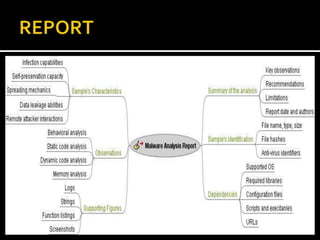
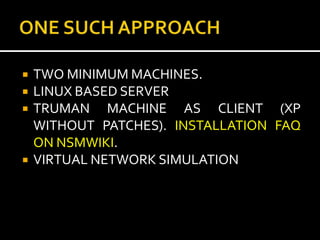
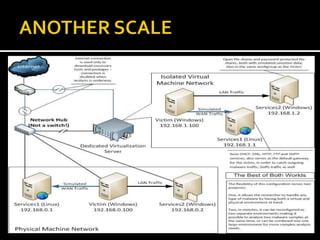
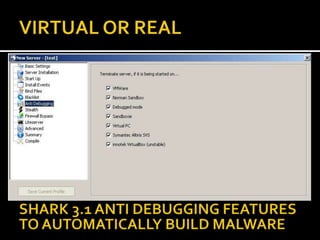
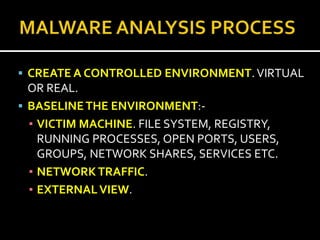
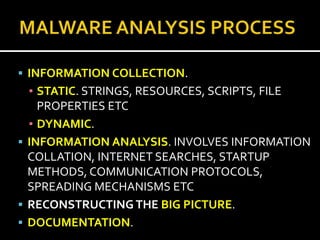
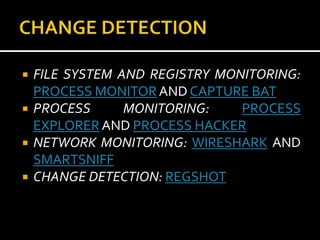
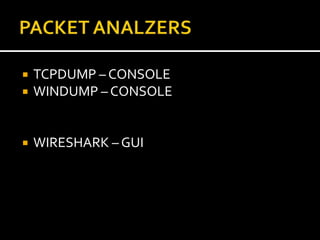
This document provides an overview of a game plan for analyzing malware. It will include a theoretical overview today followed by detailed presentations on virtualization, honeypots/honeynets, debugging, and more. It discusses setting up a controlled lab environment for analysis including static analysis, network traffic analysis, disk/file system analysis, and memory analysis. It also discusses various tools that can be used for each part of the analysis process.




















![ THE OPTIONS OFFERED IN NDIFF INCLUDE:
ndiff [-b|-baseline <file-or-:tag>] [-o|-observed <file-or-:tag>]
[-op|-output-ports <ocufx>] [-of|-output-hosts <nmc>]
[-fmt|-format <terse | minimal | verbose | machine | html | htmle>]
NDIFF OUTPUT MAY BE REDIRECTED TO A WEB PAGE:
ndiff –b base-line.txt –o tested.txt –fmt machine | ndiff2html >
differences.html
THE OUTPUT FILE, “DIFFERENCES.HTML”, MAY BE DISPLAYED
IN A WEB BROWSER. THIS WILL SEPARATE HOSTS INTO THREE
MAIN CATEGORIES:
o NEW HOSTS,
o MISSING HOSTS, AND
o CHANGED HOSTS.](https://image.slidesharecdn.com/malwareanalysis-anoverview-100703073937-phpapp01-100707023912-phpapp01/85/Malware-Analysis-an-overview-by-PP-Singh-31-320.jpg)