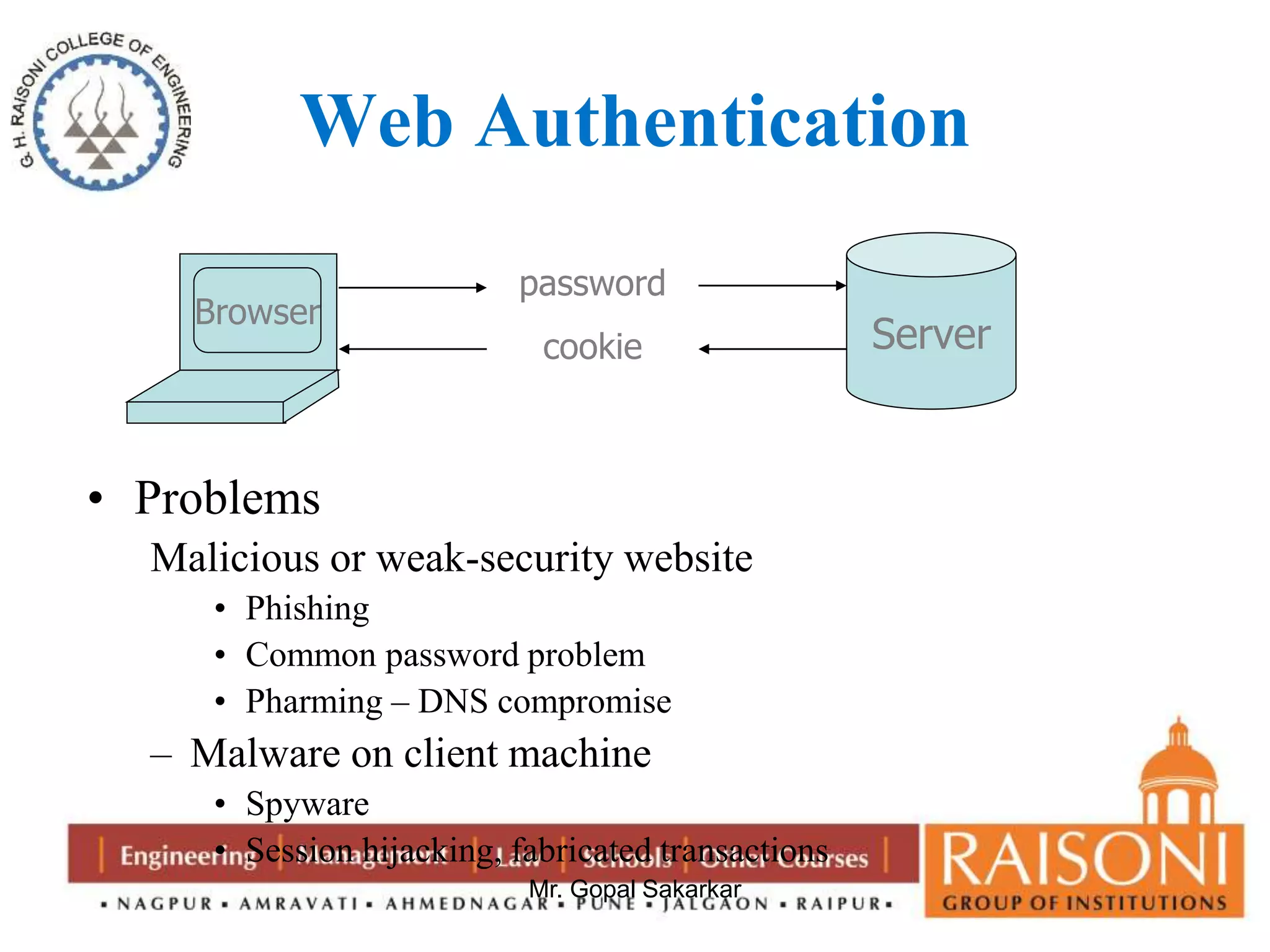
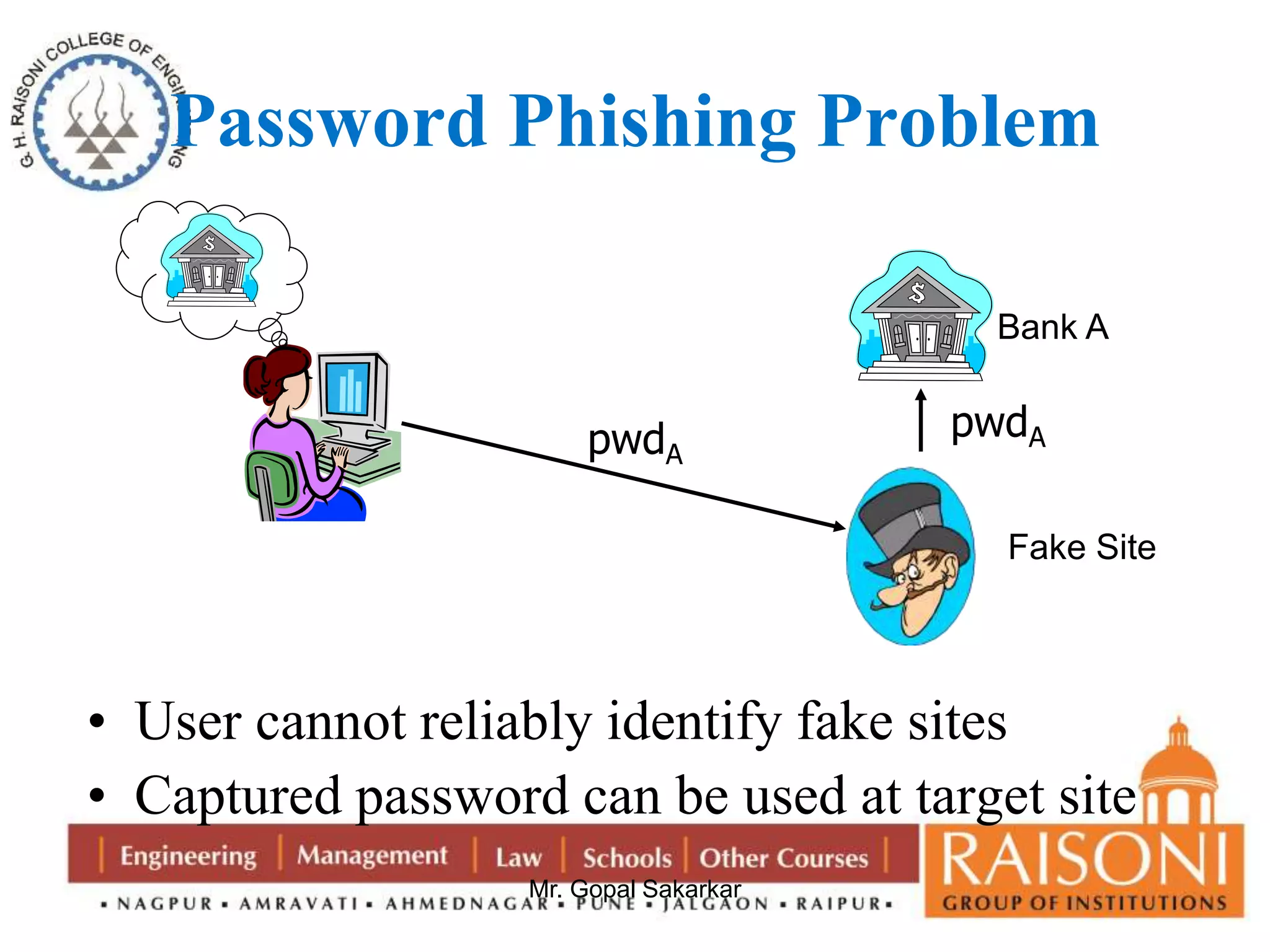
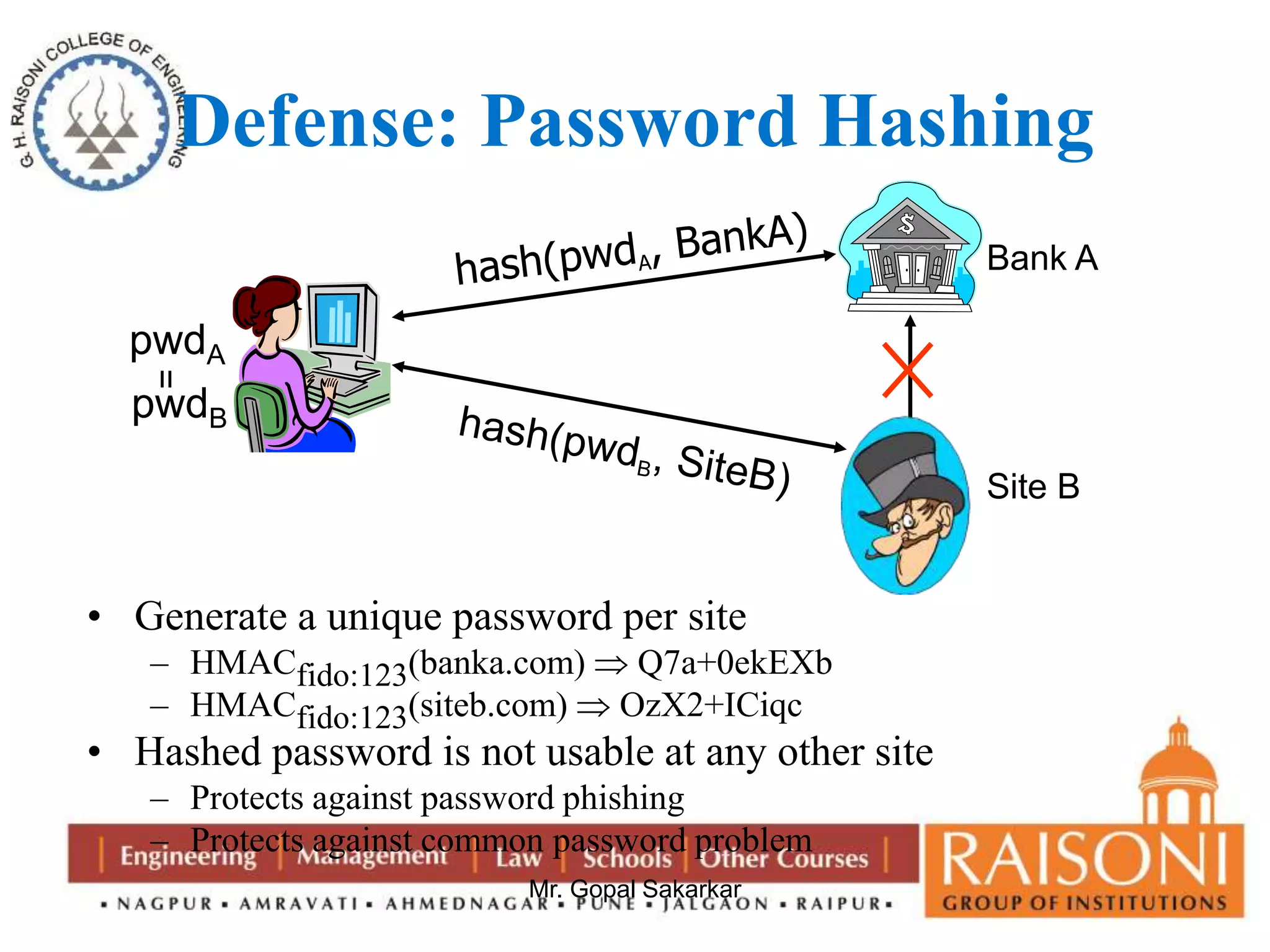
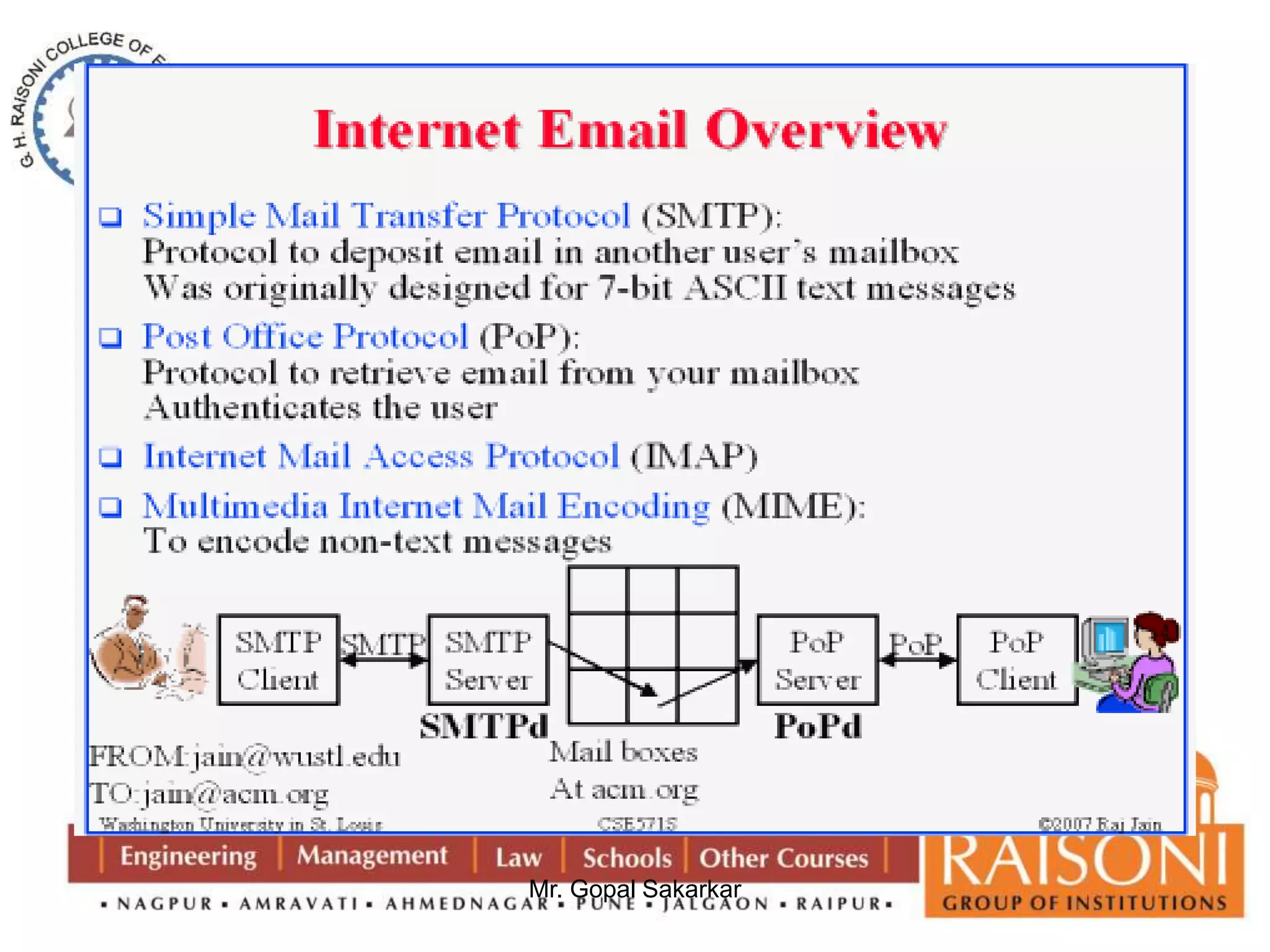
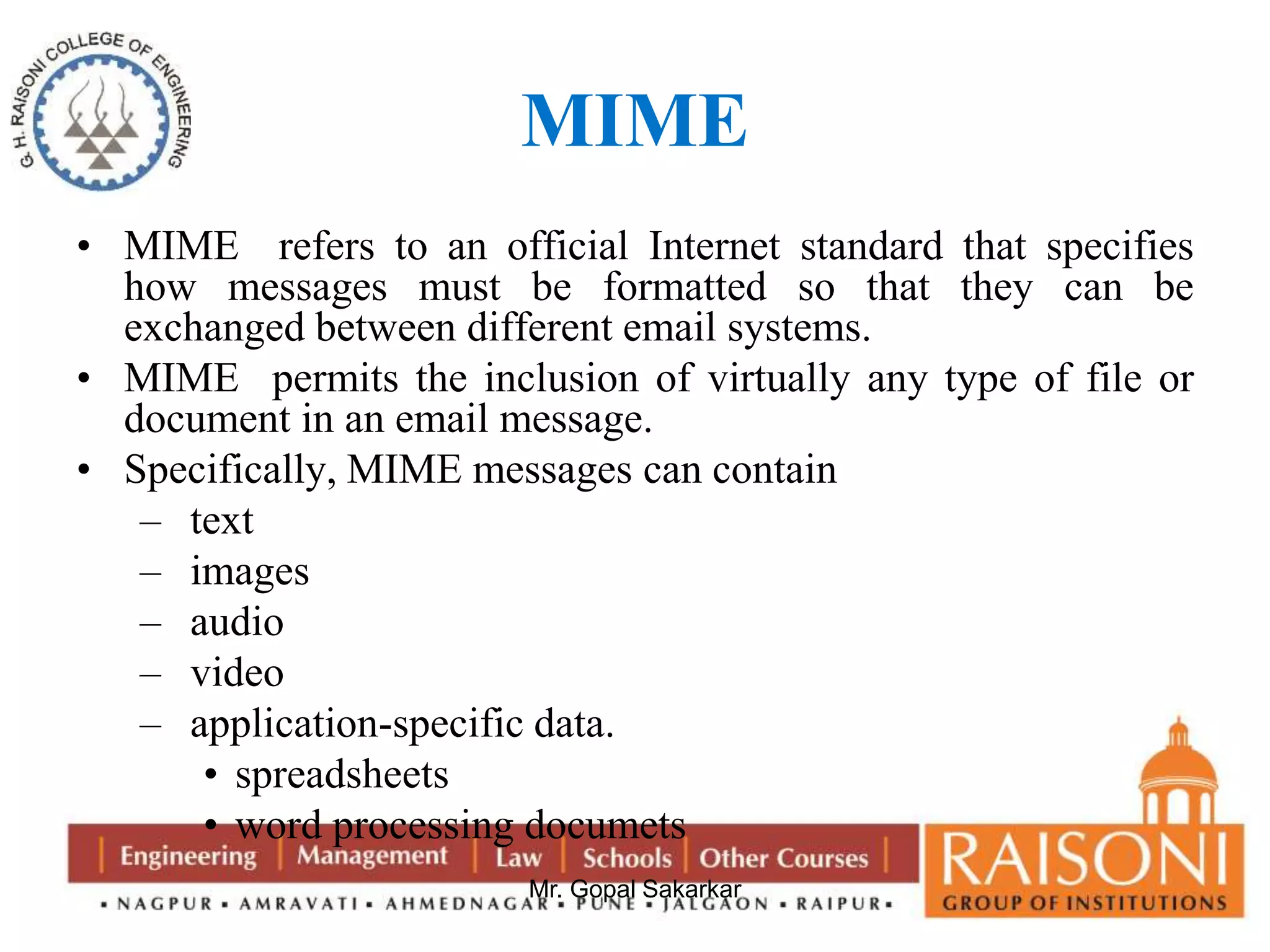
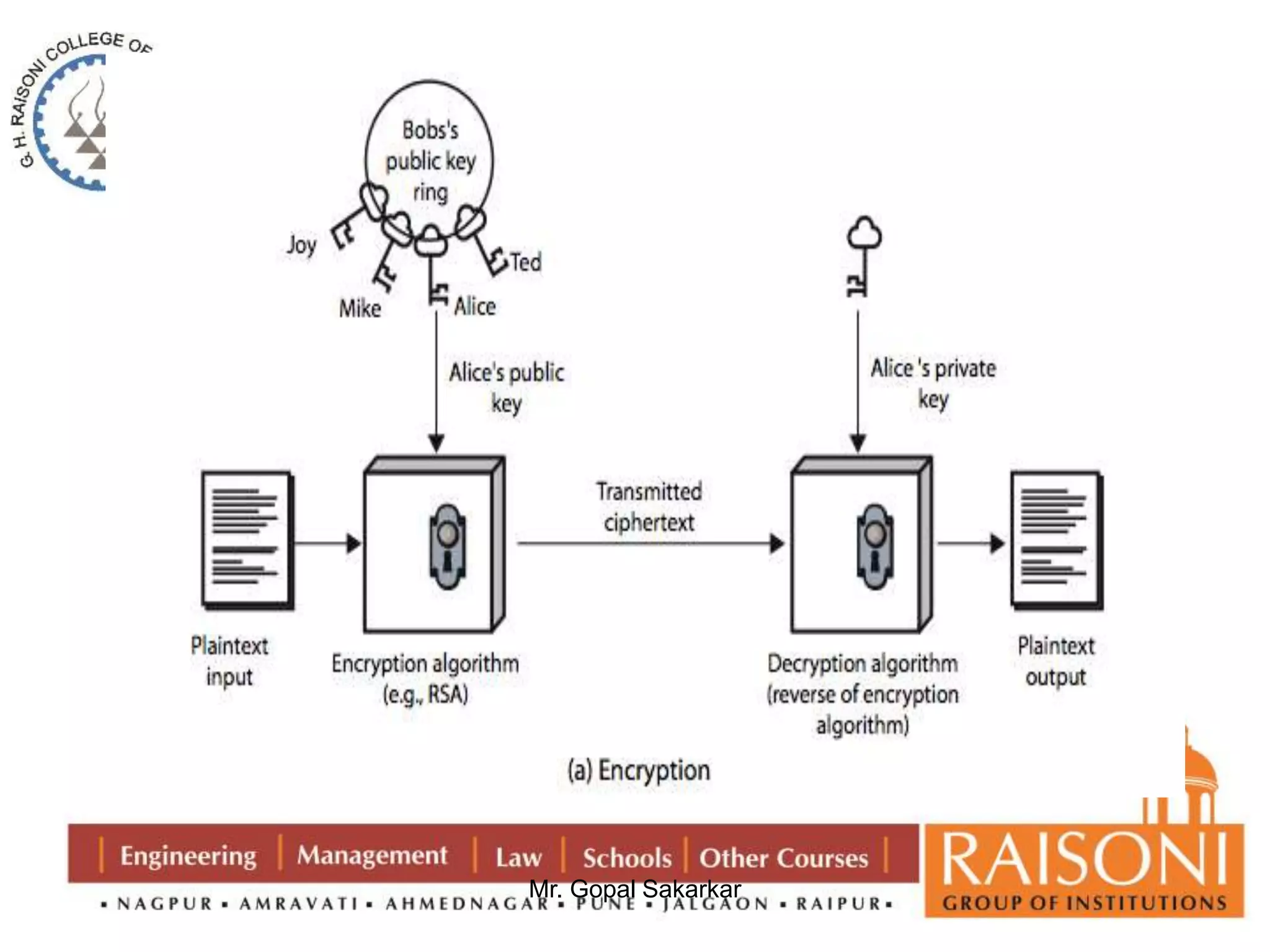
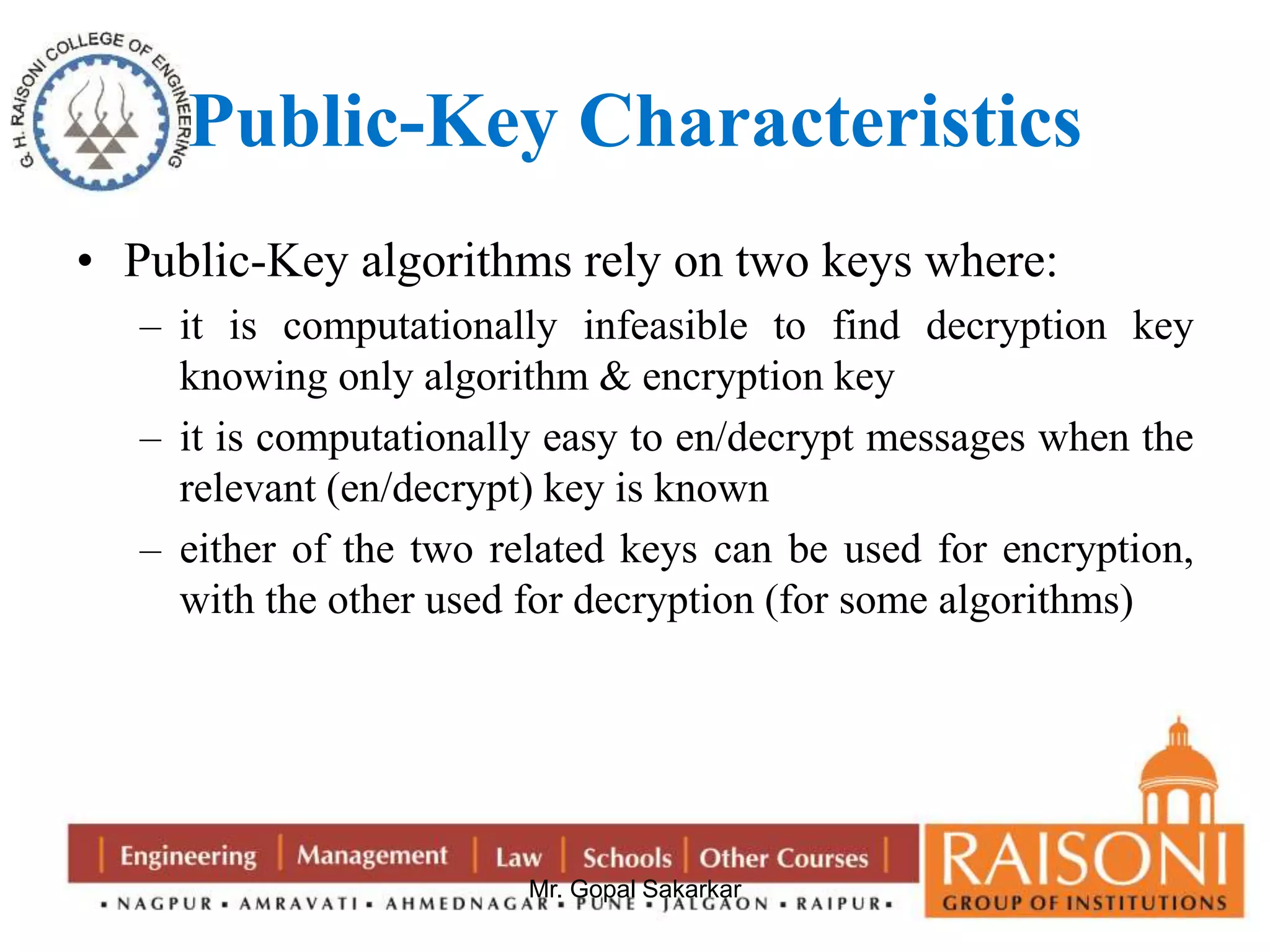
Public key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts messages. It has six components: plain text, encryption algorithm, public and private keys, ciphertext, and decryption algorithm. Some key characteristics are that it is computationally infeasible to determine the private key from the