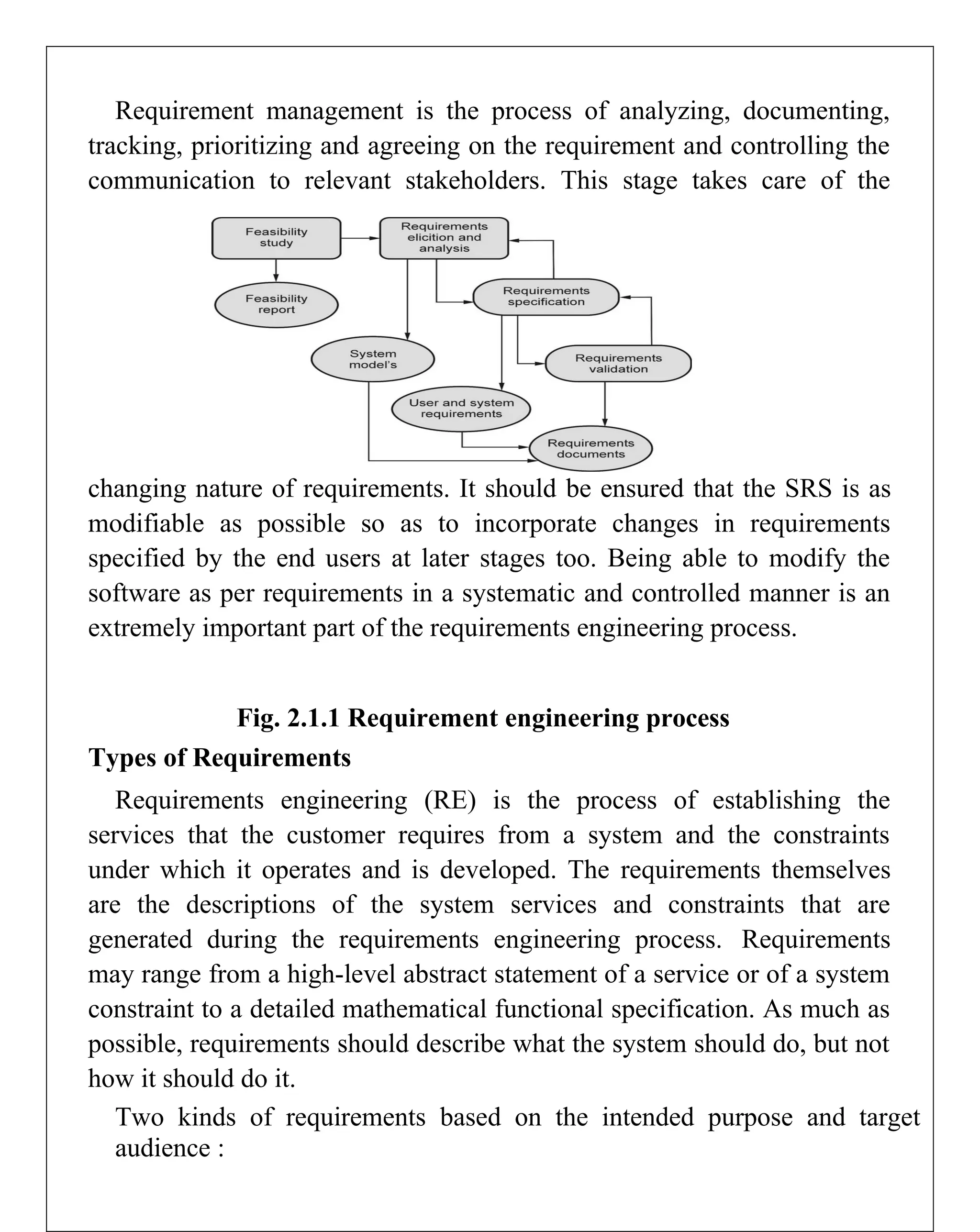
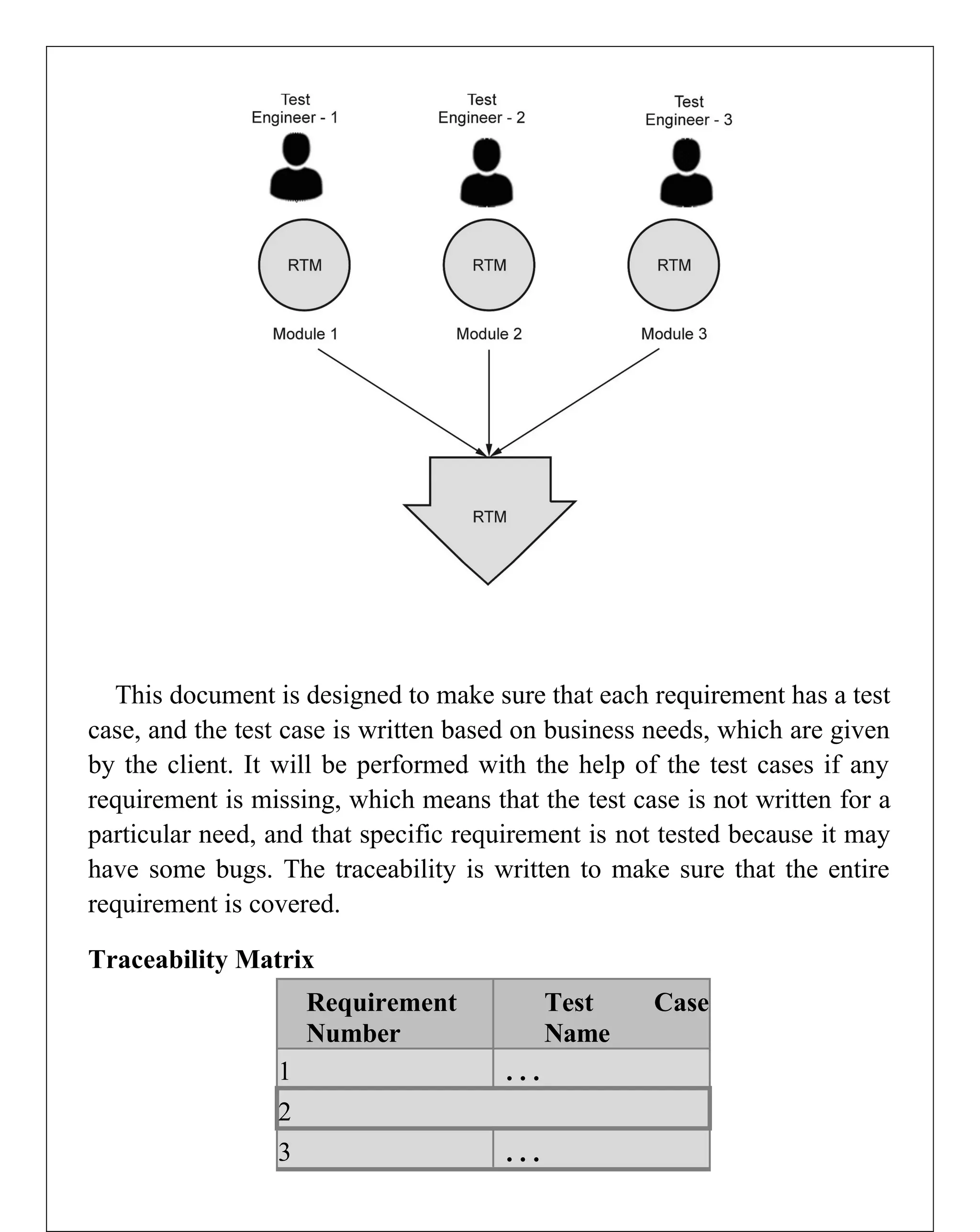
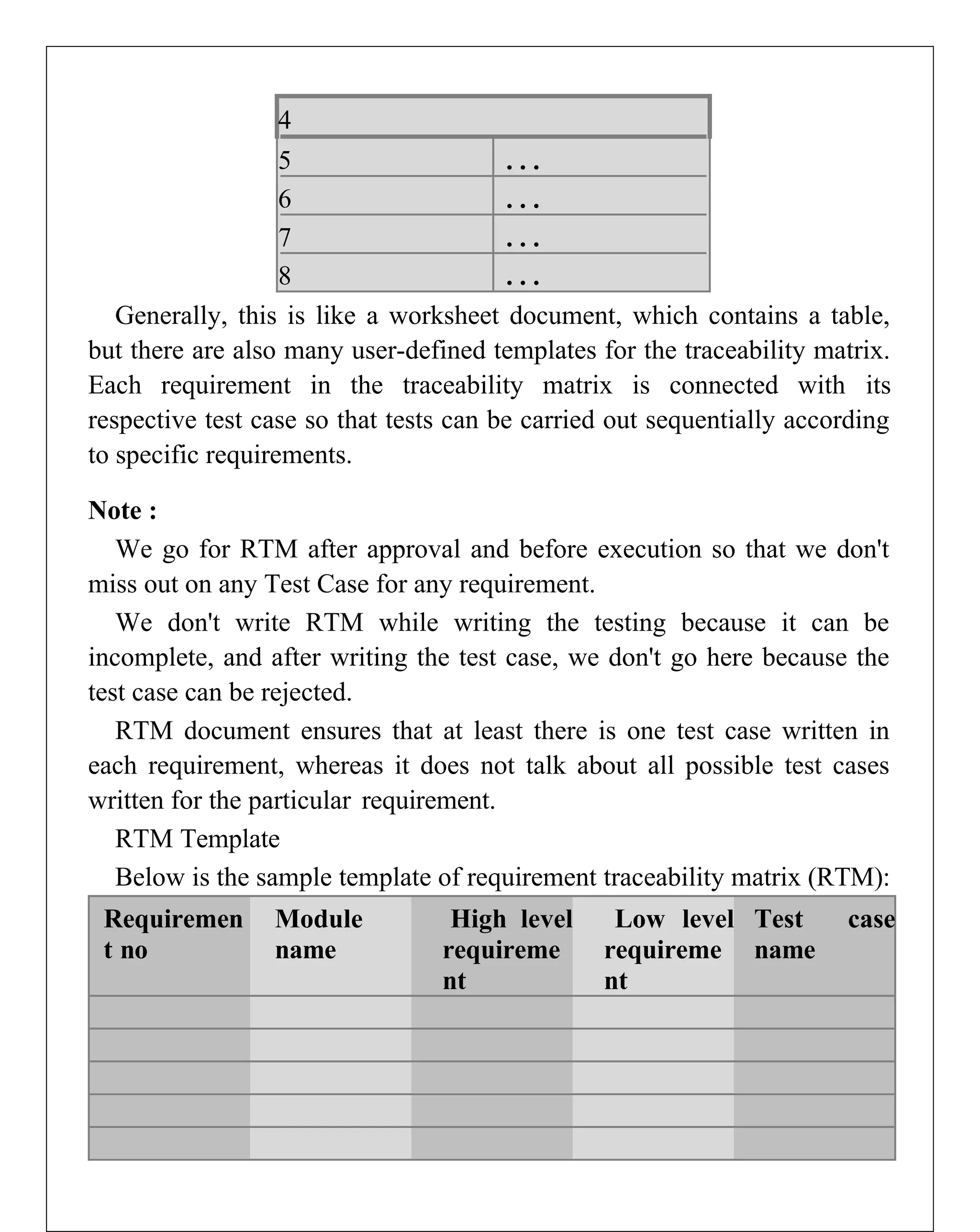
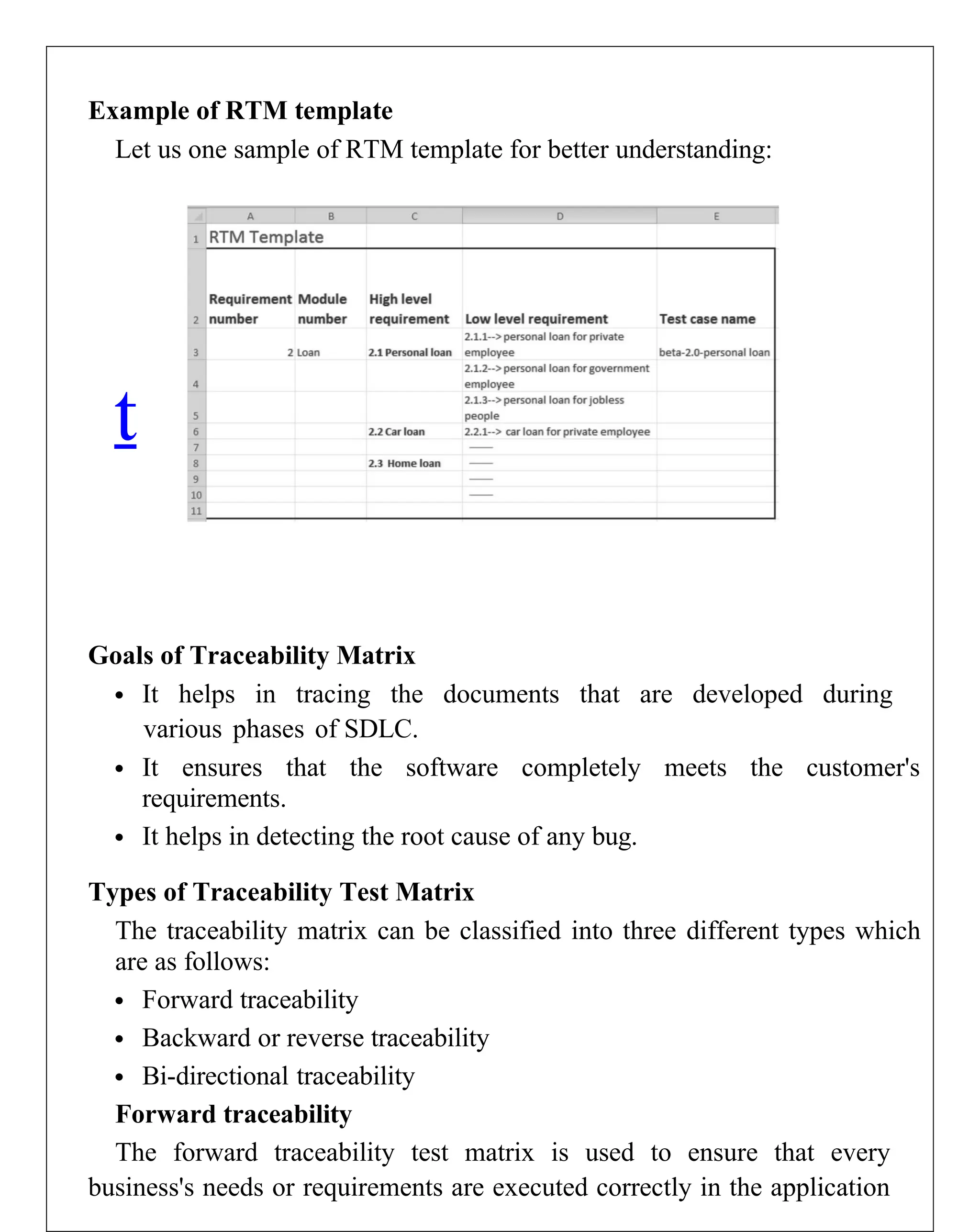
