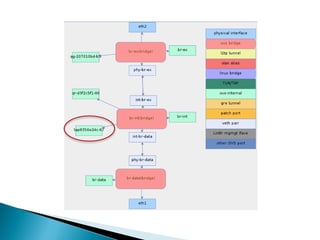
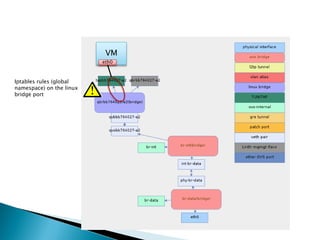
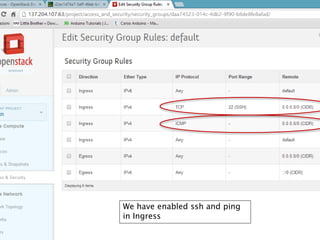
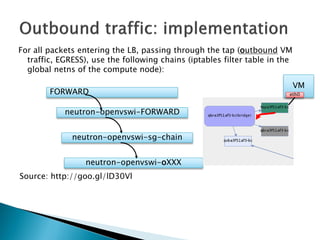
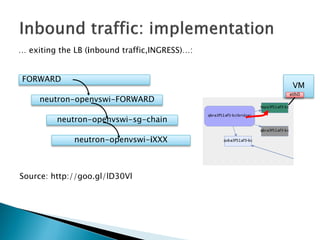
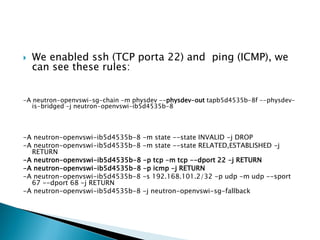
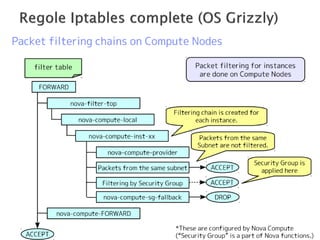
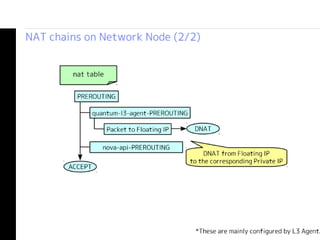
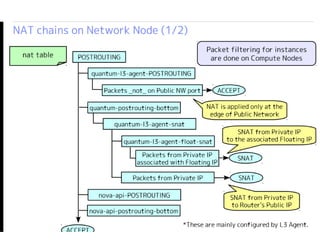
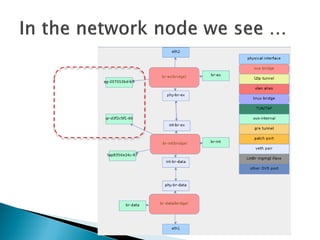
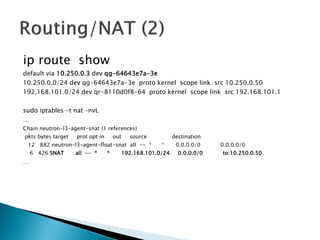
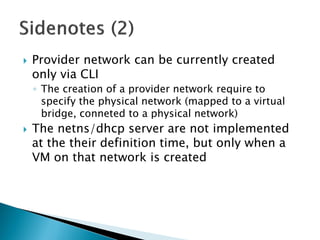
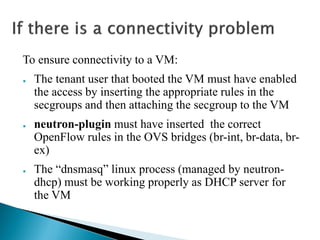
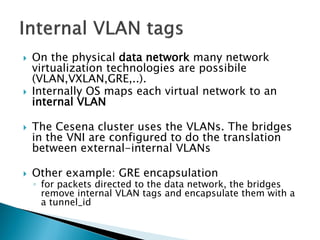
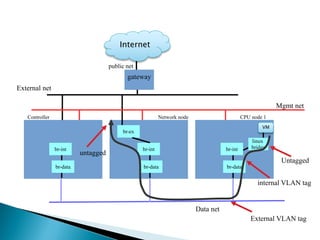
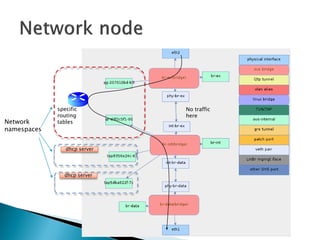
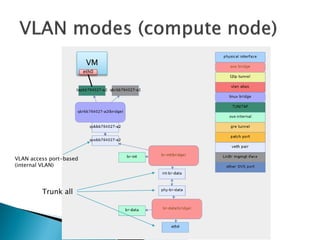
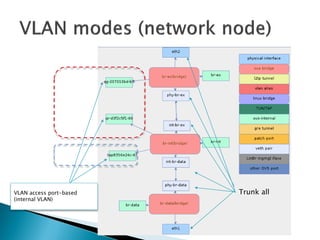
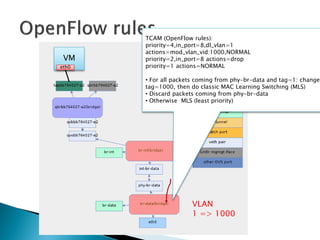
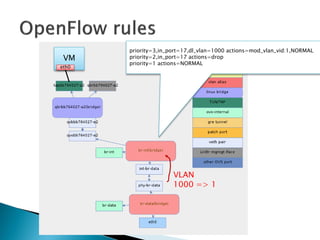
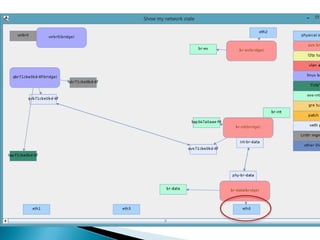
The document details the internal architecture and operations of network virtualization technologies used in a cloud environment, specifically focusing on VLANs, packet captures, security groups, and routing during VM creation. It describes components created during VM and router creation, their internal mappings, and the related configurations for firewall rules implemented by security groups. Additionally, it outlines various network configurations such as the creation of provider networks, DHCP functions, and OpenFlow rules for efficient data transmission within virtualized environments.


