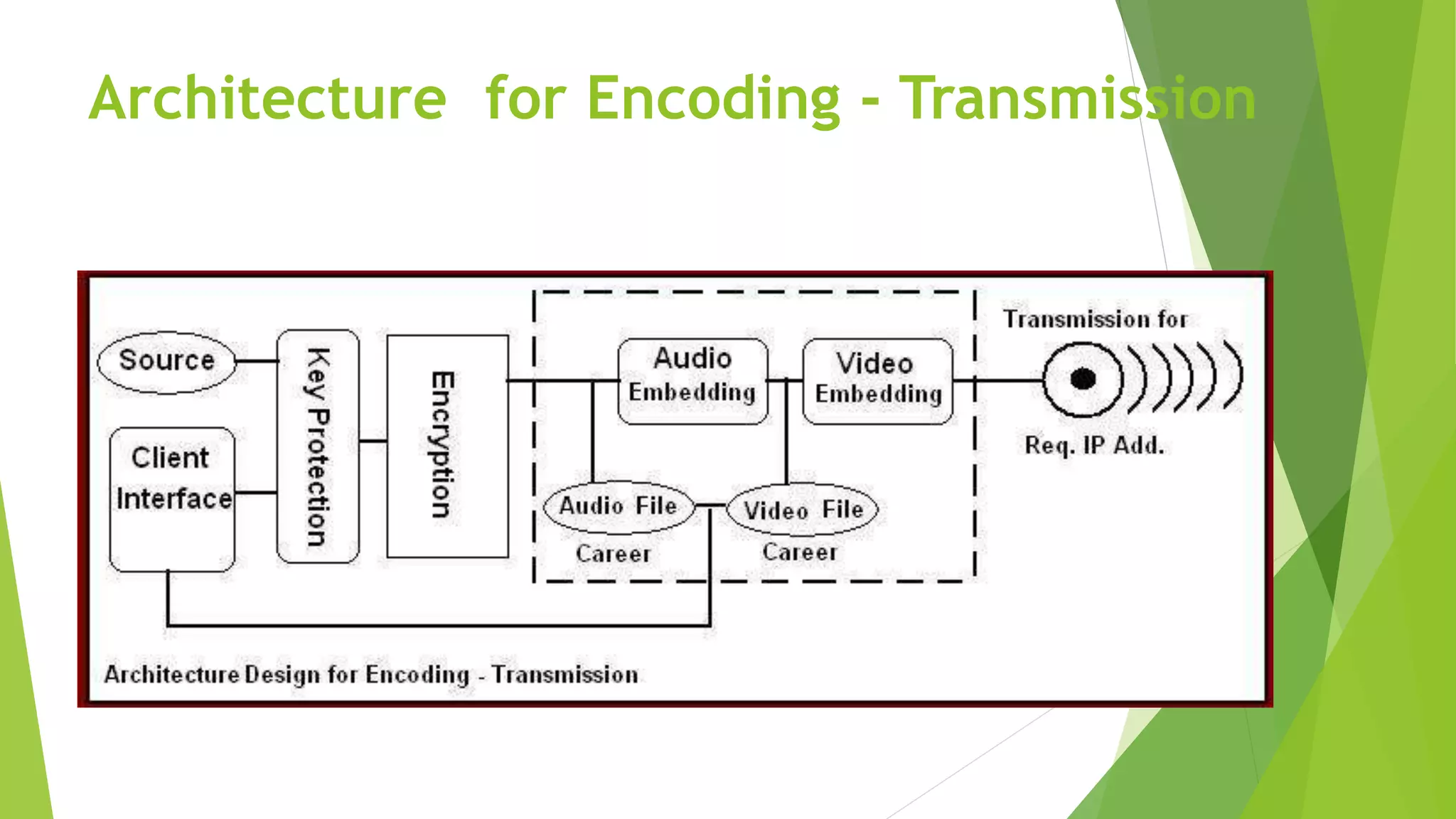
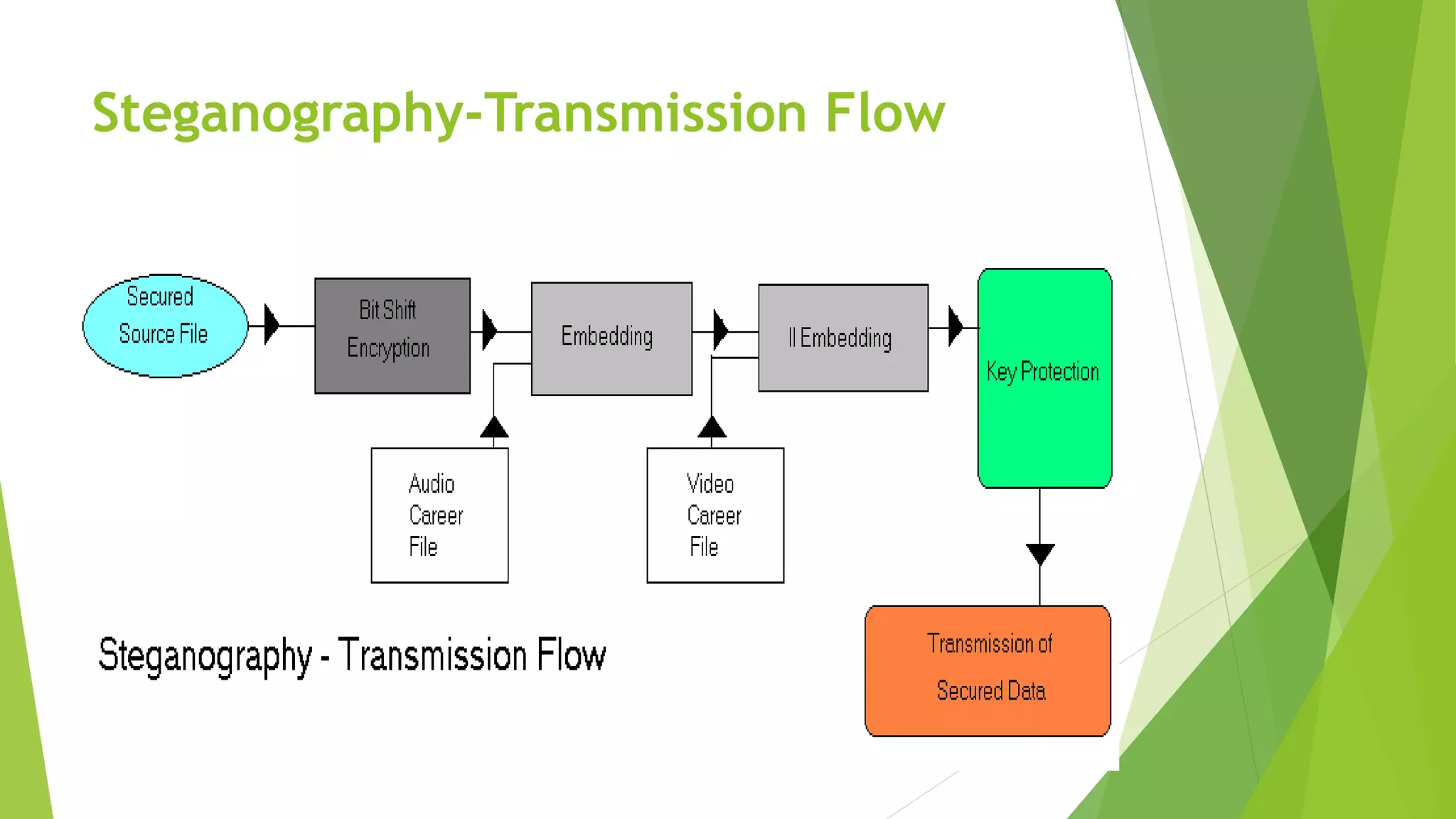
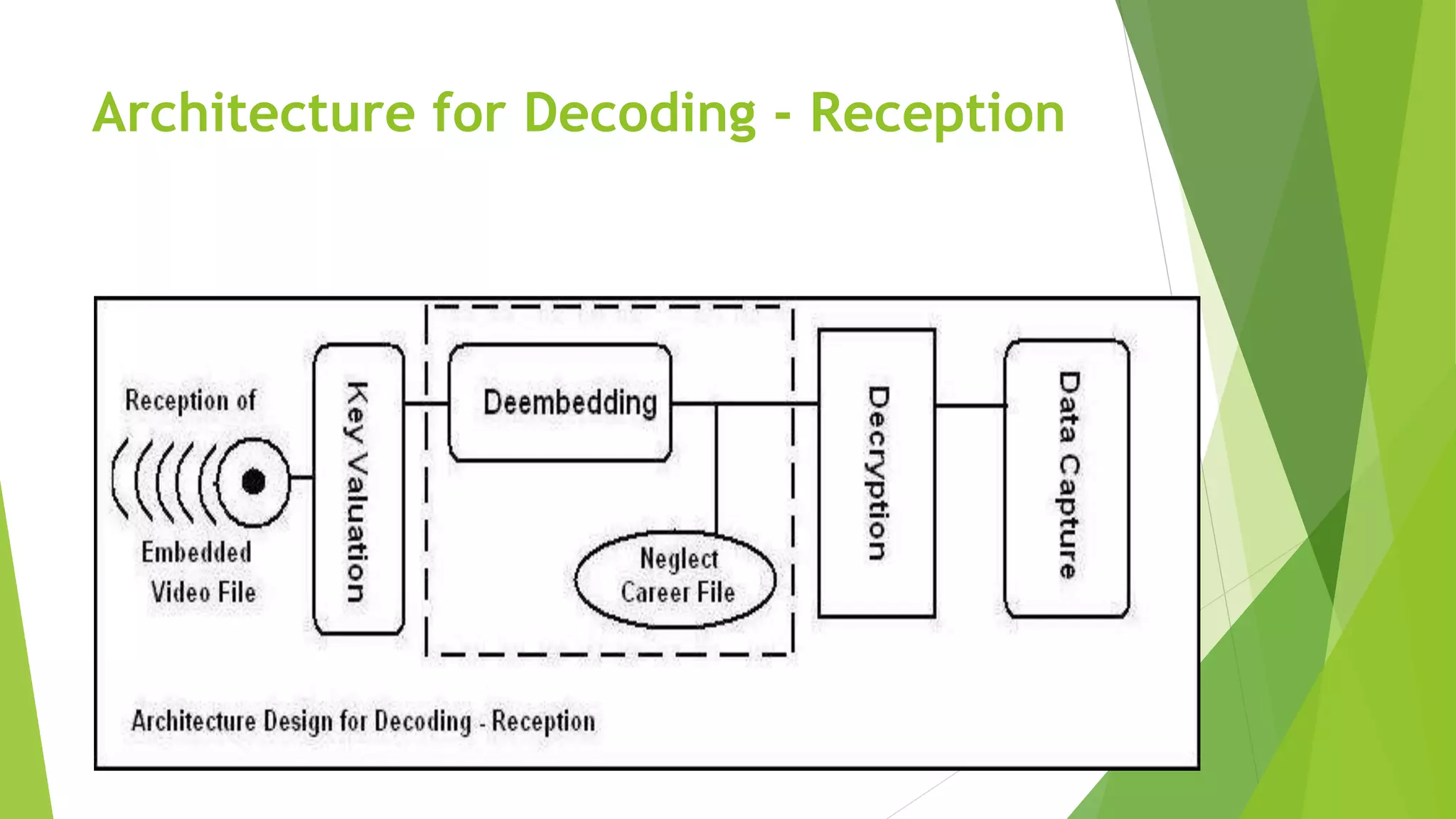
