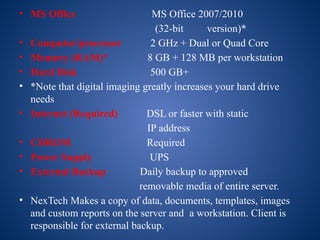
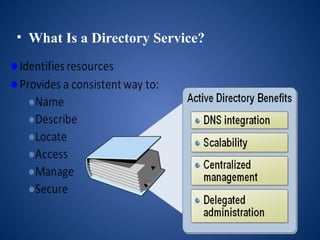
The document outlines the configuration and administration of server-based and peer-to-peer networks, detailing their components and advantages/disadvantages. Server-based networks are preferred for larger organizations due to centralized control and security, while peer-to-peer networks are cost-effective for smaller setups without specialized servers. Additionally, it provides technical specifications for terminal servers and client stations, as well as an overview of Active Directory and the DNS resolution process.