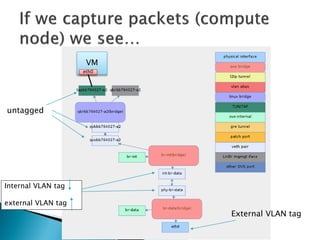
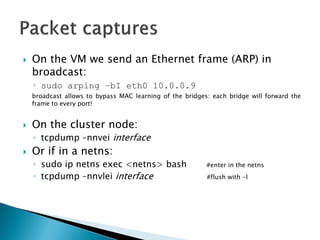

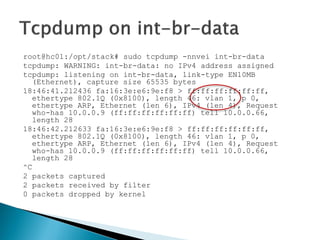
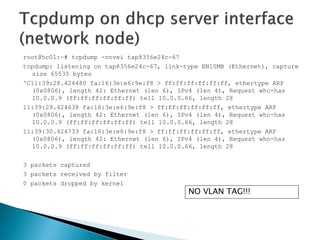
![root@hc01:/opt/stack#sudo tcpdump-nnveieth0
tcpdump: WARNING: eth0: no IPv4 addressassigned
tcpdump: listeningon eth0, link-typeEN10MB (Ethernet), capturesize65535 bytes
18:49:57.241431 fa:16:3e:e6:9e:f8 > ff:ff:ff:ff:ff:ff, ethertype802.1Q (0x8100), length46: vlan1000, p 0, ethertypeARP, Ethernet (len6), IPv4 (len4), Requestwho-has10.0.0.9 (ff:ff:ff:ff:ff:ff) tell10.0.0.66, length28
18:49:58.020910 d0:7e:28:90:d9:4b > 01:80:c2:00:00:00, 802.3, length64: LLC, dsapSTP (0x42) Individual, ssapSTP (0x42) Command, ctrl0x03: STP 802.1w, RapidSTP, Flags[Forward], bridge-id8000.d0:7e:28:90:d9:3d.800d, length47
message-age0.00s, max-age20.00s, hello-time2.00s, forwarding-delay15.00s
root-id8000.d0:7e:28:90:d9:3d, root-pathcost0, port-roleDesignated
18:49:58.241620 fa:16:3e:e6:9e:f8 > ff:ff:ff:ff:ff:ff, ethertype802.1Q (0x8100), length46: vlan1000, p 0, ethertypeARP, Ethernet (len6), IPv4 (len4), Requestwho-has10.0.0.9 (ff:ff:ff:ff:ff:ff) tell10.0.0.66, length28
^C
3 packetscaptured
3 packetsreceivedbyfilter
0 packetsdroppedbykernel](https://image.slidesharecdn.com/openstackadvancedpart-141104104601-conversion-gate01/85/Open-stack-advanced_part-21-320.jpg)