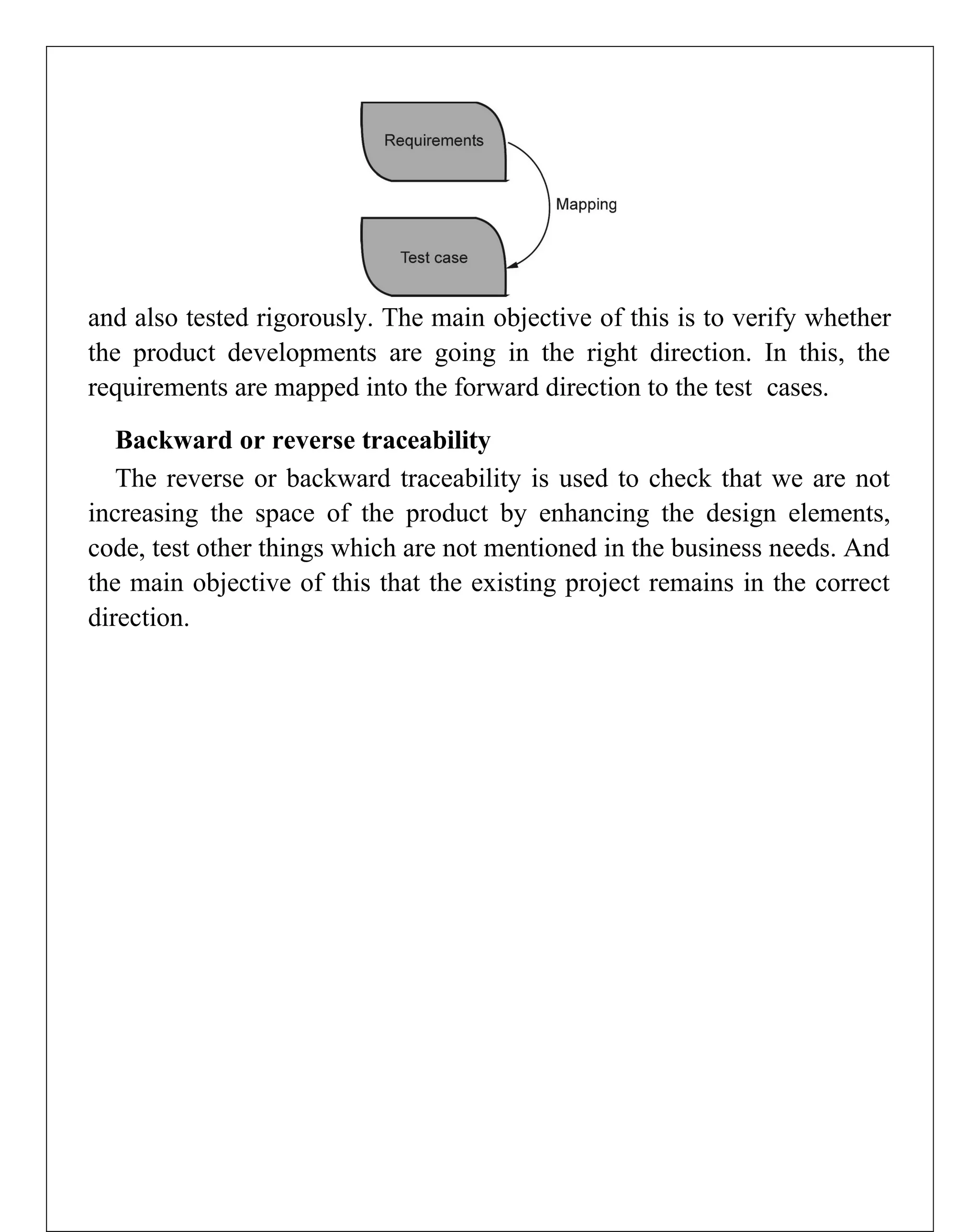
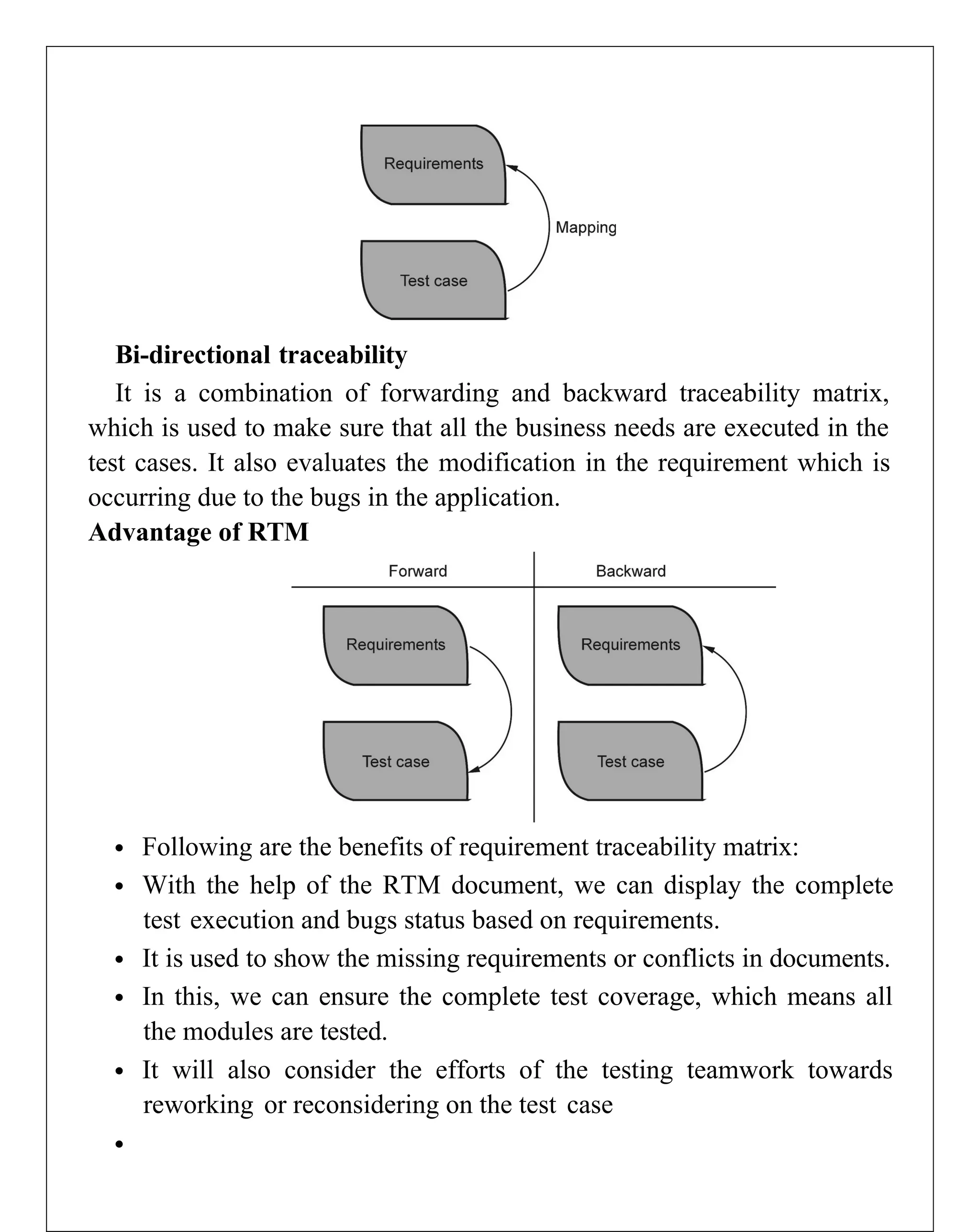
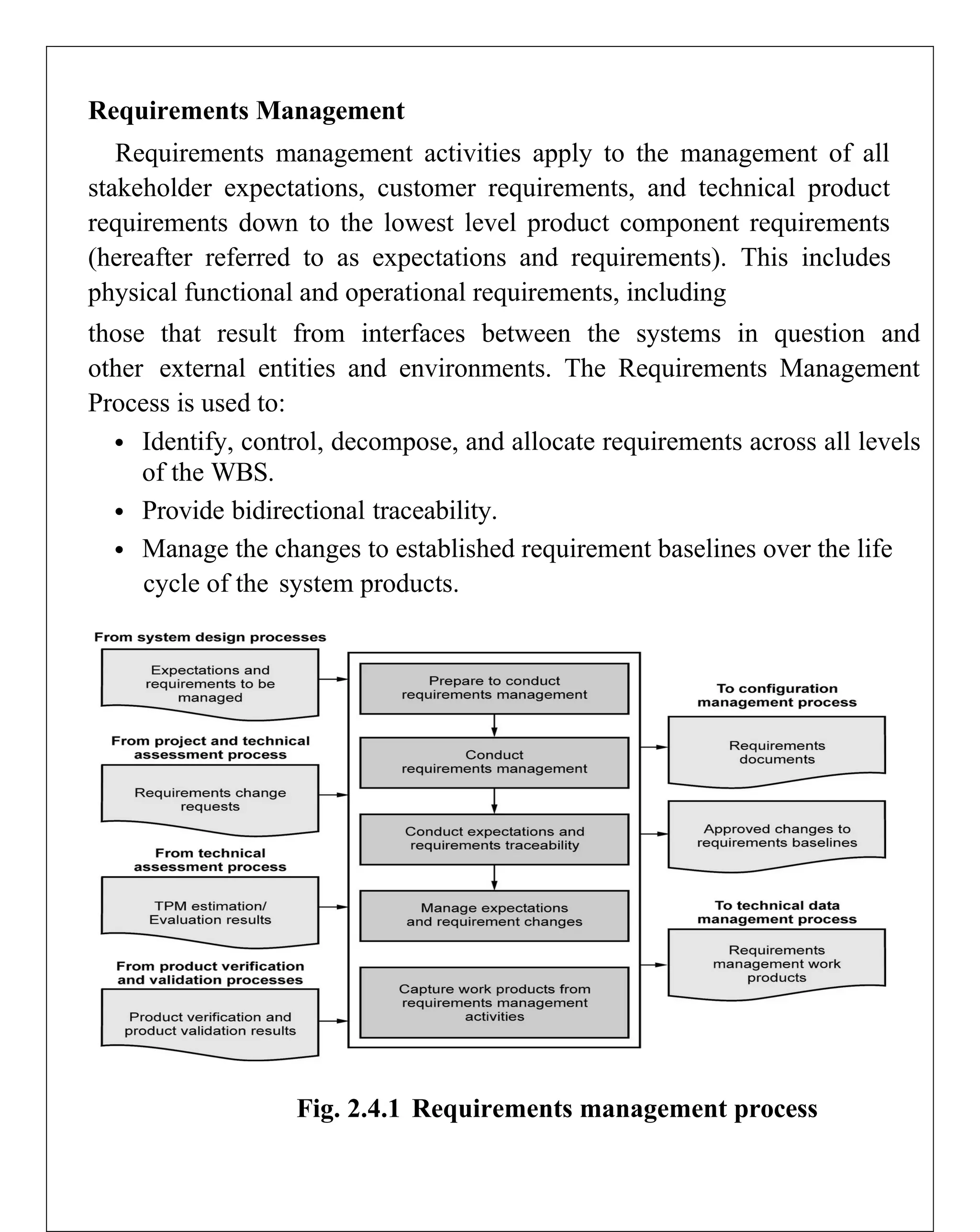