public key alone, and encryption/decryption is easy when the relevant key is known. The requirements of public key cryptography are that it is easy to generate a public-private key pair, easy to encrypt with the public key, easy for the recipient to decrypt with the private key, and infeasible to determine the private key from the public key or recover the plaintext from the ciphertext and public key alone


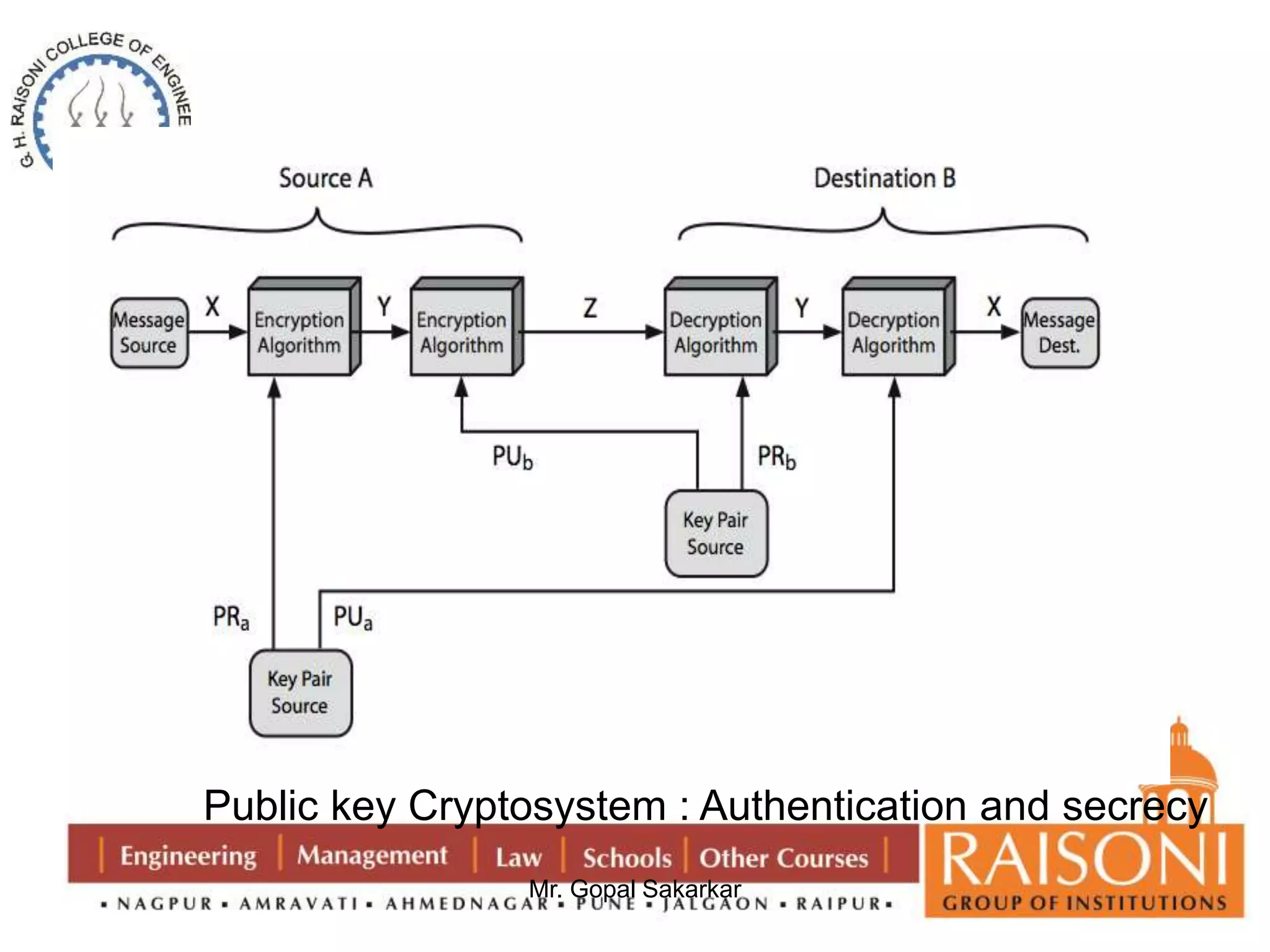
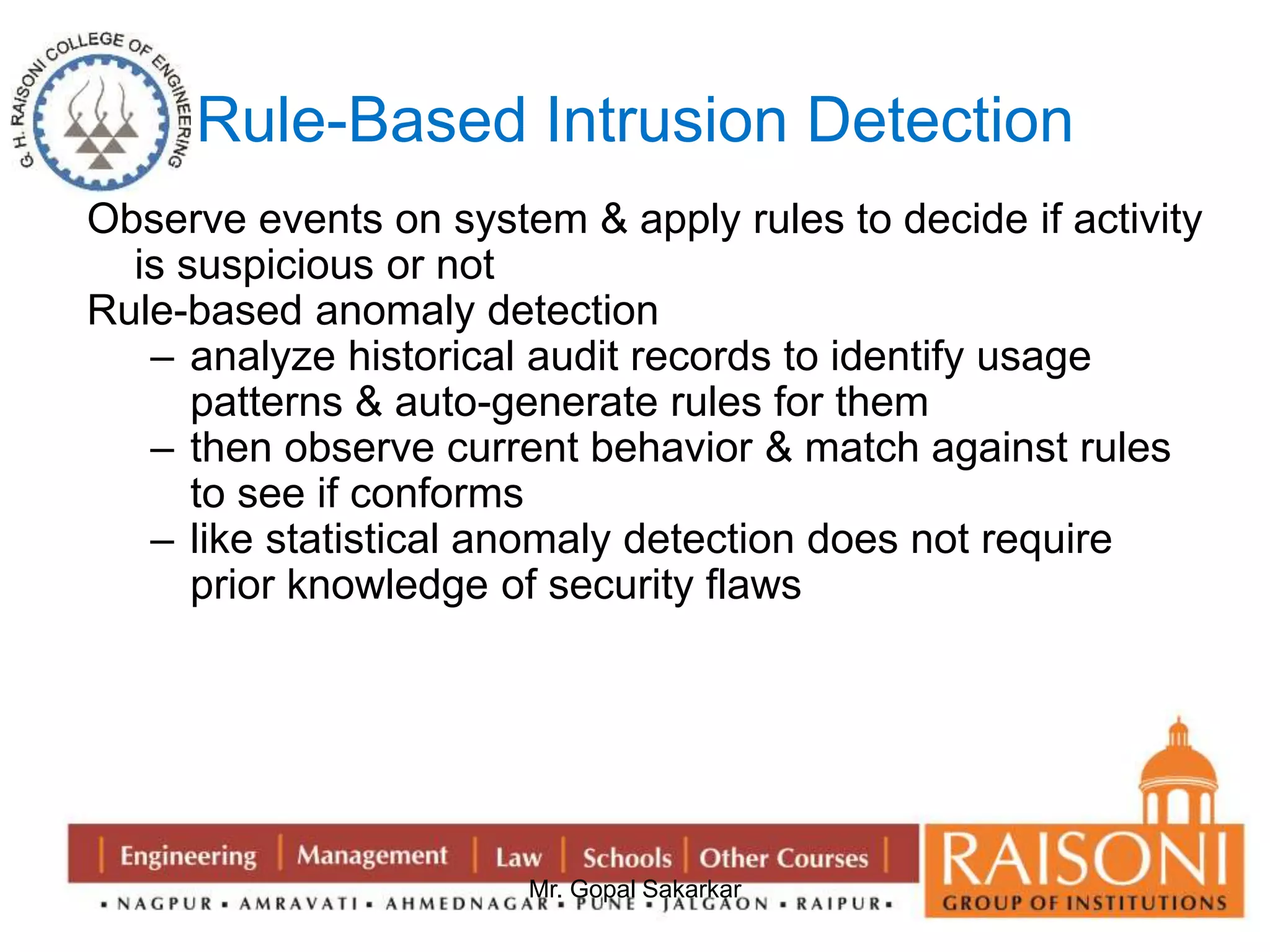
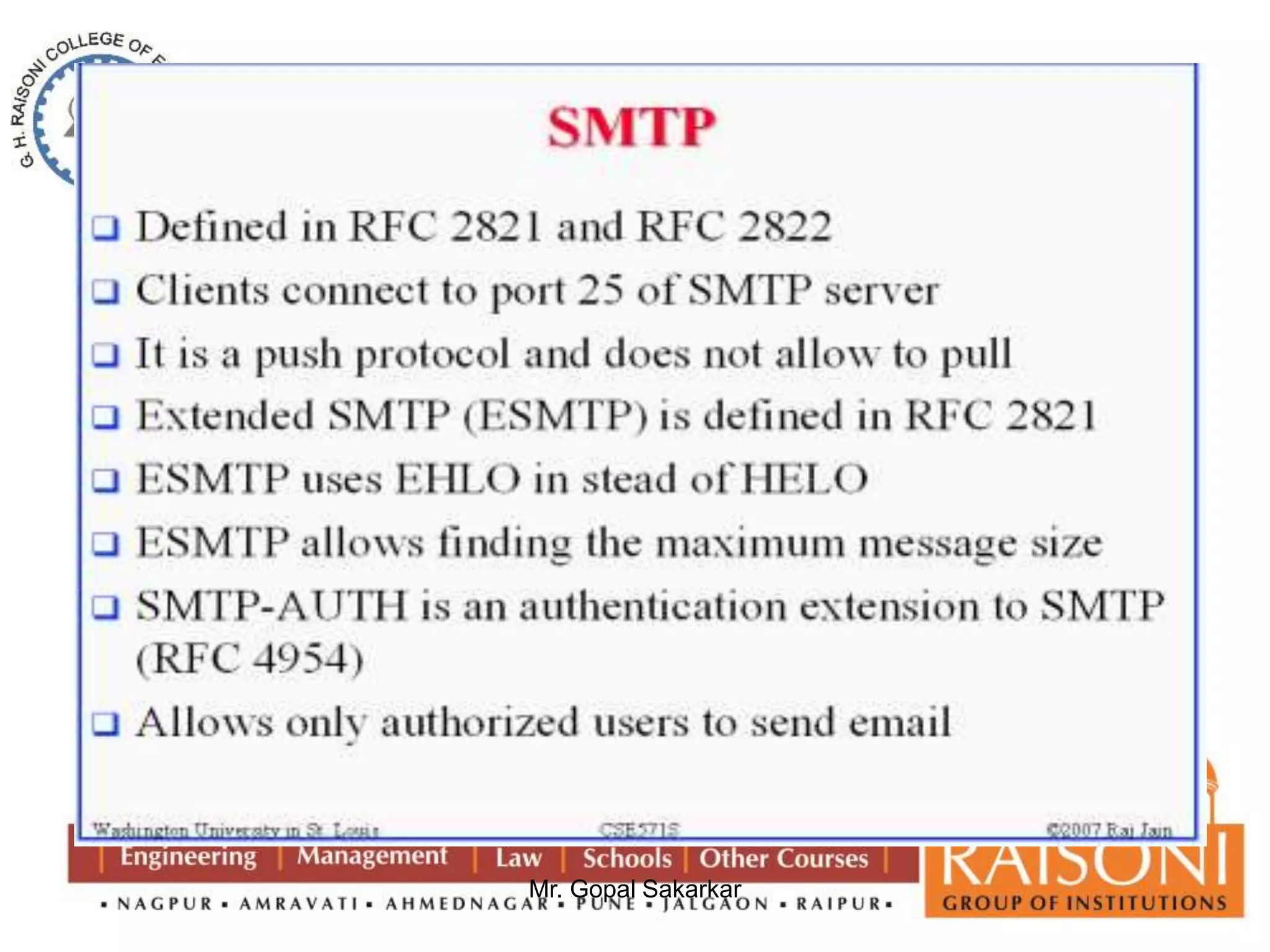
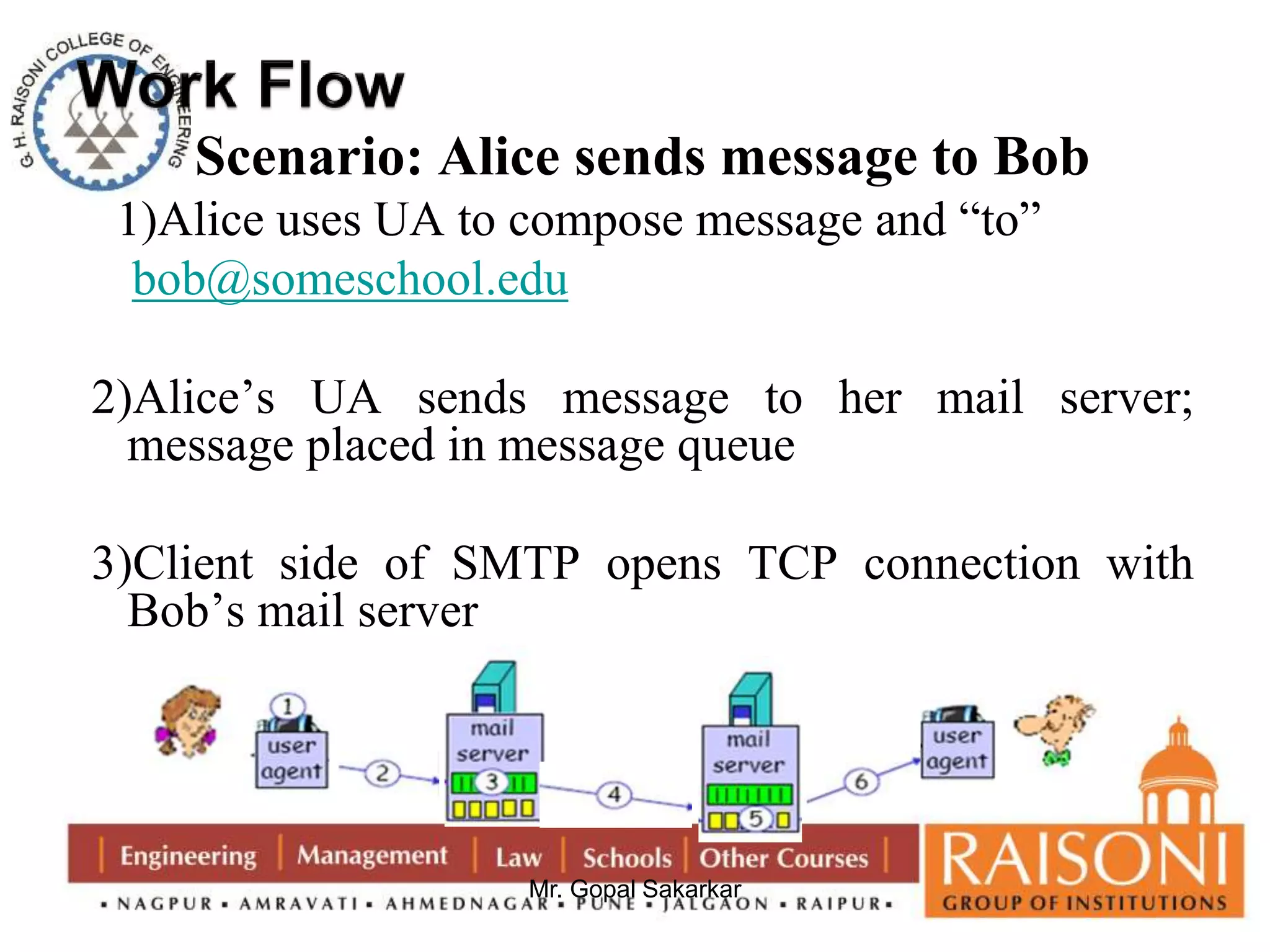
