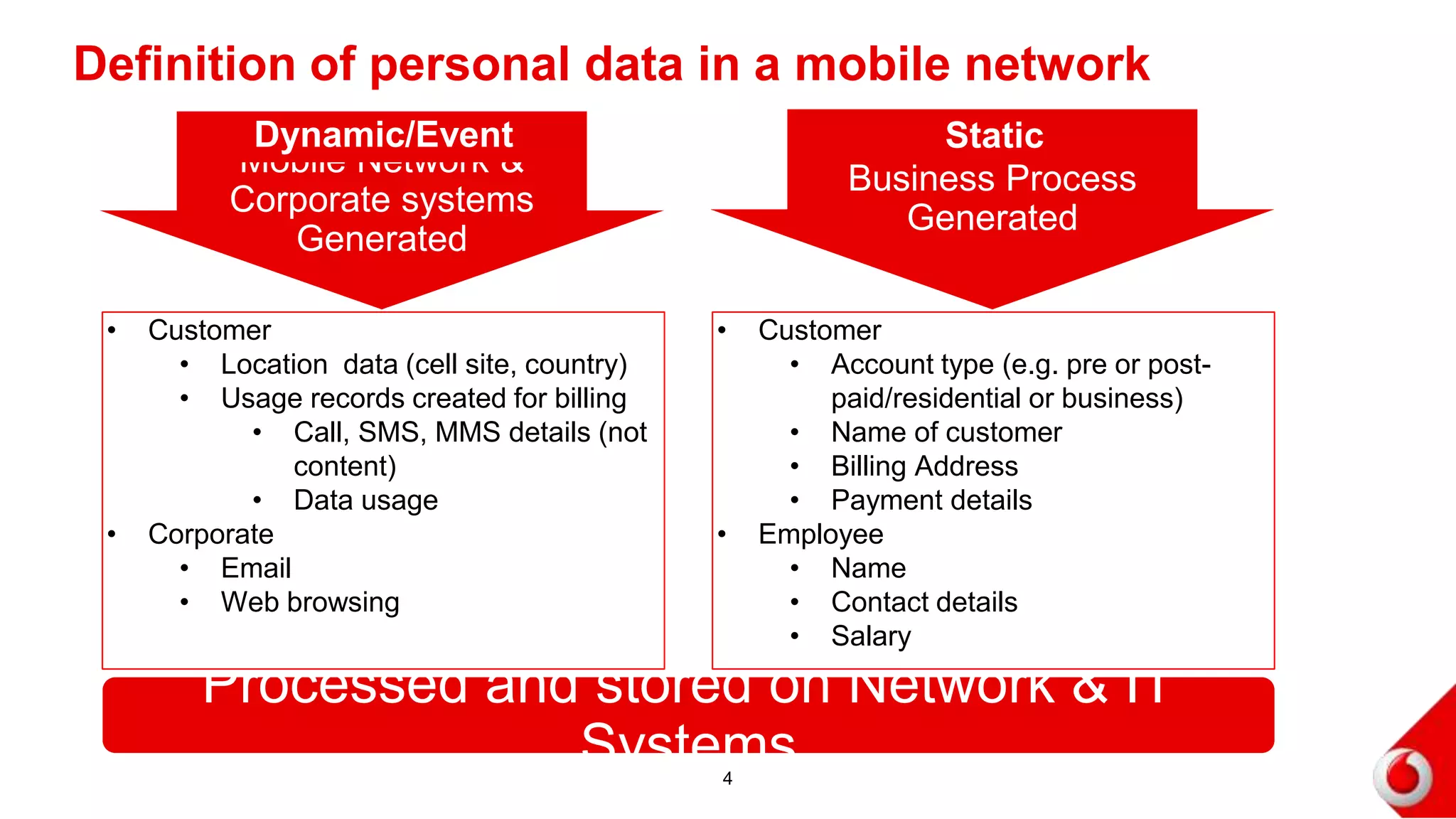
1. The document discusses preventing loss of personal data on a mobile network by addressing technical attacks and risks. It defines personal data as customer information like names, locations, call records, and payment details that are processed and stored on network and IT systems.