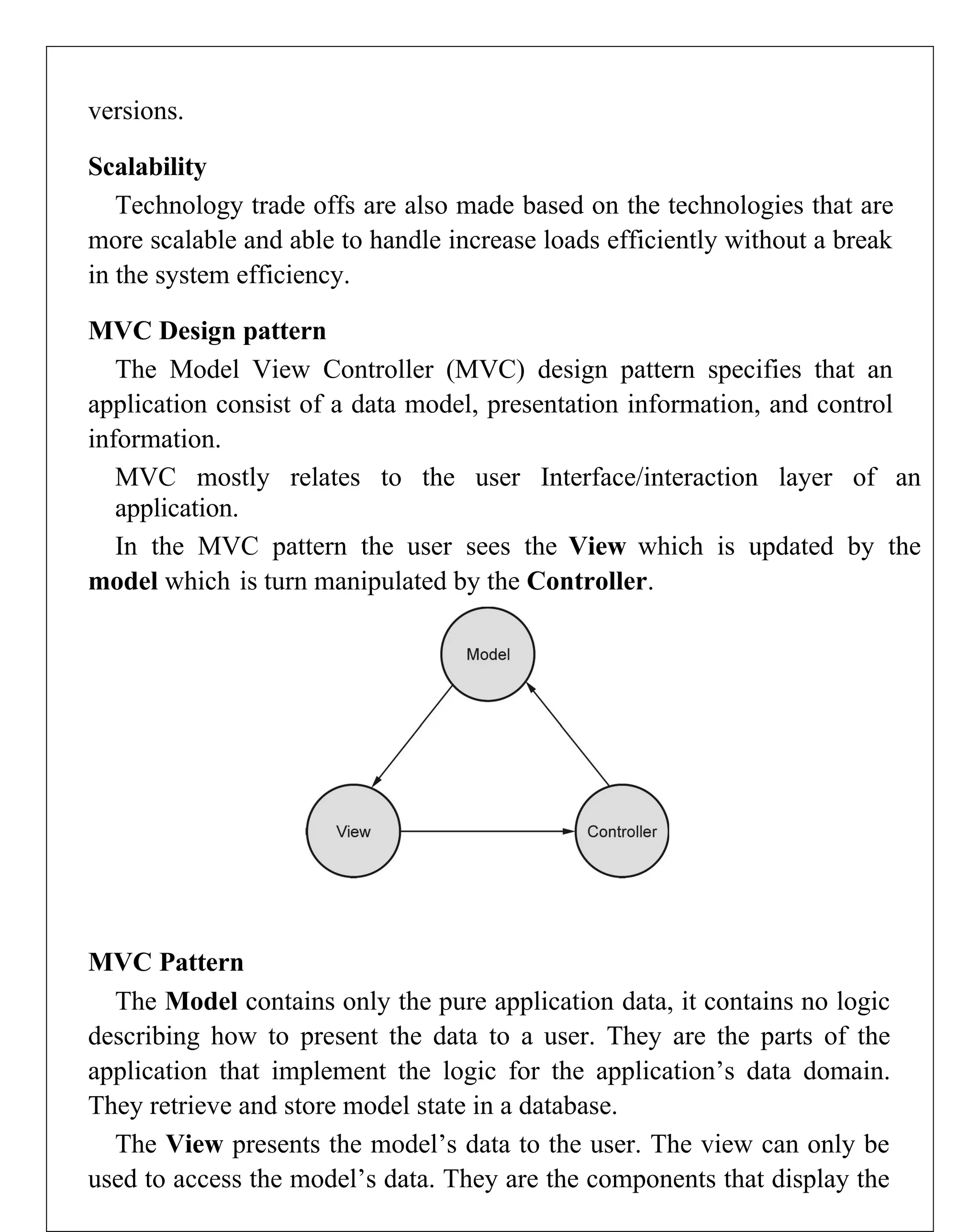
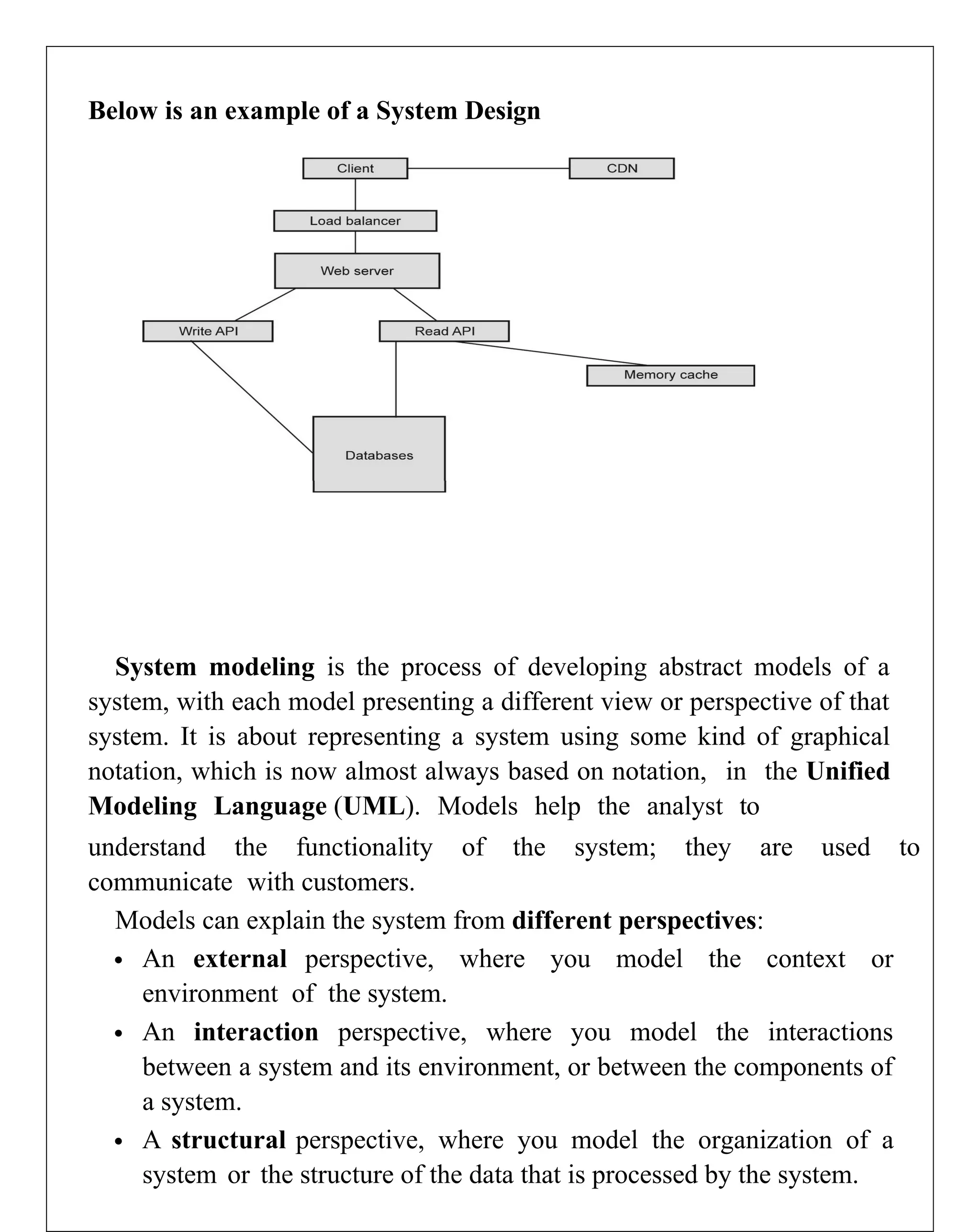
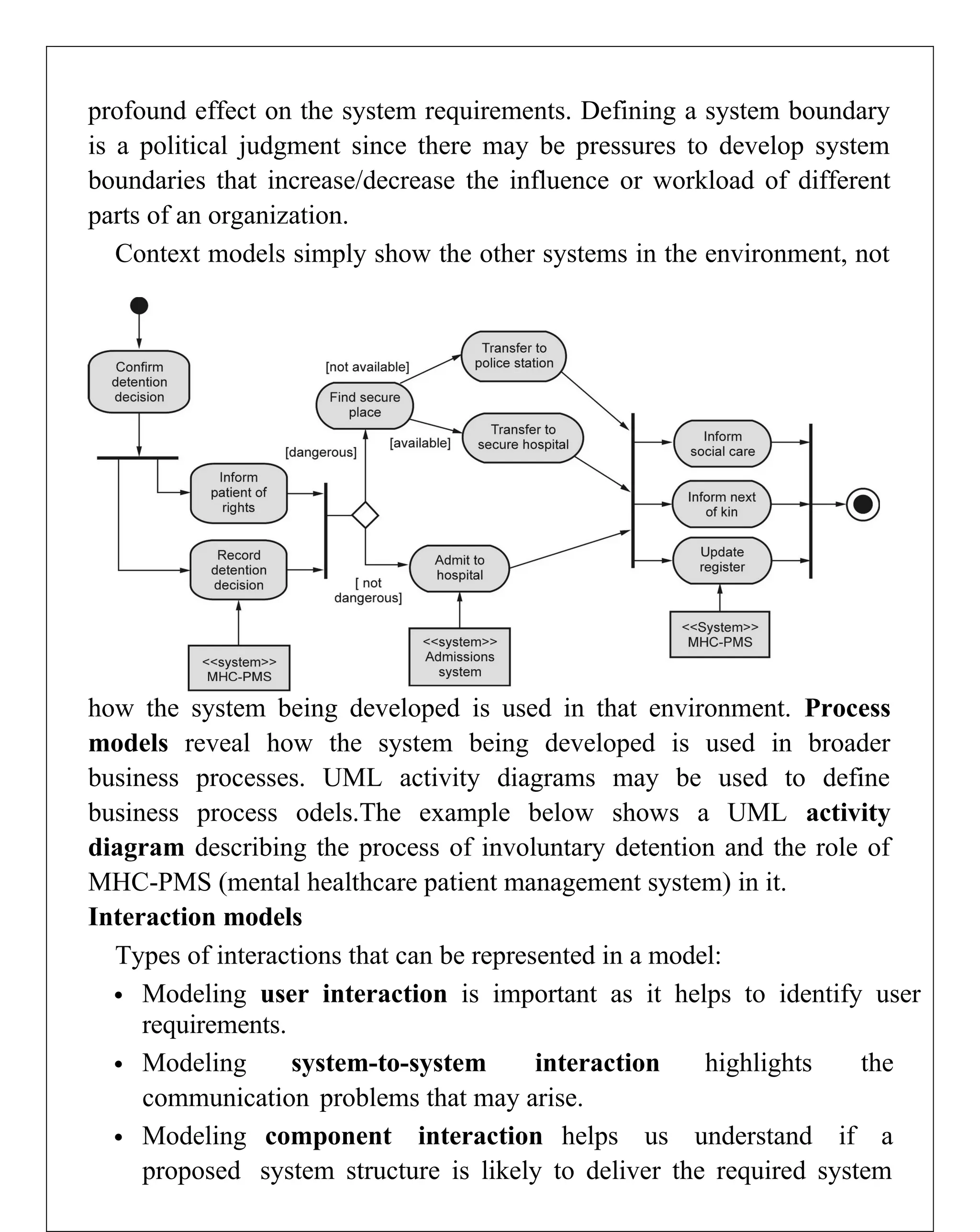
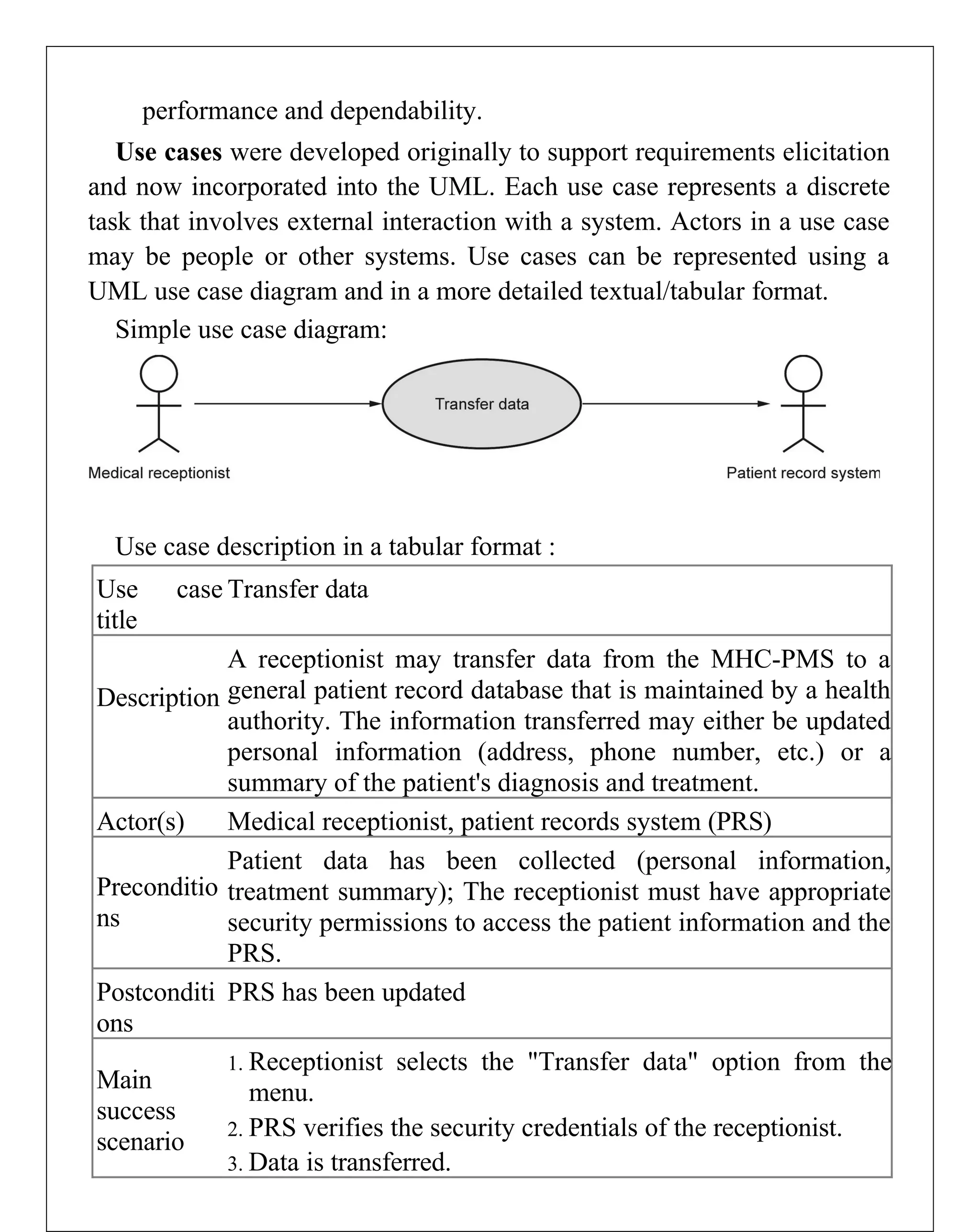
