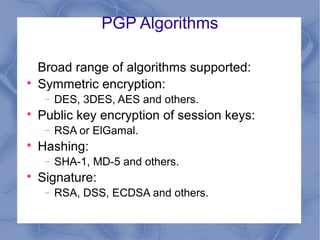
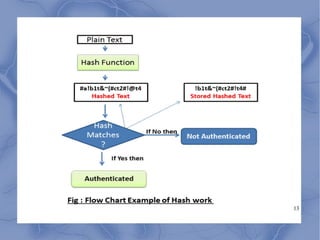
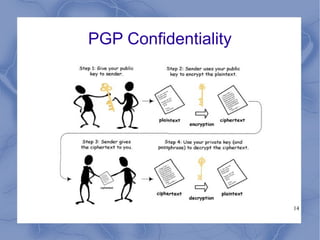
This document discusses email security threats and options to improve security. The main threats to email security are loss of confidentiality from emails being sent in clear text over open networks and stored on insecure systems, lack of integrity protection allowing emails to be altered, and lack of authentication and non-repudiation. Options to improve security include encrypting server-client connections using POP/IMAP over SSH or SSL, and end-to-end encryption using PGP. PGP provides encryption for confidentiality and digital signatures for authenticity and non-repudiation. The document also discusses email-based attacks and spam, as well as the algorithms and authentication process used by PGP.