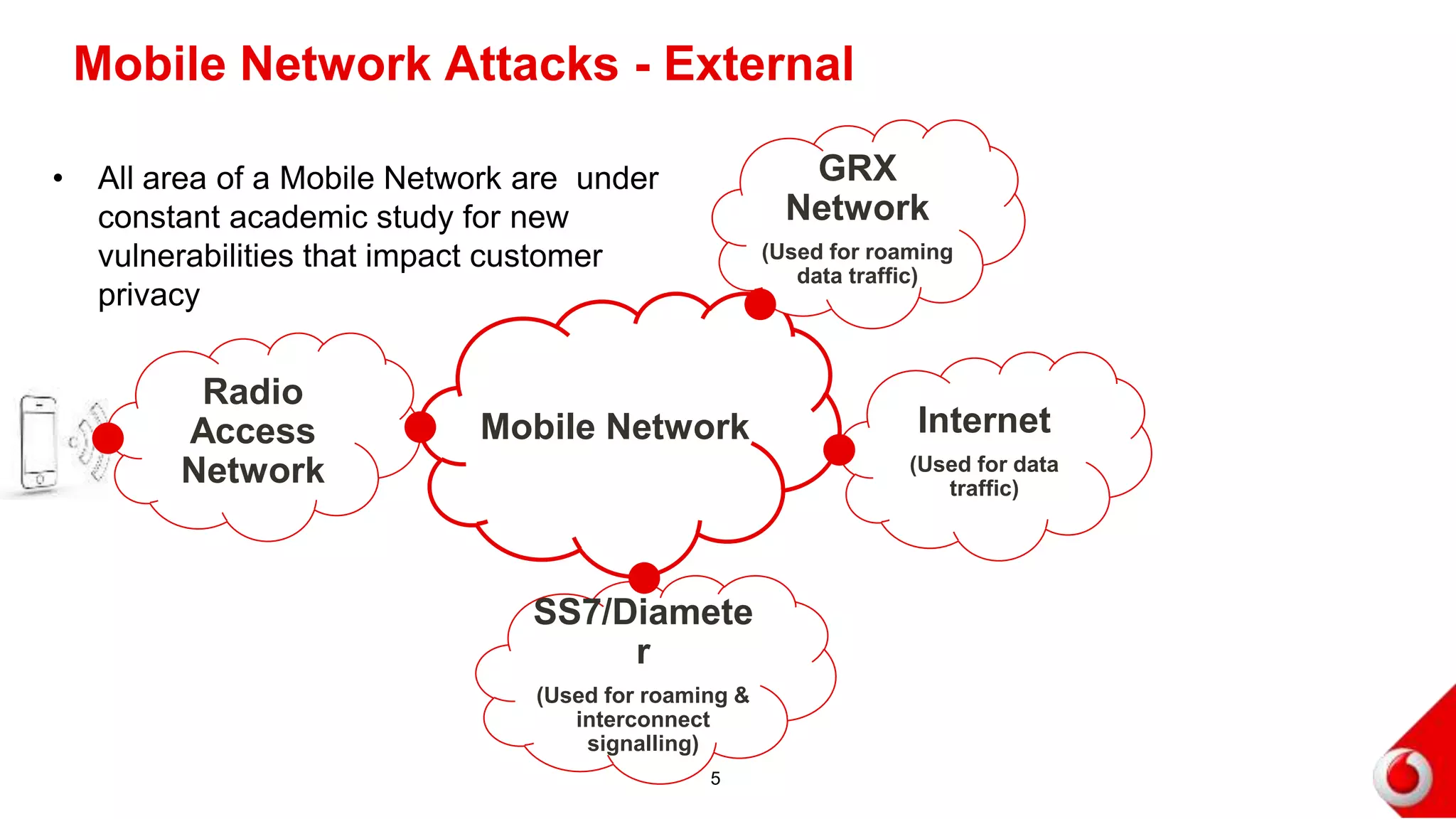
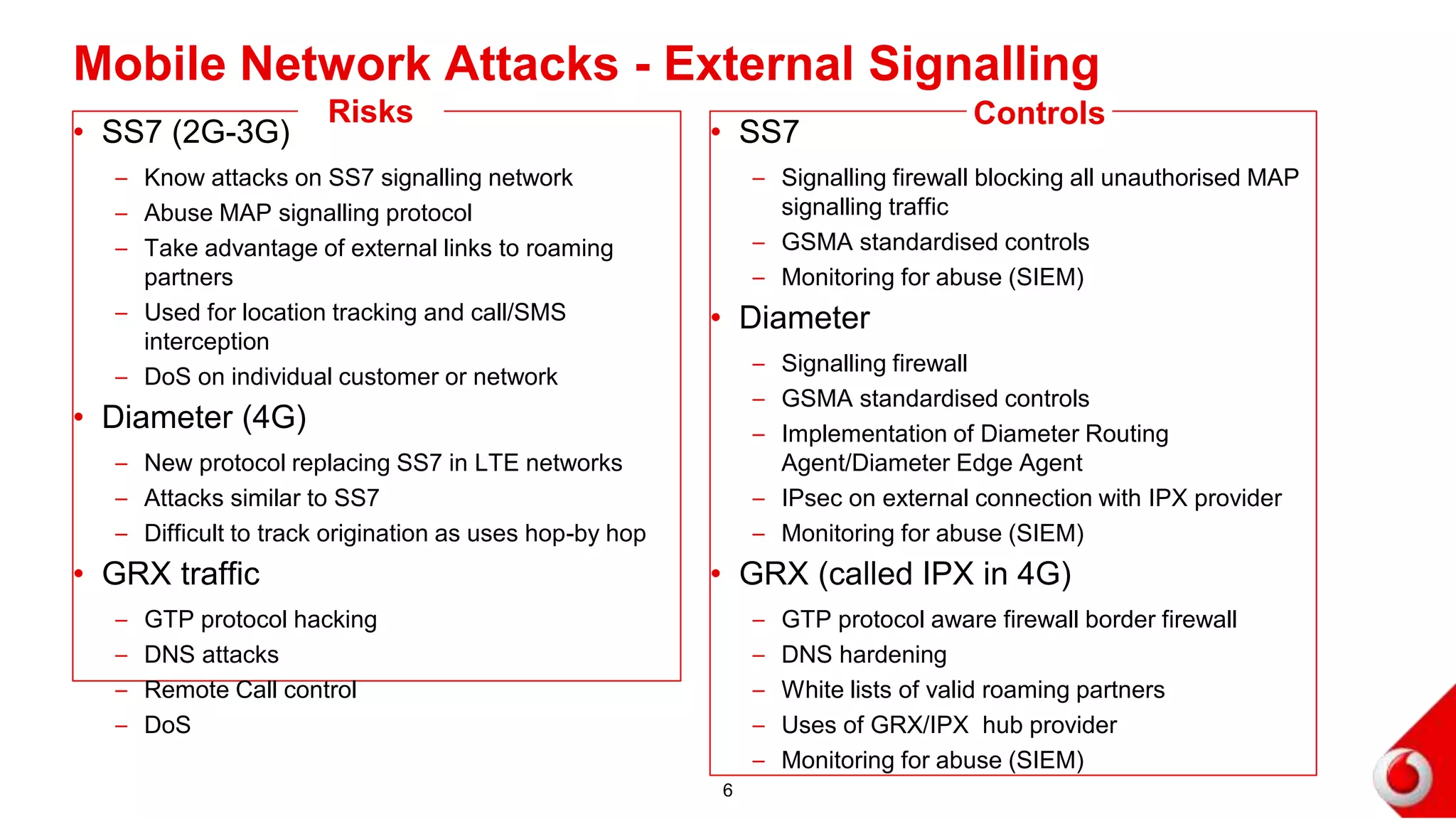
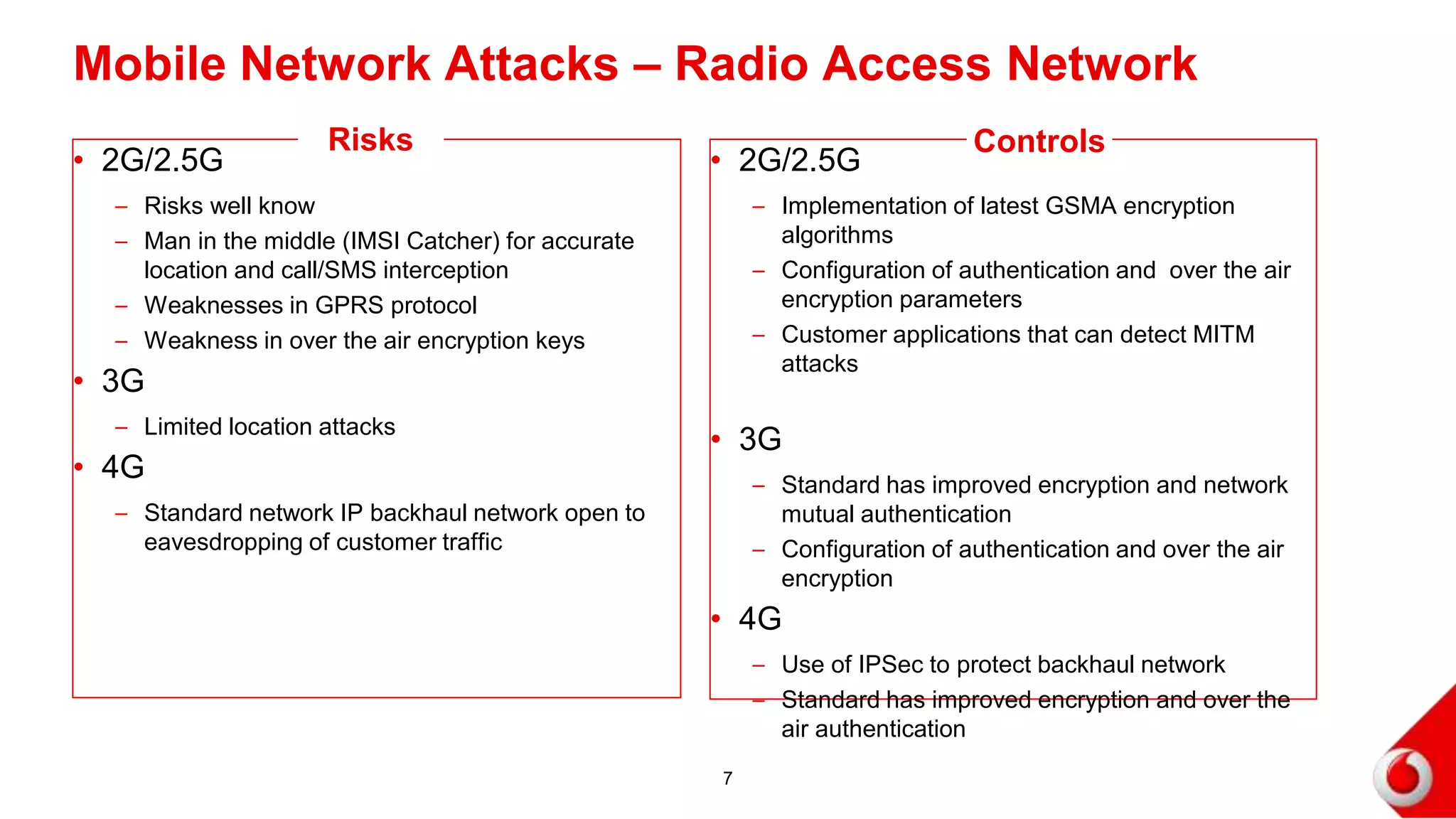
