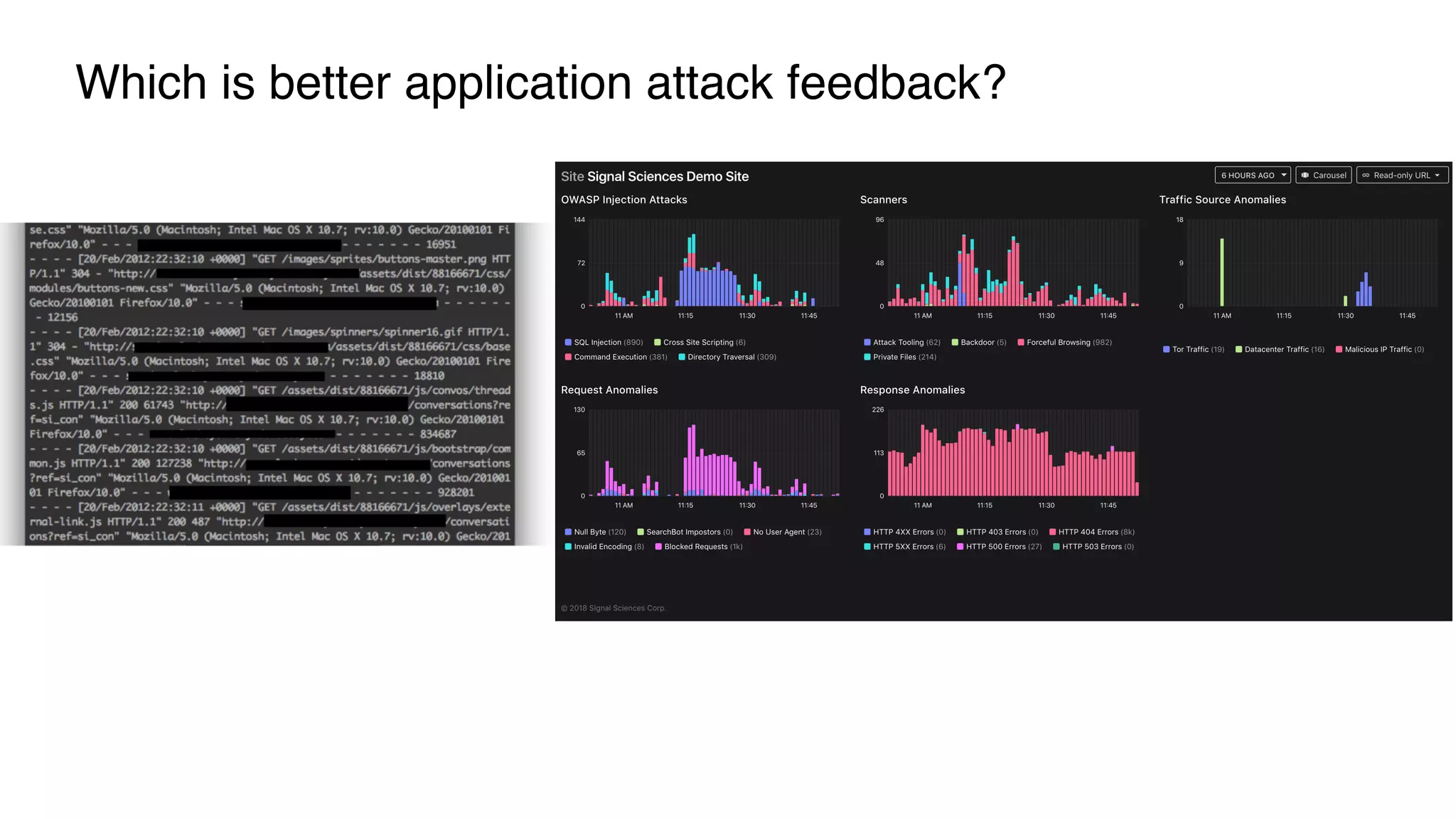
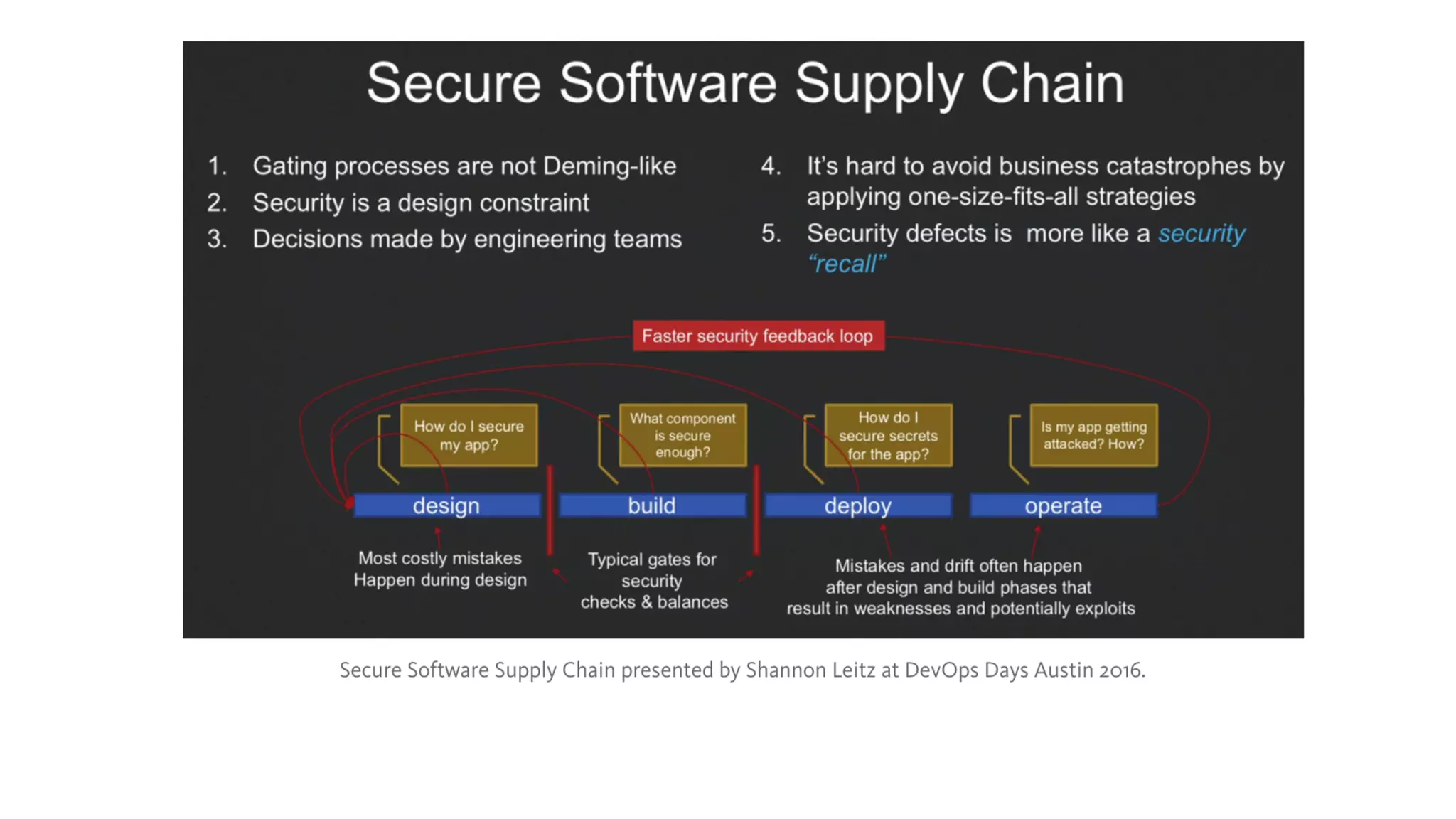
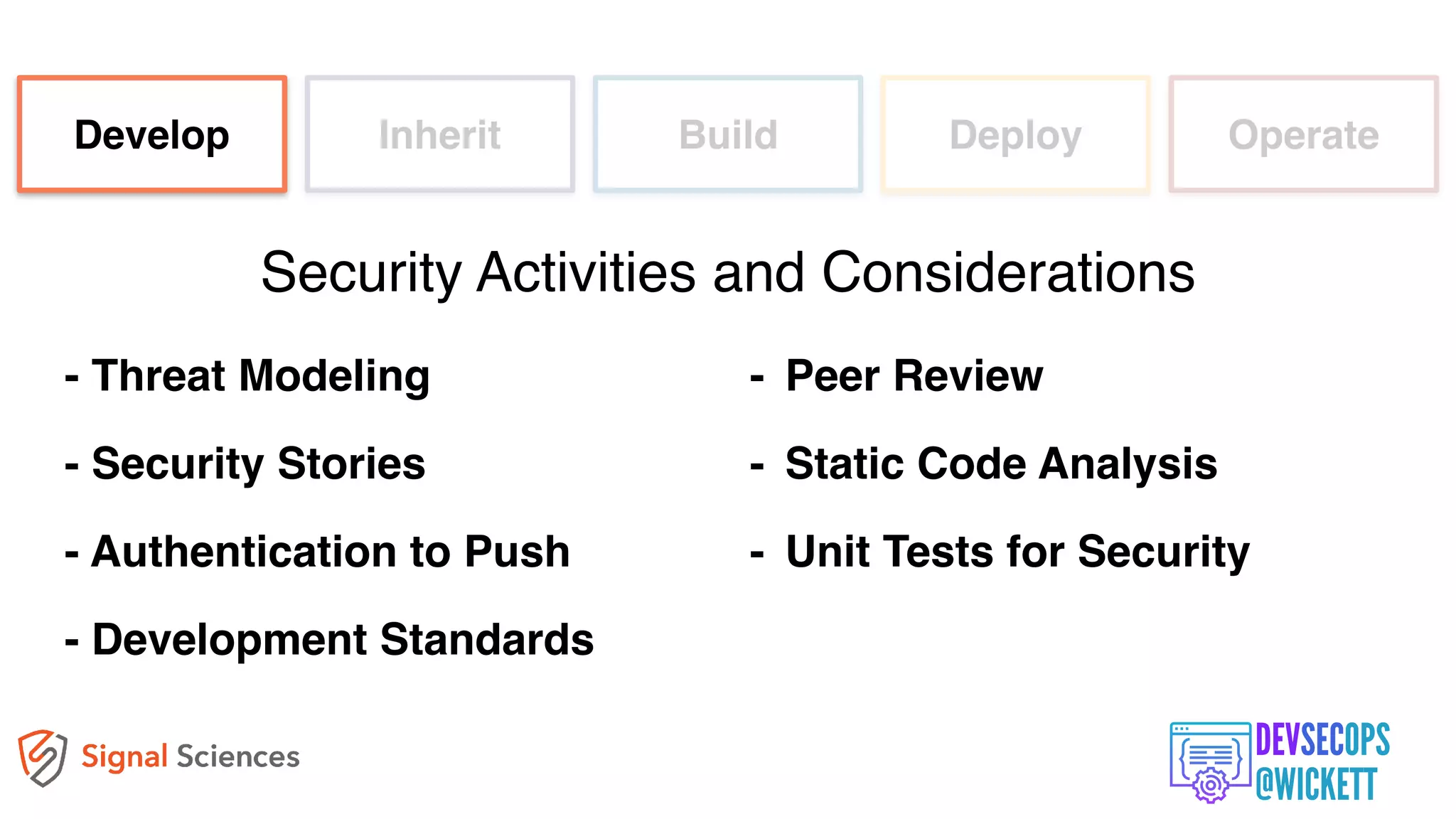
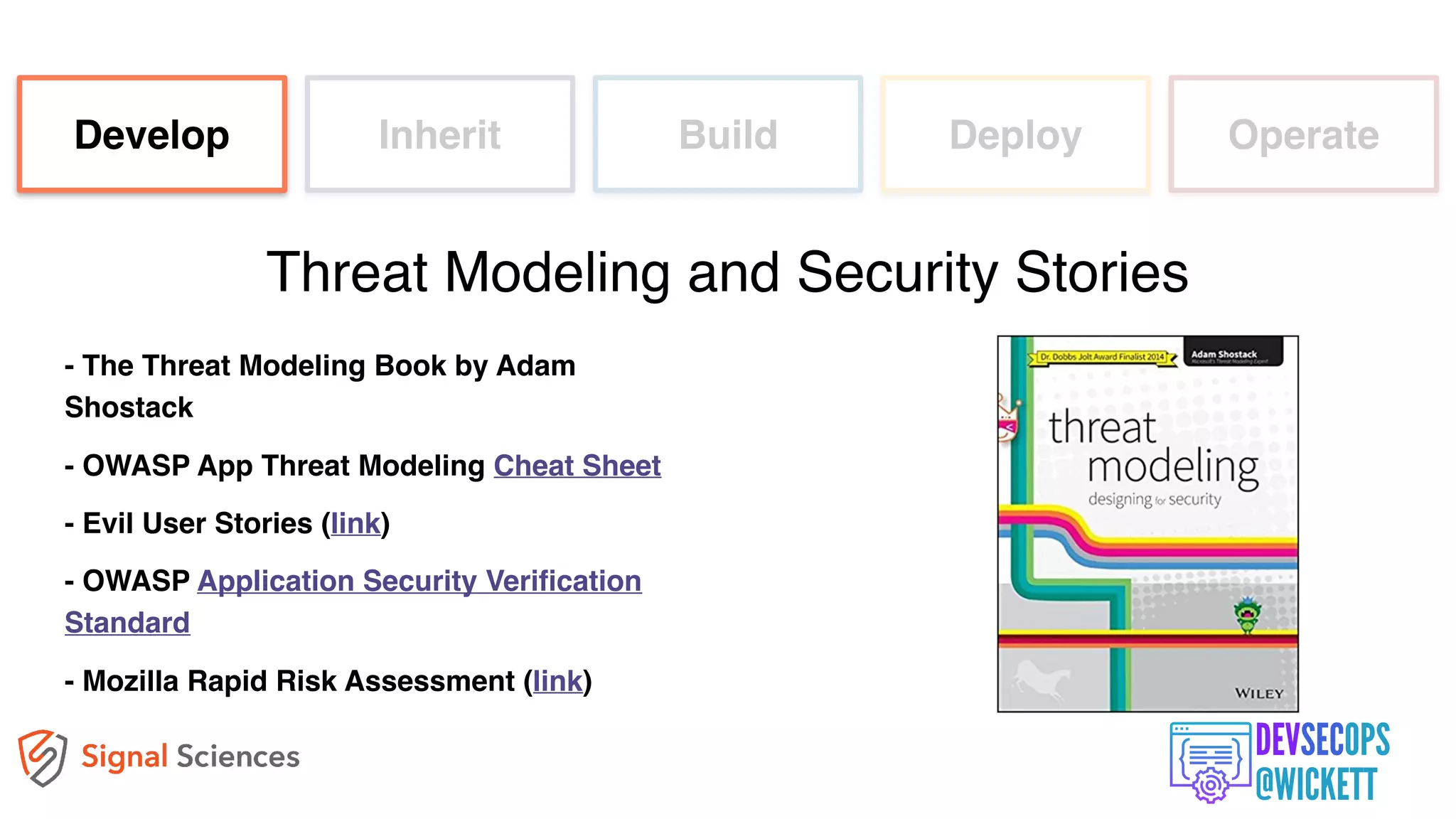
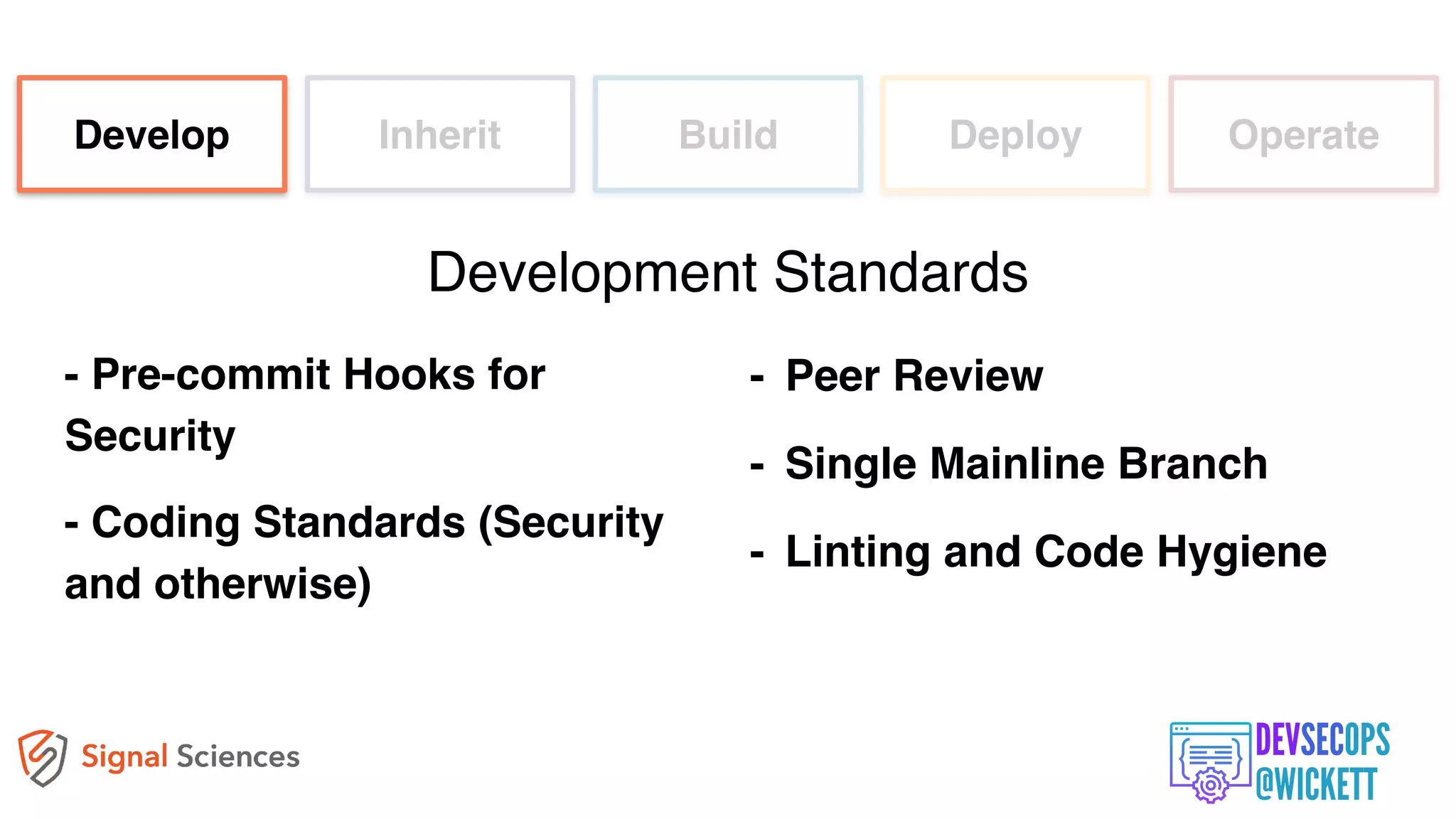
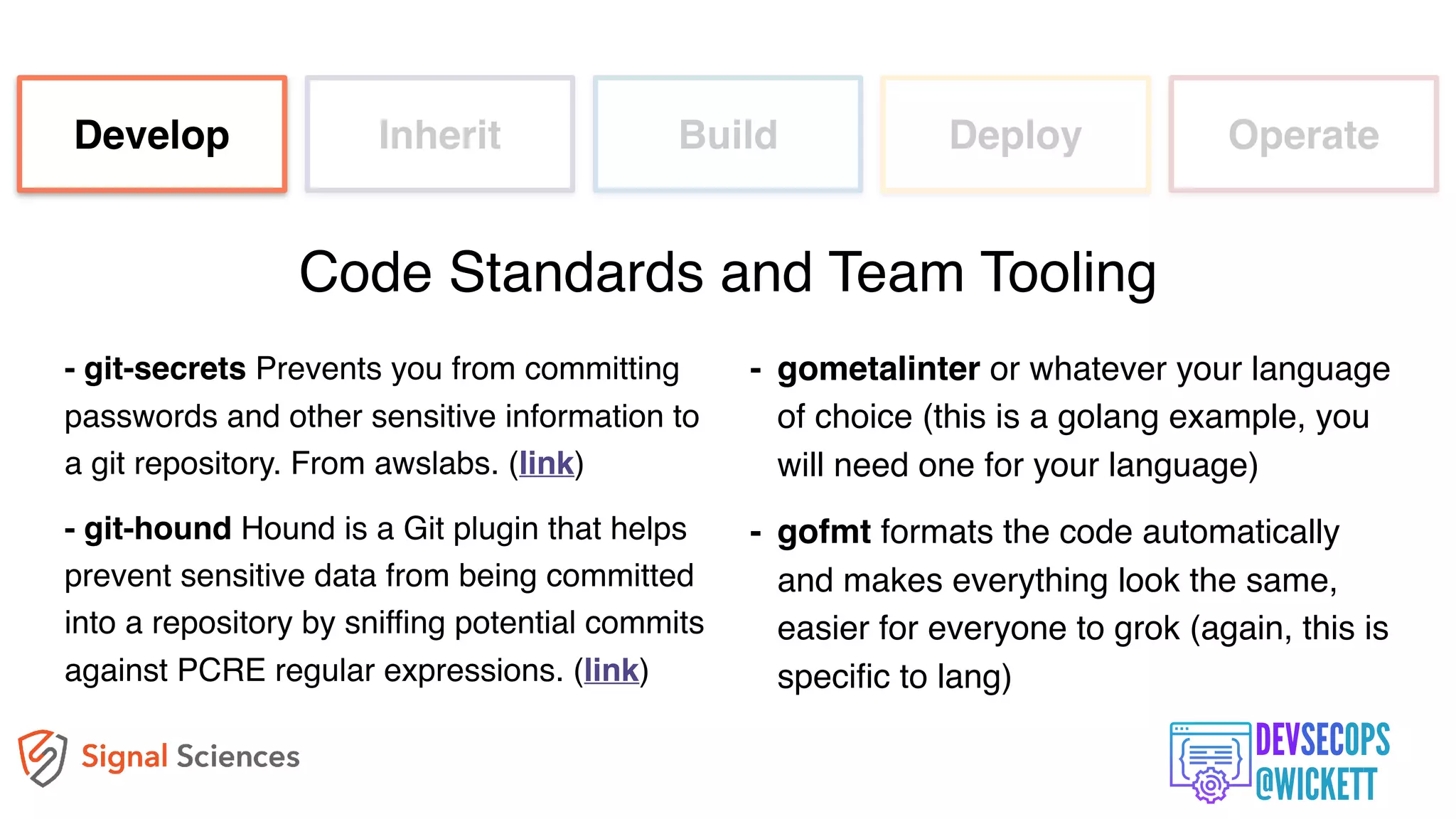