![Requirement of Public key Cryptography
1. It is easy for party B to generate a pair of keys (public key PUb ,
Mr. Gopal Sakarkar
Private key PRb).
2. It is easy for a sender A , knowing the public key and message to
be encrypt. C=E(PUb, M)
3. It is easy for receiver B to decrypt the resulting ciphertext using
the private key . M=D(PRb,C)=D[PRb,E(PUb,M)]
4. It is infeasible for an any person , to know the public key PUb to
determine the private key PRb.
5. It is infeasible for any person to know the public key PUb and a
ciphertext C to recover the original message M.
6. Two keys can be applied in either order
M=DP[PUb, E(PRb,M)] = D[PRb,E(PUb, M)]](https://image.slidesharecdn.com/ns-140920073509-phpapp02/75/Public-Key-Cryptography-6-2048.jpg)











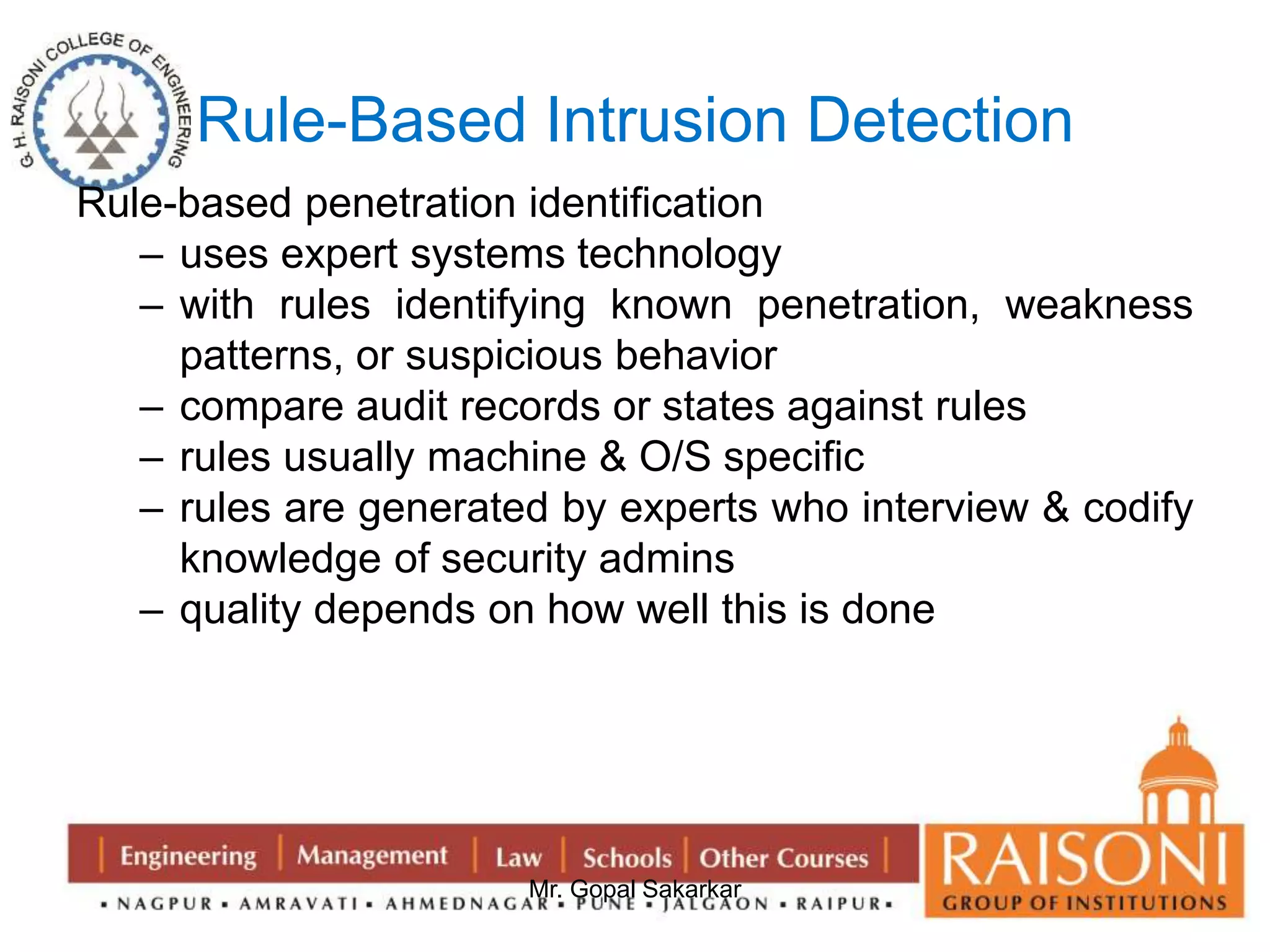
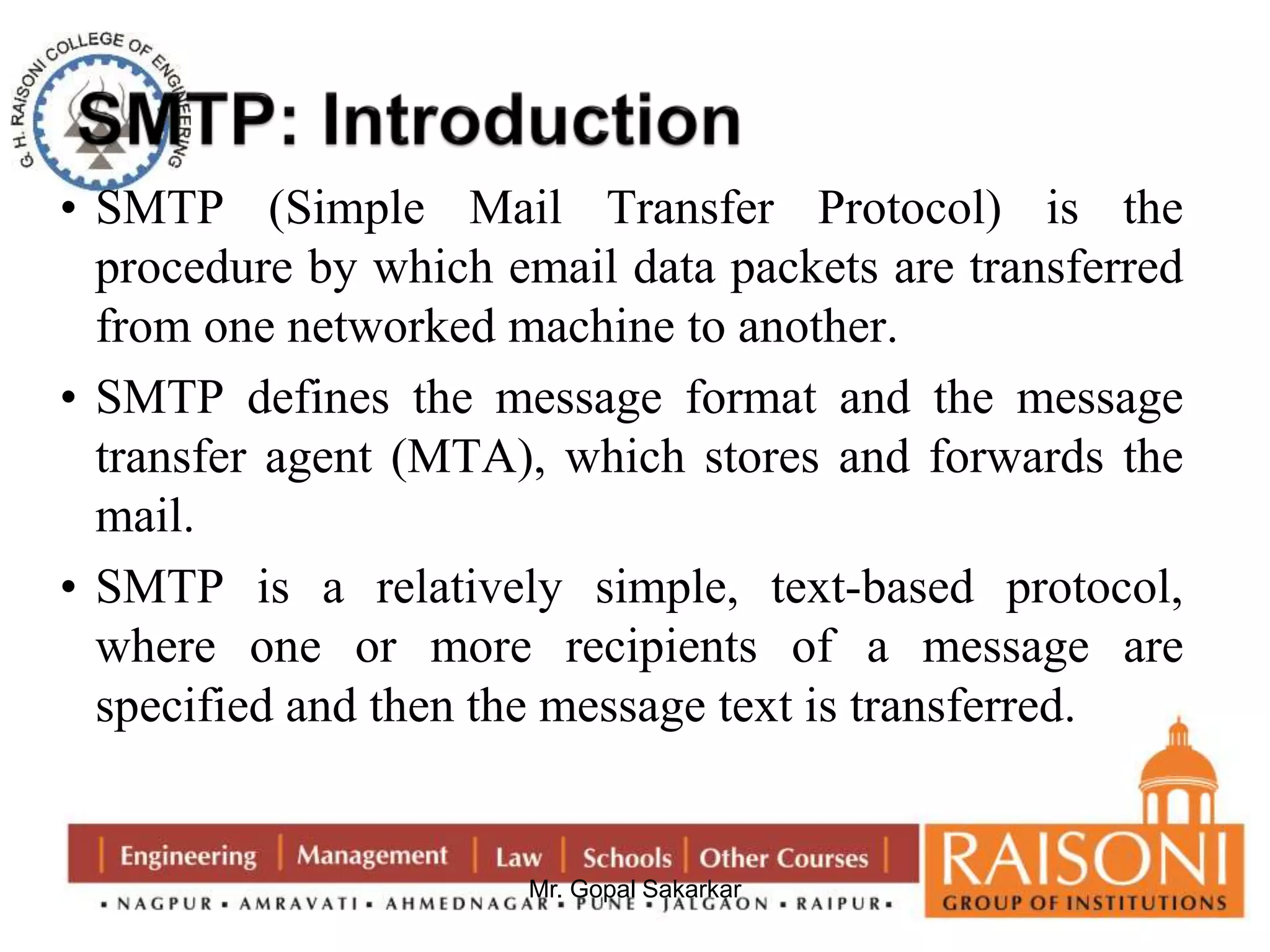
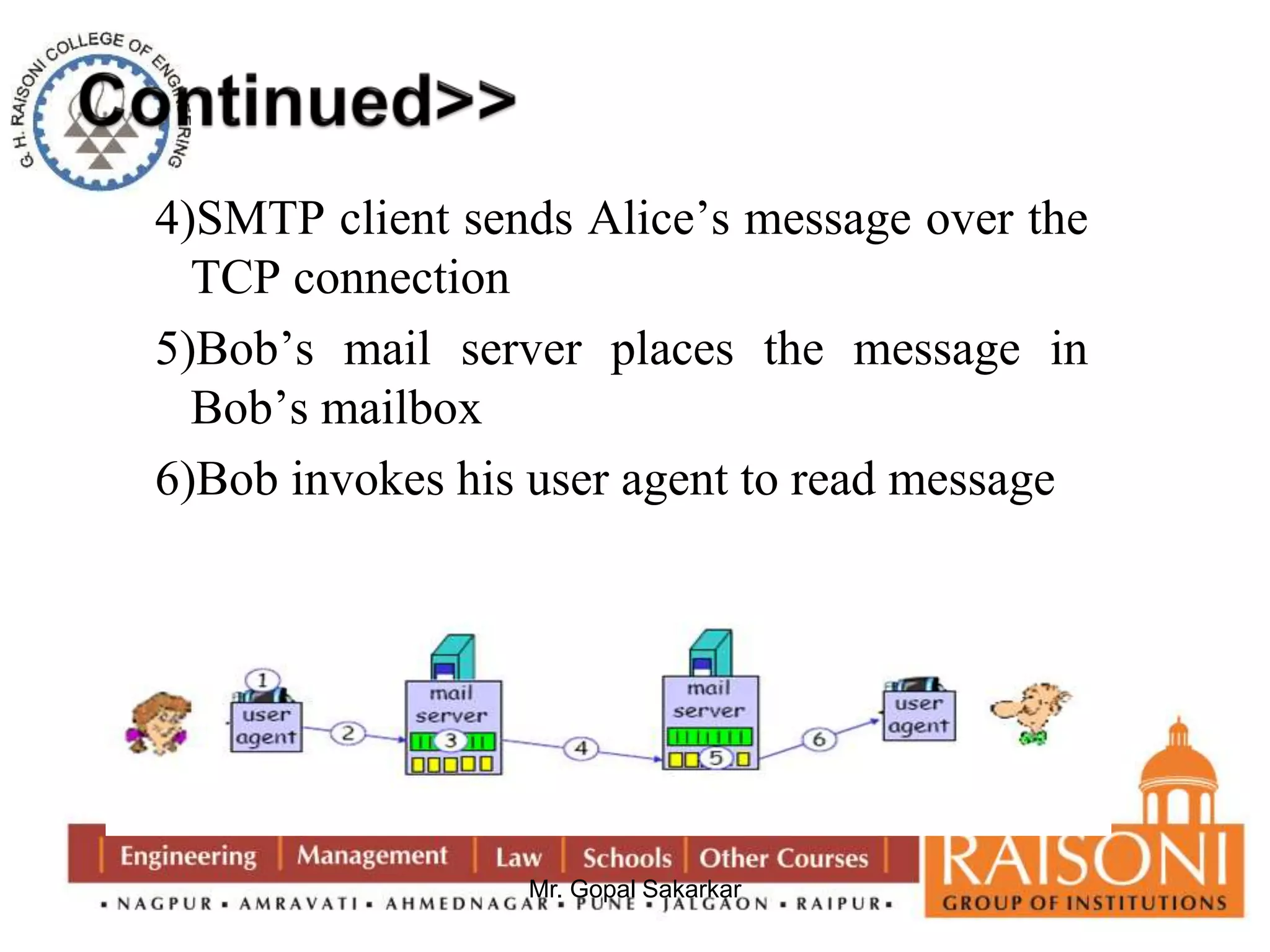
![DSA Signature Creation
to sign a message M the sender:
– generates a random signature key k, k<q
– k must be random, be destroyed after use,
and never be reused
Mr. Gopal Sakarkar
then computes signature pair:
r = (gk mod p)mod q
s = [k-1(H(M)+ xr)] mod q