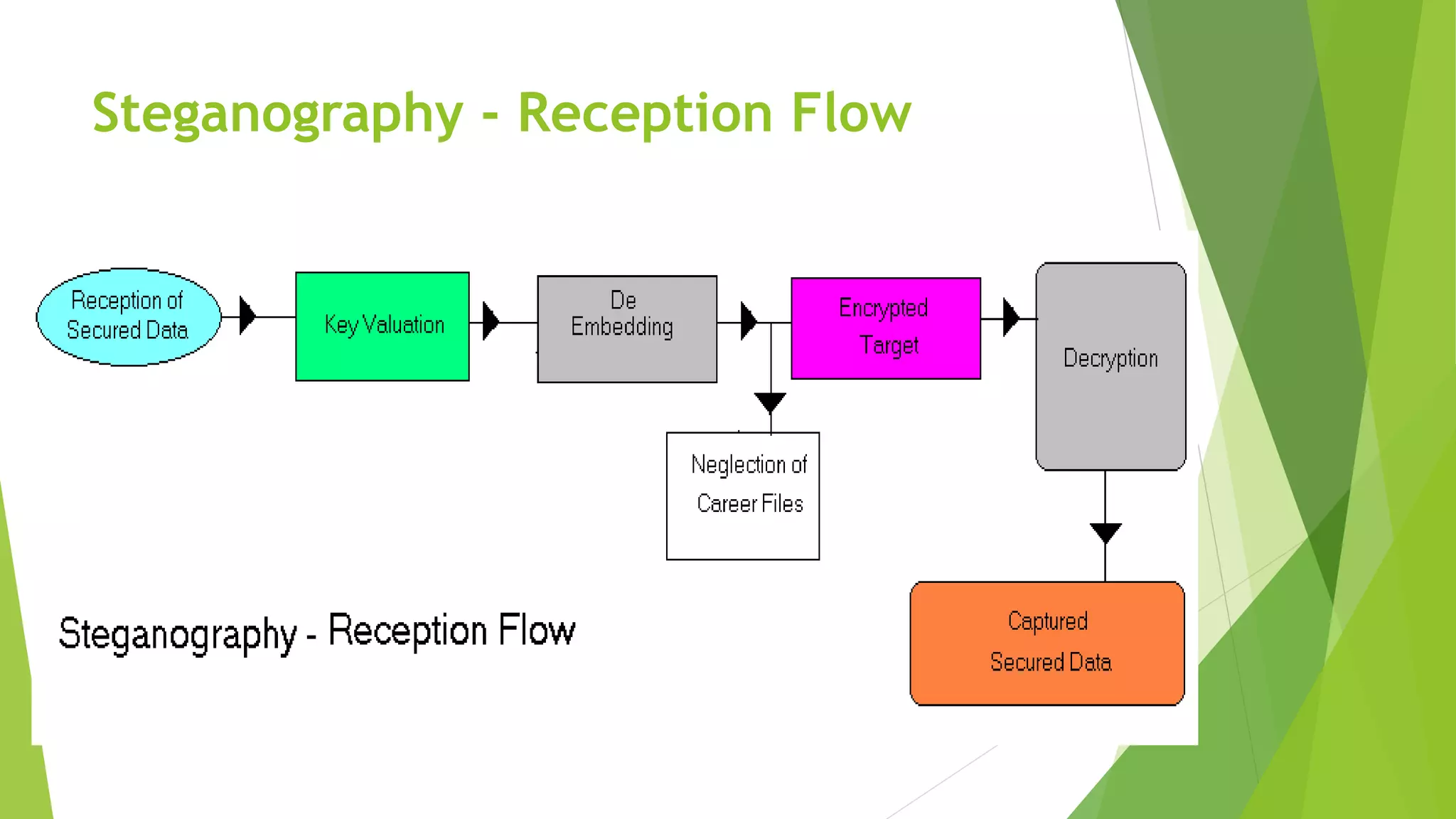
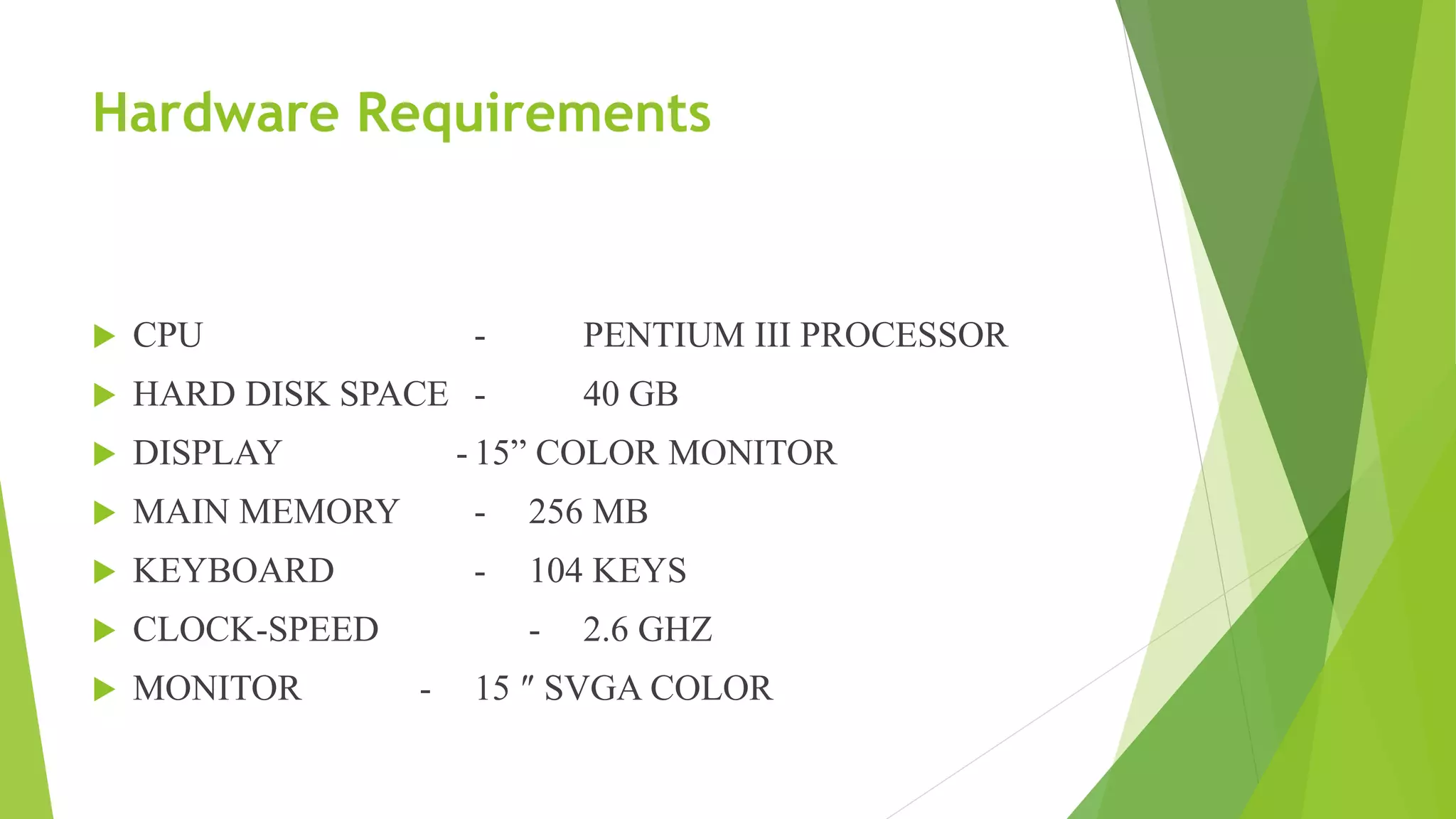
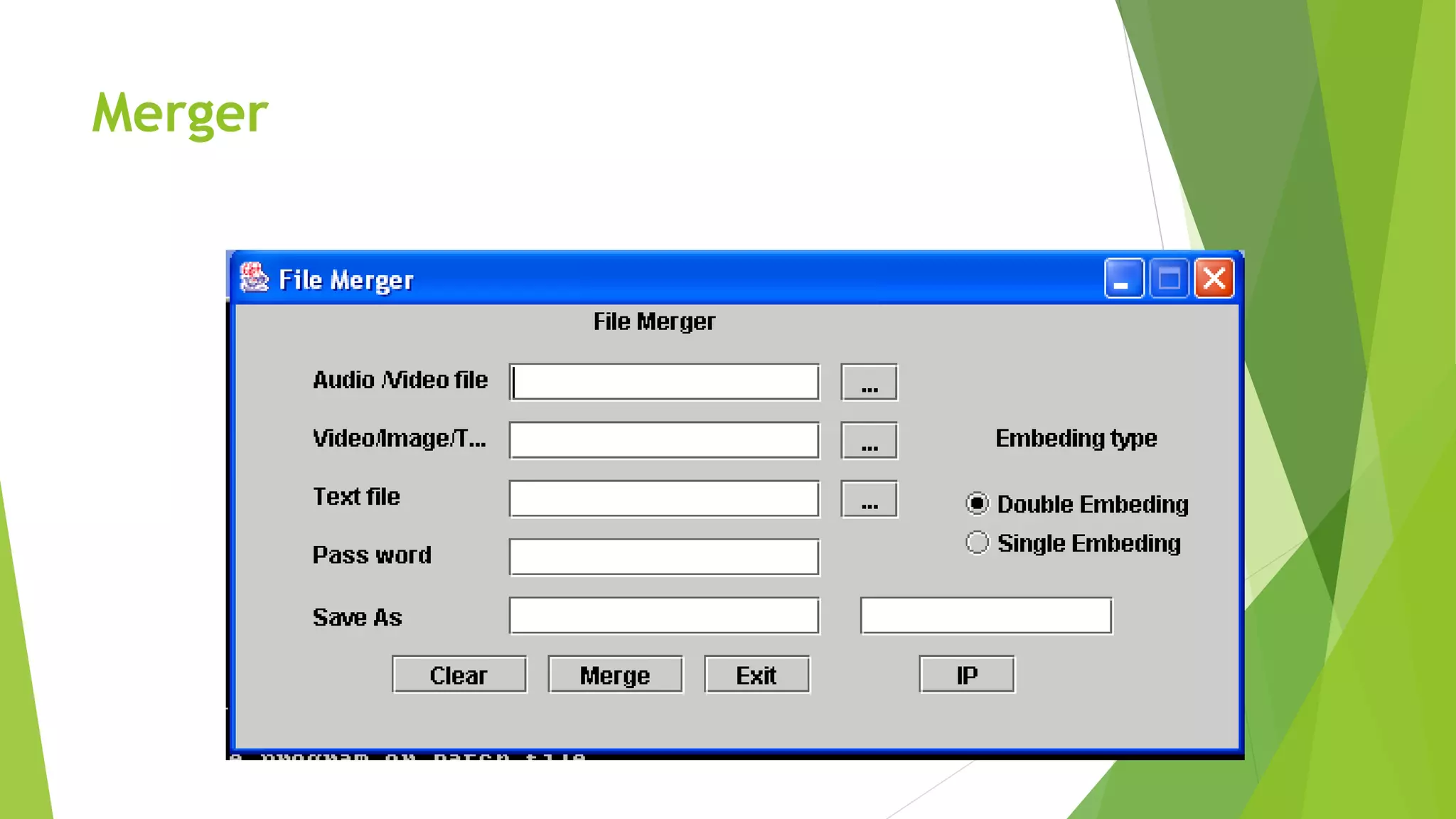