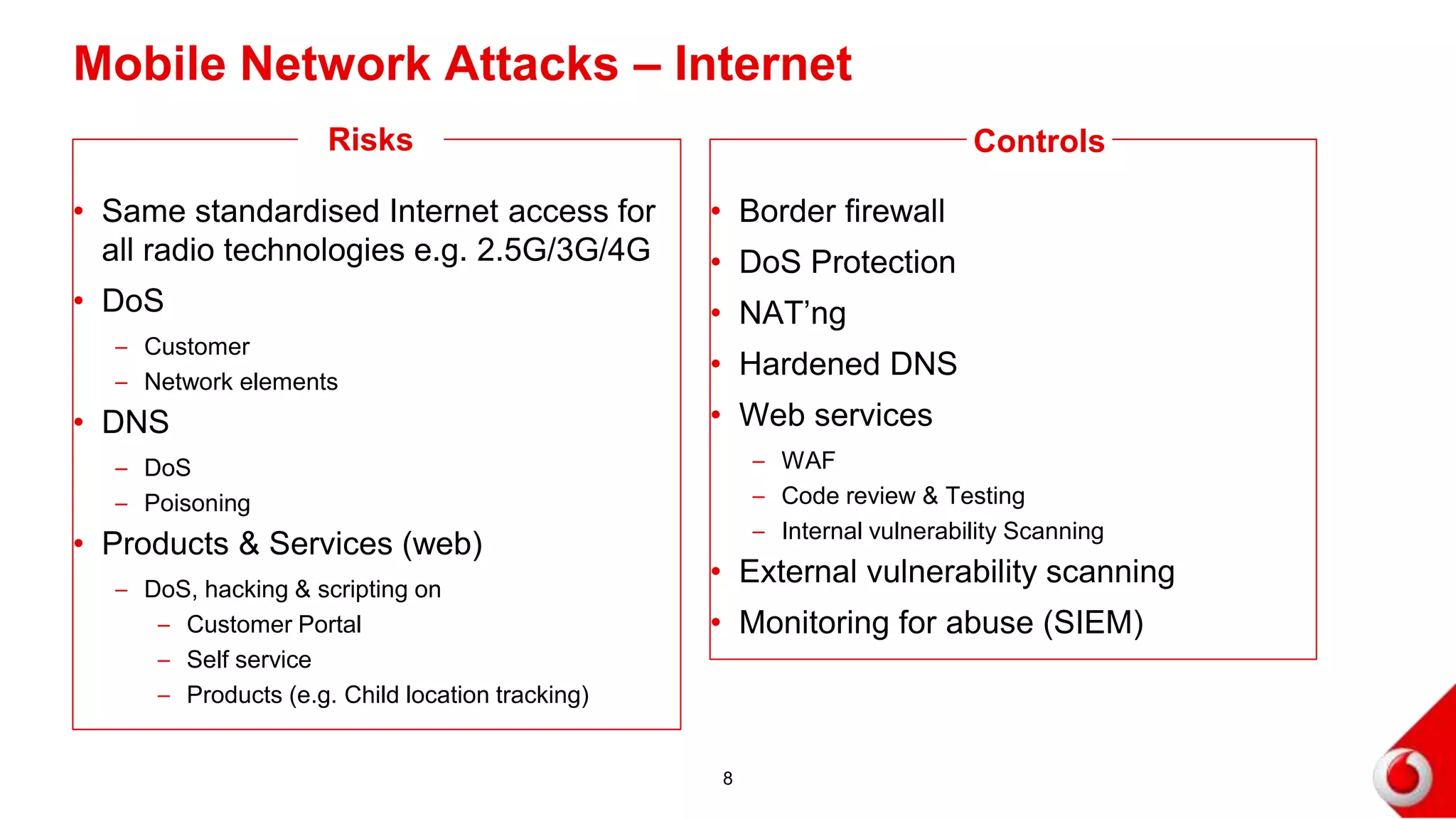
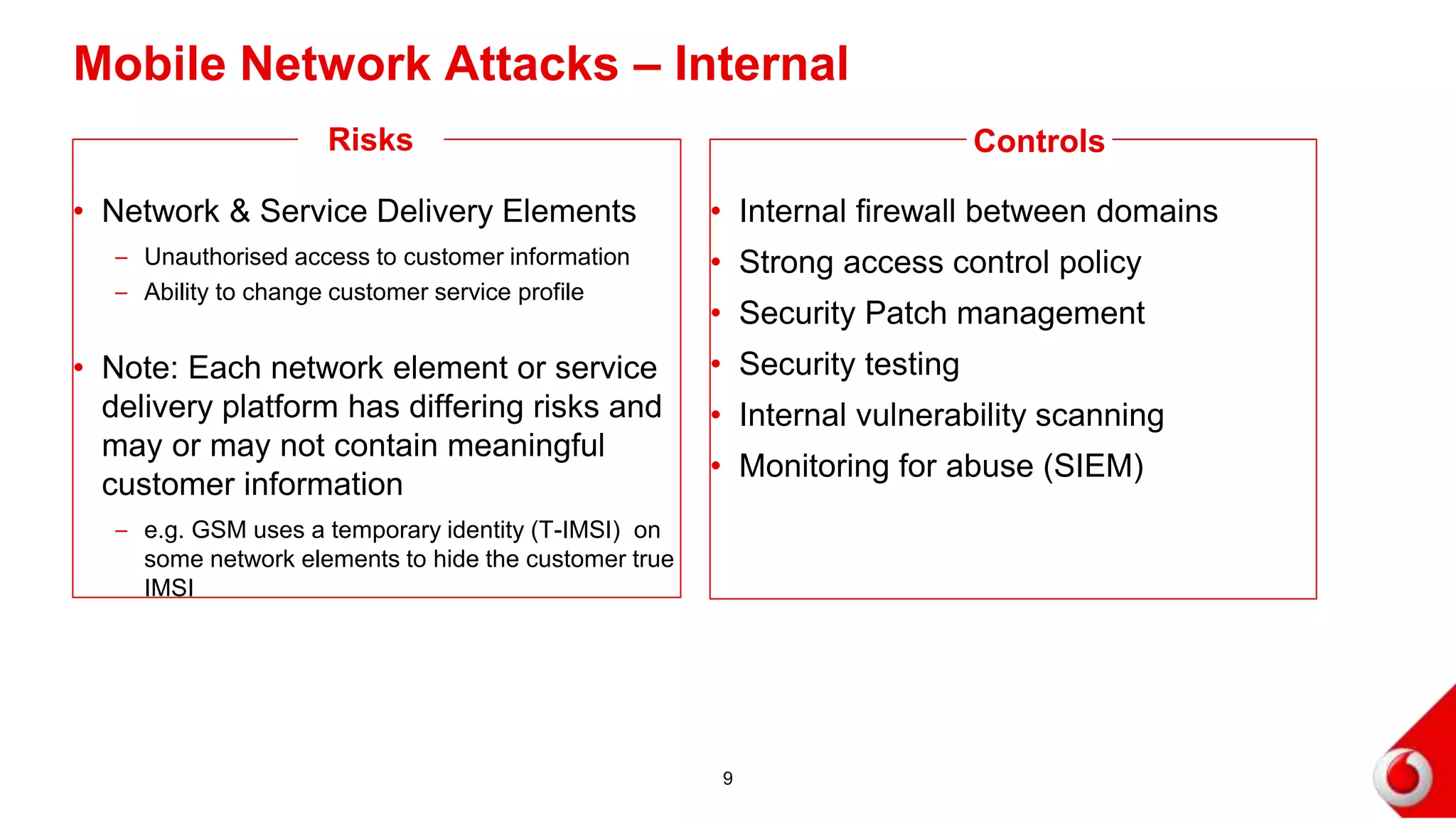
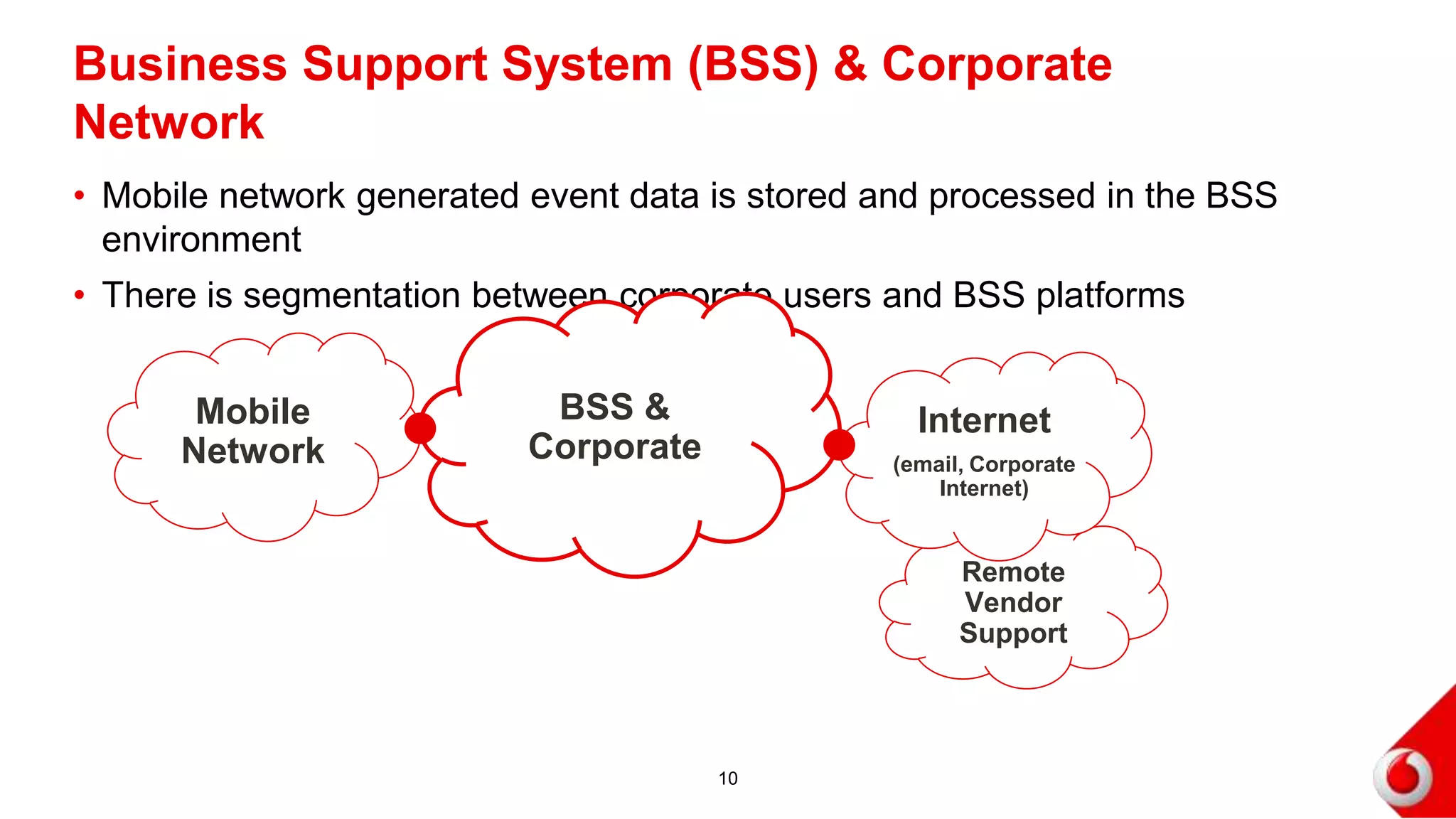
