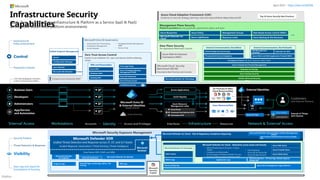
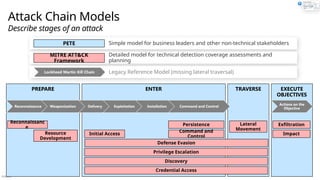
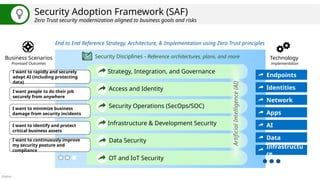
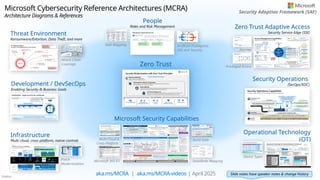
Microsoft Cybersecurity Reference Architectures (MCRA)Plan your end-to-end security architecture using Zero Trust principles
Overview of Security Adoption Framework and end to end cybersecurity architecture
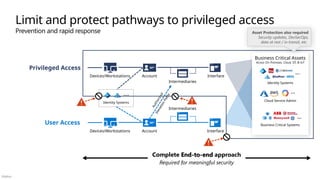
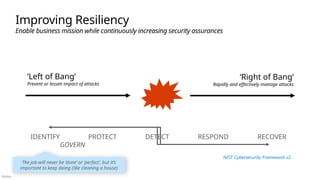
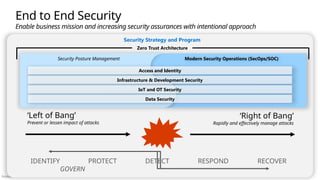
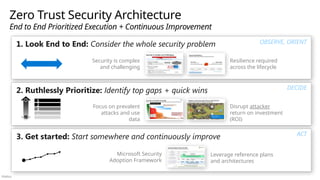
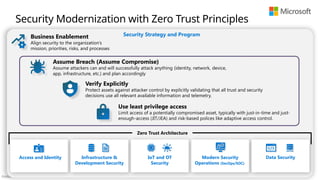
End to End Security: Consider the whole problem
Ruthlessly Prioritize: Identify top gaps + quick wins
Get started: Start somewhere & continuously improve
Antipatterns and best practices
Guiding rules and laws for security
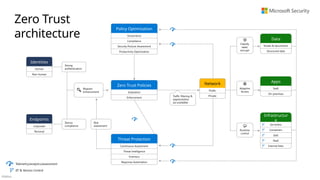
Diagrams and references�Applying Zero Trust principles
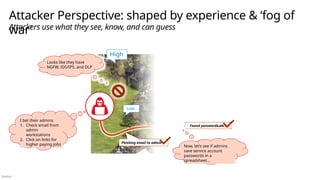
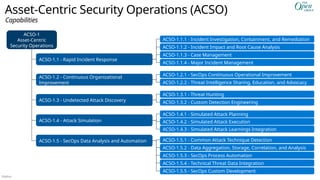
Top End to End Security Challenges
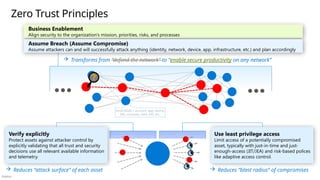
Incomplete or network-centric architectures aren’t agile & can’t keep up with continuous change (security threats, technology platform, and business requirements)
Challenges with
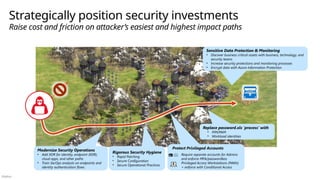
Creating integrated end to end architecture
Integrating security technologies
Planning and prioritizing security �modernization initiatives













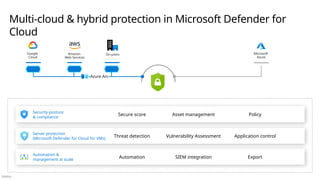
![Público
App &
Data
Teams
IoT Security
App Security / DevSecOps
Apps & Data
Data Security
People
Teams
Identity
Teams
IT Operations
Insider Risk
User Education & Awareness
People
Identity & Keys
Administrator
Security
Identity System
Security
Key Management
Endpoint
Security
Mitigate
Vulnerabilities
Infrastructure & Endpoint
Infrastructure &
Network Security
Deploy
Tools
OT Operations
Operational Technology (OT) Security
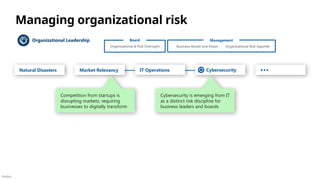
Leadership and Culture
Risk Management
Policy & Standards
Security Leadership
Information Risk Management
Supply Chain Risk (People, Process, Technology)
Enable Productivity and Security
Stay Agile - Adapt to changes to threat environment,
technology, regulations, business model, and more
Program Management Office (PMO)
Plan (Governance) Run (Operations)
Build
Managing Information/Cyber
Risk
Security responsibilities or “jobs to be done”
Organizational Leadership External
Intelligence Sources
April 2025 - https://aka.ms/SecurityRoles
Threat
Intelligence
Strategic Threat
Insight/Trends
Tactical Threat
Insight/Trends
Posture Management
Monitor & Remediate Risk
(Conditional Access, Secure Score, Sharing
Risks, Threat and Vulnerability Management
(TVM) User & Asset Scores, etc.)