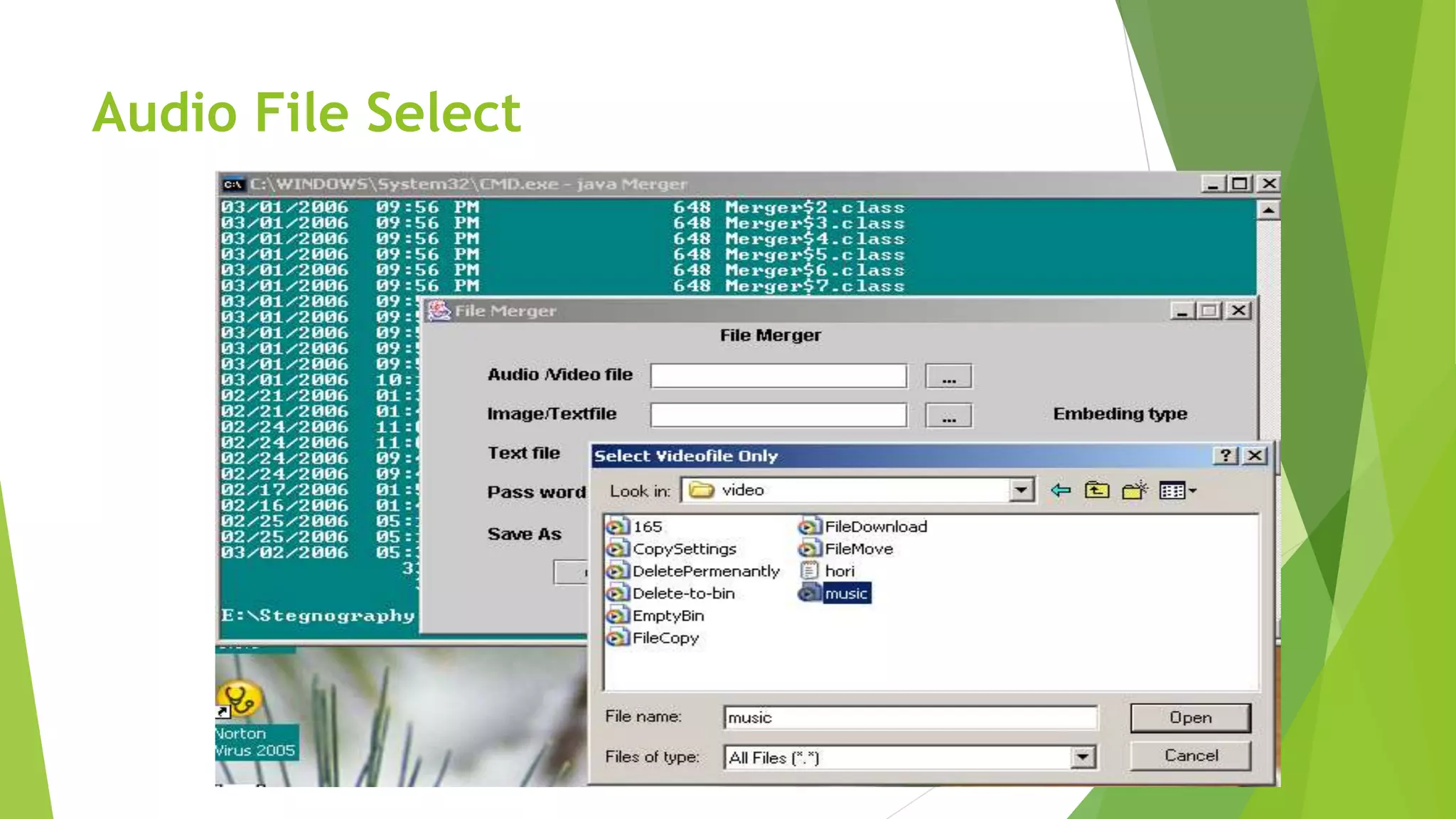
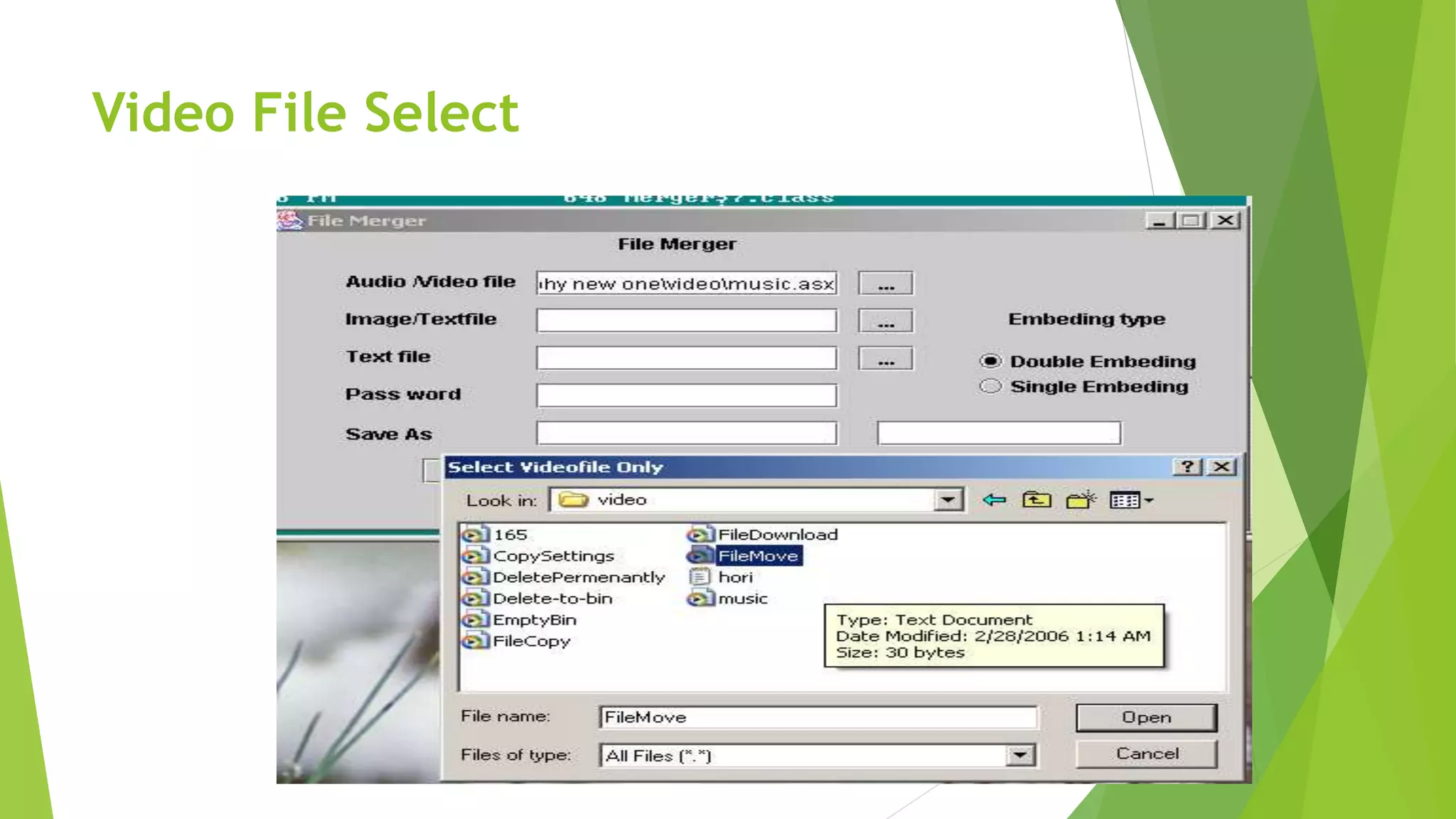
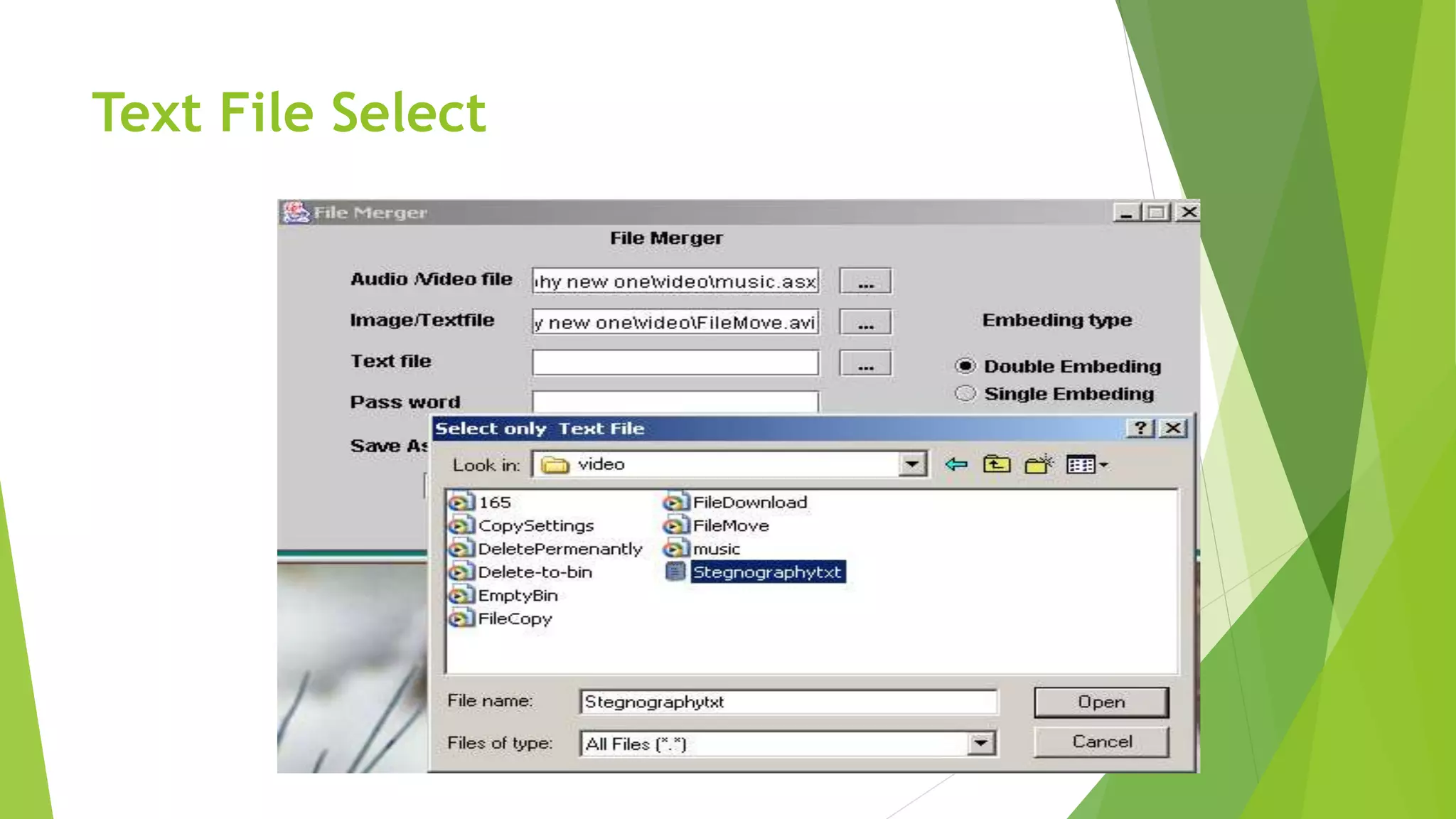
