Embed presentation
Download to read offline






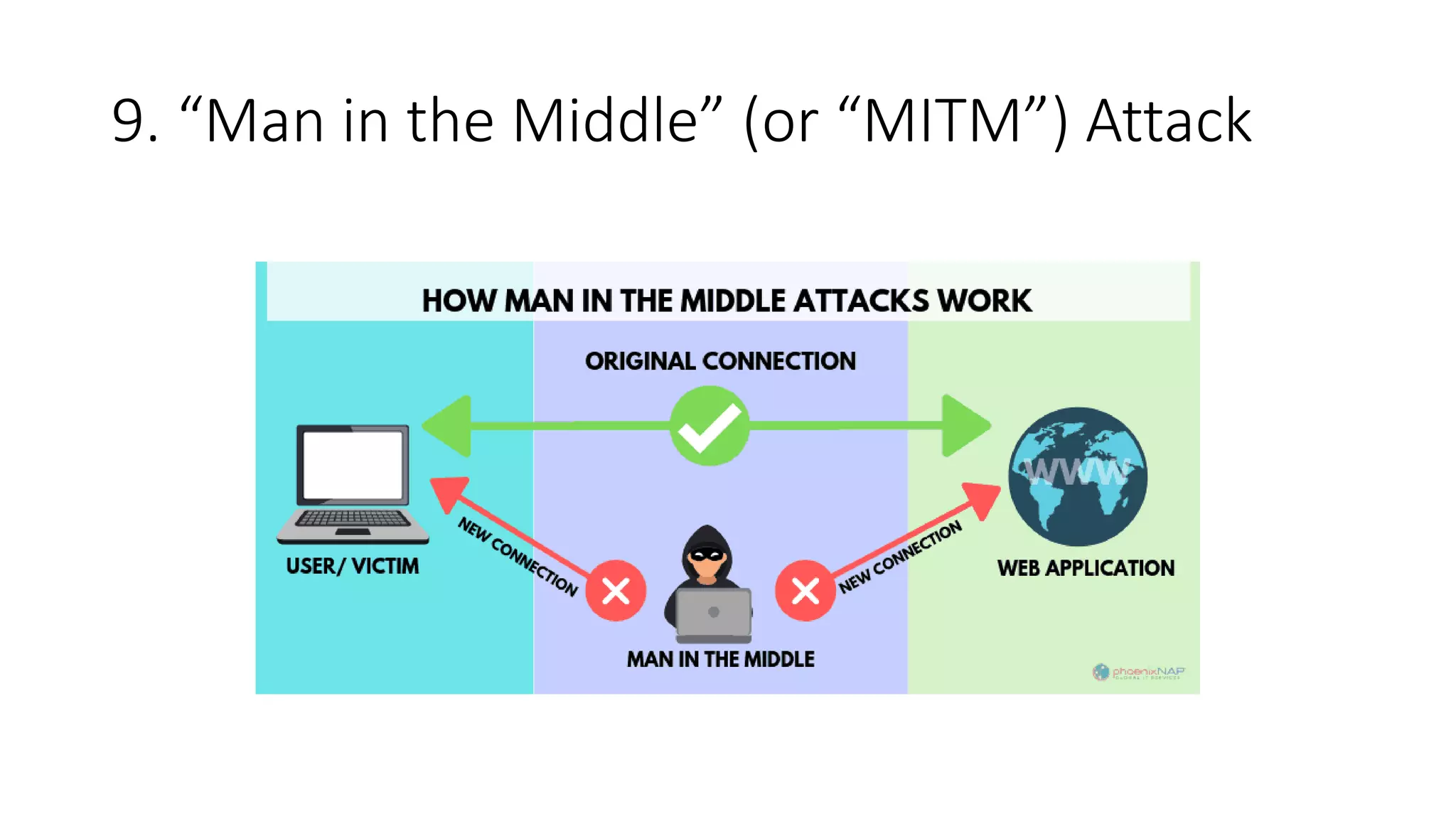
The document outlines various hacking techniques, including bait and switch, cookie theft, denial of service (DoS/DDoS), eavesdropping, keylogging, malware, phishing, watering hole attacks, and man-in-the-middle (MITM) attacks. Each method represents a different approach hackers use to compromise systems and data. Understanding these techniques is essential for cybersecurity awareness and defense.