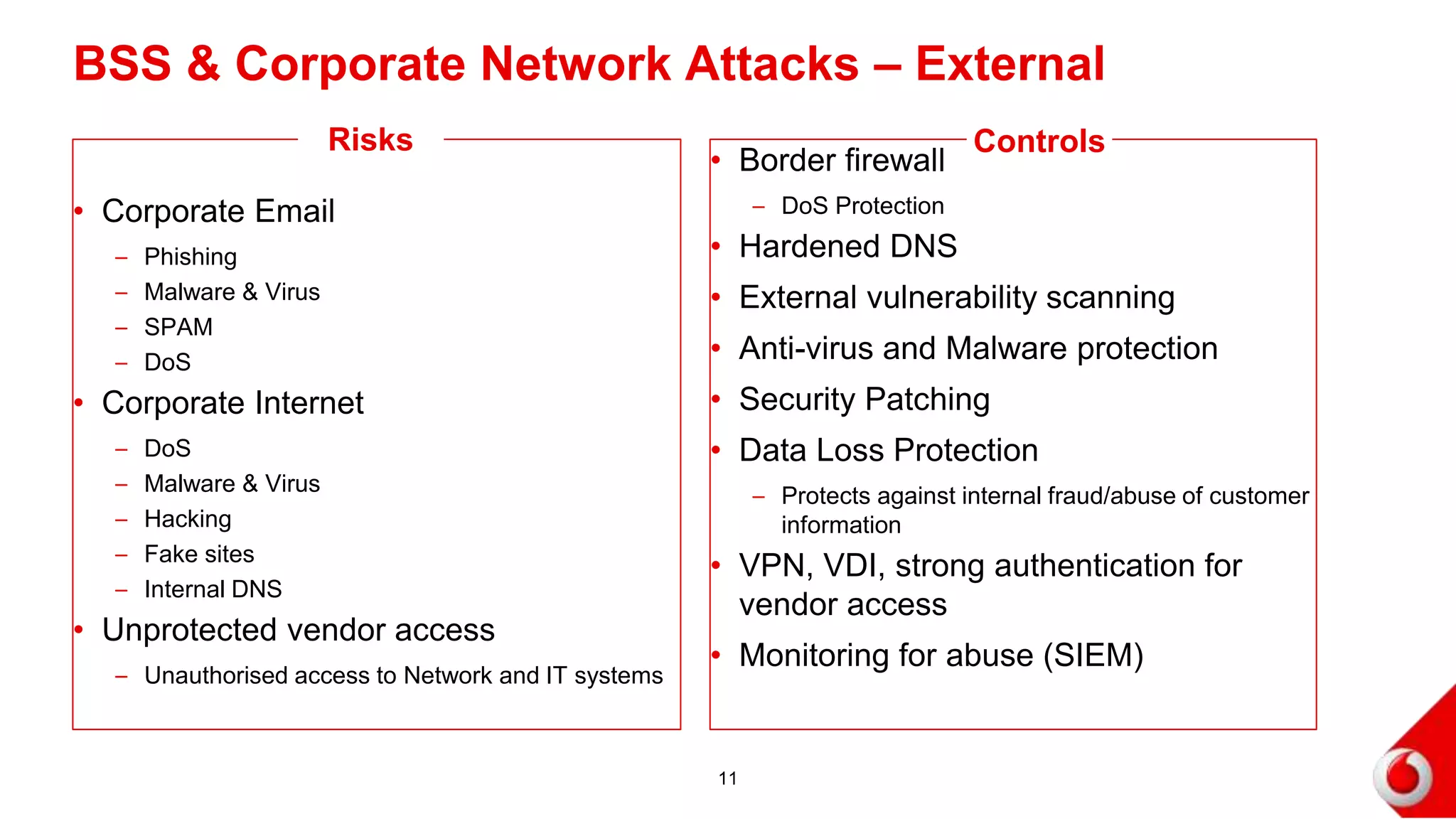
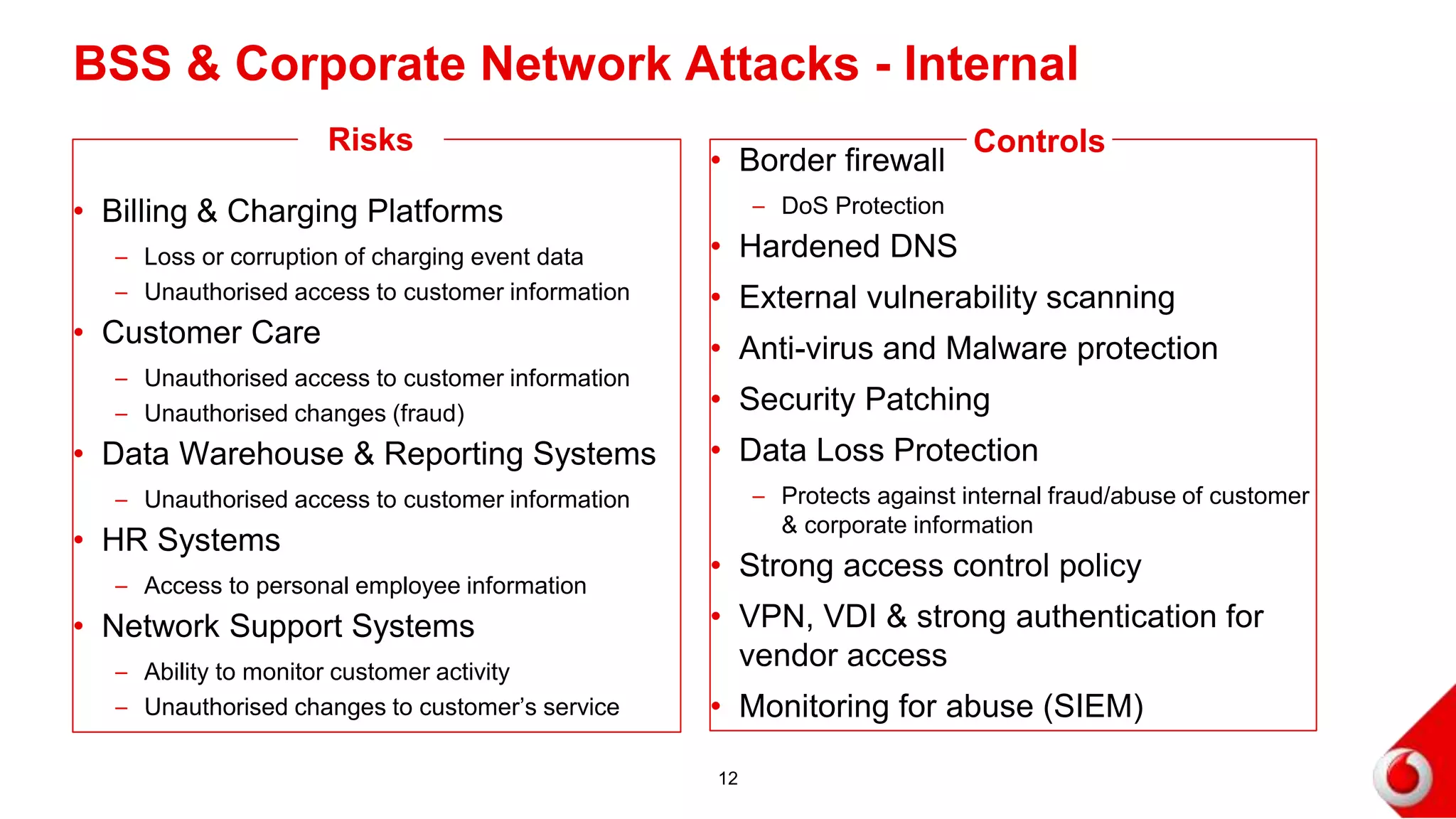
2. Attacks on the mobile network, signaling infrastructure, radio access network, internet, internal networks and business support systems are outlined. Risks include hacking, fraud, and unauthorized access to or corruption of customer data. Controls proposed include firewalls, encryption, access controls, monitoring and security best practices.
3. Managing risks to personal data requires ongoing assessment, testing, monitoring and incident response as technologies and attacks evolve over time. Security must be applied across