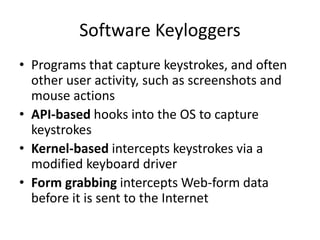
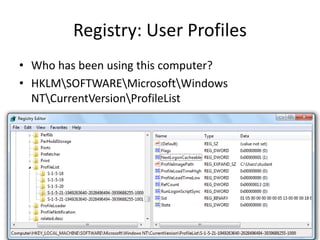
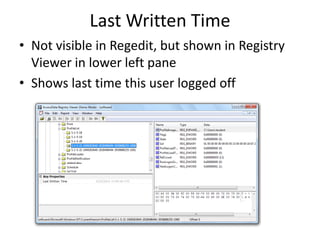
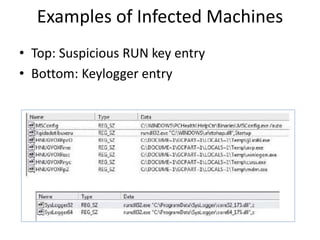
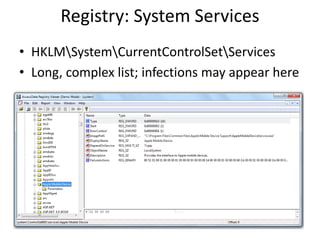
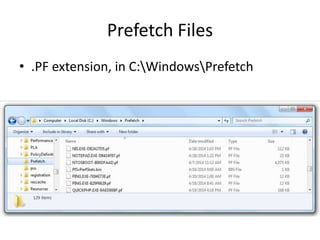
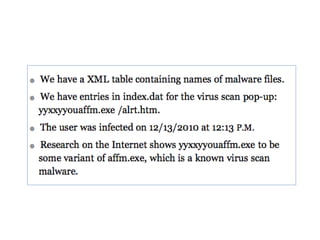
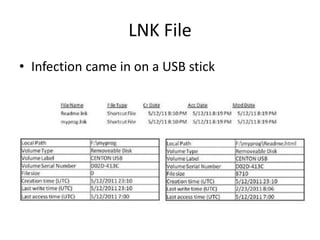
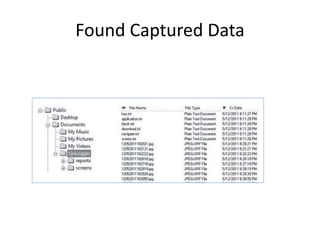
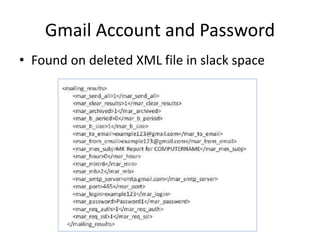
This document discusses keyloggers, malware detection, and forensic investigation of infected systems. It defines keyloggers as hardware or software that captures keystrokes and malware as malicious software like viruses and Trojans. It provides tips for detecting keyloggers and malware through artifacts in the system, registry, prefetch files, and suspicious files and entries. It outlines methods for determining the infection source and timeline, and identifying captured data, attacker information, and next steps for investigators.