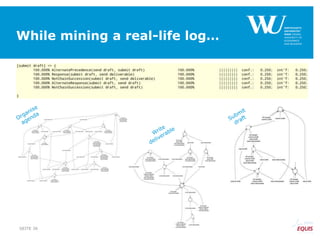
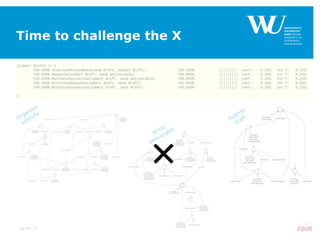
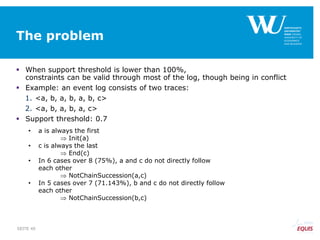
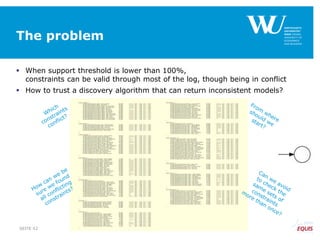
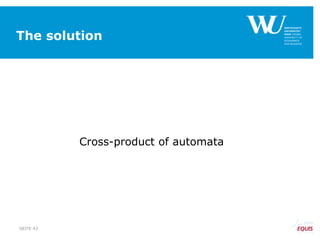
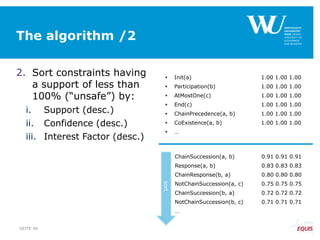
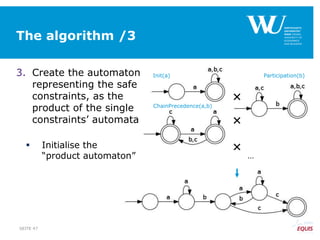
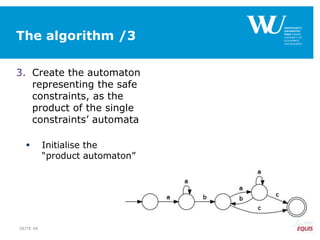
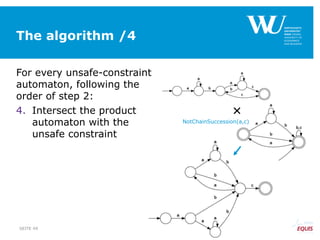
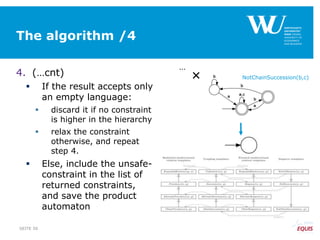
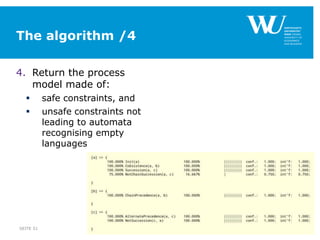
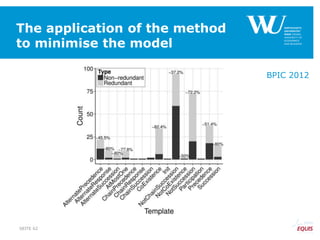
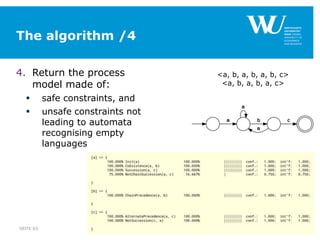
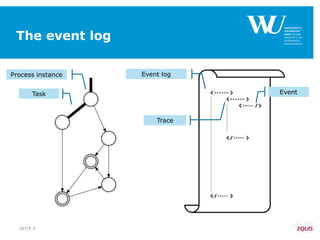
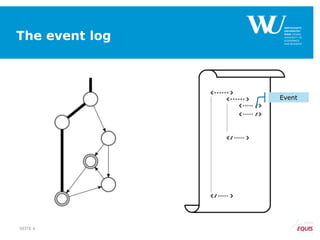
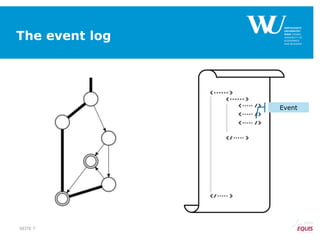
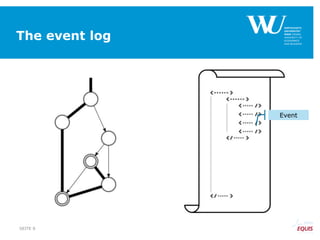
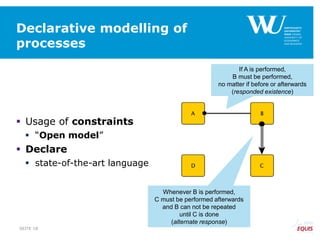
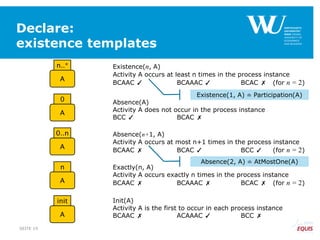
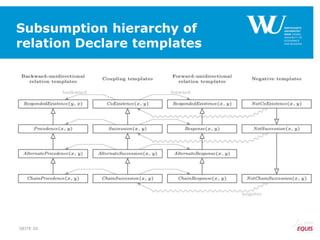
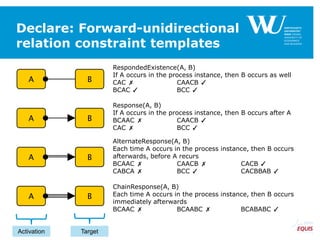
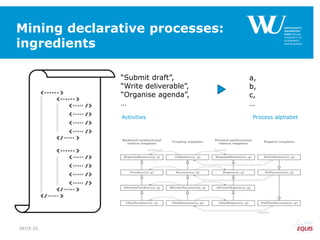
The document discusses an algorithm for ensuring consistency in declarative process discovery, highlighting how to identify and address conflicting constraints within event logs. It emphasizes the importance of safe constraints with 100% support and presents a systematic methodology for handling constraints to prevent inconsistencies in discovered process models. Limitations and future work are noted, including potential applications for mixed declarative-imperative models and user-defined criteria for constraint management.