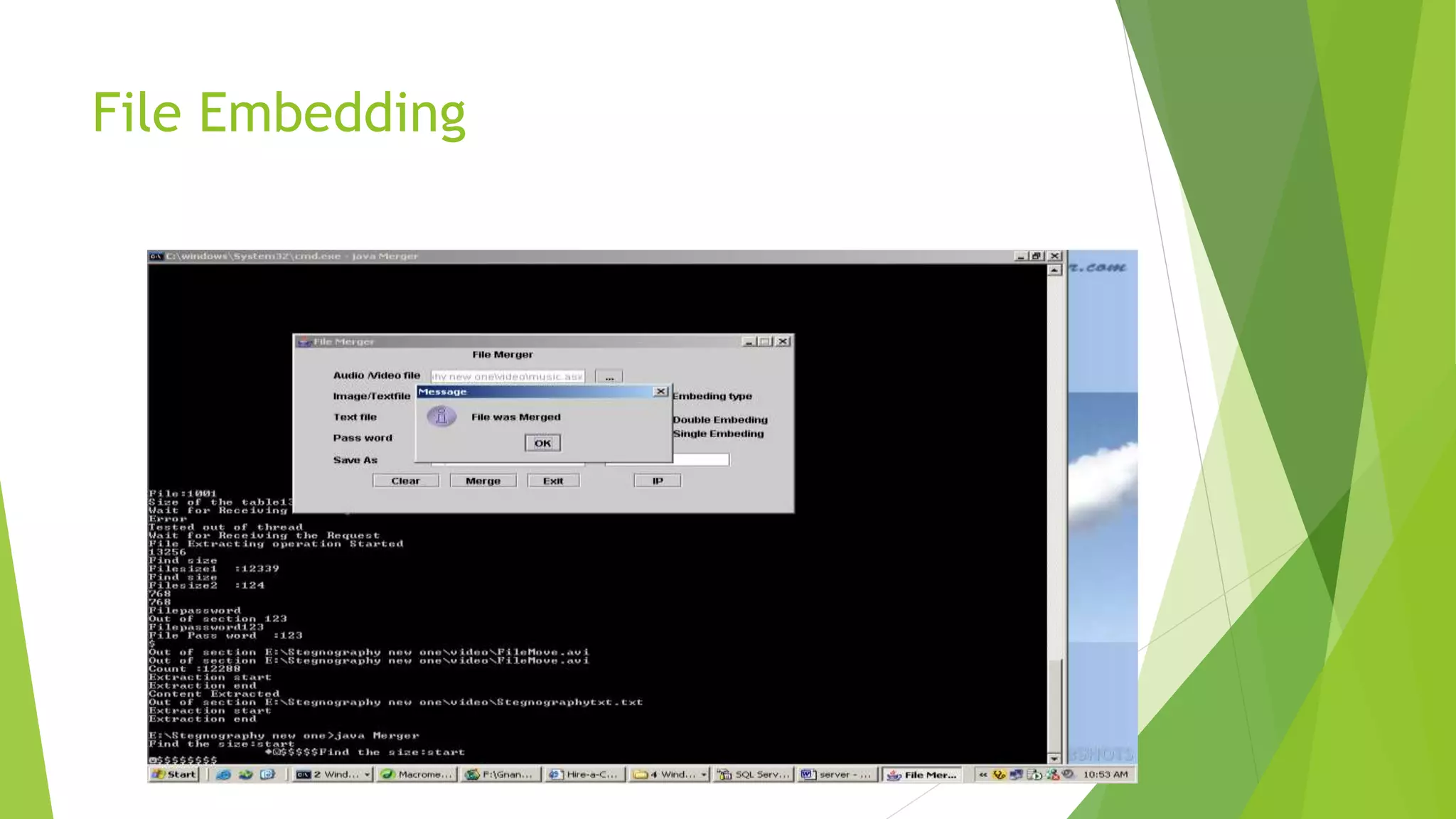
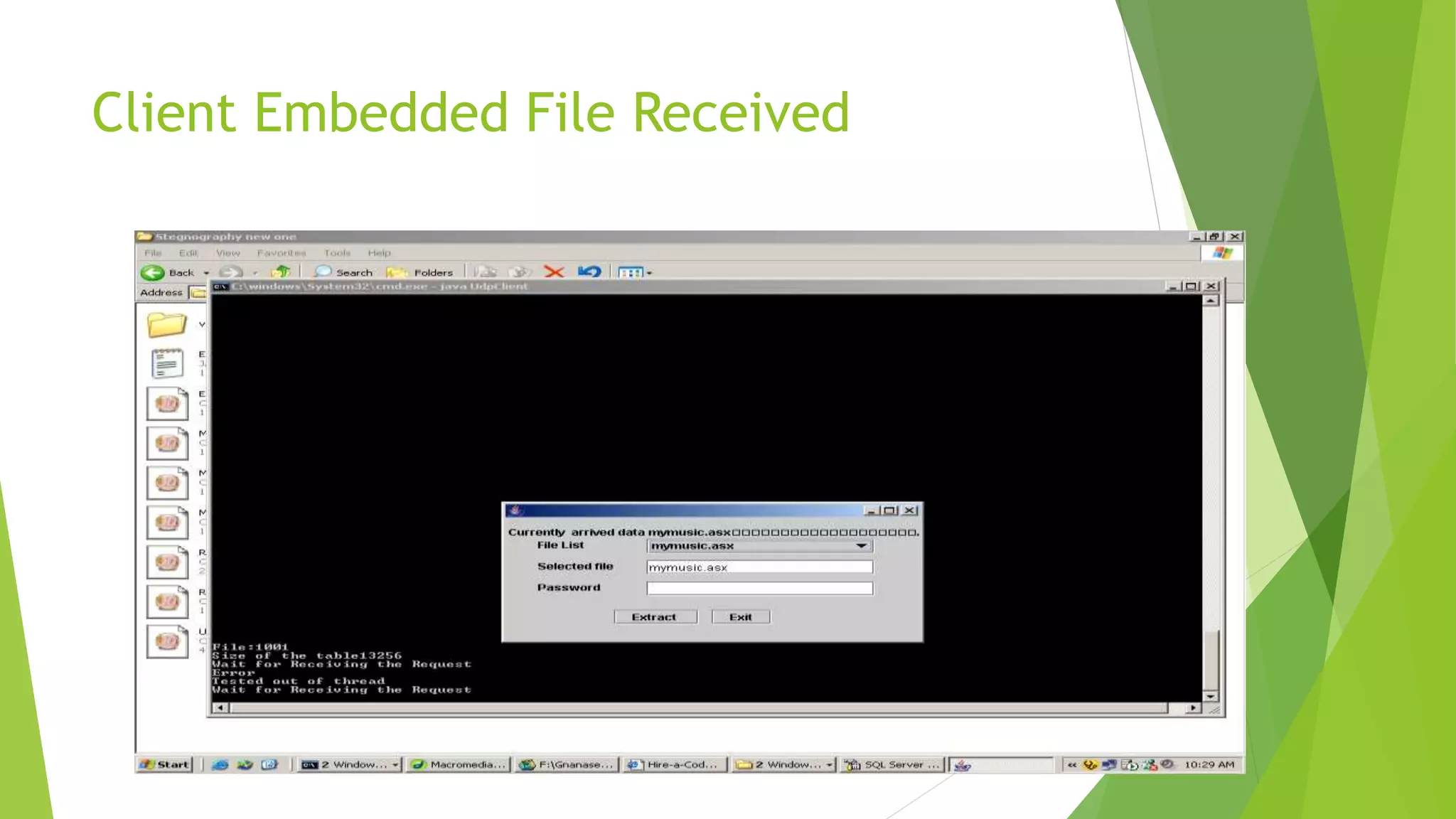
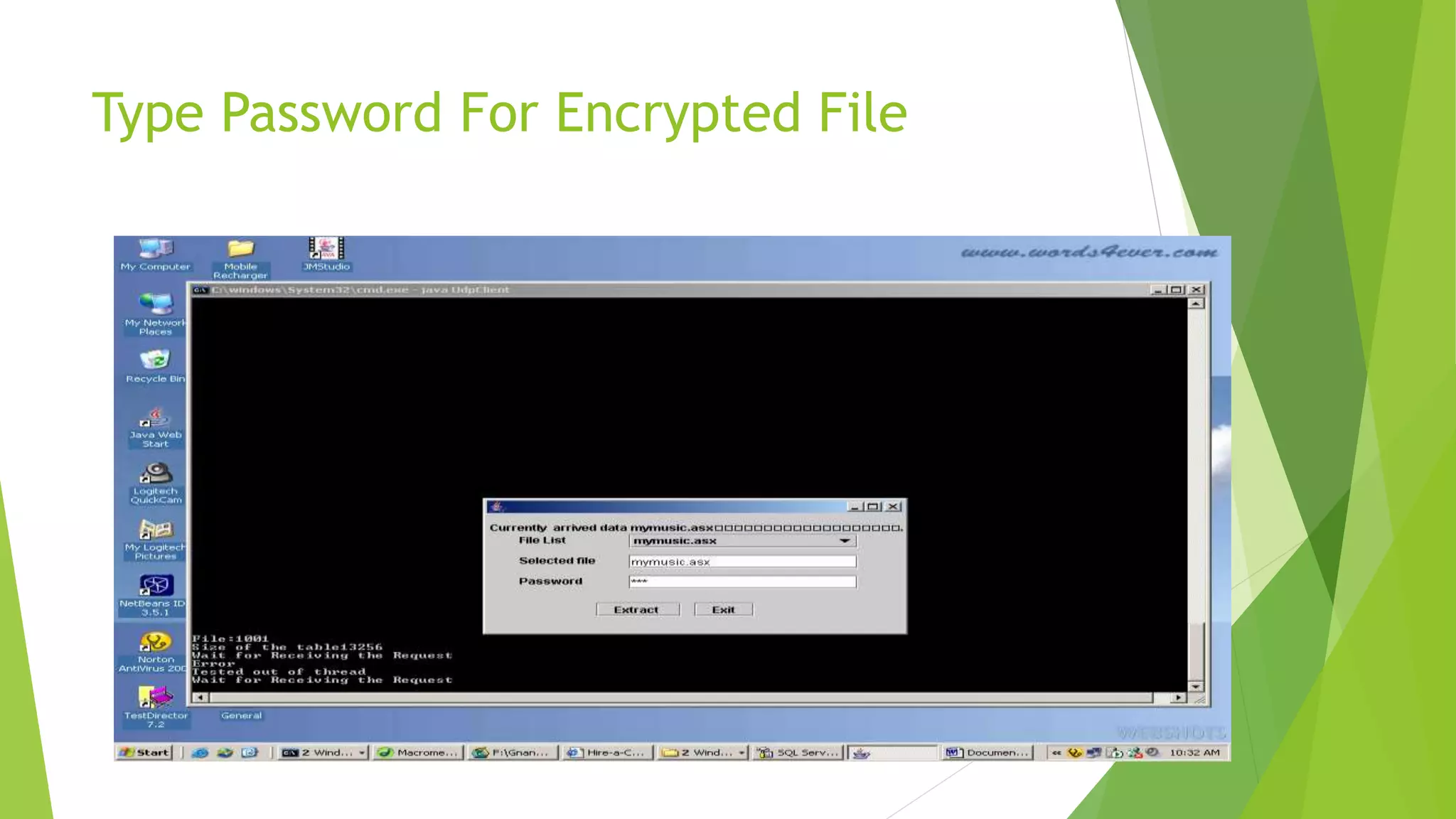