Incident
Management
Incident
Response
Threat
Hunting
Security
Operations
[Center]
(SOC)
Practice
Exercises
Risk
Scenarios
Incident
Preparation
Technical Policy
Authoring
Compliance
Reporting
Architecture &
Risk Assessments
Technical Policy
Monitoring
Privacy &
Compliance
Requirements
Compliance
Management
Requirements
Translation
Technical Risk Management
Security
Architecture
Organizational & Risk Oversight
Board Management
Organizational Risk Appetite
Business Model and Vision](https://image.slidesharecdn.com/mcra-april-2025-250819192426-181b2221/85/MicrosoftCybserSecurityReferenceArchitecture-April-2025-pptx-42-320.jpg)
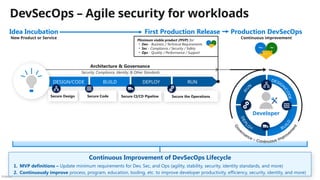
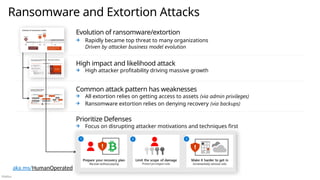
![Público
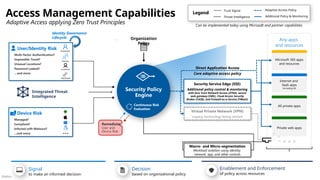
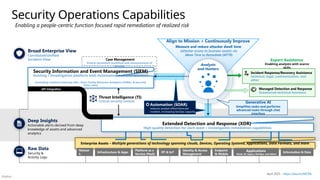
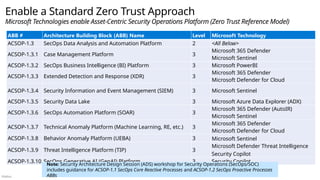
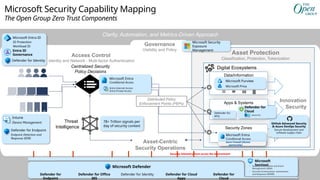
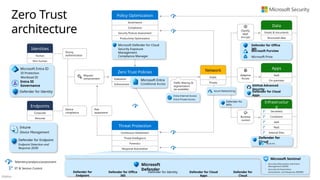
Microsoft security capability mapping
Which roles typically use which capabilities
Access Control Asset Protection
Security Governance
Security Operations
Establish Zero Trust access model to modern and
legacy assets using identity & network controls
Detect, Respond, and Recover from attacks;
Hunt for hidden threats; share threat intelligence
broadly
Protect sensitive data and systems. Continuously
discover, classify & secure assets
Continuously Identify, measure, and manage security
posture to reduce risk & maintain compliance
Identity Admin, Identity Architect,
Identity Security
• Entra ID (Formerly Azure AD)
• Multifactor Authentication
• Conditional Access
• Application Proxy
• External Identities / B2B & B2C
• Internet/Private Access
• Identity Governance
• and more..
• Windows Hello for Business
• Microsoft 365 Defender
• Microsoft Defender for Identity
• Microsoft Defender for Cloud Apps
• Azure Bastion
• Azure Administrative Model
• Portal, Management Groups, Subscriptions
• Azure RBAC & ABAC
Network Security
• Azure Firewall
• Azure Firewall Manager
• Azure DDoS
• Azure Web Application Firewall
• Azure Networking Design
• Virtual Network, NSG, ASG, VPN, etc.