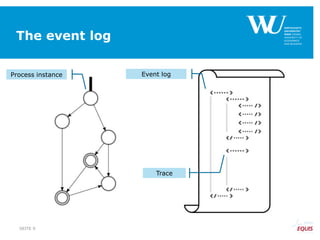
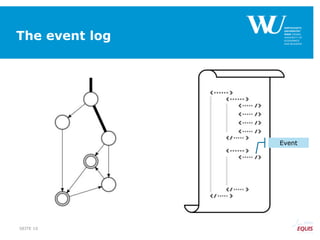
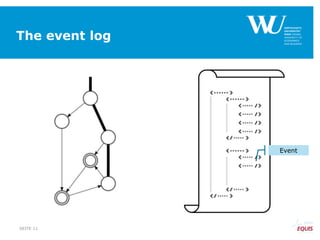
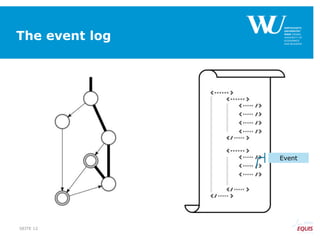


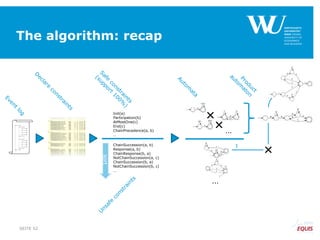
![From constraints-based model
to FSA
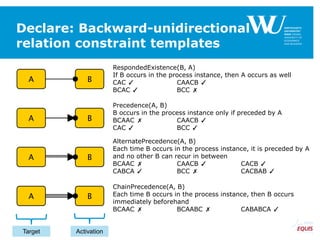
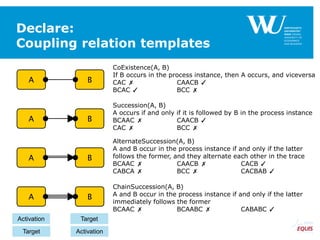
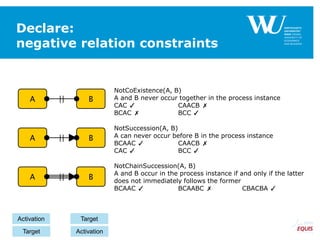
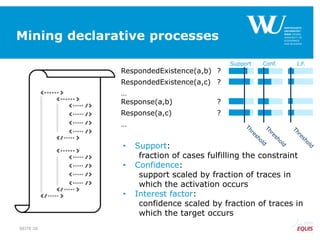
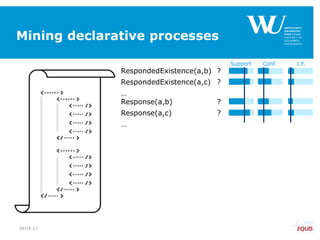
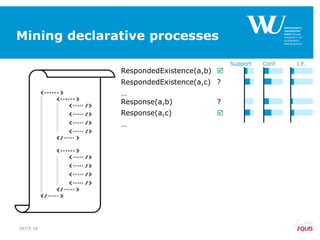
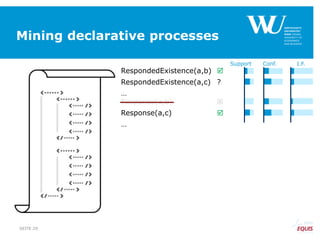
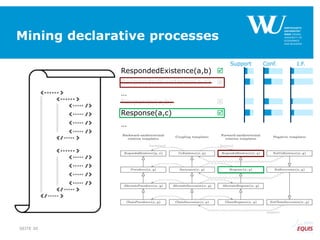
RespondedExistence(a,b)
RespondedExistence(a,c)
and
Response(a,b)
Response(a,c)
and
…
SEITE 32
[^a]*((a.*b.*)|(b.*a.*))*[^a]* [^a]*(a.*c)*[^a]*
Regular
Expression
Deterministic
Finite
State
Automaton](https://image.slidesharecdn.com/declaremodelconsistencybpm2015-150909082933-lva1-app6892/85/Ensuring-Model-Consistency-in-Declarative-Process-Discovery-32-320.jpg)
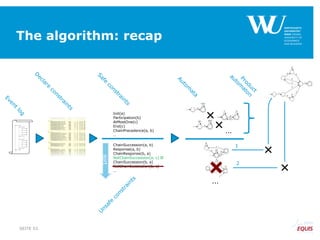
![To be kept in mind
RespondedExistence(a,b)
RespondedExistence(a,c)
and
Response(a,b)
Response(a,c)
and
…
SEITE 33
[^a]*((a.*b.*)|(b.*a.*))*[^a]* [^a]*(a.*c)*[^a]*
Regular
Expression
Deterministic
Finite
State
Automaton](https://image.slidesharecdn.com/declaremodelconsistencybpm2015-150909082933-lva1-app6892/85/Ensuring-Model-Consistency-in-Declarative-Process-Discovery-33-320.jpg)