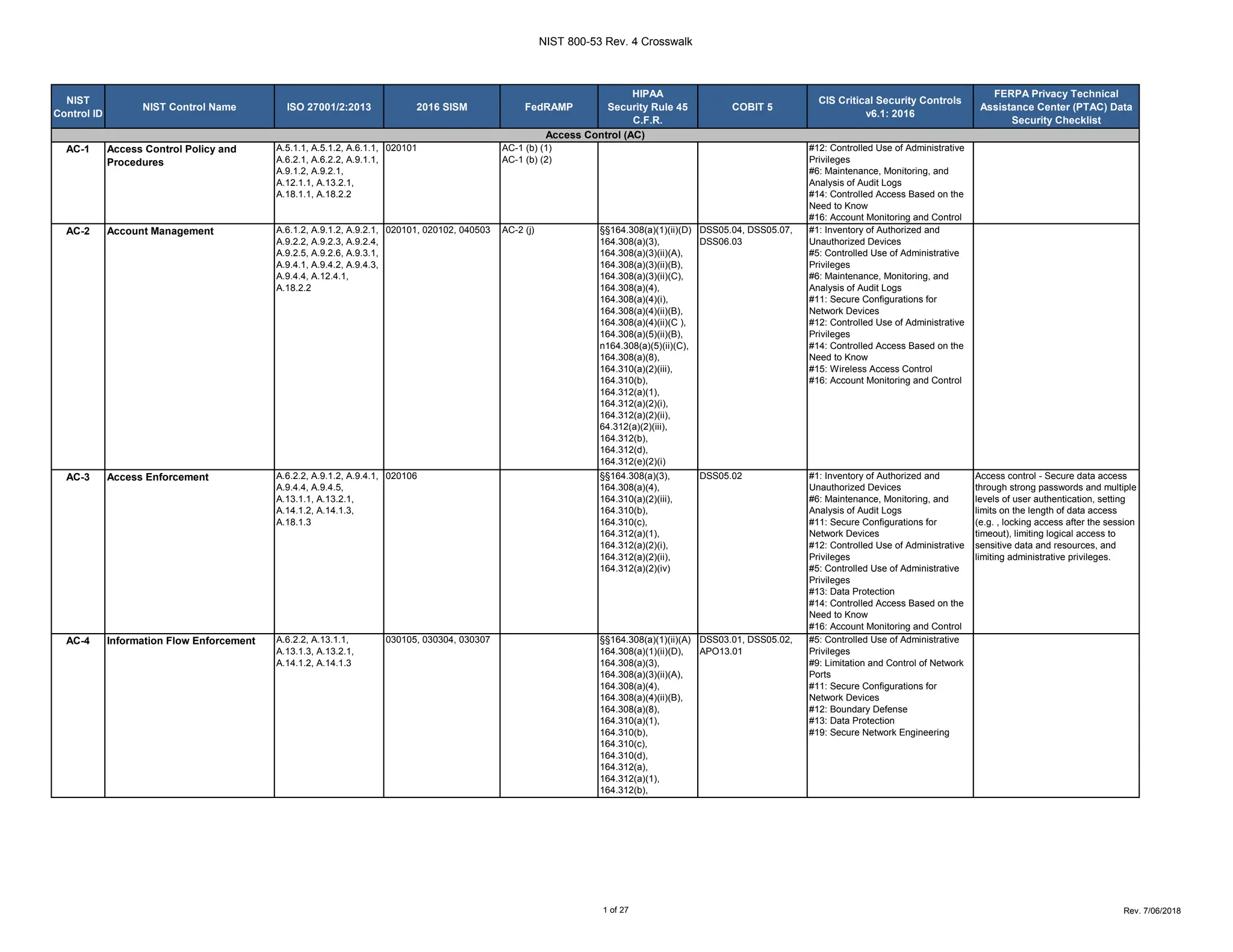
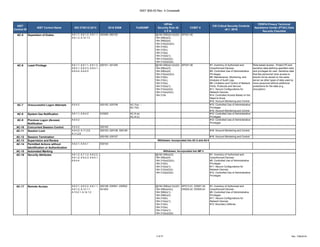
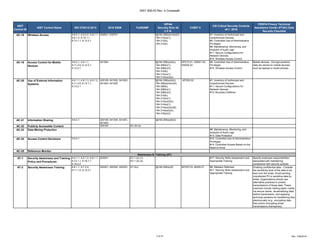
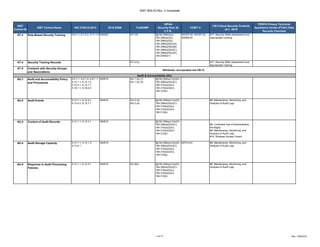
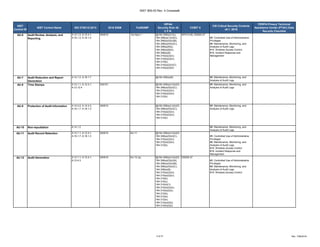
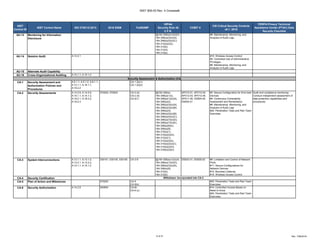
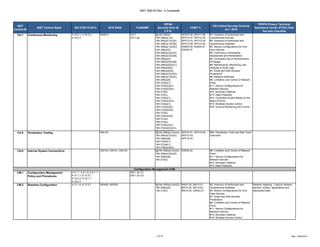
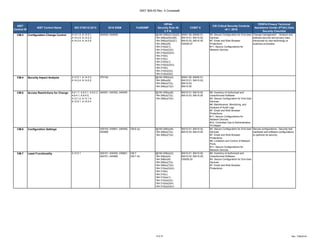
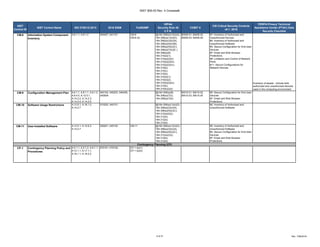
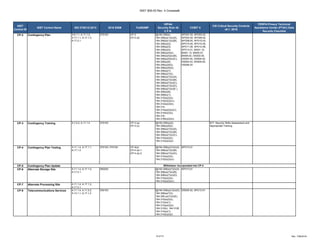
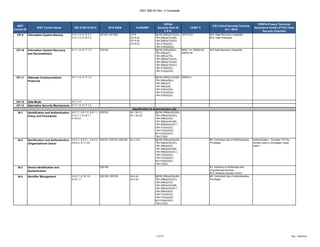
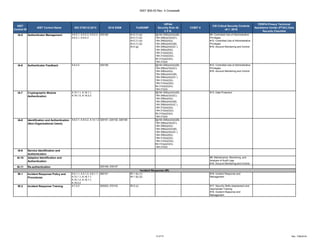
The document outlines a crosswalk of NIST 800-53 Rev. 4 controls against various standards and regulations such as ISO 27001, HIPAA, and COBIT. It details specific controls related to access control, information security, and awareness training, providing references to relevant legal requirements and best practices. The crosswalk serves as a reference for organizations to align their security measures with multiple compliance frameworks.