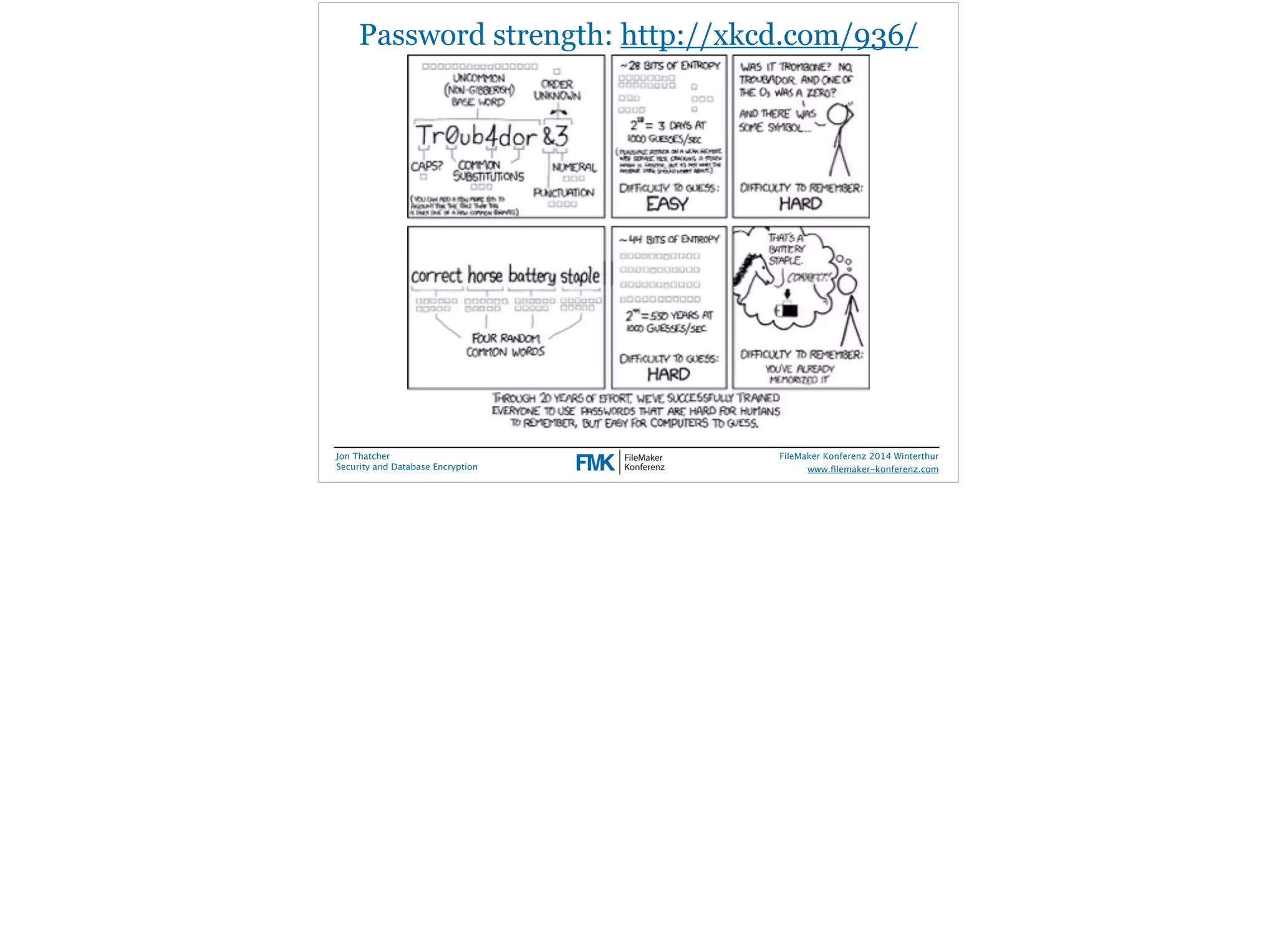
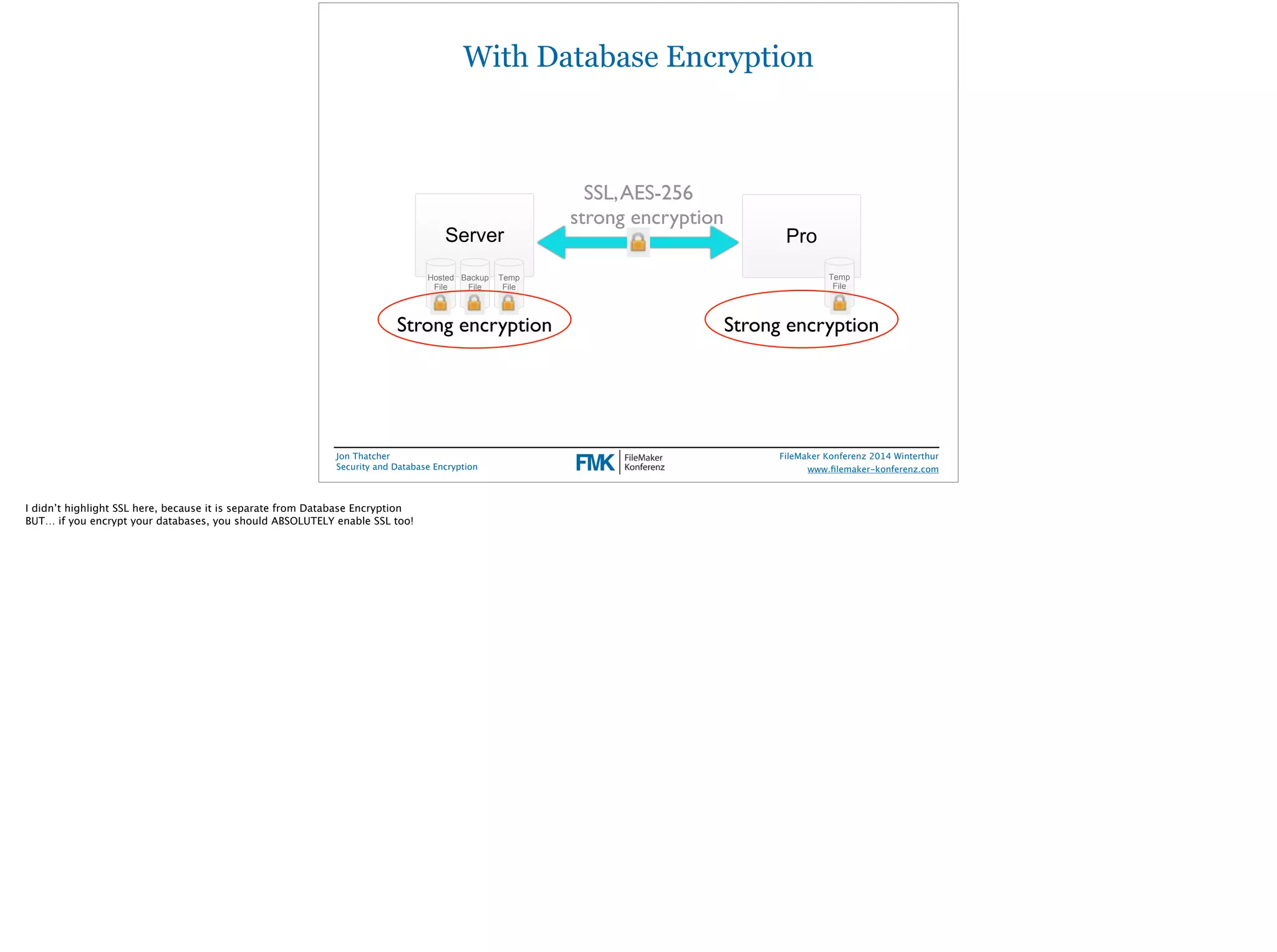
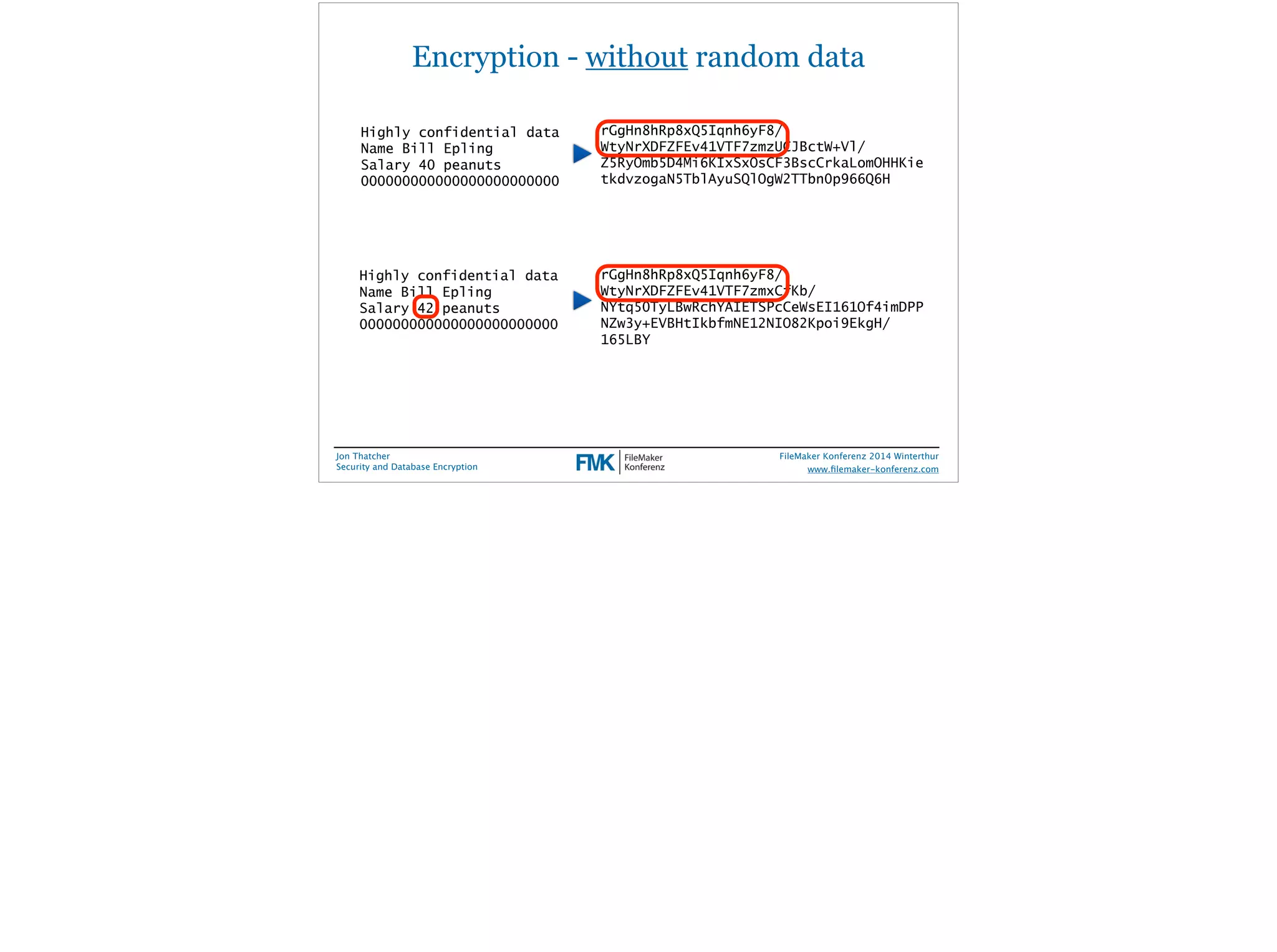
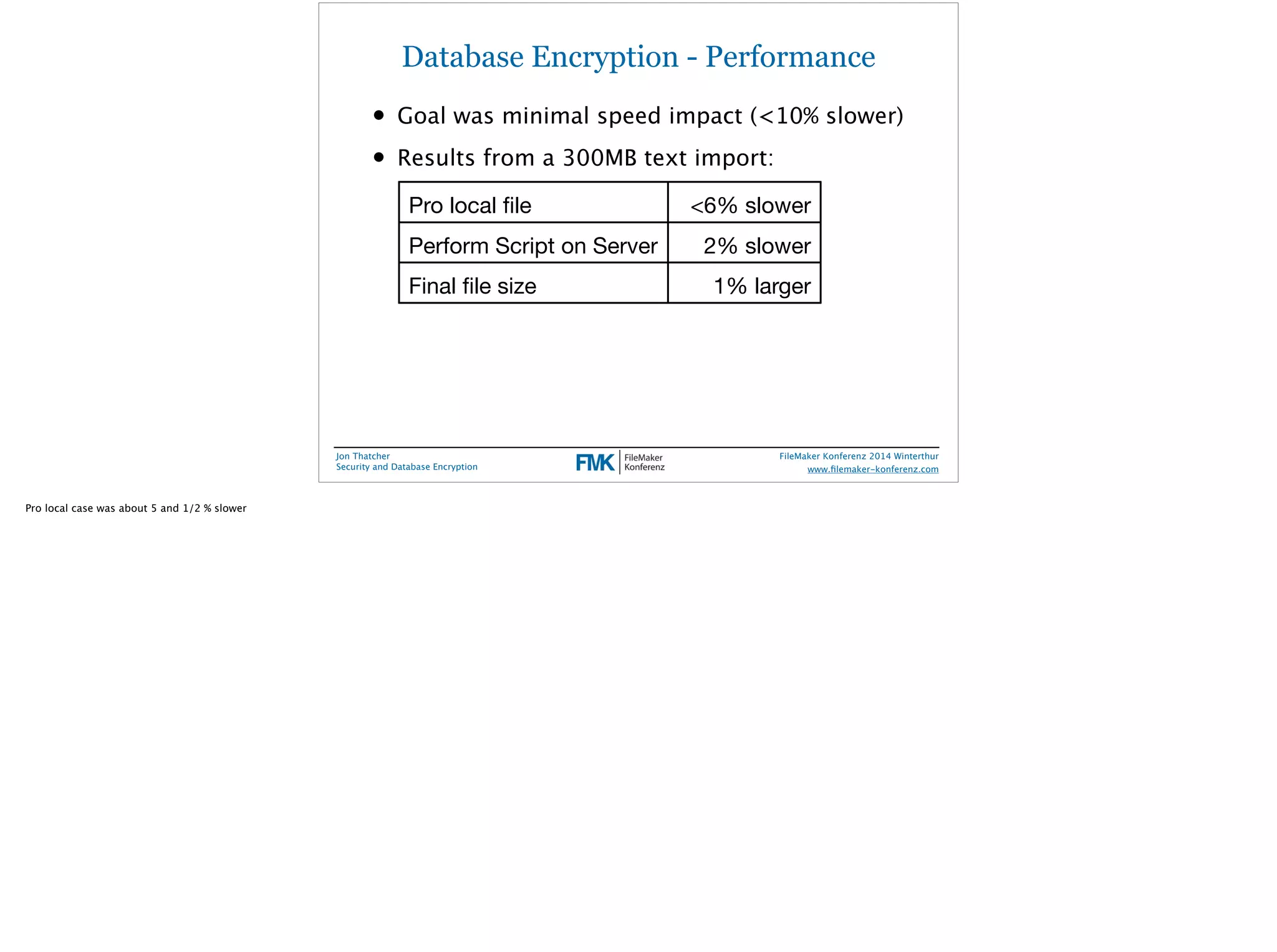
Jon Thatcher, a lead software engineer at FileMaker, Inc., presents on security and database encryption at the 2014 FileMaker Conference. The session covers the current threat landscape, attack vectors, and incident patterns, highlighting the alarming statistics on data breaches and vulnerabilities, particularly affecting small to medium businesses. Practical recommendations for enhancing database security in FileMaker solutions are also provided, emphasizing the importance of user access management and data encryption.