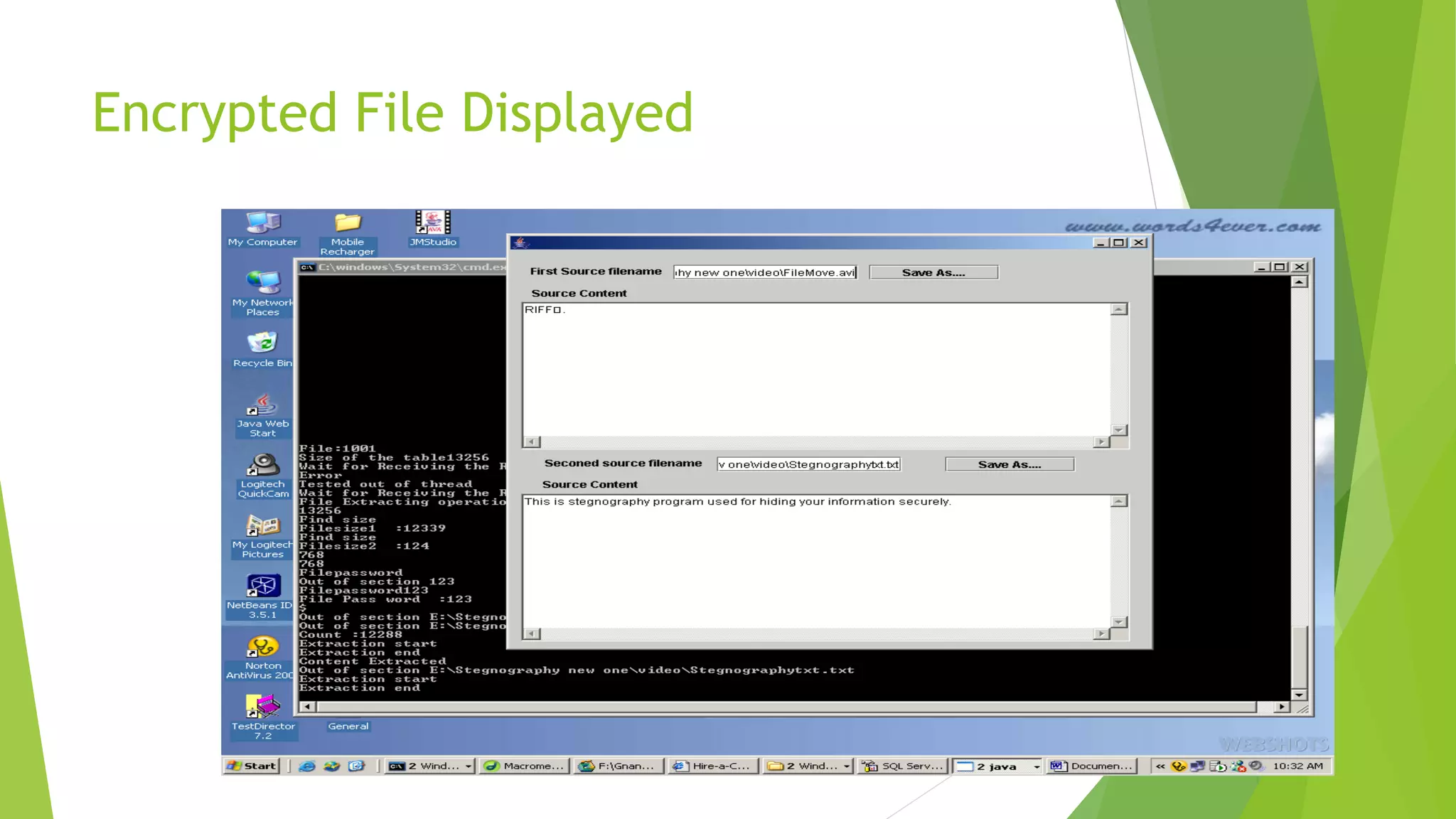
The document describes a security system utilizing steganography for secure file transmission over networks by embedding encrypted files within audio or video files. It proposes a novel algorithm called bit-shift for encryption and aims to enhance security with double embedding and password protection. The system's architecture comprises various modules for file merging, transmission, extraction, and displaying results, ensuring greater security than traditional encryption methods.