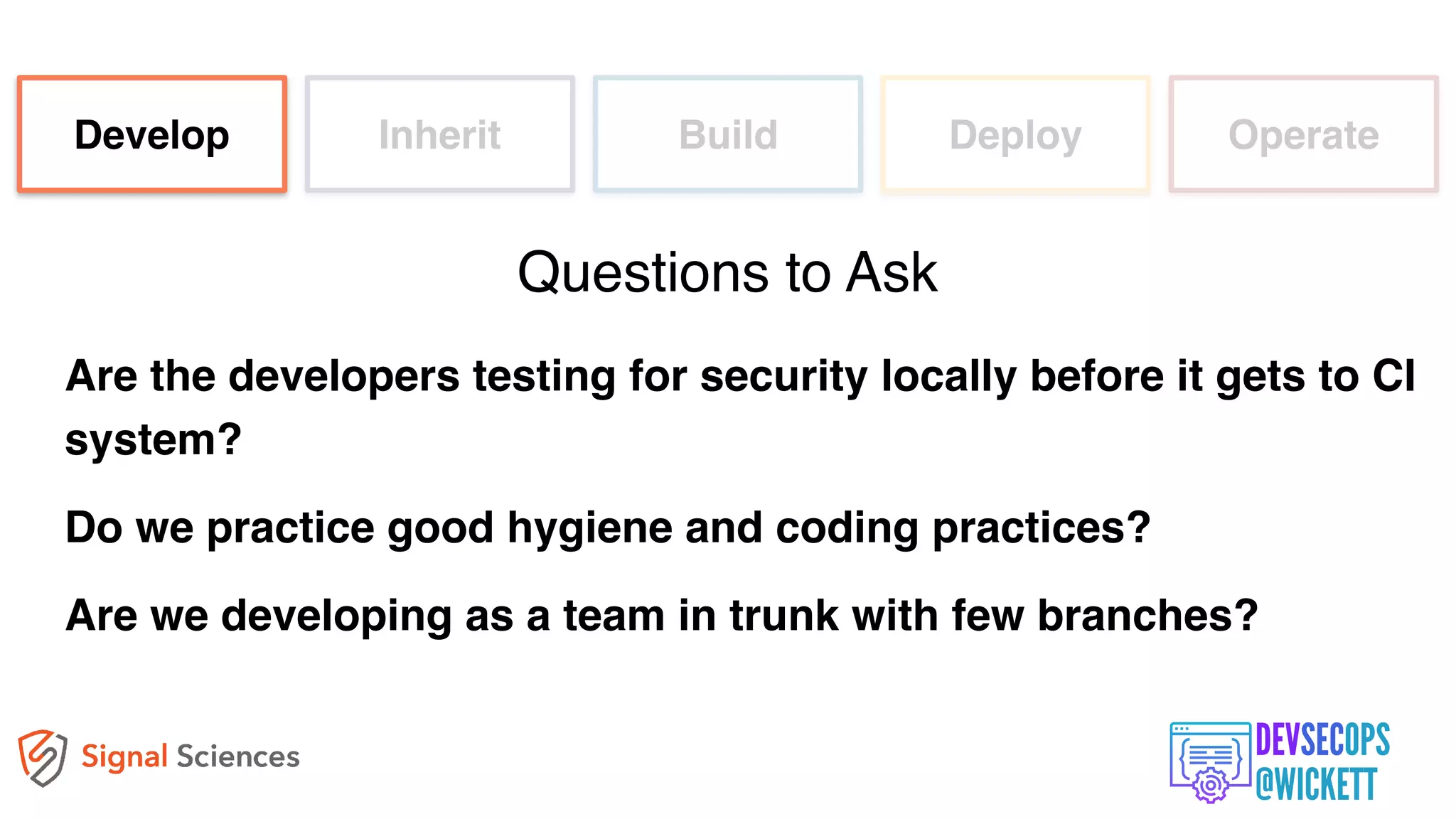
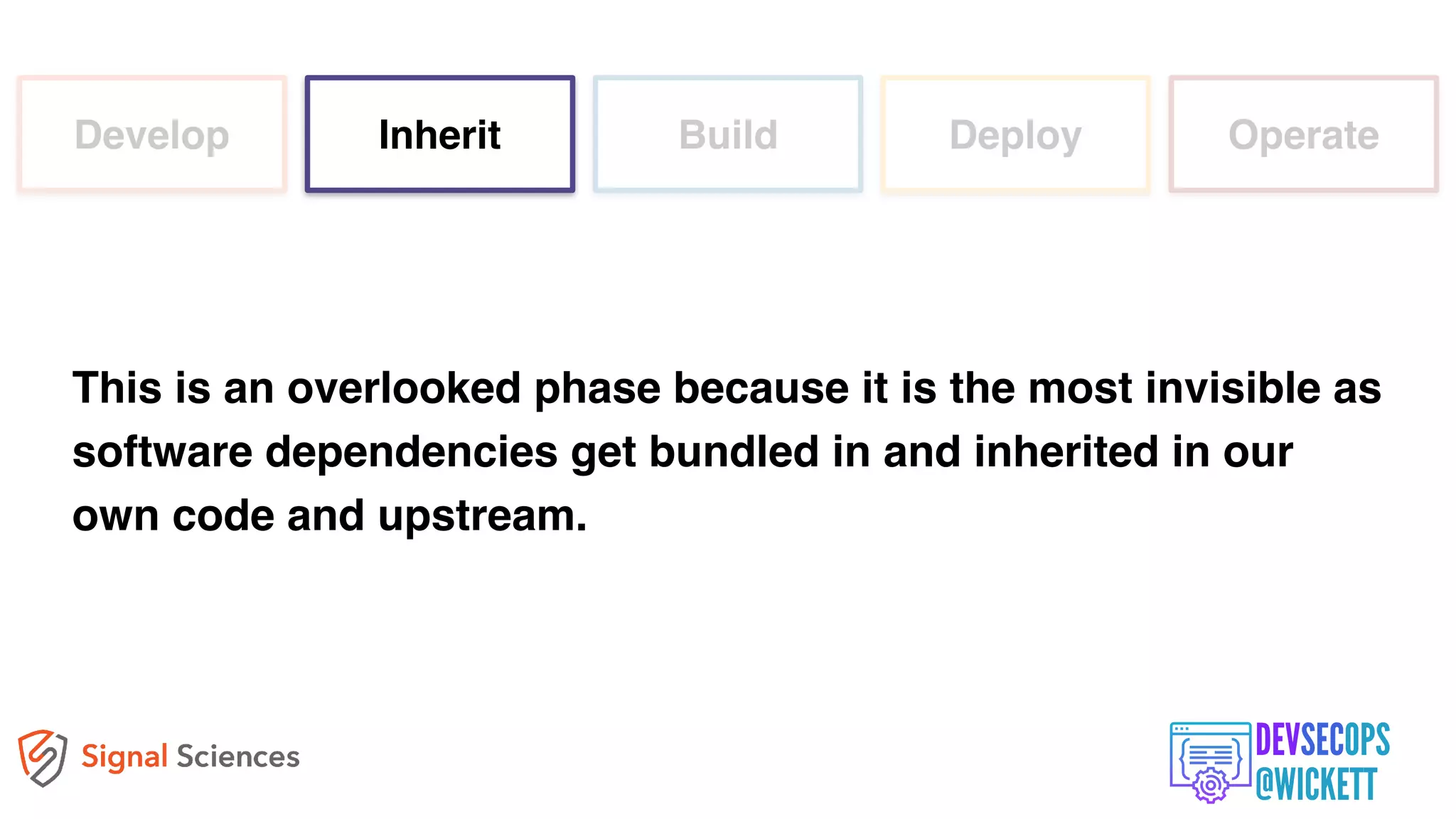
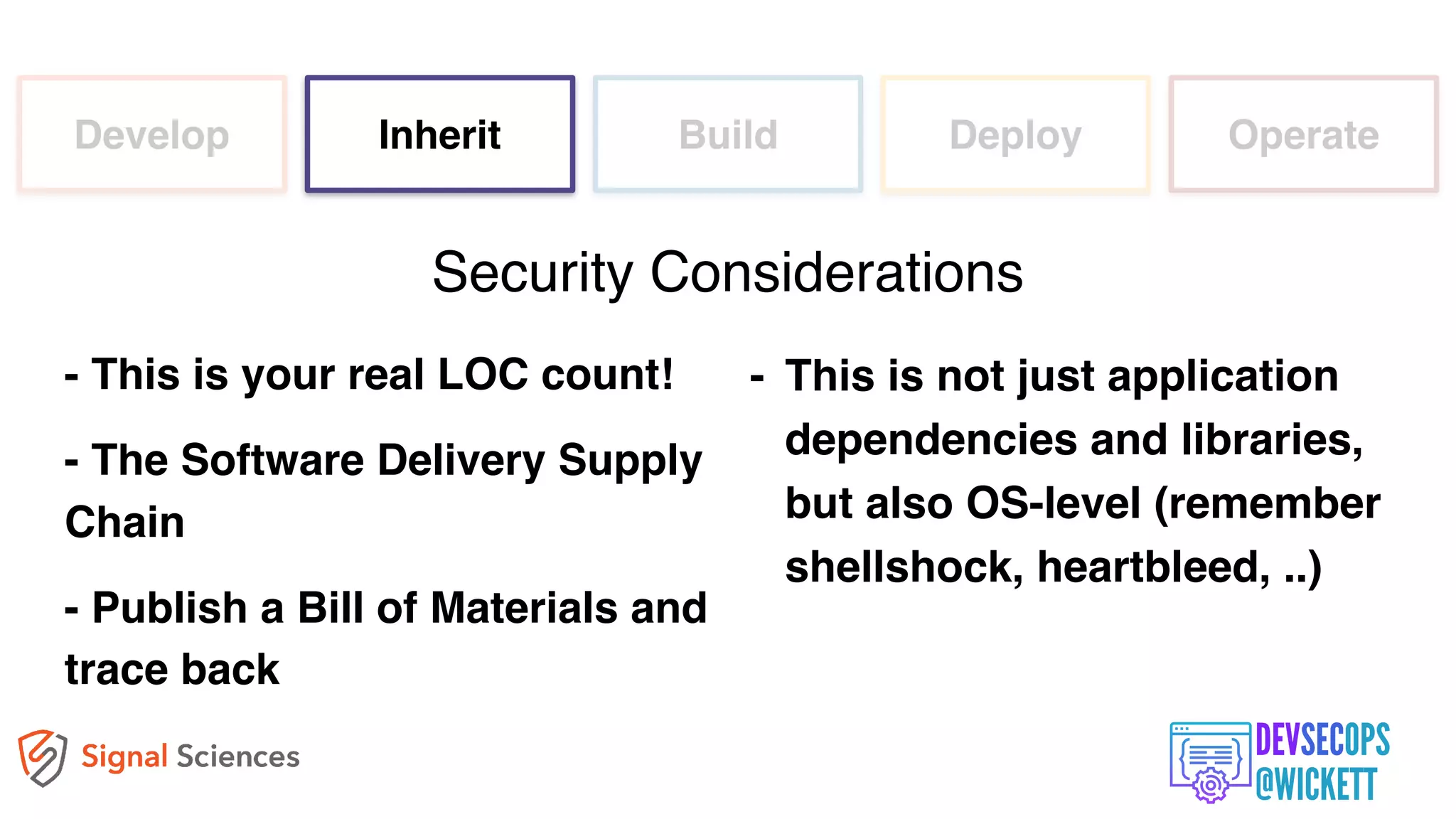
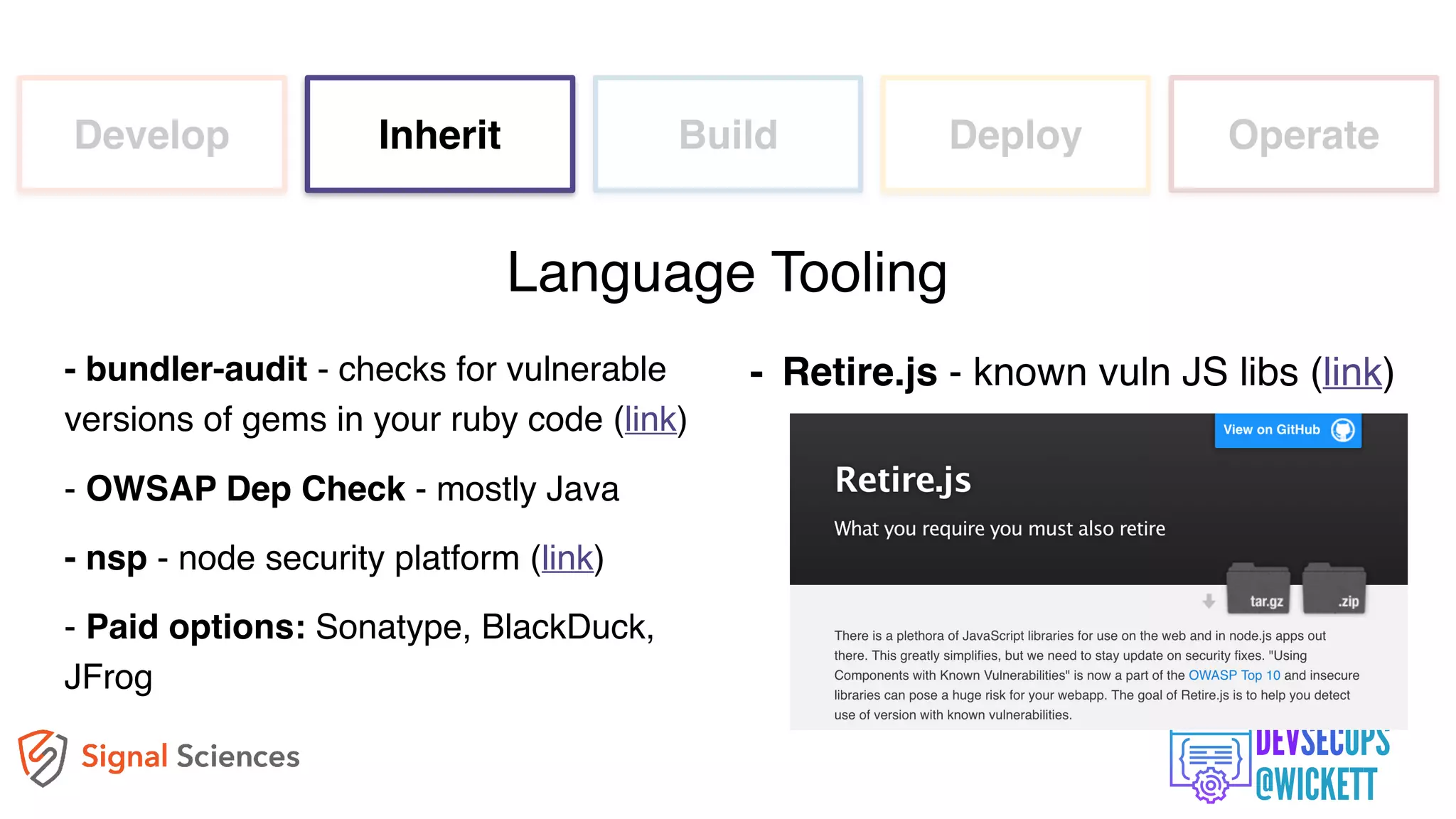
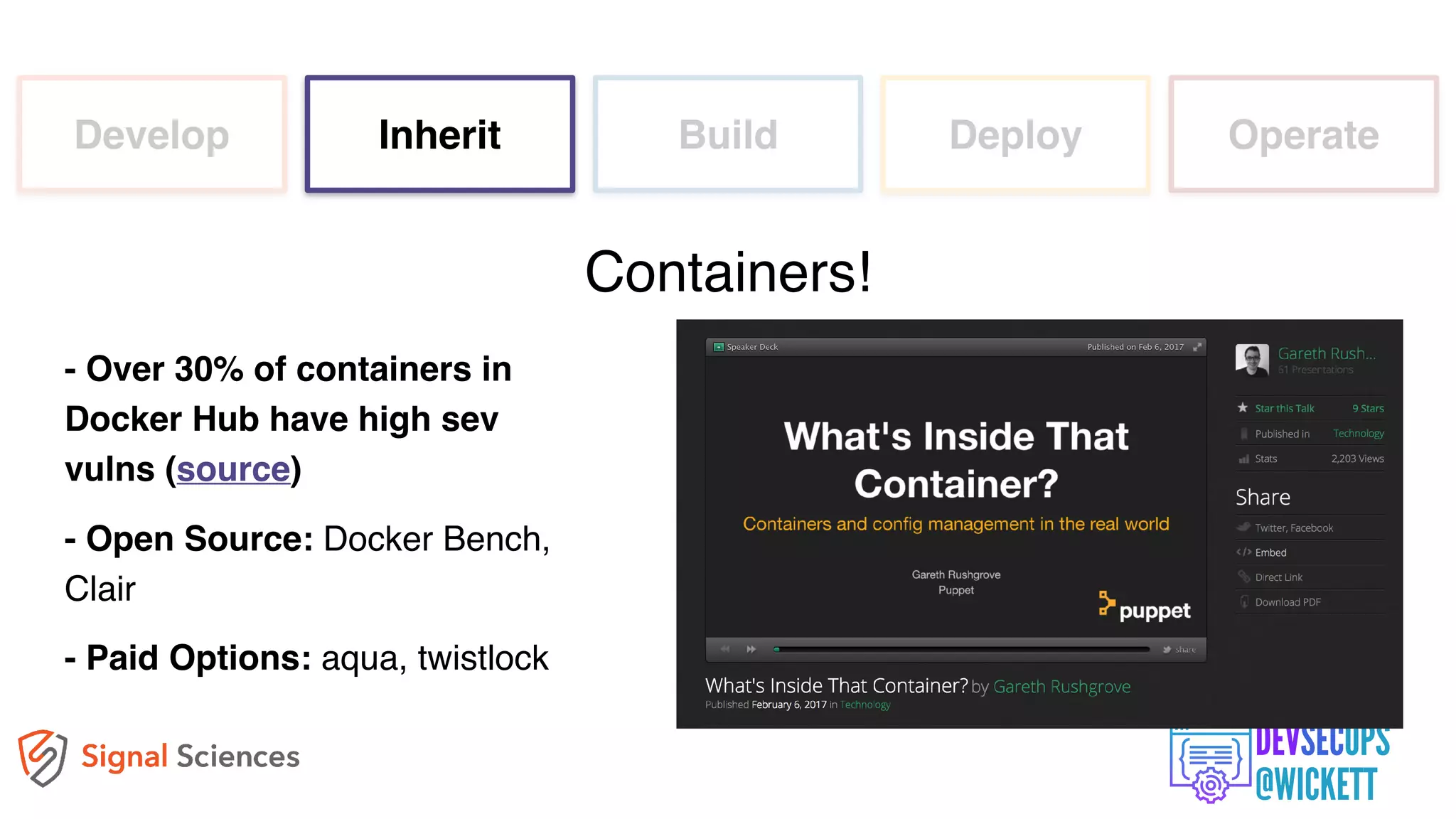
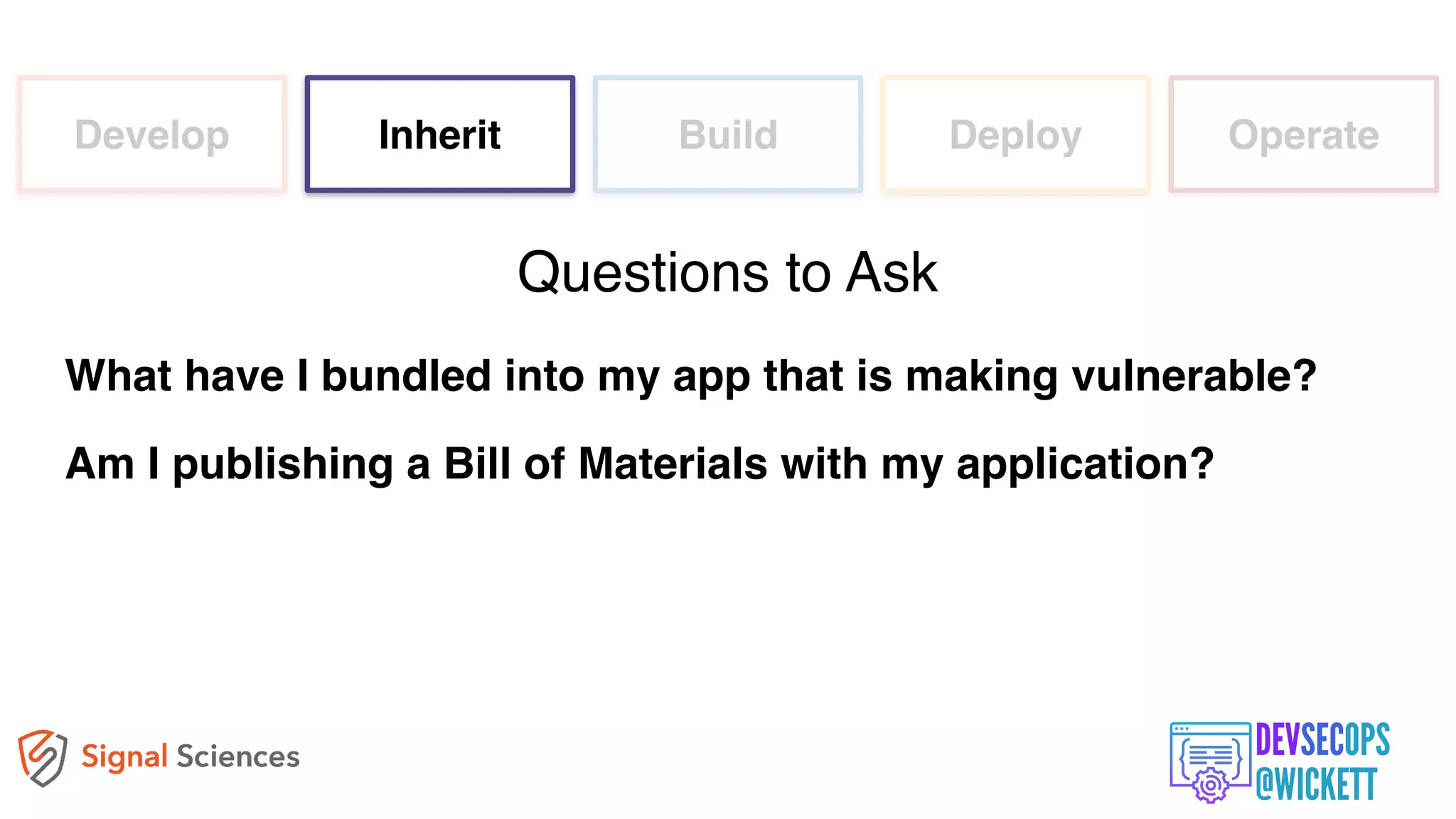
