This document provides an overview and critique of ANSI SQL isolation levels. It begins with an introduction to transaction isolation and phenomena like dirty reads, non-repeatable reads, and phantoms. It then defines serialization and discusses ANSI SQL isolation levels in terms of locking models. The document analyzes issues with ANSI SQL isolation levels and phenomena. It proposes modifications to more accurately characterize isolation levels and phenomena. Finally, it discusses other isolation types like cursor stability and snapshot isolation that provide higher concurrency than serializable isolation.



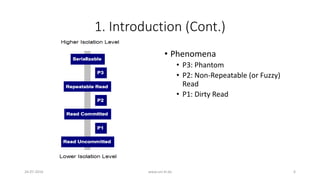
![1. Introduction
• ACID Transaction
• Atomicity [All or nothing]
• Consistency [Only valid data]
• Isolation [No Interference]
• Durability [Data is recoverable]
26-07-2016 www.uni-kl.de 4](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-4-320.jpg)


![Shorthand notations
26-07-2016 www.uni-kl.de 8
Operation Description
r1[x] read of x by transaction 1
w2[x] write by transaction 2 on data item x
r1[p] transaction 1 reading a set of records satisfying predicate p
w2[p] transaction 2 writing a set of records satisfying predicate p
a1 transaction 1 abort
c2 transaction 2 commit](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-8-320.jpg)
![2.1 Serializability Concepts
• Definitions
• History: A history models the interleaved execution of a set of transactions as
a linear ordering of their actions, such as Reads and Writes (i.e., inserts,
updates, and deletes) of specific data items
• H1: r1[x] w1[x] c1 r2[y] w2[y] c2
26-07-2016 www.uni-kl.de 9](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-9-320.jpg)
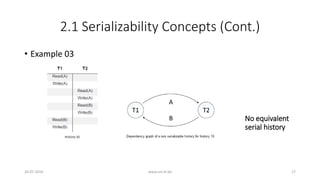
![2.1 Serializability Concepts (Cont.)
• Definitions (Cont.)
• Serializable: A history that is equivalent (in its outcome) to a serial history
• H2: r1[x] r2[y] w1[x] w2[y] c1 c2
26-07-2016 www.uni-kl.de 10](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-10-320.jpg)
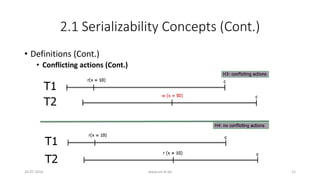
![2.1 Serializability Concepts (Cont.)
• Definitions (Cont.)
• Conflicting actions: Two actions are said to be in conflict if
• The actions belong to different transactions.
• The actions access the same object (read or write).
• At least one of the actions is a write operation.
• H3: r1[x] w2[x] : conflicting actions
• H4: r1[x] r2[x] : no conflicting actions
26-07-2016 www.uni-kl.de 11](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-11-320.jpg)
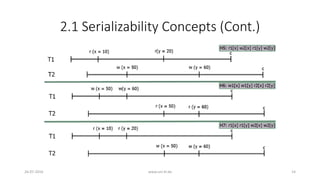
![2.1 Serializability Concepts (Cont.)
• Definitions (Cont.)
• Conflicting equivalence: The histories H5 and H7 are said to be conflict-
equivalent if following two conditions are satisfied
• Both histories H5 and H7 involve the same set of transactions (including ordering of
actions within each transaction).
• Both schedules have same set of conflicting operations.
• Example:
• H5: r1[x] w2[x] r1[y] w2[y]
• H6: w1[x] w1[y] r2[x] r2[y]
• H7: r1[x] r1[y] w2[x] w2[y]
26-07-2016 www.uni-kl.de 13](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-13-320.jpg)

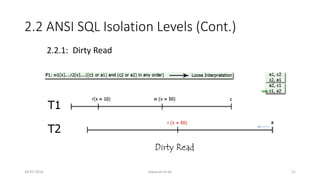
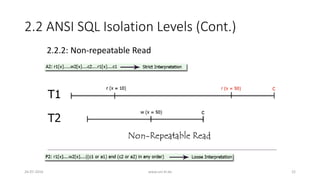
![2.2 ANSI SQL Isolation Levels (Cont.)
2.2.3: Phantom Read [strict interpretation]
26-07-2016 www.uni-kl.de 23](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-23-320.jpg)
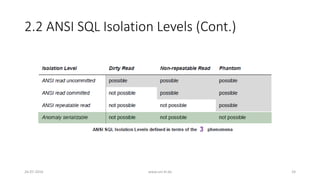

