As Presented at CollabDays Portugal - 25 October, 2025
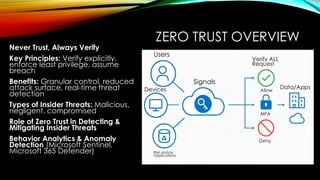
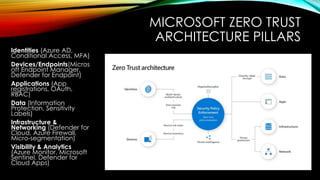
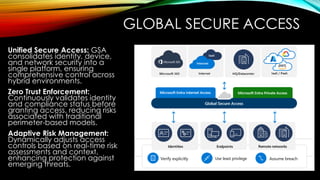
As organizations continue to embrace hybrid and cloud environments, traditional network security approaches are no longer sufficient to protect against the rapidly evolving threat landscape. Enter Zero Trust—a security model that assumes no user, device, or application should be trusted by default. Microsoft’s Zero Trust architecture is designed to protect identities, endpoints, applications, networks, and data by continuously verifying the legitimacy of every access request and enforcing granular least-privilege access.
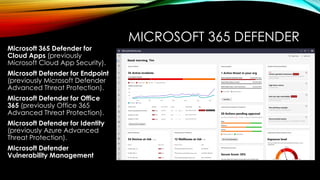
This session will explore how Microsoft cloud services such as Azure AD Conditional Access, Microsoft Endpoint Manager, and Microsoft Defender for Cloud can be used to implement Zero Trust principles across your organization’s IT environment. Learn how to move beyond perimeter-based security and embrace a Zero Trust approach that aligns with today’s sophisticated threats and the needs of a modern enterprise.
• Discover the Zero Trust model: Understand the key principles of Zero Trust and how Microsoft technologies can help enforce these principles in your cloud and hybrid environments.
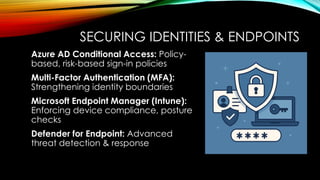
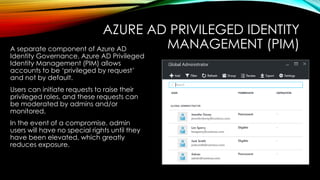
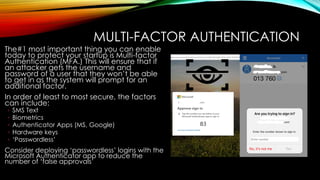
• Secure identities and endpoints: Gain insights into best practices for protecting your workforce with Azure AD Conditional Access policies, Multi-Factor Authentication (MFA), and Microsoft Endpoint Manager.
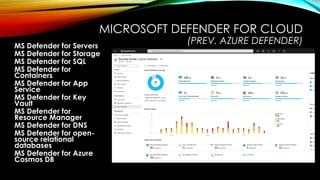
• Implement Zero Trust for applications and data: Explore how to safeguard your applications and data using Microsoft Defender for Cloud, role-based access control (RBAC), and information protection policies.
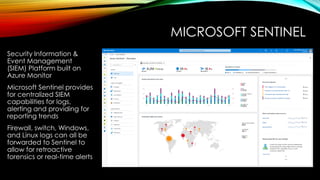
• Build continuous monitoring and automated response capabilities: Learn how to leverage AI and automation within Microsoft’s security solutions to detect and respond to suspicious activity in real-time.