Gramax-Cybersec-Role of Cybersecurity in Maritime A high-risk sector.pdf
Role of Cybersecurity in Maritime: A high-risk sector Maritime, an ancient industry responsible carriage for 90% of global trade, stands as a cornerstone of the world economy. Despite initial perceptions that maritime assets are immune, the increased reliance on industrial control systems (ICS) and satellite communications renders this age-old industry susceptible to cyber adversaries. The reluctance to openly share information and collaborate on cybersecurity best practices has exacerbated the issue, leading to a surge in maritime cyber incidents, up by a staggering 900% since 2017. The NotPetya cyberattack in June 2017 stands out as one of the most devastating incidents, causing over $10 billion in damages. This malware, initially targeting Ukrainian companies, had a far-reaching impact, affecting global giants like Maersk, which lost significant data and infrastructure. In this article, we will take you through the crucial role of cybersecurity in the maritime sector, offering insights into the intricacies of the maritime ecosystem, and identifying key vulnerable systems. Additionally, we will explore the far-reaching consequences of successful cyberattacks and effective strategies for cyber risk management in this high-stakes domain.
Recommended
Recommended
More Related Content
Similar to Gramax-Cybersec-Role of Cybersecurity in Maritime A high-risk sector.pdf
Similar to Gramax-Cybersec-Role of Cybersecurity in Maritime A high-risk sector.pdf (20)
Recently uploaded
Recently uploaded (20)
Gramax-Cybersec-Role of Cybersecurity in Maritime A high-risk sector.pdf
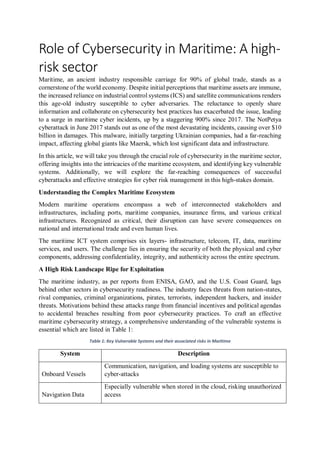
- 1. Role of Cybersecurity in Maritime: A high- risk sector Maritime, an ancient industry responsible carriage for 90% of global trade, stands as a cornerstone of the world economy. Despite initial perceptions that maritime assets are immune, the increased reliance on industrial control systems (ICS) and satellite communications renders this age-old industry susceptible to cyber adversaries. The reluctance to openly share information and collaborate on cybersecurity best practices has exacerbated the issue, leading to a surge in maritime cyber incidents, up by a staggering 900% since 2017. The NotPetya cyberattack in June 2017 stands out as one of the most devastating incidents, causing over $10 billion in damages. This malware, initially targeting Ukrainian companies, had a far-reaching impact, affecting global giants like Maersk, which lost significant data and infrastructure. In this article, we will take you through the crucial role of cybersecurity in the maritime sector, offering insights into the intricacies of the maritime ecosystem, and identifying key vulnerable systems. Additionally, we will explore the far-reaching consequences of successful cyberattacks and effective strategies for cyber risk management in this high-stakes domain. Understanding the Complex Maritime Ecosystem Modern maritime operations encompass a web of interconnected stakeholders and infrastructures, including ports, maritime companies, insurance firms, and various critical infrastructures. Recognized as critical, their disruption can have severe consequences on national and international trade and even human lives. The maritime ICT system comprises six layers- infrastructure, telecom, IT, data, maritime services, and users. The challenge lies in ensuring the security of both the physical and cyber components, addressing confidentiality, integrity, and authenticity across the entire spectrum. A High Risk Landscape Ripe for Exploitation The maritime industry, as per reports from ENISA, GAO, and the U.S. Coast Guard, lags behind other sectors in cybersecurity readiness. The industry faces threats from nation-states, rival companies, criminal organizations, pirates, terrorists, independent hackers, and insider threats. Motivations behind these attacks range from financial incentives and political agendas to accidental breaches resulting from poor cybersecurity practices. To craft an effective maritime cybersecurity strategy, a comprehensive understanding of the vulnerable systems is essential which are listed in Table 1: Table 1: Key Vulnerable Systems and their associated risks in Maritime System Description Onboard Vessels Communication, navigation, and loading systems are susceptible to cyber-attacks Navigation Data Especially vulnerable when stored in the cloud, risking unauthorized access
- 2. Major Ports Systems Including Terminal Operating Systems (TOS) and Port Community Systems (PCS) Mainland Computer Systems Operated by maritime companies, potentially targeted for data breaches Personal Devices Laptops, smartphones, and USB keys used by crew members are potential entry points for cyber threats Potential Maritime Cybersecurity Attacks The vulnerabilities within maritime systems can lead to various high-impact cyberattacks, including: Attacks on OEM networks or third-party suppliers spreading to client vessel OT networks. Attacks on satellite providers gaining access to vessel IT/OT networks. Exploited cyber vulnerabilities enabling attacks on critical ship systems like GPS/navigation, propulsion, and ballast control. Ransomware and malware threats compromising vessel systems. Compromised systems causing physical harm to personnel, cargo, and the ship itself. Cyber Risk Management in Maritime To mitigate these risks effectively, a robust Cyber Risk Management plan should be in place: 1. Roles and Responsibilities: Clearly define the roles and responsibilities of personnel, both onshore and aboard, to establish accountability for cybersecurity. 2. System Identification: Identify systems, assets, data, and capabilities that, if breached, could pose a threat to ship operations and safety. 3. Technical and Procedural Measures: Implement a combination of technical and procedural measures to protect against cyber incidents, ensuring business continuity. 4. Preparation and Response: Conduct activities to prepare for and respond to cyber incidents, aligning with existing security risk management requirements. Future Developments and Cybersecurity Measures The maritime industry is moving towards Internet of Things (IoT) to enhance safety and efficiency. Shipbuilders like Hyundai Heavy Industries are developing IoT applications to improve ship operations and crew well-being. However, this digital transformation also introduces new cybersecurity challenges. In addition to that, the concept of crewless ships, expected to be realized by companies like Rolls-Royce by 2020, brings potential benefits in terms of safety, cost, and environmental impact. However, it also poses new cybersecurity challenges that need to be addressed proactively. What’s Next? Recognizing the criticality of cybersecurity in the maritime, it is important to have a collaborative effort across stakeholders, including government for developing and enforcing international regulations, promoting information sharing, and fostering research and
- 3. development in maritime cybersecurity, port authorities for implementing cybersecurity measures at ports and facilitating secure communication channels between vessels and shoreside facilities, shipping companies for investing in cybersecurity solutions, training crew members, and conducting regular cyber risk assessments and technology providers for secure hardware and software solutions for maritime applications and collaborating with industry stakeholders to address emerging threats. Read More
