1. The document discusses various myths and misconceptions around cookie security, focusing on the 'Secure', 'HttpOnly', 'Path', and 'Domain' cookie attributes.
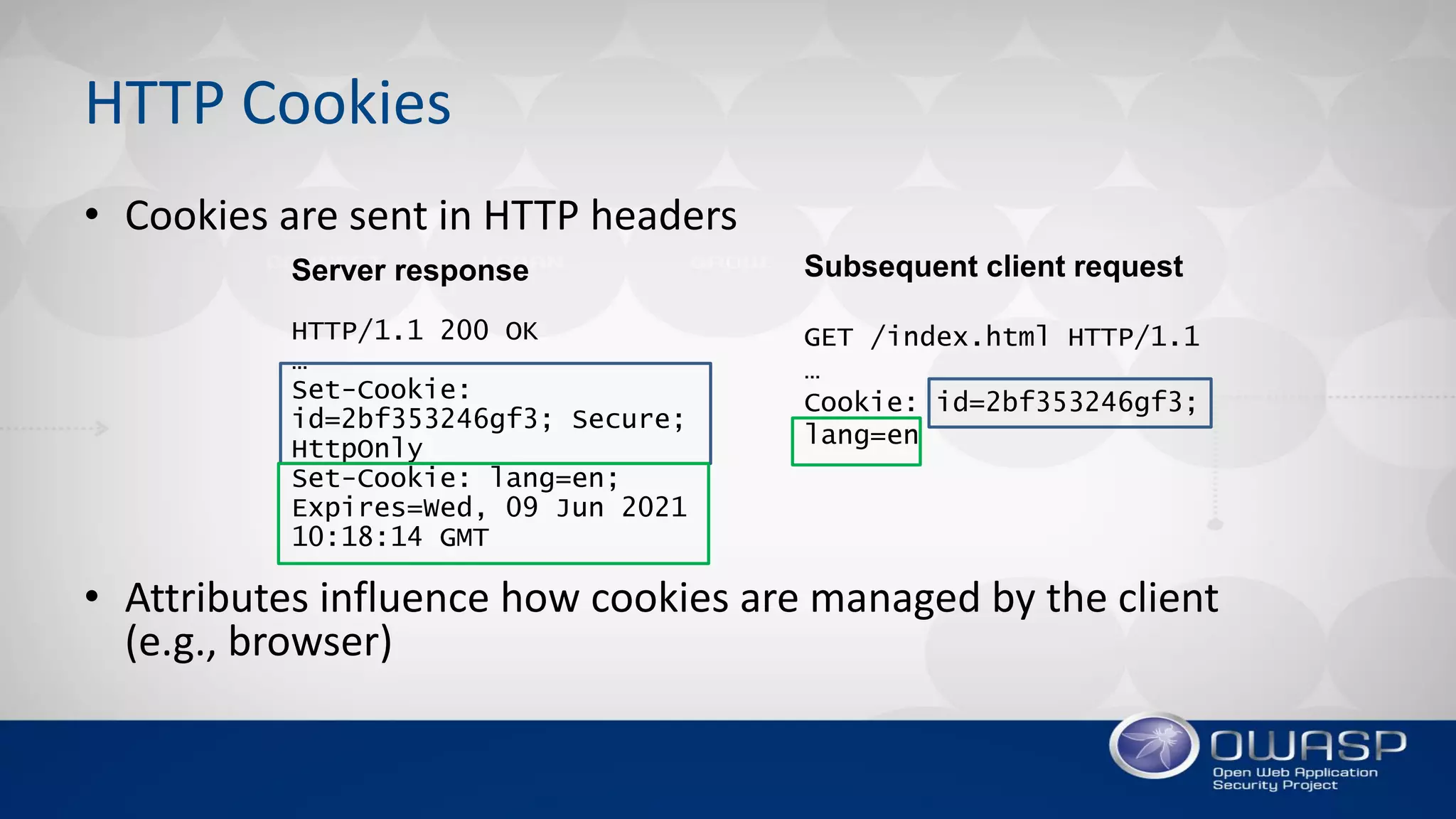
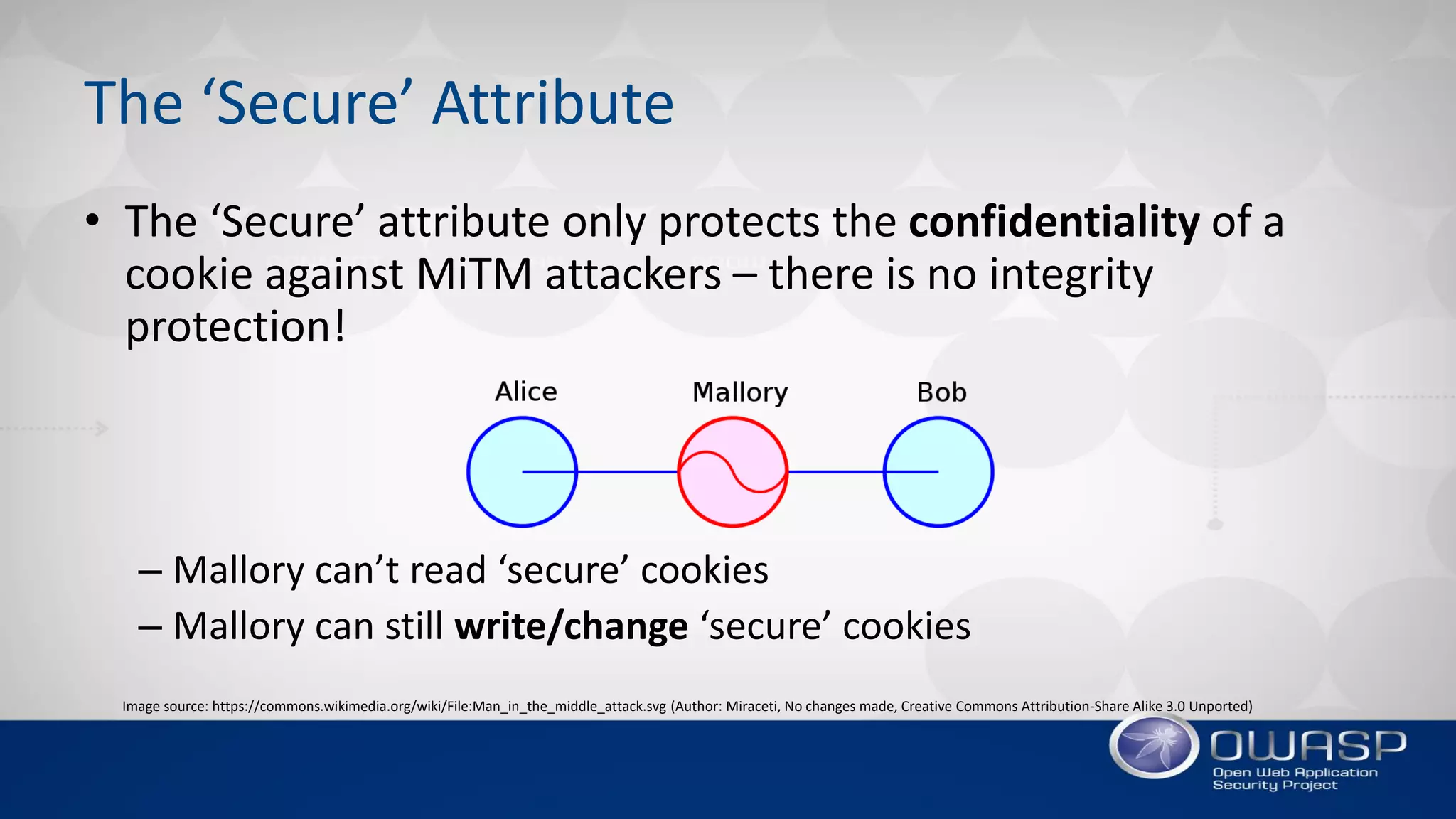
2. While attributes like 'Secure' and 'HttpOnly' provide some protections, they have limitations and weaknesses that can be exploited. For example, 'Secure' only protects confidentiality, not integrity, while 'HttpOnly' can be bypassed through JavaScript.