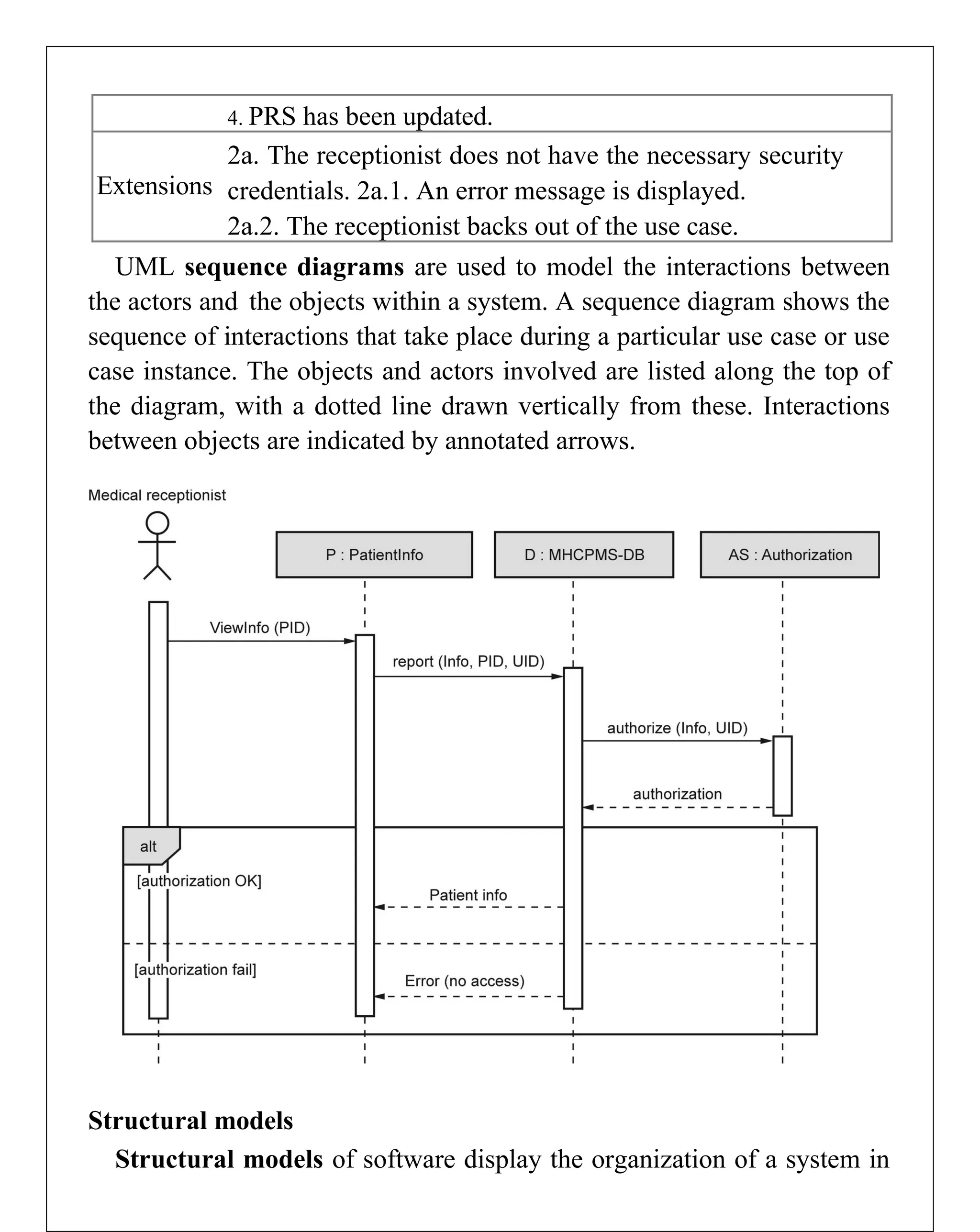
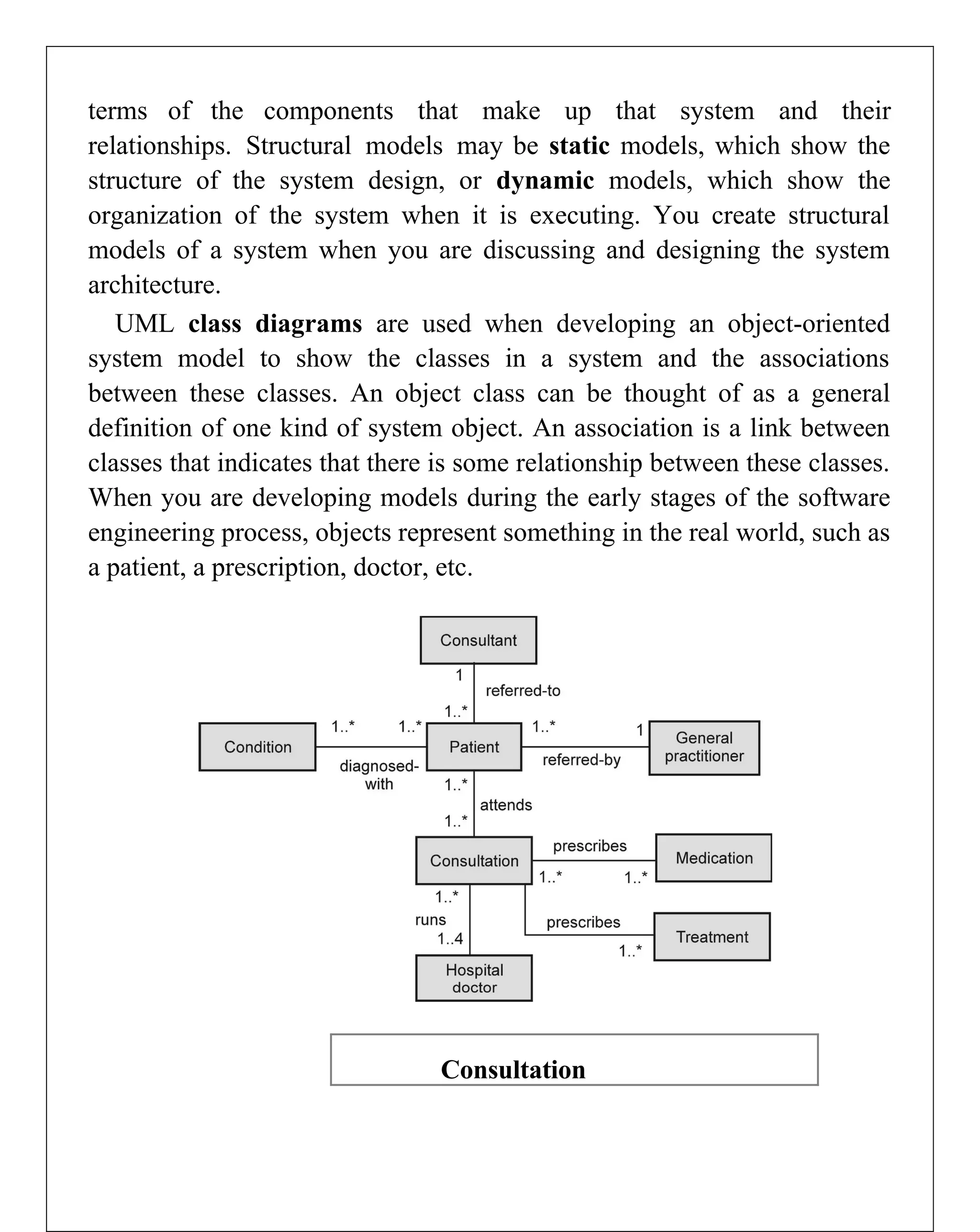
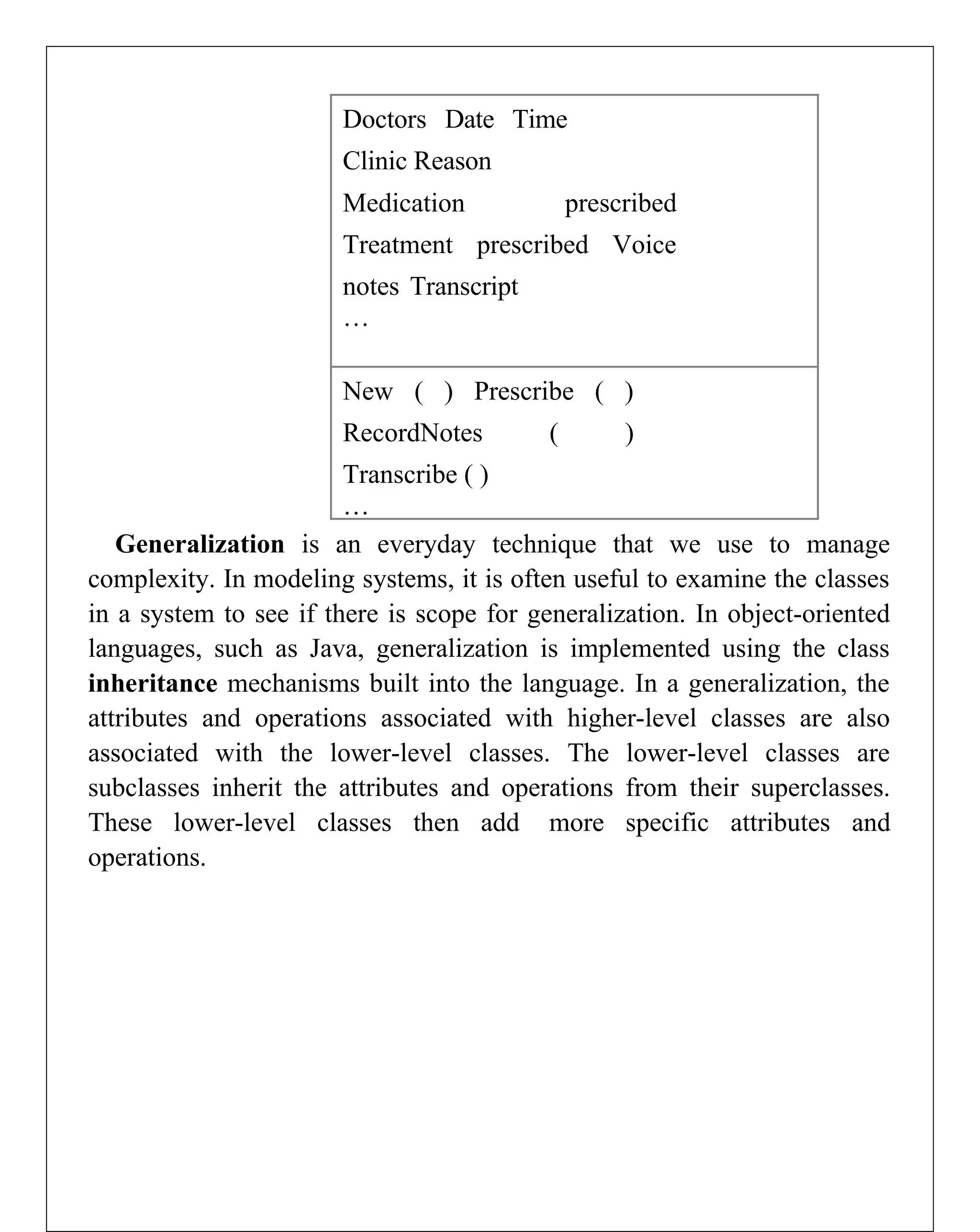
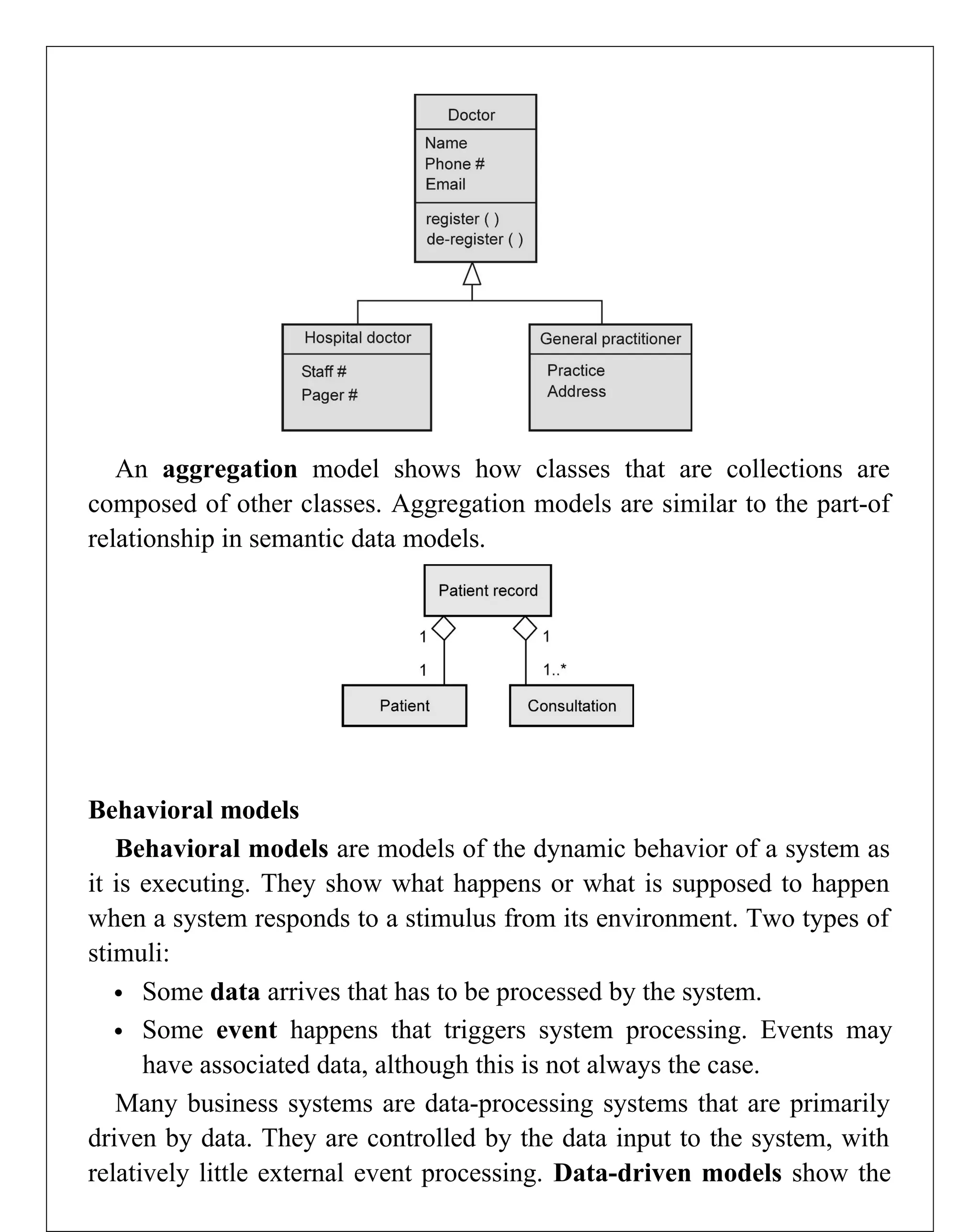