• PrivateLink / Private EndPoint
Endpoint / Device Admin
• Microsoft Intune
• Configuration Management
• Microsoft Defender for Endpoint
Data security
• Microsoft Purview
• Information Protection
• Data Loss Prevention
• Microsoft 365 Defender
• Microsoft Defender for Cloud Apps
People security
• Attack Simulator
• Insider Risk Management
Security architecture
• Microsoft Cybersecurity Reference Architecture
https://aka.ms/MCRA
Microsoft
Entra
• Microsoft 365 Lighthouse
• Azure Lighthouse
[multi-tenant]
Security Operations Analyst
Microsoft Defender XDR
• Microsoft Defender for Endpoint
• Microsoft Defender for Office 365
• Microsoft Defender for Identity
• Microsoft Defender for Cloud Apps
• Microsoft Entra Identity Protection
• Microsoft Defender for Cloud
• Microsoft Defender for DevOps
• Microsoft Defender for Servers
• Microsoft Defender for Storage
• Microsoft Defender for SQL
• Microsoft Defender for Containers
• Microsoft Defender for App Service
• Microsoft Defender for APIs
• Microsoft Defender for Key Vault
• Microsoft Defender for DNS
• Microsoft Defender for open-source
relational databases
• Microsoft Defender for Azure
Cosmos DB
• Microsoft Security Copilot
• Microsoft Sentinel
• Microsoft Security Experts
• Microsoft Incident Response
Detection and Response Team (DART)
Posture management,
Policy and standards,
Compliance management
• Microsoft Defender for Cloud
• Secure Score
• Compliance Dashboard
• Azure Security Benchmark
• Azure Blueprints
• Azure Policy
• Microsoft Defender External Attack
Surface Management (MD-EASM)
• Azure Administrative Model
• Portal, Management Groups, Subscriptions
• Azure RBAC & ABAC
• Microsoft Purview
• Compliance manager
Microsoft
Purview
Microsoft
Defender
Innovation Security
Integrate Security into DevSecOps
processes. Align security, development,
and operations practices.
Application security and DevSecOps
• (Same as Infrastructure Roles)
• GitHub Advanced Security
• Azure DevOps Security
Infrastructure and endpoint security,
IT Ops, DevOps
• Microsoft Defender for Cloud
(including Azure Arc)
• Azure Blueprints
• Azure Policy
• Azure Firewall
• Azure Monitor
• Azure Web Application Firewall
• Azure DDoS
• Azure Backup and Site Recovery
• Azure Networking Design
• Virtual Network, NSG, ASG, VPN, etc.
• PrivateLink / Private EndPoint
• Azure Resource Locks
Incident preparation
Threat intelligence Analyst
• Microsoft Defender Threat
Intelligence (Defender TI)
• Microsoft Sentinel
OT and IoT Security
• Microsoft Defender for IoT (& OT)
• Azure Sphere
Privacy Manager
• Microsoft Priva
April 2025 – https://aka.ms/MCRA](https://image.slidesharecdn.com/mcra-april-2025-250819192426-181b2221/85/MicrosoftCybserSecurityReferenceArchitecture-April-2025-pptx-43-320.jpg)


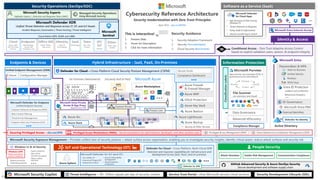
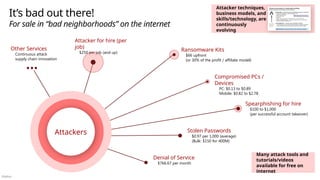
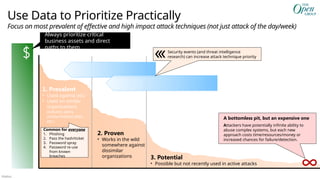
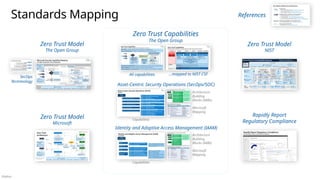
![Público
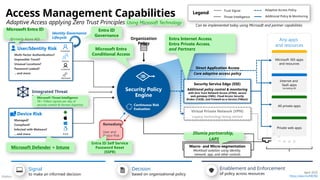
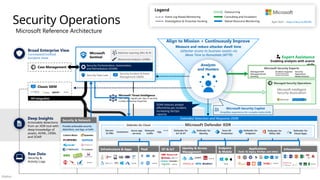
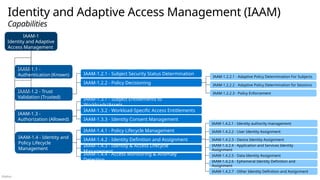
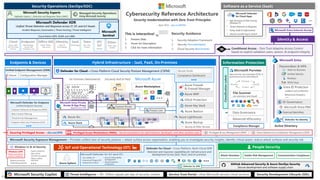
Cross-cloud and cross-platform
Comprehensive Security, Compliance and Identity capabilities that integrate with your existing solutions
CERTs / ISACs / Others
NIST / CIS / The Open Group / Others Solution Integration and MDR/MSSP Partners
Microsoft Intelligent Security Association Law Enforcement
Industry Partnerships
Microsoft Security, Compliance, and Identity Capabilities
Access Control
Identity and Network
