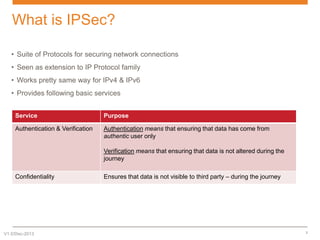
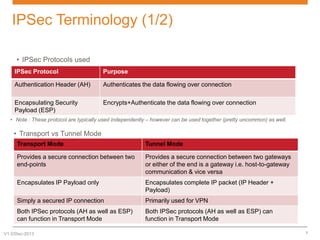
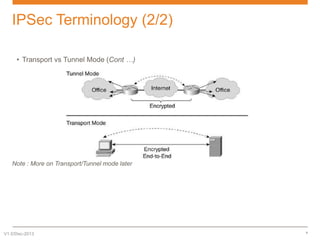
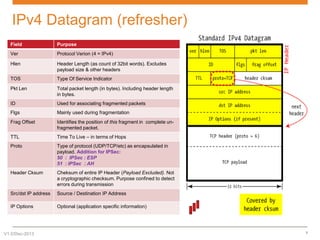
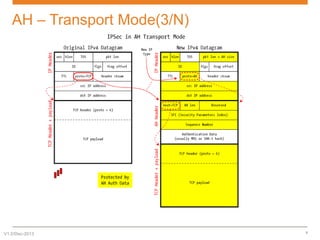
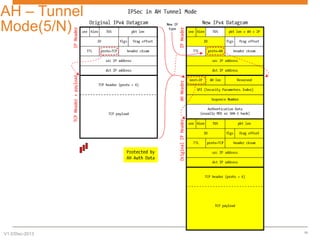
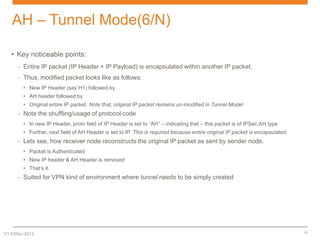
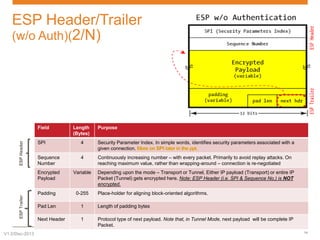
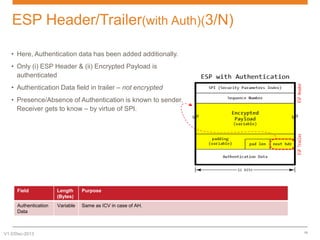
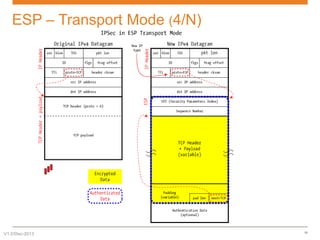
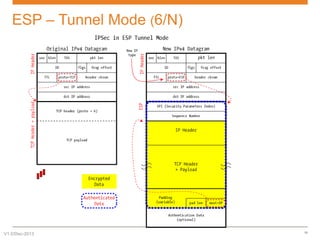
IPsec is a suite of protocols designed to secure network connections, applicable to both IPv4 and IPv6, providing authentication, verification, and confidentiality of data. It includes protocols like Authentication Header (AH) and Encapsulating Security Payload (ESP), which can function in transport or tunnel modes, addressing different security needs. AH focuses on authenticating data without encryption, while ESP offers both authentication and encryption, suitable for secure VPN communications.