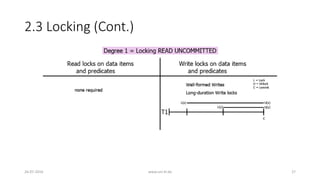
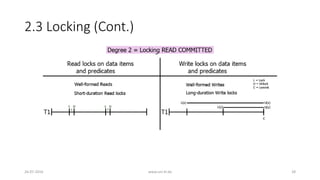
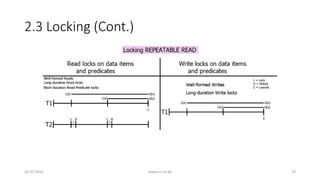
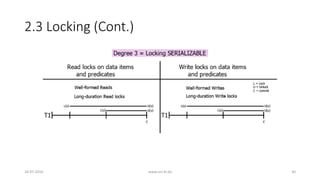


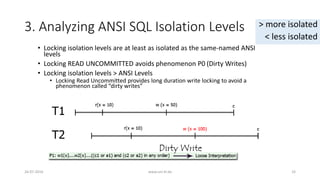
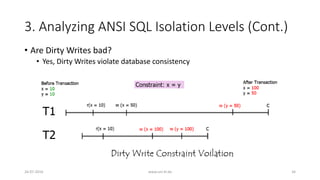
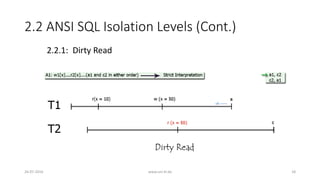
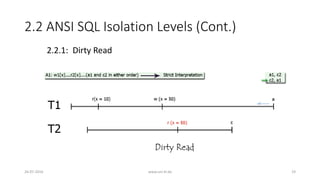
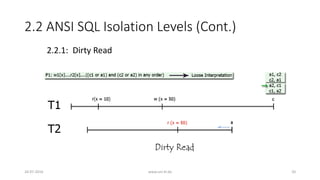
![3. Analyzing ANSI SQL Isolation Levels (Cont.)
• Hence, ANSI SQL isolation should be modified to require P0 for all
isolation levels
• Loose interpretation of three ANSI phenomena is required
• Recall strict interpretation
• A1: w1[x]...r2[x]...(a1 and c2 in either order) (Dirty Read)
• A2: r1[x]...w2[x]...c2...r1[x]...c1 (Fuzzy or Non-Repeatable Read)
• A3: r1[P]...w2[y in P]...c2....r1[P]...c1 (Phantom)
26-07-2016 www.uni-kl.de 35](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-35-320.jpg)
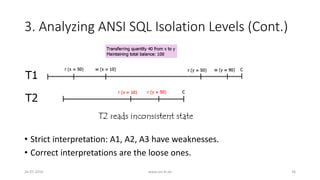
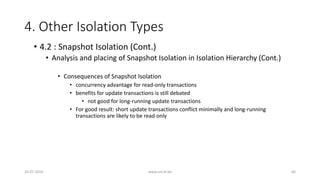
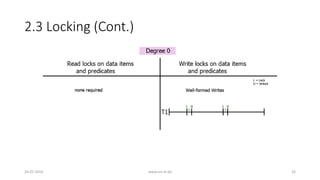
![3. Analyzing ANSI SQL Isolation Levels (Cont.)
• ANSI SQL isolation phenomena are incomplete
• Number of anomalies still can arise
• New phenomena must be defined
• P3 must be restated
• Restating P3
• ANSI SQL P3 only prohibits inserts to a predicate
• P3: r1[P]...w2[y in P]...(c1 or a1) prohibits any write to a predicate
• e.g. insert, update, delete
26-07-2016 www.uni-kl.de 37](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-37-320.jpg)
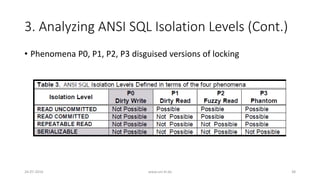


![4. Other Isolation Types
26-07-2016 www.uni-kl.de 41
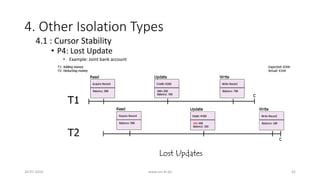
• 4.1 : Cursor Stability
• P4 (Lost Update)
• P4: r1[x]...w2[x]...w1[x]...c1](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-41-320.jpg)

![4. Other Isolation Types
26-07-2016 www.uni-kl.de 45
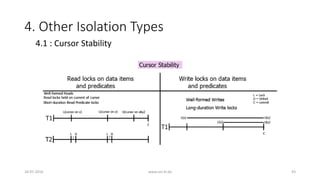
• 4.1 : Cursor Stability
• P4C (Cursor Lost Update)
• P4C: rc1[x]...w2[x]...w1[x]...c1
• Phenomenon P4 renamed to P4C
• Read Committed < Cursor Stability < Repeatable Read](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-45-320.jpg)