Modern Security Operations
Rapid Resolution with XDR, SIEM, SOAR, UEBA and more
Asset Protection
Information Protection and App Security / DevSecOps
Technical Governance
Risk Visibility, Scoring, and Policy Enforcement
Threat Intelligence – 78+ Trillion signals per day of security context
People Security – User Education/Empowerment and Insider Threats
Security Operations [Center] (SOC) – Reduce attacker time/opportunity to impact business
Endpoints & Devices Hybrid Infrastructure – IaaS, PaaS, On-Premises
Software as a Service (SaaS)
S3
Operational Technology (OT)
IoT Devices
April 2025
https://aka.ms/MCRA](https://image.slidesharecdn.com/mcra-april-2025-250819192426-181b2221/85/MicrosoftCybserSecurityReferenceArchitecture-April-2025-pptx-48-320.jpg)
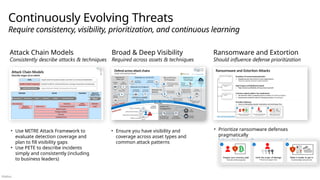
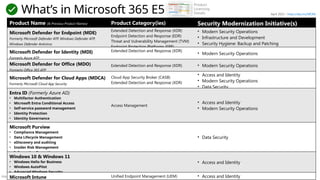
![Público
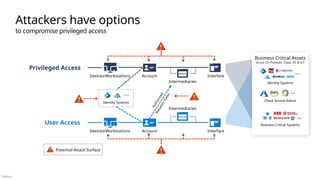
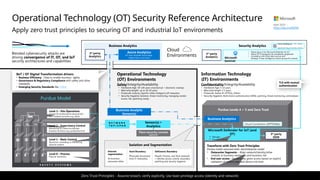
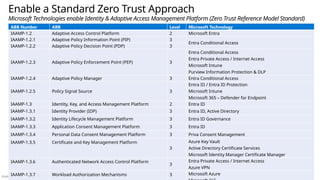
Multi-Cloud and Cross-Platform Technology
Secure the enterprise you have
Microsoft Purview
Discovery, Classify, Protect, and Monitor across unstructured data (documents, spreadsheets, files, etc.) and structured data (SQL, Databases, etc.) to identify and mitigate critical risks
Information Protection
Identity & Access
Identity Enablement
Access cloud and legacy applications for Enterprise users and
External Identities like Partners (B2B) and Customers/Citizens (B2C)
Identity Security
Zero Trust Access Control using Behavioral Analytics, Threat Intelligence,
and integration of device and app trust signals
Microsoft Entra
formerly Azure AD
Security Operations [Center] (SOC)
Microsoft Sentinel – Cloud Native SIEM, SOAR, and UEBA for IT, OT, and IoT
• Threat & Vulnerability Management
• Integrated data classification
• Threat analytics on top attacks
• Advanced Detection & Remediation
• Automated Investigation & Remediation
• Advanced Threat Hunting
Microsoft Defender XDR - Extended Detection and
Response
Threat visibility and capabilities tailored to resources
Microsoft Defender for Cloud
IaaS, PaaS, and On-Premises
• VMs, Servers, App Environments
• Storage and Databases
• Containers and Orchestration
• DevOps, APIs, CI/CD, and more
Microsoft Defender for Endpoint
Unified Endpoint Security
• Endpoint Detection & Response (EDR)
• Data Loss Protection (DLP)
• Web Content Filtering
• Threat & Vuln Management
Microsoft Defender for Cloud Apps
• App Discovery & Risk Scoring (Shadow IT)
• Threat Detection & Response
• Policy Audit & Enforcement
• Session monitoring & control
• Info Protection & Data Loss Prevention (DLP)
Microsoft Defender for IoT
• Asset &
Vulnerability management
• Threat Detection & Response
• ICS, SCADA, OT
• Internet of Things (IoT)
• Industrial IoT (IIoT)
Azure Arc Threat Intelligence – 78+ Trillion
signals per day of security context
Endpoints & Devices Hybrid Infrastructure – IaaS, PaaS, On-Premises
Software as a Service (SaaS)
Operational Technology (OT)
IoT Devices
Microsoft Intune
Unified Endpoint Management (UEM)
PaaS
On-Premises IaaS
S3
April 2025
https://aka.ms/MCRA
Cloud-native application protection platform (CNAPP)
Microsoft Defender (CSPM+CWPP), Azure Security (CSNS), DevSecOps
GitHub Advanced Security – Secure development capabilities Securing components common most enterprise software supply chains](https://image.slidesharecdn.com/mcra-april-2025-250819192426-181b2221/85/MicrosoftCybserSecurityReferenceArchitecture-April-2025-pptx-49-320.jpg)