sends signature (r,s) with message M](https://image.slidesharecdn.com/ns-140920073509-phpapp02/75/Public-Key-Cryptography-35-2048.jpg)
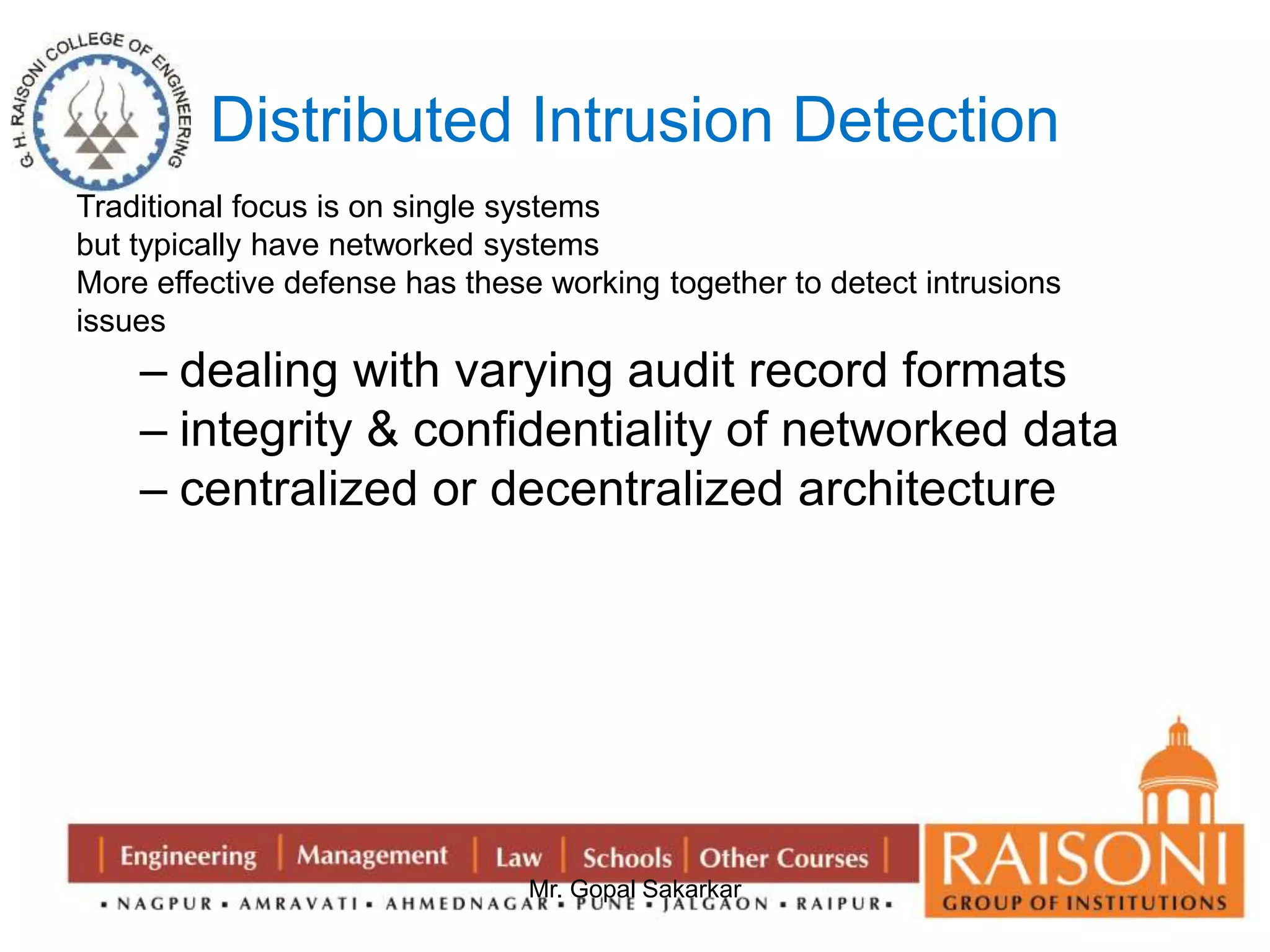
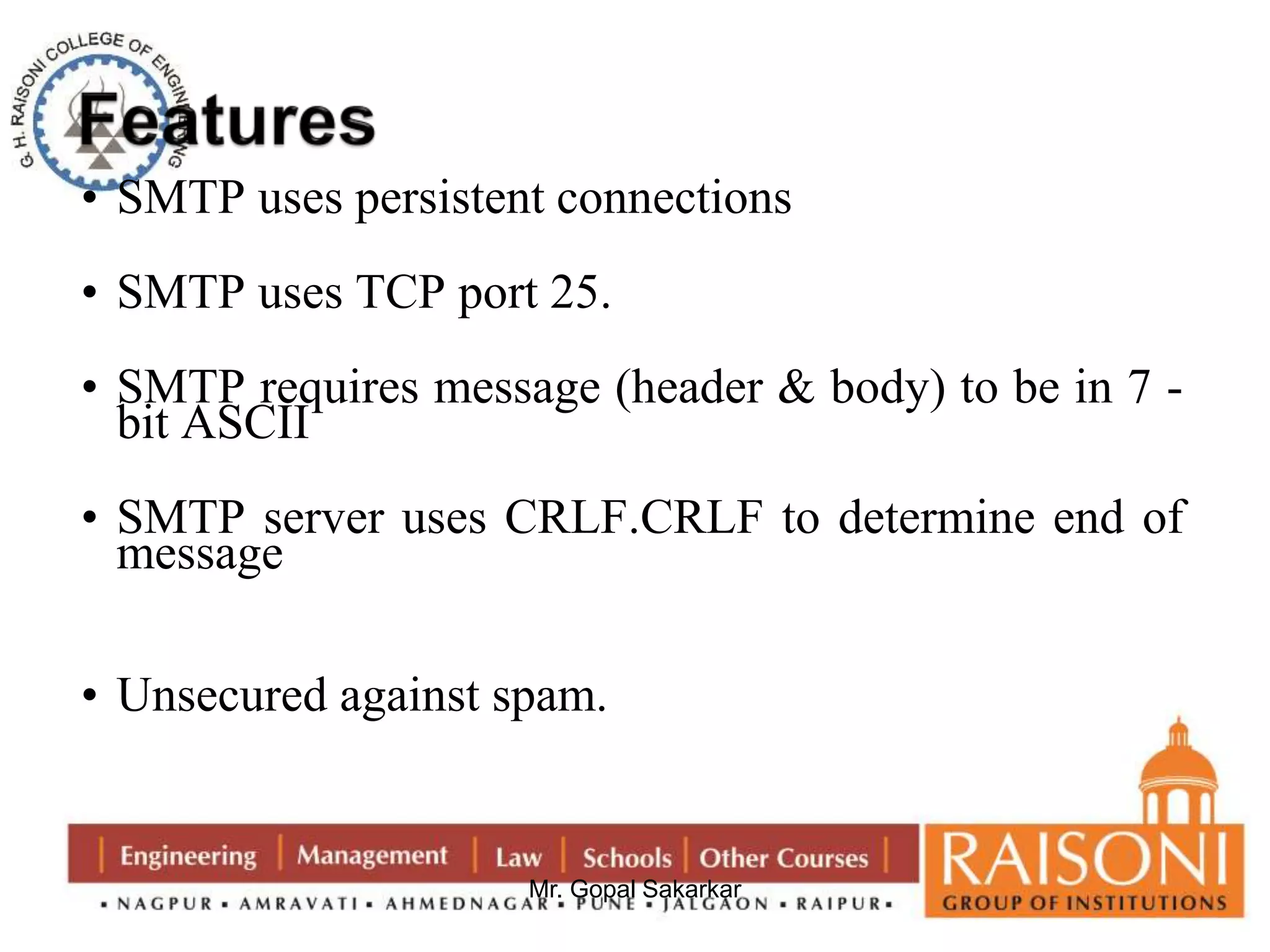
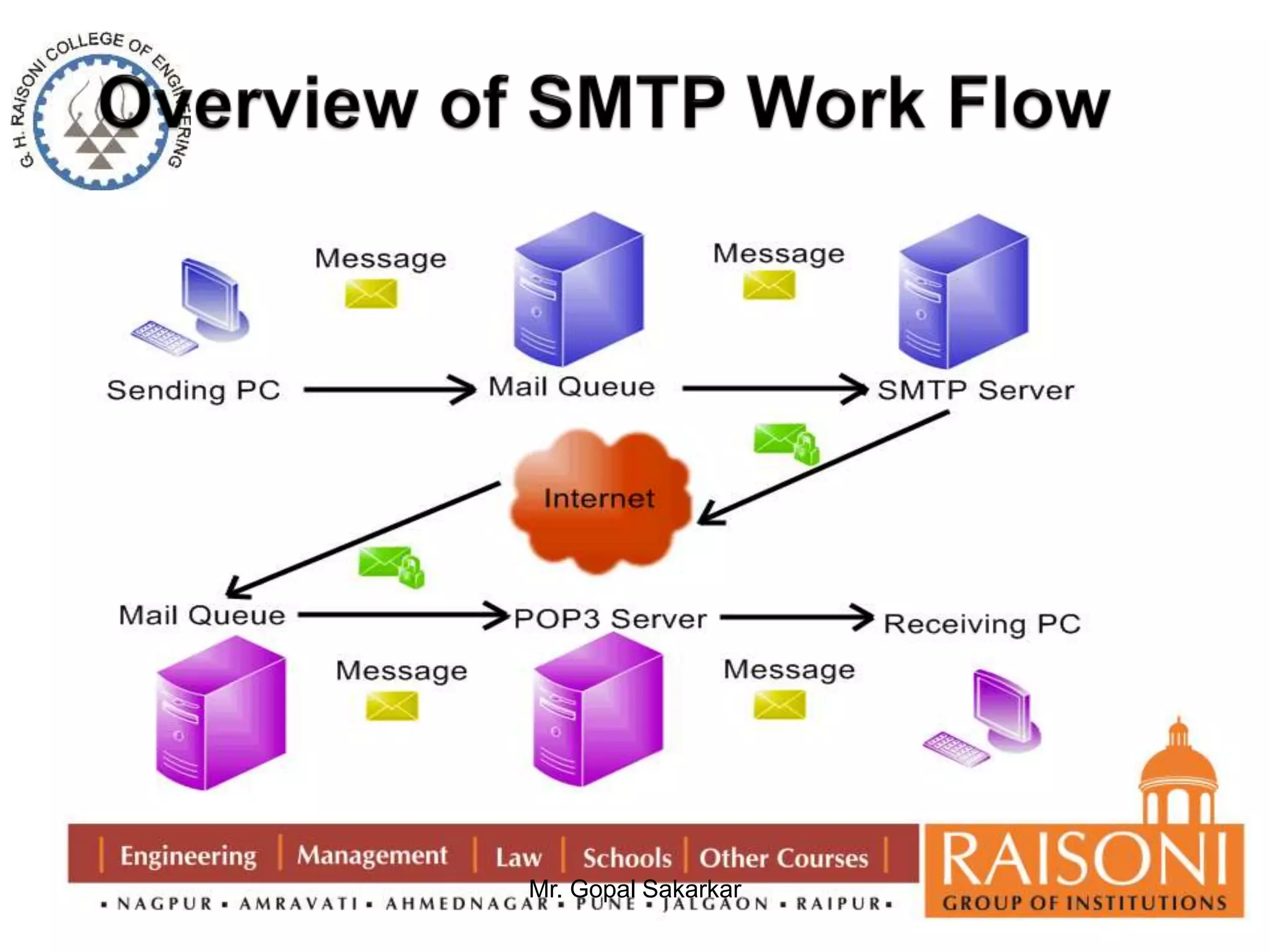
![DSA Signature Verification
having received M & signature (r,s)
to verify a signature, recipient computes:
w = s-1 mod q
u1= [H(M)w ]mod q
u2= (rw)mod q
v = [(gu1 yu2)mod p ]mod q
Mr. Gopal Sakarkar
if v=r then signature is verified](https://image.slidesharecdn.com/ns-140920073509-phpapp02/75/Public-Key-Cryptography-36-2048.jpg)




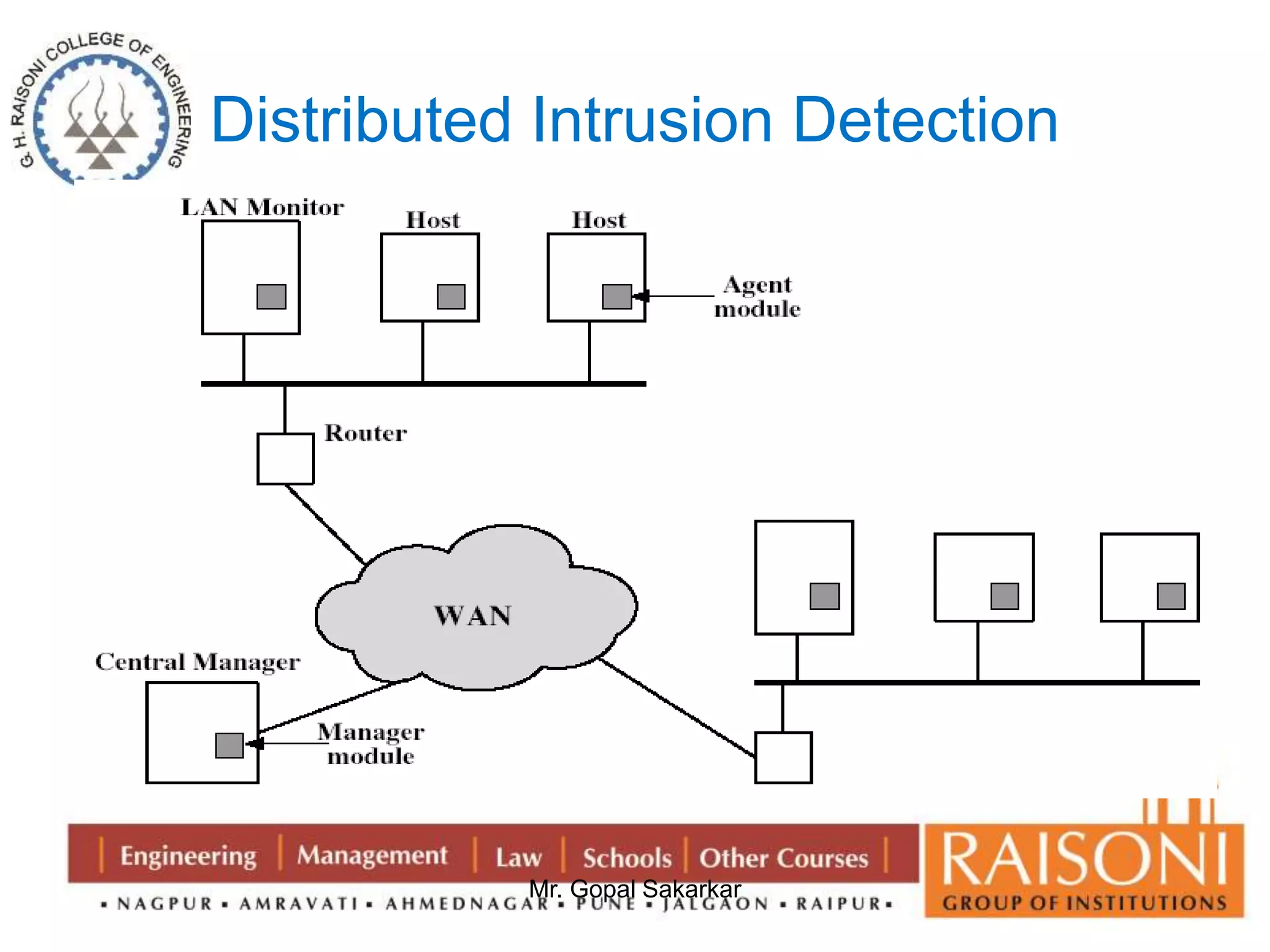
