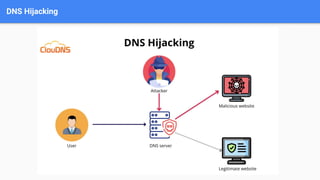
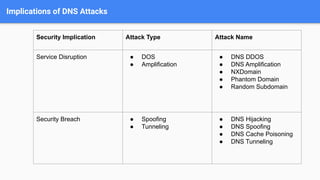
Demystifying DNS Attacks provides an in-depth exploration of malicious DNS activities, including different types of DNS attacks such as denial of service, cache poisoning, hijacking, and data exfiltration attacks. It describes techniques for each attack type, such as DNS amplification and spoofing for denial of service and cache poisoning attacks. The document also covers implications of DNS attacks like service disruption and security breaches. It proposes mitigation techniques including DNSSEC, DOH/DoT, security audits, and ODoH to enhance DNS security and privacy.