Embed presentation
Download as PDF, PPTX





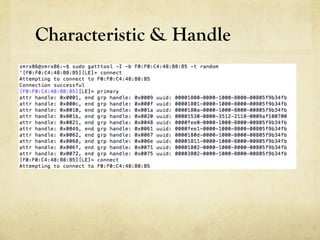



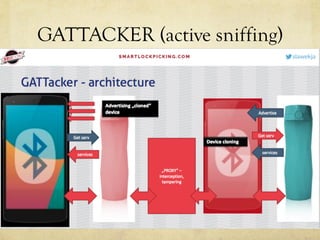
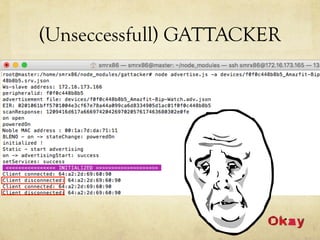
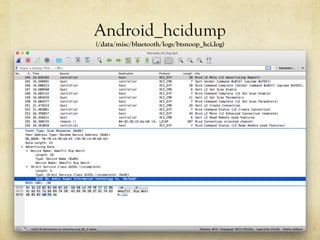

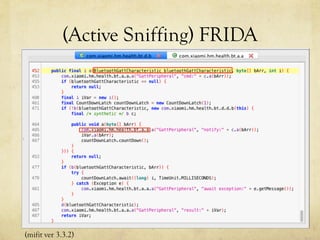
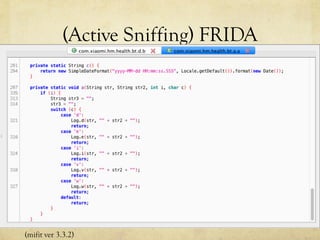
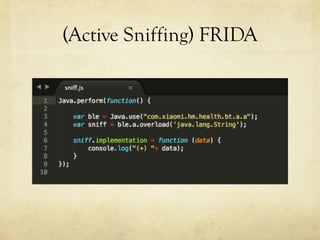
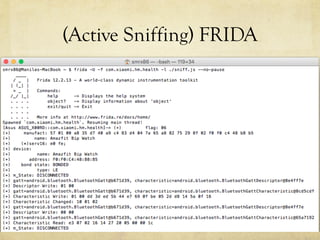

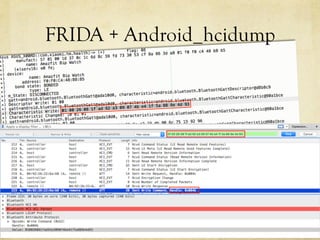



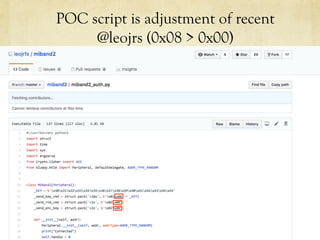



The document discusses hacking a BLE smartwatch. It begins with an introduction of the speaker as an independent security researcher. It then covers relevant research on authenticating Mi Band 2 and reverse engineering BLE from Android apps. The rest of the document discusses the speaker's process of discovering the authentication procedure of a smartwatch by using tools like GATTACKER, Android hcidump, and FRIDA to actively sniff the communication and map out the characteristic UUIDs and handles. It concludes with a proof-of-concept script to demonstrate altering the authentication by adjusting a recent proof-of-concept from another researcher.
























