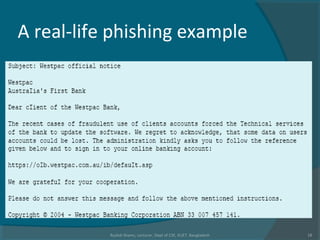
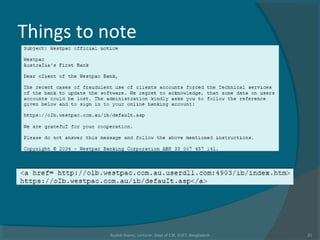
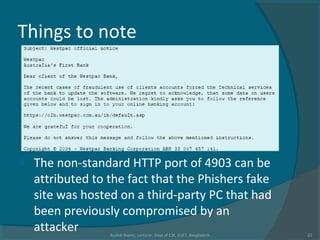
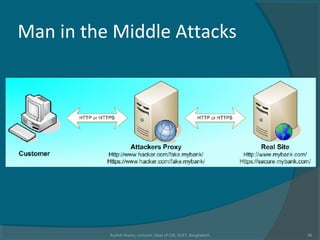
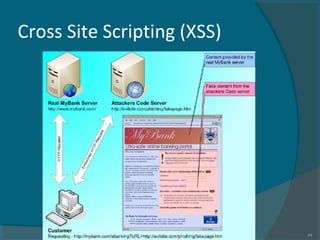
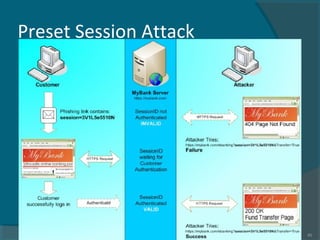
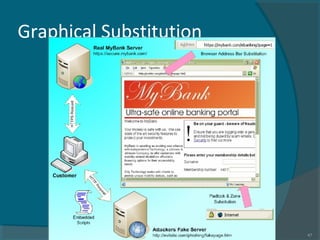
The document discusses various techniques used in phishing attacks, including sending phishing emails disguised as legitimate companies to steal users' personal information. It notes that phishing attacks doubled from 2004 to 2005 according to one report. The document outlines common phishing techniques like using official-looking emails, URL obfuscation, and hosting malicious software on spoofed websites. It also discusses evolving threats like man-in-the-middle attacks, cross-site scripting, and exploiting weaknesses in interconnected systems and human tendencies to trust familiar brands.