Embed presentation
Download to read offline


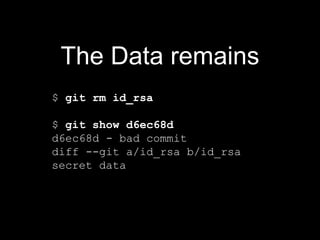
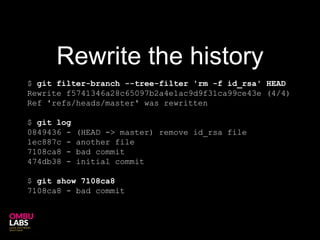

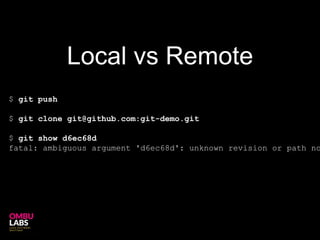
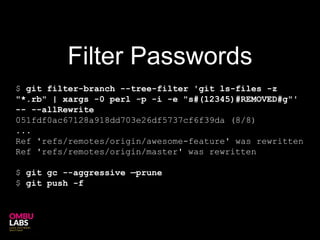
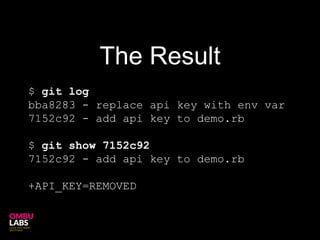



Git can unintentionally store sensitive data like passwords or keys in its commit history. While commands like filter-branch can remove sensitive data from the local history, it may still be retrievable from remote repositories unless the history is rewritten there as well. The safest approach is to change all credentials and remove the local git repository entirely.










