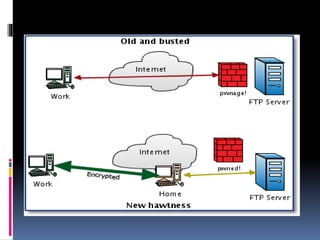
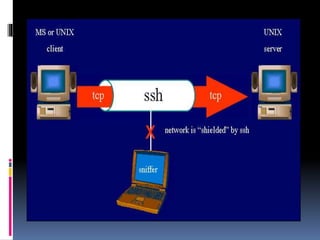
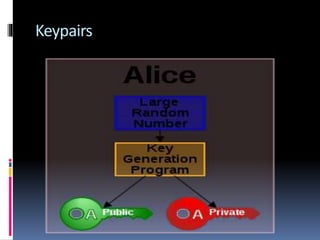
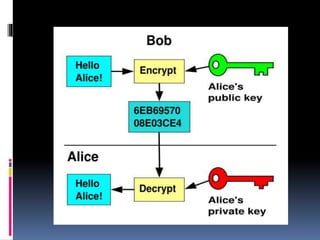
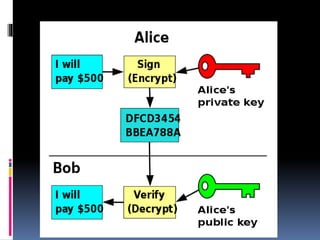
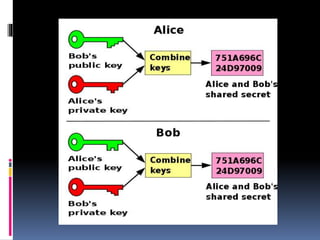
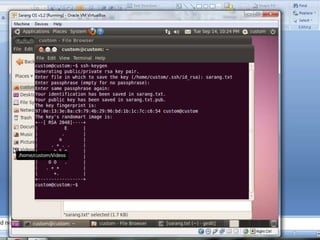
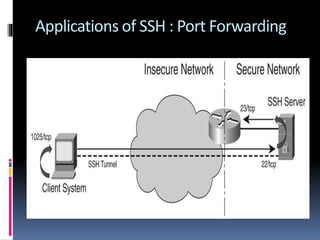
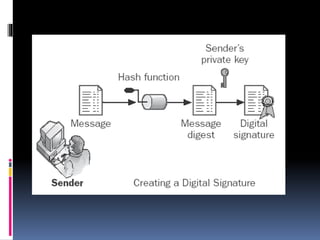
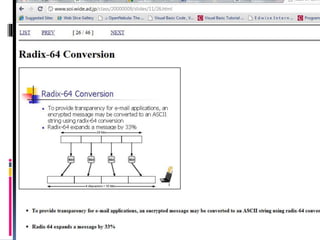
This document provides an introduction to SSH and PGP protocols for secure communication. It discusses how SSH uses public-key cryptography to authenticate connections and encrypt data transmitted over untrusted networks, protecting against threats like IP spoofing. It also explains how SSH uses key pairs and configuration files. PGP is introduced as providing encryption, authentication and integrity for email through techniques like hashing, symmetric/asymmetric encryption and digital signatures. It describes how PGP handles the technical challenges of encoding encrypted data for transmission in email systems.