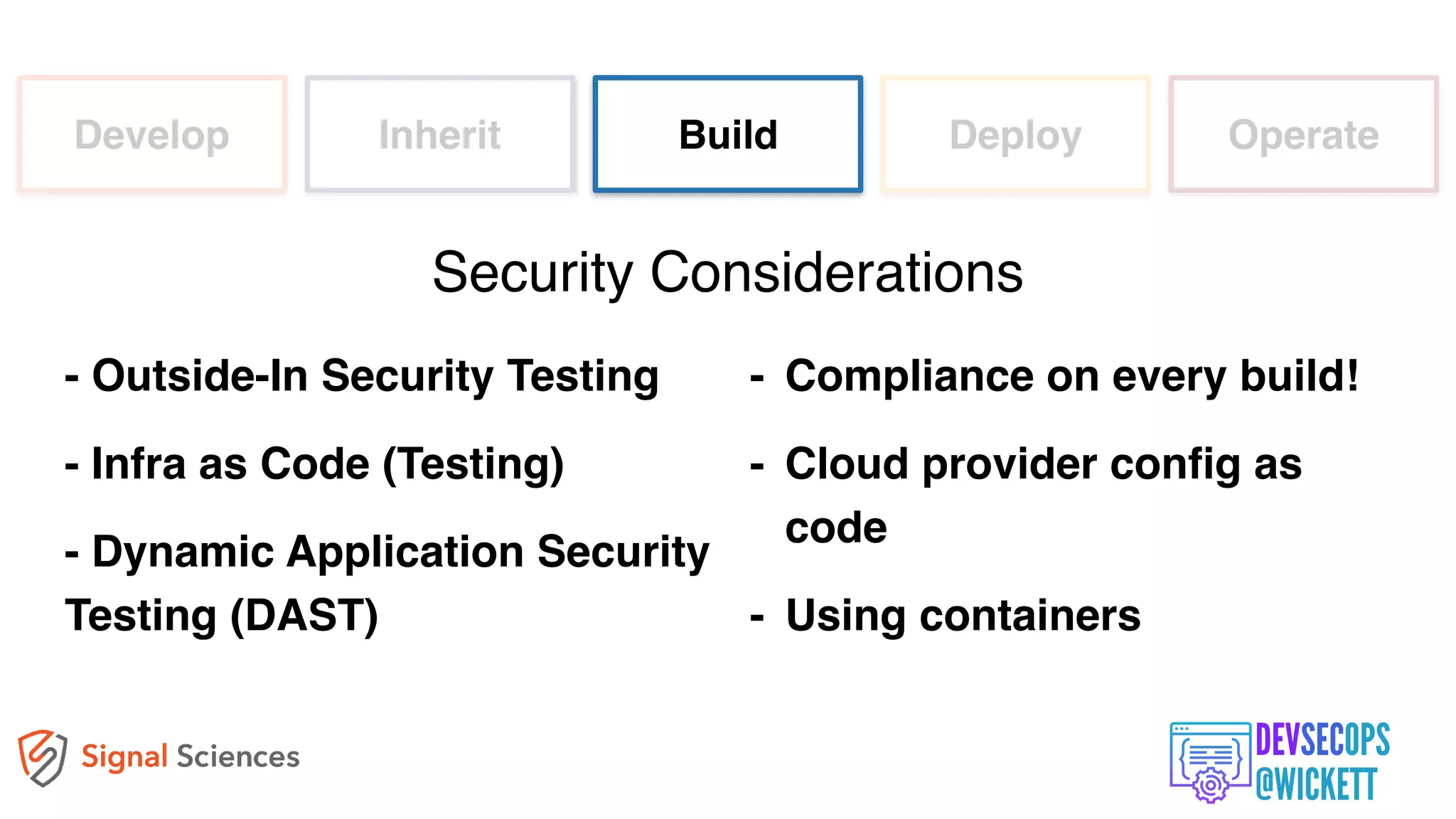
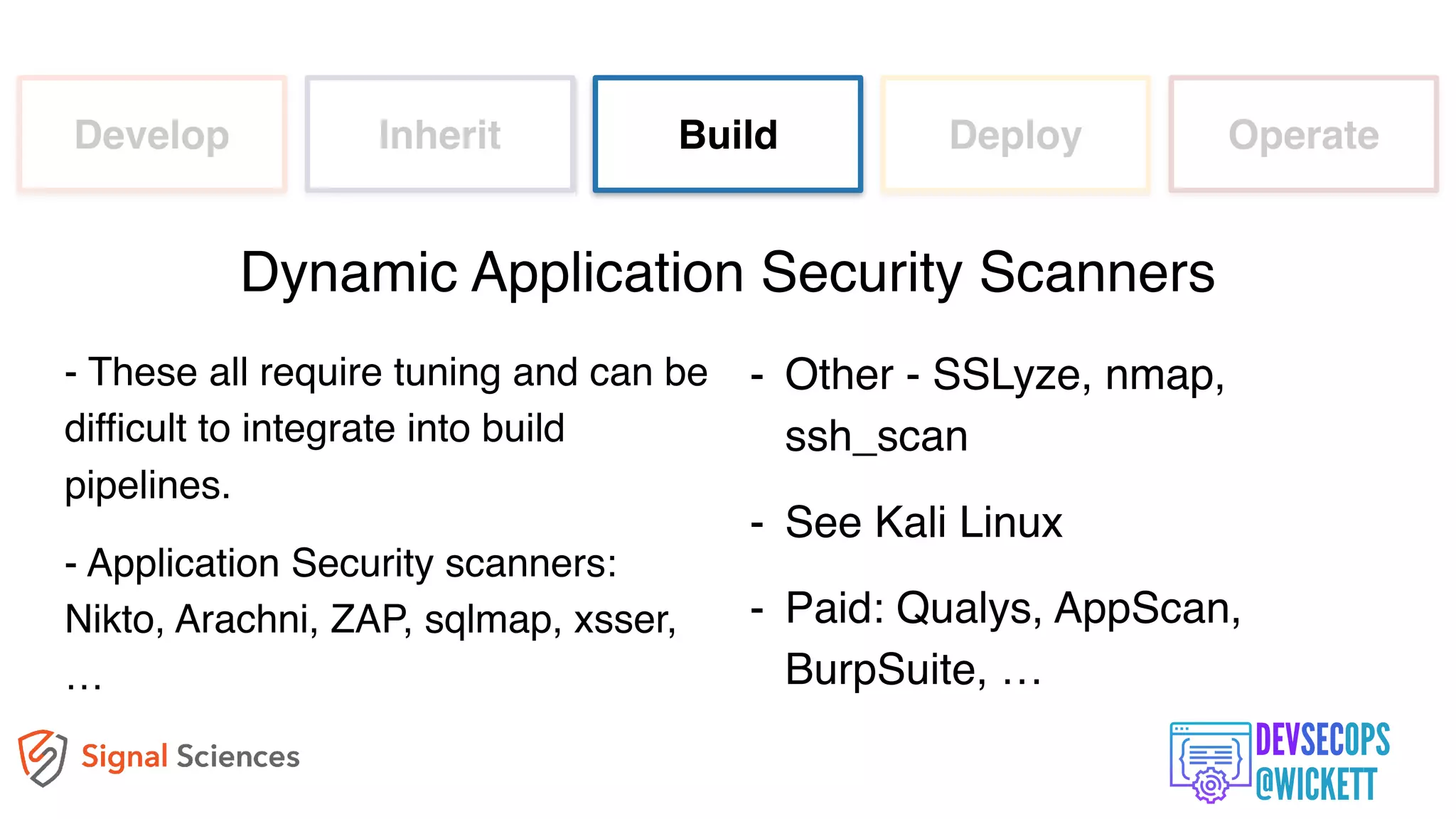
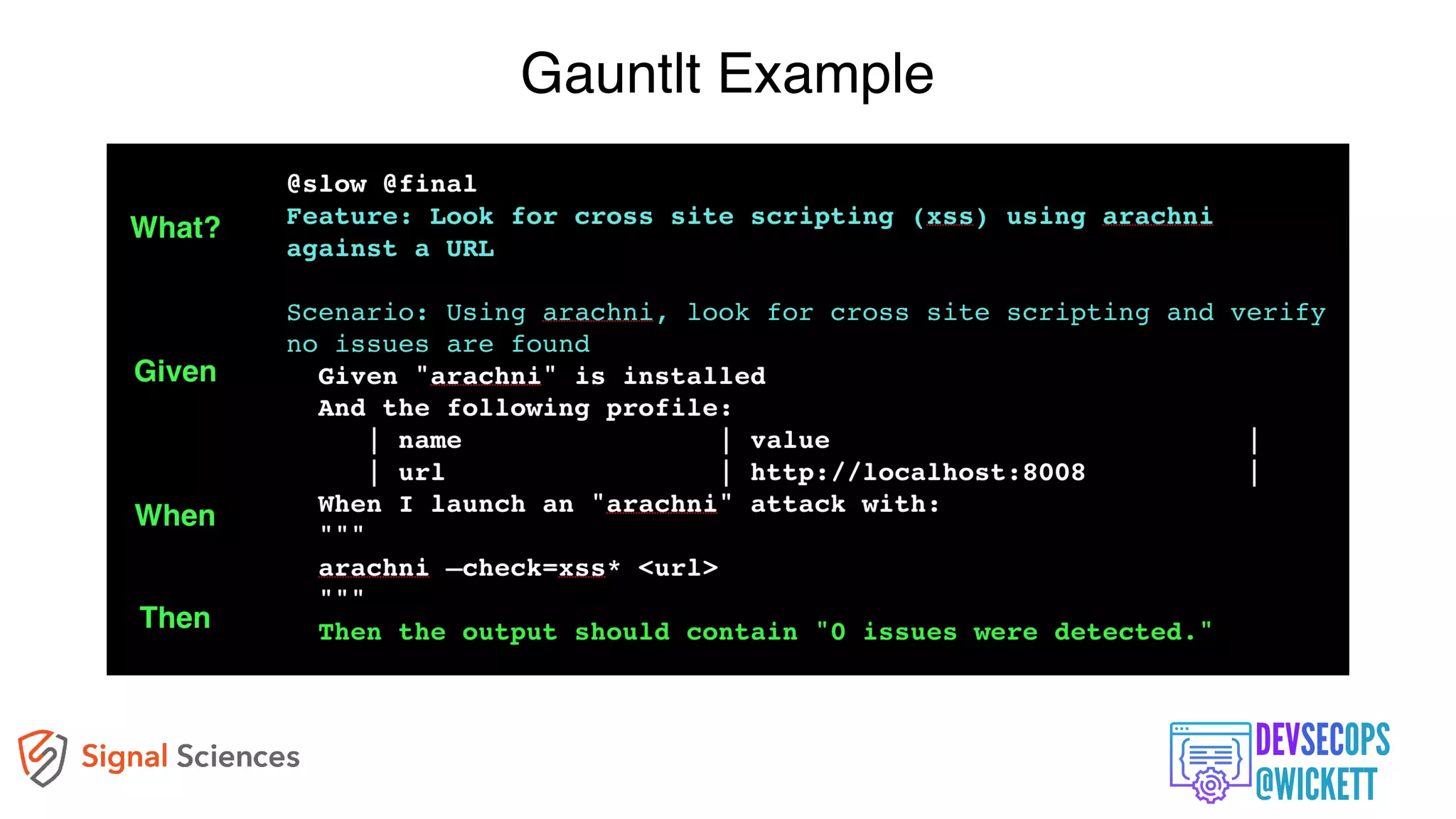
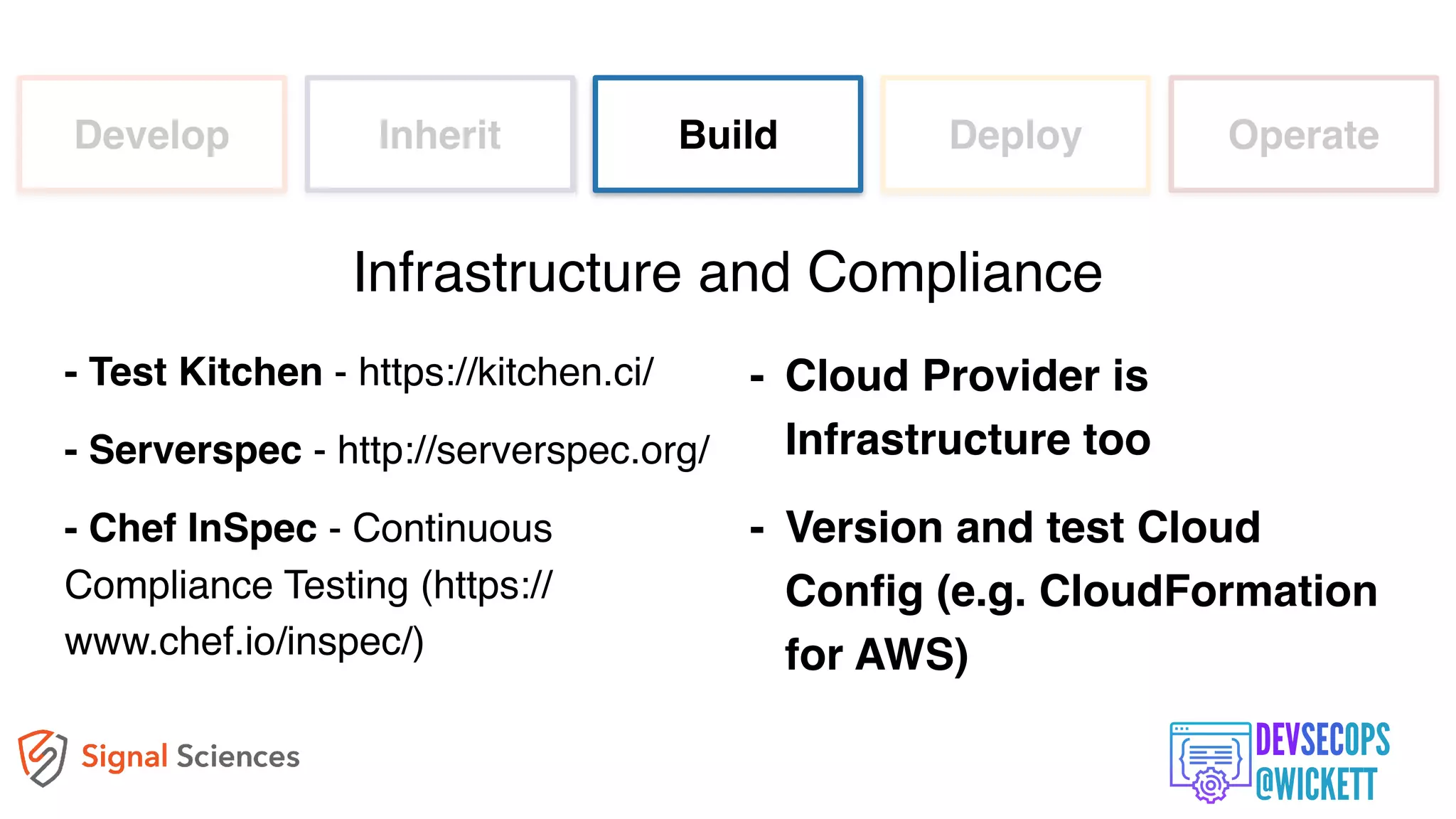
The document discusses the integration of security into the DevOps culture through a practice known as DevSecOps, emphasizing the need for collaboration between development and security teams to improve overall software delivery and security measures. It outlines various phases of the continuous integration/continuous deployment (CI/CD) pipeline while highlighting tools and techniques to enhance security throughout the development process. The document stresses the urgent need for a shift in security practices to adapt to modern development methodologies and maintain productivity.








![[Security by risk assessment]
introduces a dangerous fallacy: that
structured inadequacy is almost as
good as adequacy and that
underfunded security efforts plus risk
management are about as good as
properly funded security work](https://image.slidesharecdn.com/devsecops-pipeline-sept2018-180926025301/75/DevSecOps-and-the-CI-CD-Pipeline-10-2048.jpg)






























![[Deploys] can be treated as
standard or routine changes
that have been pre-approved
by management, and that
don’t require a heavyweight
change review meeting.](https://image.slidesharecdn.com/devsecops-pipeline-sept2018-180926025301/75/DevSecOps-and-the-CI-CD-Pipeline-75-2048.jpg)