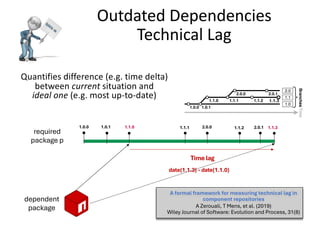
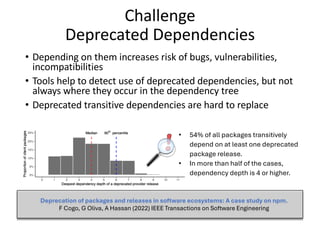
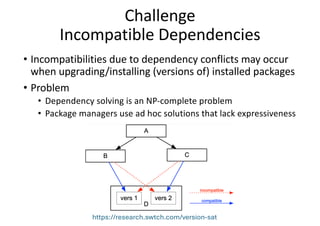
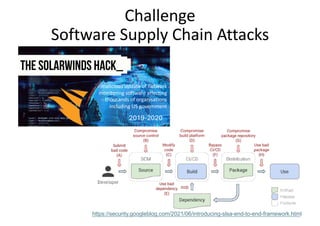
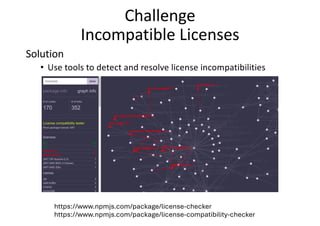
The document discusses the various dependency issues in open source software package registries, including outdated, deprecated, and incompatible dependencies, and the risks associated with software supply chain attacks. It highlights the challenges faced by maintainers and the potential for security vulnerabilities and legal issues arising from dependency management. Solutions are suggested, such as using monitoring tools, semantic versioning, and community maintenance organizations to improve the sustainability and reliability of software ecosystems.