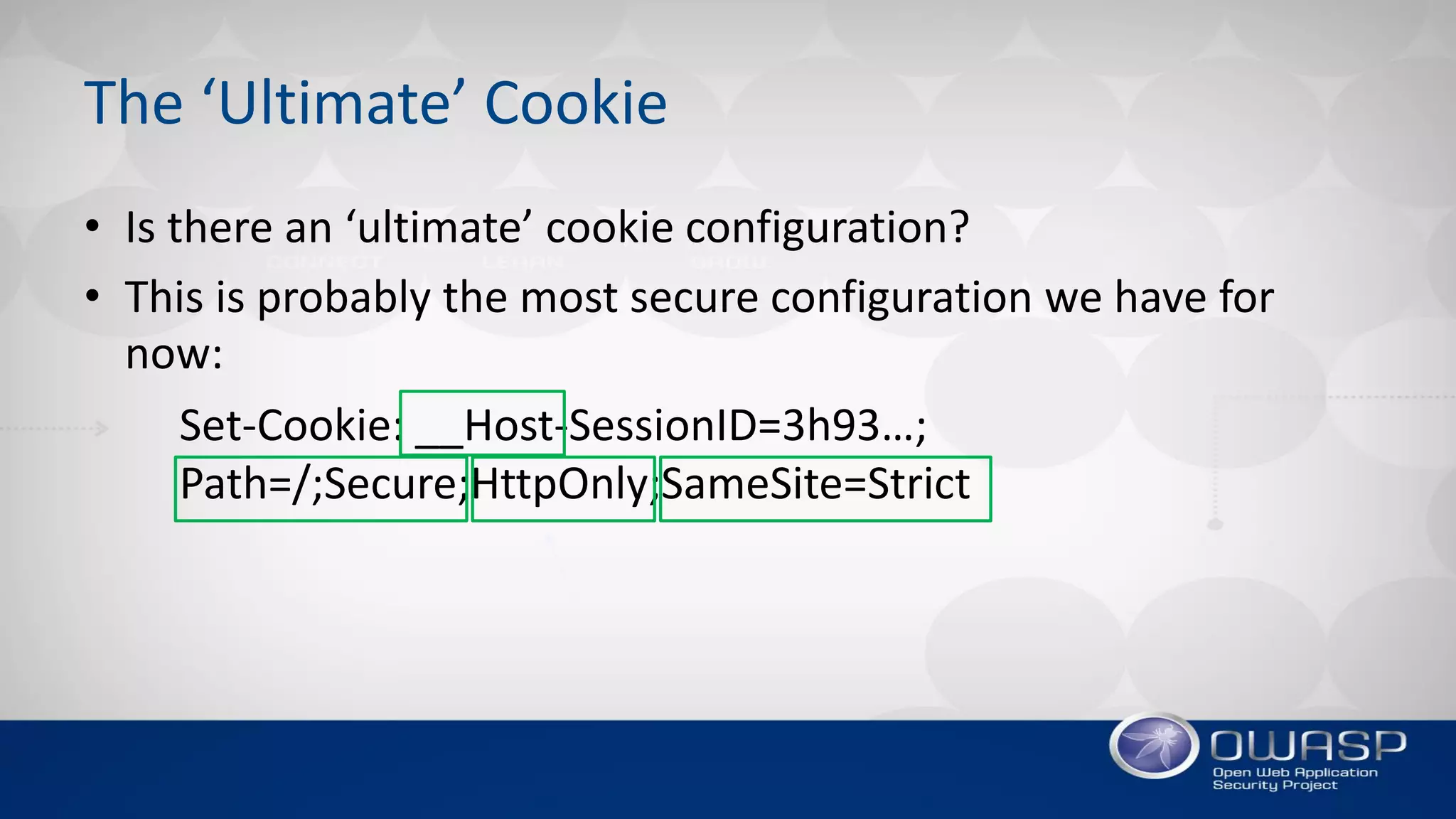
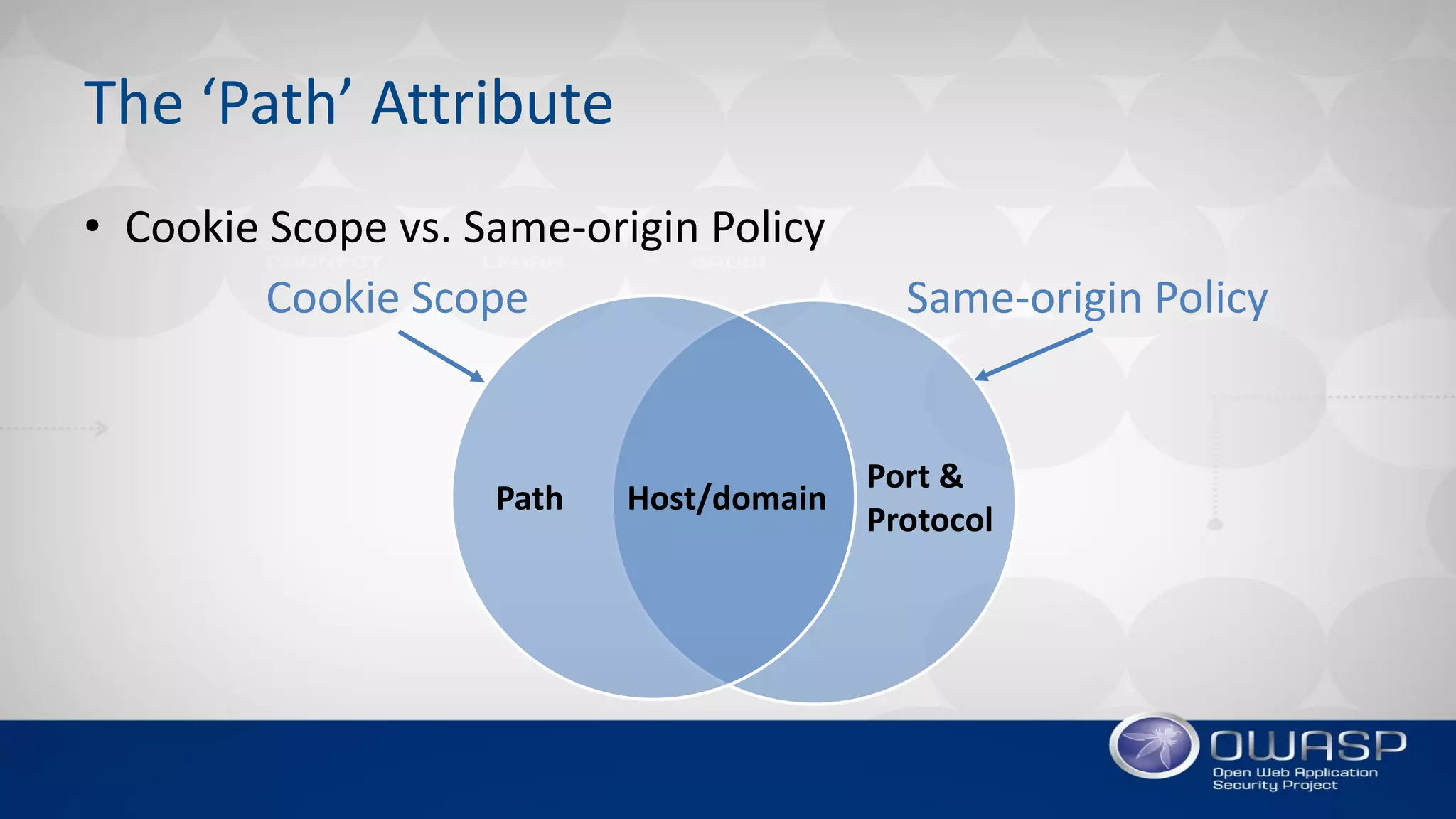
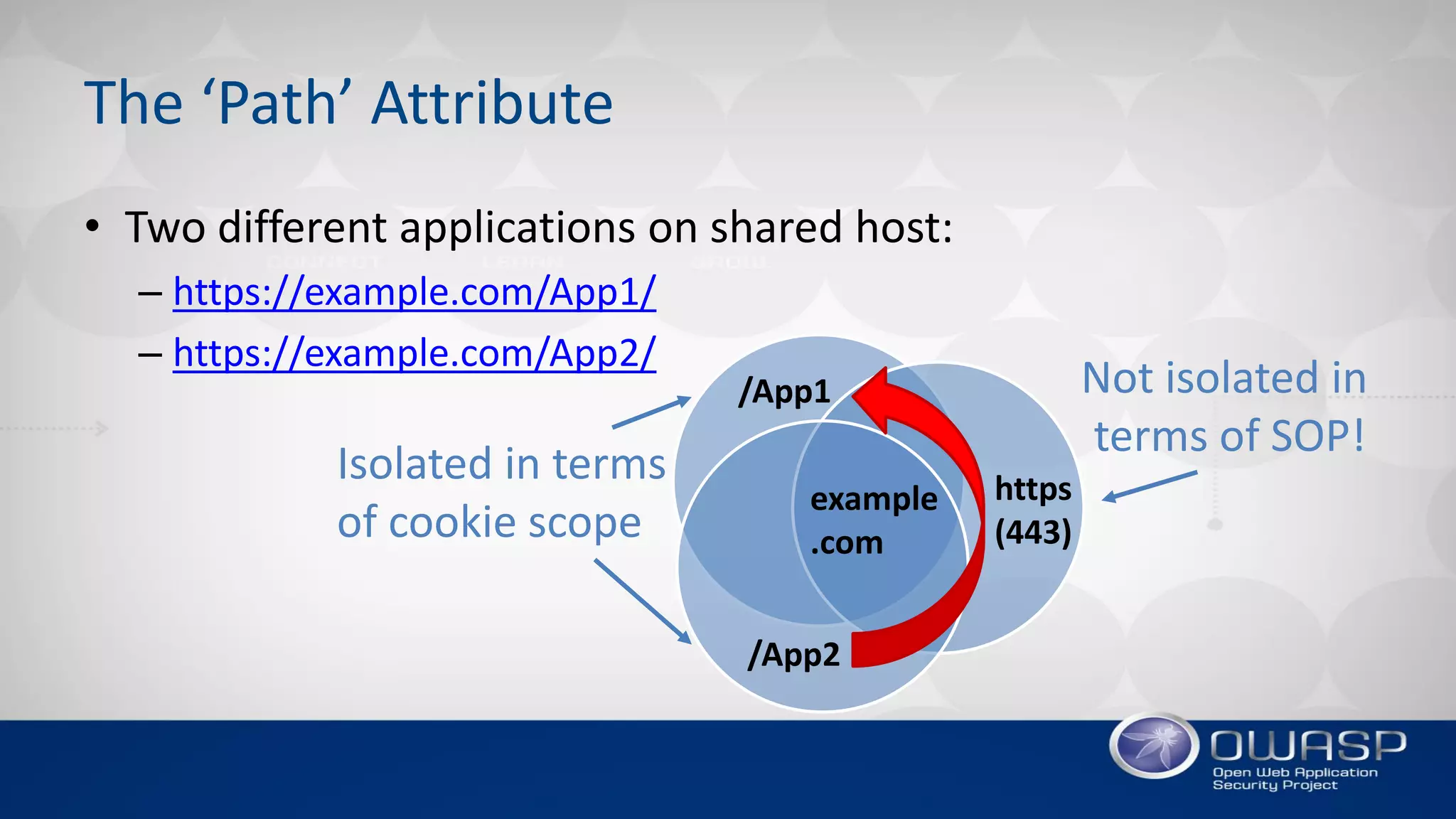
3. The document recommends using the strictest cookie settings possible, like limiting the cookie domain and path, using short expiration times, and taking advantage of new protections in RFC6265bis such as 'SameSite' and cookie prefixes.
























![The ‘SameSite’ Attribute
• Problem:
– Cookies are sent with all requests to a server, regardless of request
origin
– Attackers can abuse this by initiating authenticated cross-origin
requests, e.g., CSRF, XSSI, etc.
• Solution:
– New cookie attribute SameSite=[Strict|Lax]
– Prevents cookies from being attached to cross-origin requests](https://image.slidesharecdn.com/appsecusa2017davidjohansson-cookiesecuritymythsandmisconcepti-171002212453/75/OWASP-AppSec-USA-2017-Cookie-Security-Myths-and-Misconceptions-by-David-Johansson-29-2048.jpg)