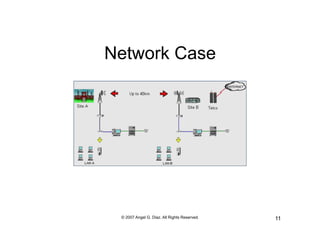
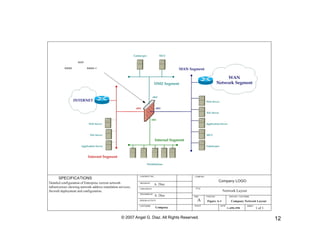
The document discusses network assessment and administration. It describes how network messages are broadcast, defining broadcast messages as messages addressed to every host on a network. It also discusses system administration, describing it as where humans interface with computers to solve problems or provide services. The document outlines various components of a computer network, such as humans, hosts, routers, switches, and cables. It provides steps for network analysis, including reviewing physical network topology, DNS data, operating systems, configurations, devices, subnets, routers, IP addresses, and services used on the network.