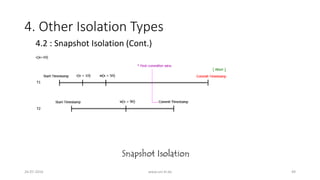
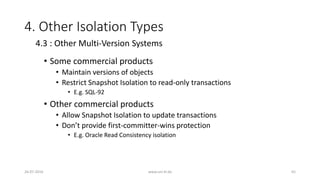
![4. Other Isolation Types
26-07-2016 www.uni-kl.de 50
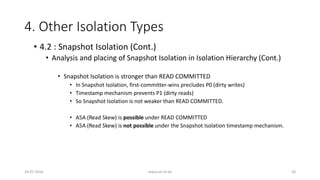
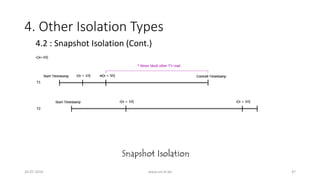
• 4.2 : Snapshot Isolation (Cont.)
• Snapshot Isolation (SI) is a multi-version method
• At any time, each data item might have multiple versions
• Reads by a transaction must choose the appropriate version
• Example : Transferring $40 from x to y
• H1: r1[x=50]w1[x=10]r2[x=10]r2[y=50]c2 r1[y=50]w1[y=90]c1](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-50-320.jpg)
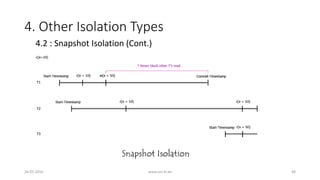
![4. Other Isolation Types
26-07-2016 www.uni-kl.de 51
• 4.2 : Snapshot Isolation (Cont.)
• Under Snapshot Isolation, the same sequence of actions would lead to the
multi-valued history
• H1.SI: r1[x0=50] w1[x1=10] r2[x0=50] r2[y0=50] c2 r1[y0=50] w1[y1=90] c1
• H1.SI has the data flows of a serializable execution](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-51-320.jpg)
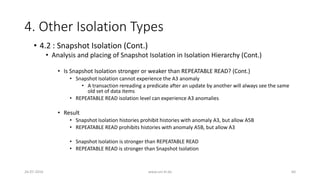
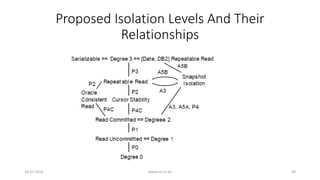
![4. Other Isolation Types
26-07-2016 www.uni-kl.de 52
• 4.2 : Snapshot Isolation (Cont.)
• Snapshot Isolation MV histories can be mapped to single-valued histories
• H1.SI.SV: r1[x=50] r1[y=50] r2[x=50] r2[y=50] c2 w1[x=10] w1[y=90] c1
• And thus, we put Snapshot Isolation in Isolation Hierarchy](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-52-320.jpg)
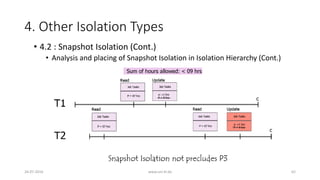
![4. Other Isolation Types
26-07-2016 www.uni-kl.de 53
• 4.2 : Snapshot Isolation (Cont.)
• Snapshot Isolation is non-serializable
• Transaction’s Reads come at one instant and the Writes at another
• H5: r1[x=50] r1[y=50] r2[x=50] r2[y=50] w1[y=-40] w2[x=-40] c1 c2
• Hence, constraint fails to hold in H5](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-53-320.jpg)

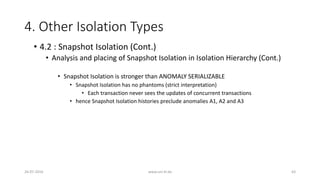
![4. Other Isolation Types
26-07-2016 www.uni-kl.de 55
• 4.2 : Snapshot Isolation (Cont.)
• A5A Read Skew
• r1[x]...w2[x]...w2[y]...c2...r1[y]...(c1 or a1)](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-55-320.jpg)
![4. Other Isolation Types
26-07-2016 www.uni-kl.de 56
• 4.2 : Snapshot Isolation (Cont.)
• A5B Write Skew
• r1[x]...r2[y]...w1[y]...w2[x]...(c1 and c2 occur)](https://image.slidesharecdn.com/5d61848d-c47a-4d71-bea3-f1ca0a742a6a-160727230250/85/Presentation_ANSI_SQL_Isolation_Levels-56-320.jpg)