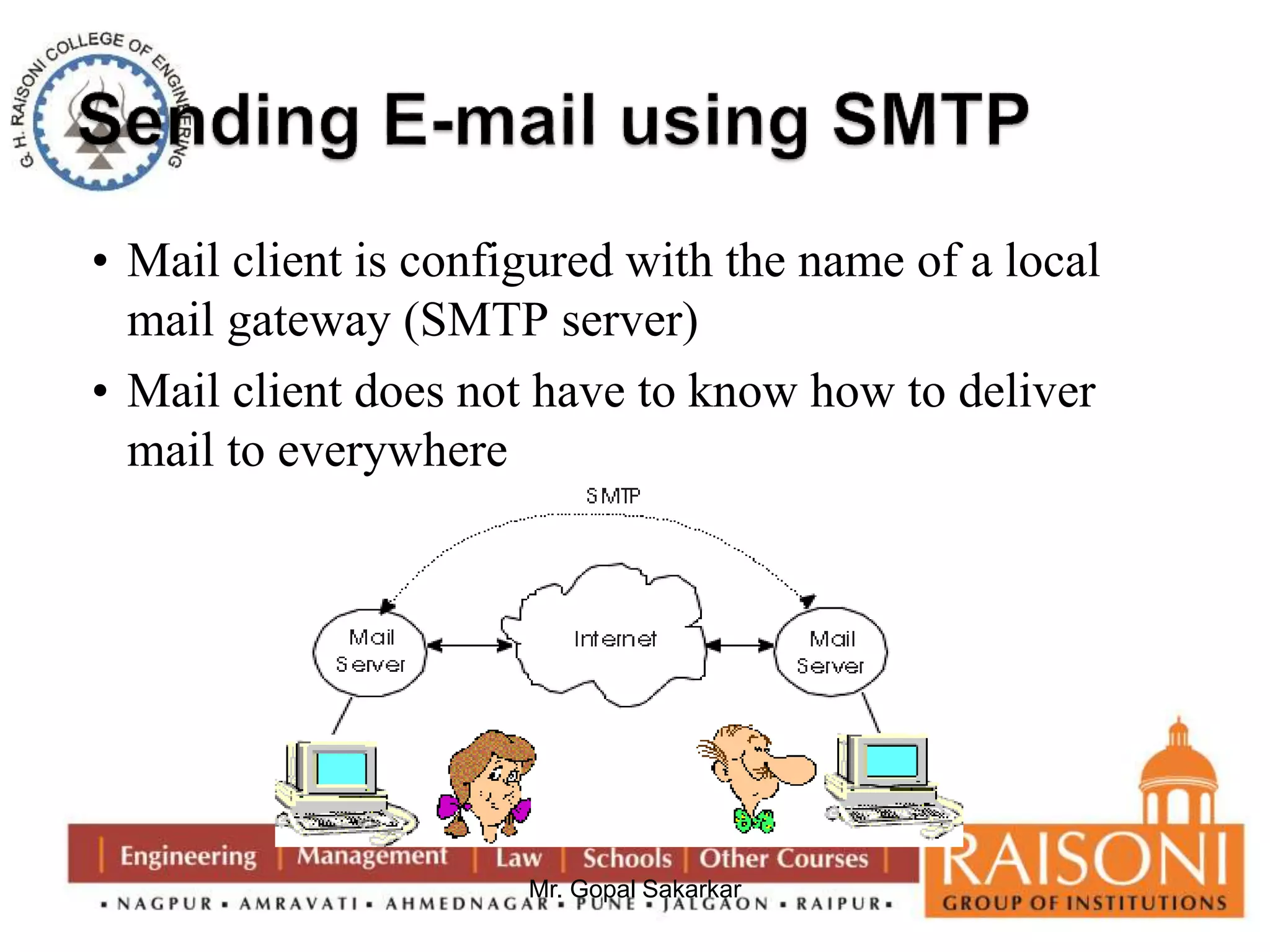
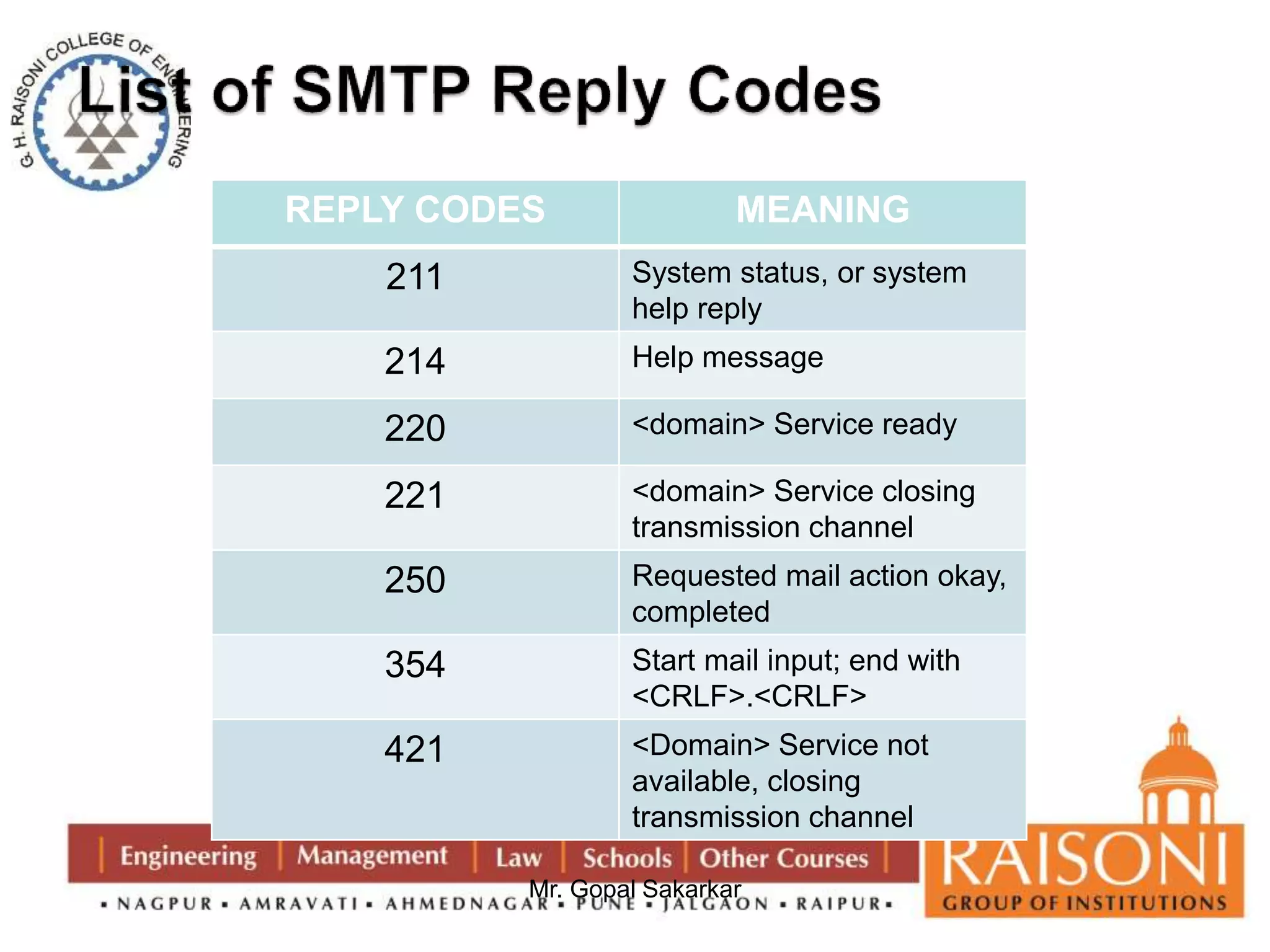
![Modular Arithmetic Operations
Mr. Gopal Sakarkar
Properties of Modular Arithmetic
(a+b) mod n = [a mod n + b mod n] mod n
<proof>
(a-b) mod n = [a mod n - b mod n] mod n
(a X b) mod n = [a mod n X b mod n] mod n
Eg. (11 + 15 ) mod 8 = [11 mod 8 + 15 mod 8] mod 8](https://image.slidesharecdn.com/ns-140920073509-phpapp02/75/Public-Key-Cryptography-44-2048.jpg)

![Greatest Common Divisor (GCD)
• GCD (a,b) of a and b is the greatest number that
divides evenly into both a and b
– eg GCD(60,24) = 12