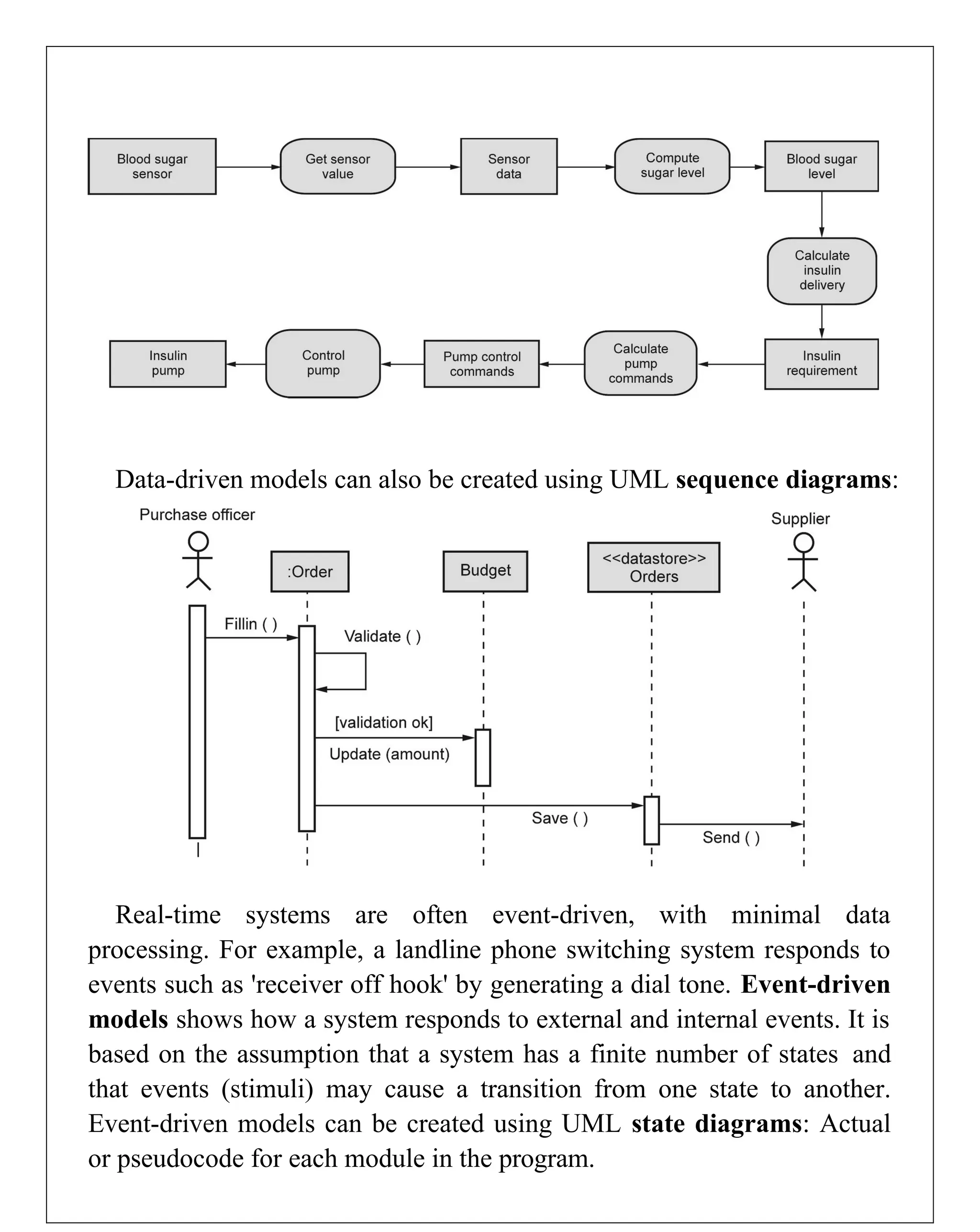
Requirements engineering is the systematic process of defining, documenting, and managing software requirements, encompassing activities like elicitation, specification, verification, validation, and management. It distinguishes between user requirements, which outline high-level services for users, and system requirements, detailing the functionalities and constraints of the system. Additionally, the document emphasizes the importance of requirement traceability and the management of changes to ensure consistent alignment with stakeholder needs and project goals.