The positive integer c is said to be the greatest
common divisor of a and b if
1. C is a divisor of a and of b
2. Any divisor of a and b is a divisor of c
It is denoted by
gcd(a,b)= max[k, such that k/a and k/b]
Mr. Gopal Sakarkar](https://image.slidesharecdn.com/ns-140920073509-phpapp02/75/Public-Key-Cryptography-47-2048.jpg)




















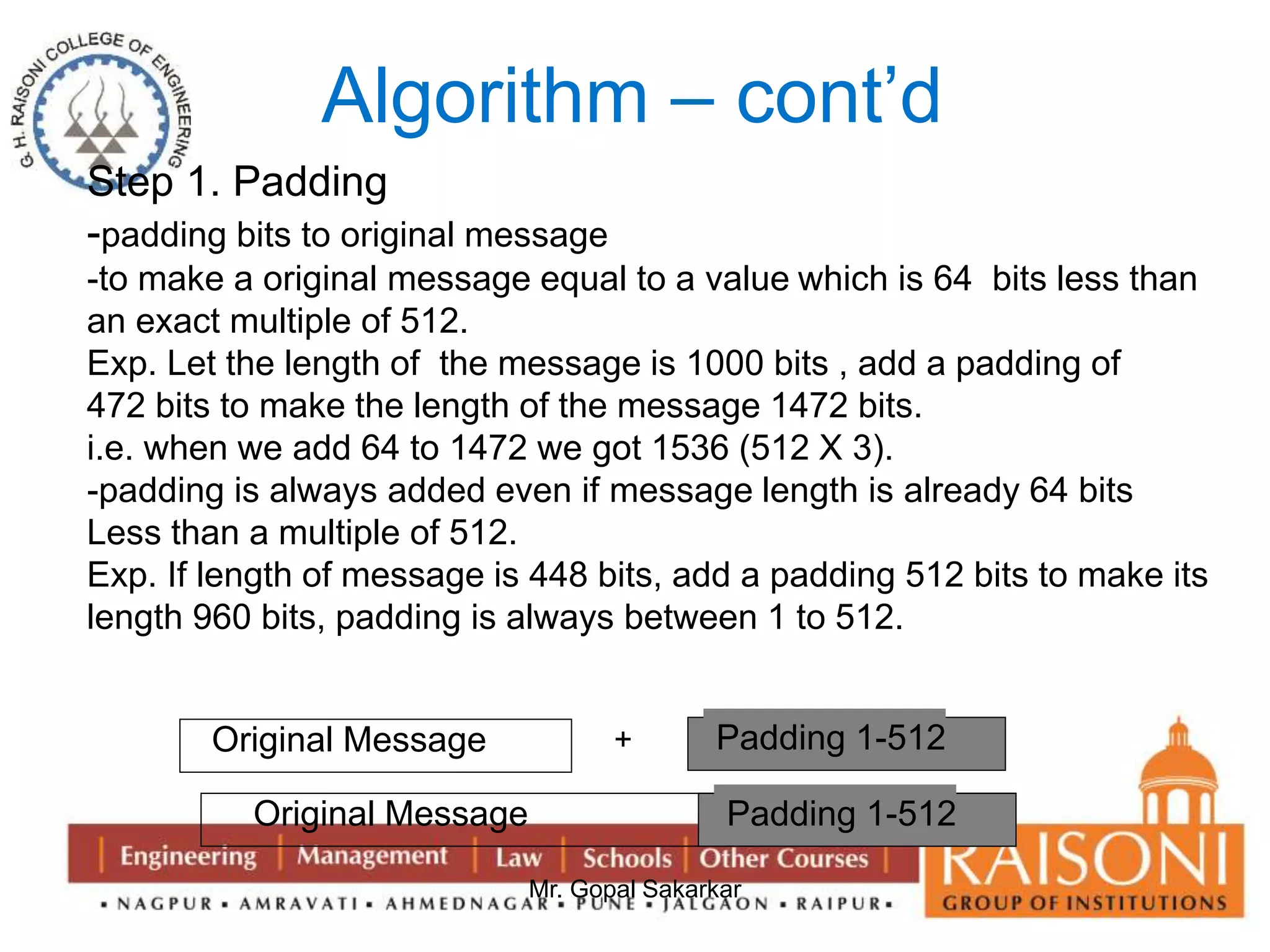
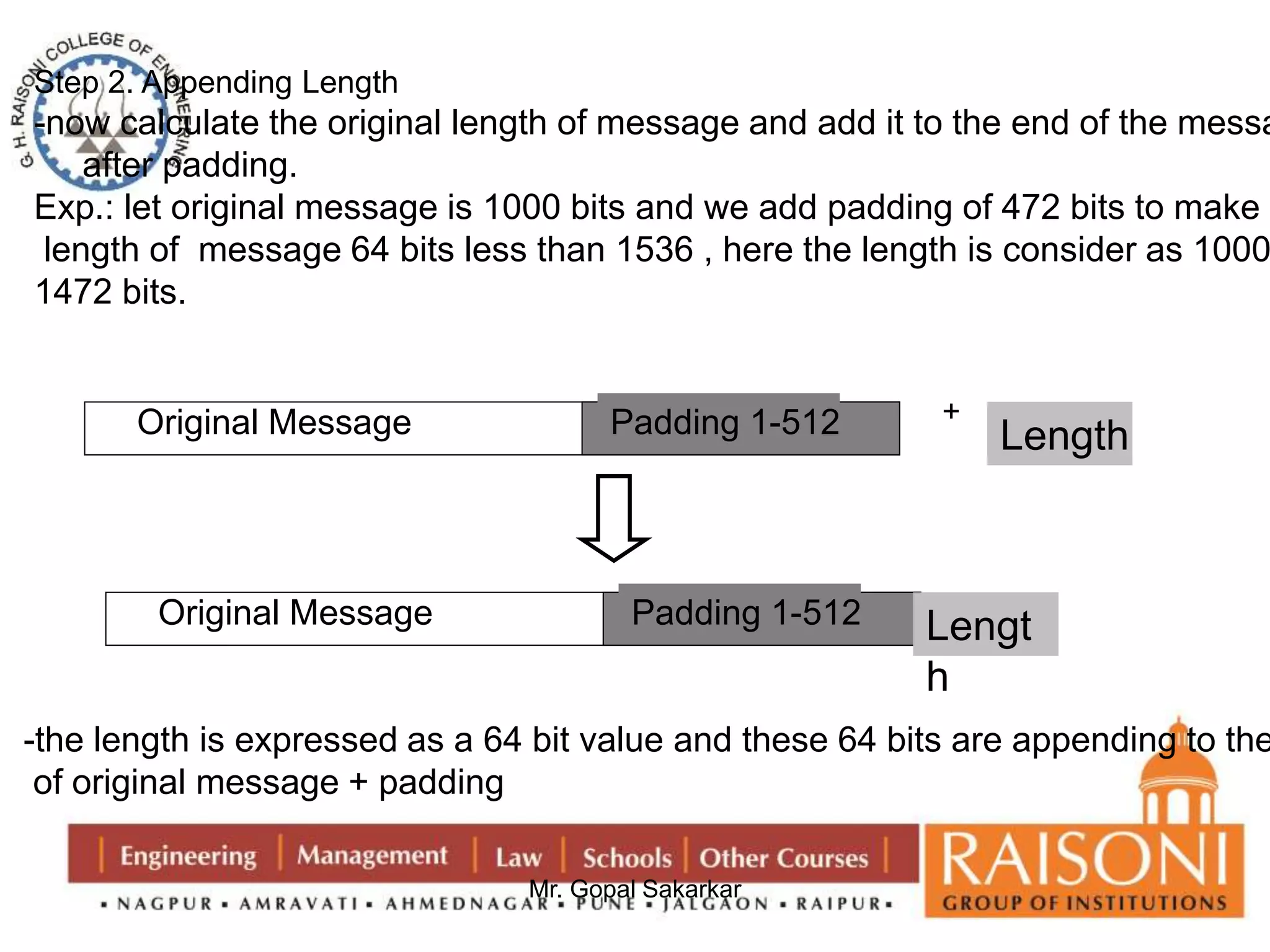
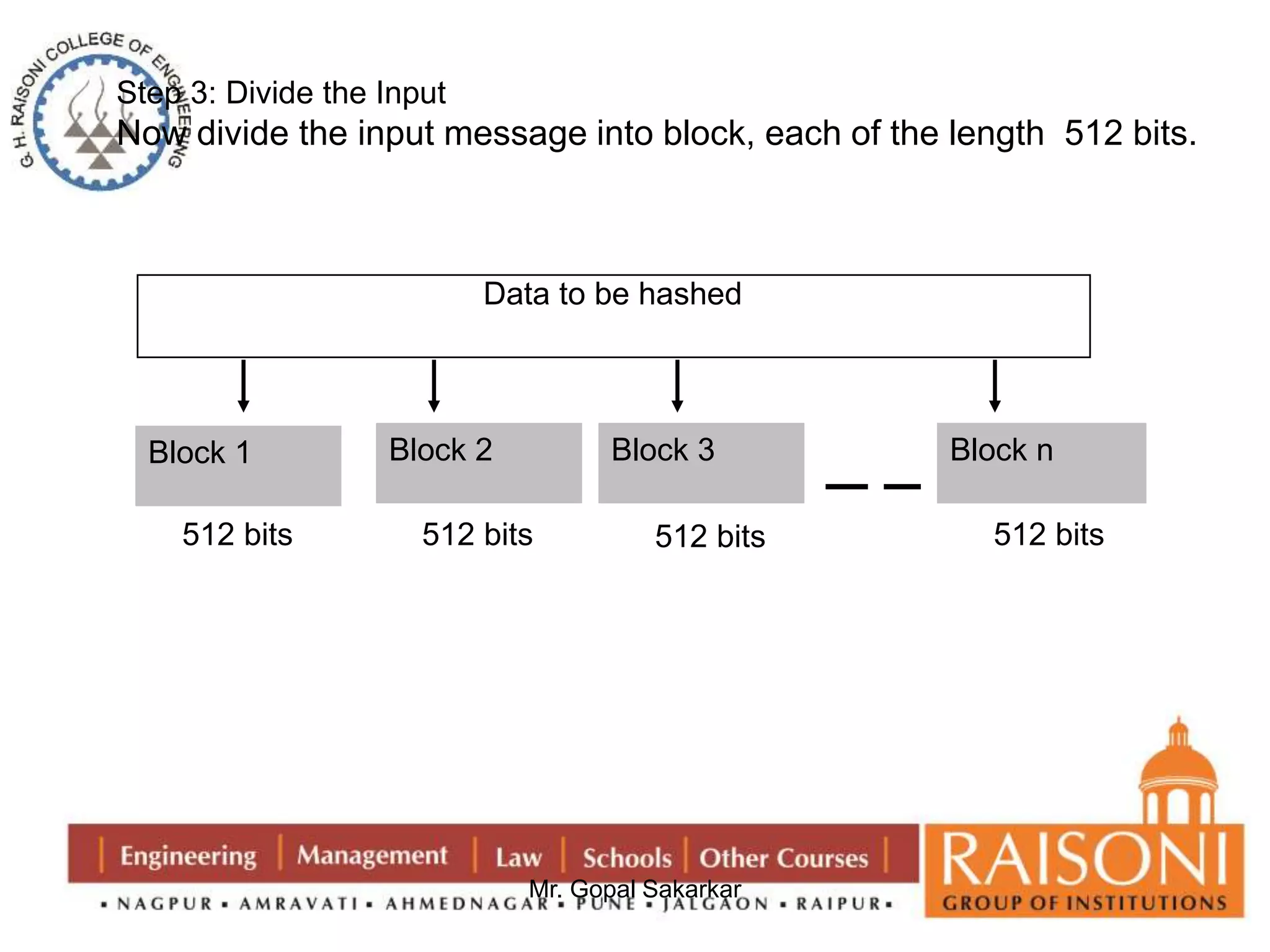
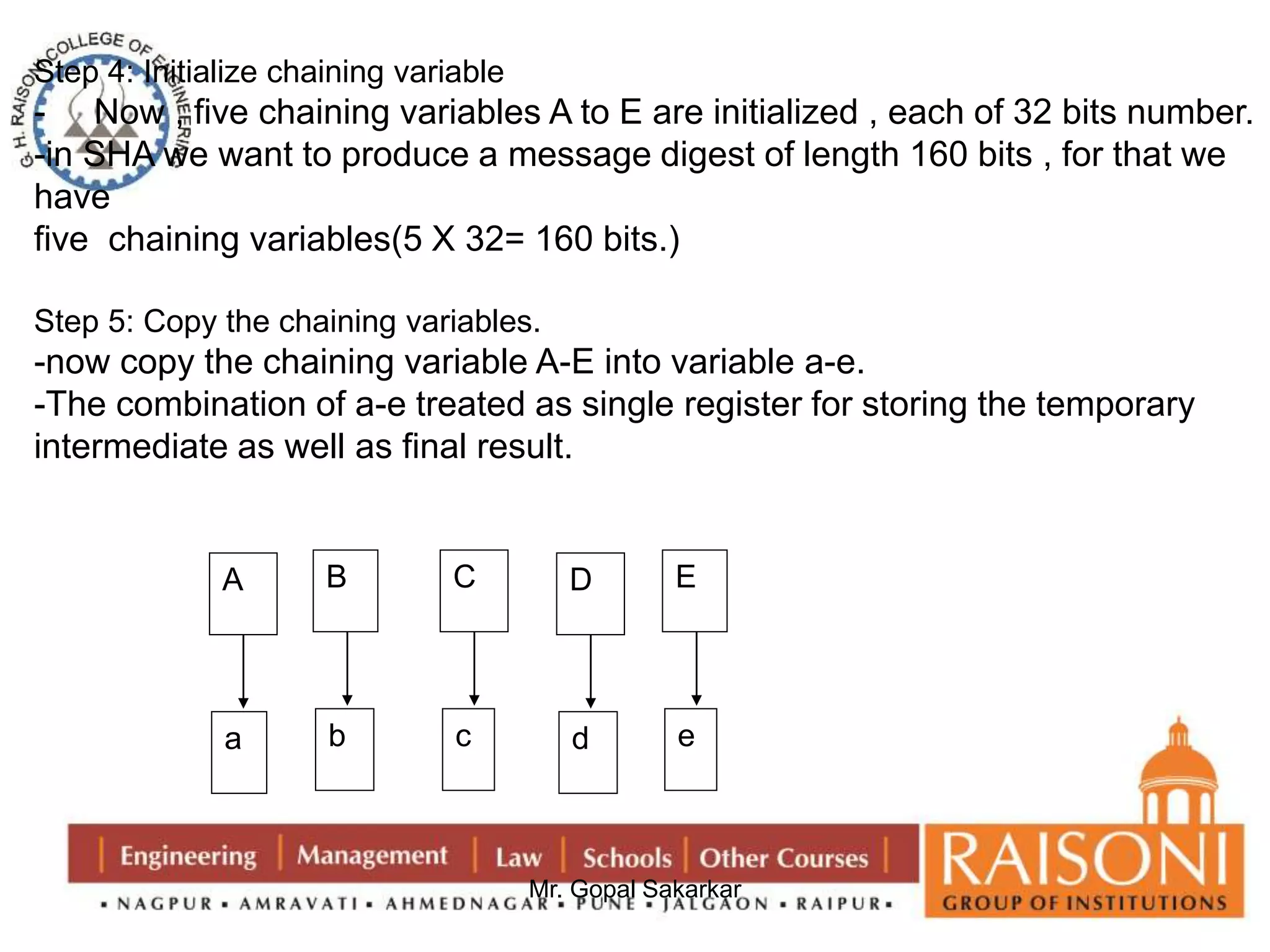
![Step 6: Divide a block
-now divide the current block 512 bits into 16 sub blocks , each of 32 bits.
Step 7: Round and Iterations
-SHA consists of four rounds , each round containing 20 iteration
-This make it total of 80 iterations
-Mathematical representation is:
abcde= (e + Process P + S^5 (a) +W [t] + K[t]) ,a , S^30 (b) ,c,d
Where,
abcde= The registers
Process P = The logical operation
S ^t = Circular –left shift of the 32 bit sub block by t bits
W[t] = A 32 bit derived from the current 32 bit sub block
K[t] = one of the five additive constant
Mr. Gopal Sakarkar](https://image.slidesharecdn.com/ns-140920073509-phpapp02/75/Public-Key-Cryptography-92-2048.jpg)