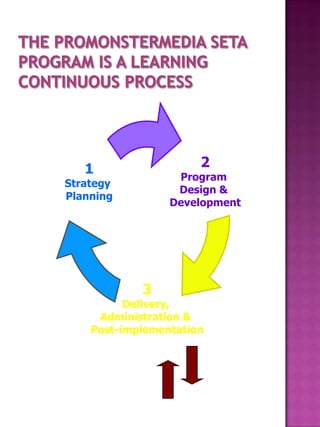
The document outlines the essential components of an incident response plan and security policy, emphasizing the importance of education, training, and stakeholder involvement in maintaining information security. It details the roles of senior management, steering committees, and development teams, as well as the necessity for ongoing monitoring, vulnerability assessments, and compliance with legal and regulatory standards. The document also provides cost estimates related to the security training and awareness program implementation.

![ Incident Response Plan
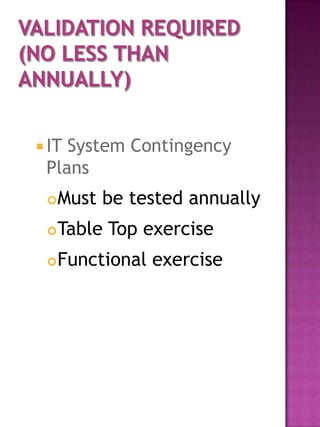
Security Requirements
Information System
Security Policy
Contingency Plan
Security Education,
Training and Awareness
Program [SETA]](https://image.slidesharecdn.com/databasedevelopmentandsecuritycertificationandaccreditationplan-pitwg-100416193820-phpapp02/85/Database-development-and-security-certification-and-accreditation-plan-pitwg-2-320.jpg)


















































![What is Security Education,
Training and Awareness
[SETA] Plan?
Michael Whitman (2006) stated that
a SETA plan is a: “Program
designed to provide direct,
applied measures to influence
employee behavior, increase
employee abilities and enable the
organization to hold employees
accountable for their actions.” (p.
22.).
Now, why educating, training and
People awareness is so important
for protecting and Securing
Critical or sensitive information?](https://image.slidesharecdn.com/databasedevelopmentandsecuritycertificationandaccreditationplan-pitwg-100416193820-phpapp02/85/Database-development-and-security-certification-and-accreditation-plan-pitwg-58-320.jpg)

![The Weakest Link
The most secure Point of Failure in any Security
program.
Security is everyone's
responsibility!
According to Wilson & Hash (2003) the
key factor to provide security is not
the technology or the state of the art
efforts to protect and secure the
Information Systems [IS].
To provide adequate information
security the people factor is the key
factor because they are the system’s
weakest link. (p. 1)
SEC_RITY is not complete without
U!](https://image.slidesharecdn.com/databasedevelopmentandsecuritycertificationandaccreditationplan-pitwg-100416193820-phpapp02/85/Database-development-and-security-certification-and-accreditation-plan-pitwg-60-320.jpg)









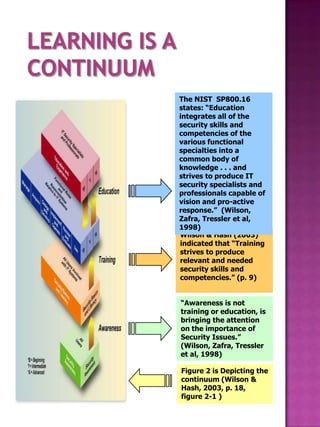




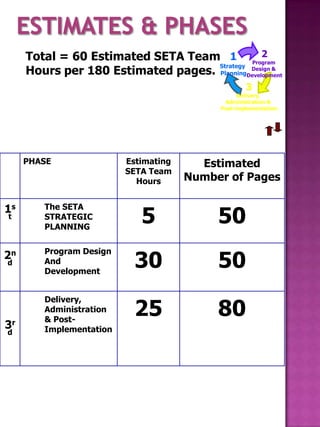
![Estimate based for completion of 180
pages
1 SETA Security Team hours equals $250.00 US
Dollars [USD]
Estimated Total of pages equals 180
Estimated Total amount of SETA Security Team
equals 60
Estimate Appendix “O” SETA plan cost 60
SETA
Security TEAM hours x $250.00 per
hours = $15,000.00 US Dollars
Other expenses and Misc. = 5,000.00
USD
ESTIMATED TOTAL COST =
$20,000.00](https://image.slidesharecdn.com/databasedevelopmentandsecuritycertificationandaccreditationplan-pitwg-100416193820-phpapp02/85/Database-development-and-security-certification-and-accreditation-plan-pitwg-81-320.jpg)






![2007 LandWarNet Conference. (2007, Aug 21) Notes
Addison, S. (July 3, 2007) Best Practices for Security
Awareness Training. Security-awareness.com. Retrieved on
October 24, 2007, from http://security-awareness-
training.com/2007/07/23/best-practices-for-security-
awareness-training/
Bowen, p. Hash, J. & Wilson, M.(2006). Information Security
Handbook. Retrieved October26, 2007, from
http://www.nist.gov
Brackin, C. (2003). Vulnerability Management: Tools,
Challenges, & Best Practices. Retrieved October 26, 2007,
from http://www.sans.org/reading room
Business Resumption Development Guide (2006, May 5) Buckley
King LPA
Canavan, S. & Diver, S. (2007). Information Security Policy- A
Development Guide for Large & Small Companies.
Retrieved October 26, 2007, from
http://www.sans.org/reading room
Department of Defense [DoD]. (July 31, 2000). Information
Technology Security
Certification and Accreditation Process (DITSCAP).
Application Manual DoD 8510.1-M. Retrieved October 24,
2007, from
http://www.dtic.mil/whs/directives/corres/pdf/851001m.
pdf](https://image.slidesharecdn.com/databasedevelopmentandsecuritycertificationandaccreditationplan-pitwg-100416193820-phpapp02/85/Database-development-and-security-certification-and-accreditation-plan-pitwg-88-320.jpg)

![G. (2002). Implementing an Effective IT Security Program.
Retrieved October 27, 2007,
from http://www.sans.org/reading room
GadAllah, S. (2003). The Importance of Logging & Traffic
Monitoring for Information
Security. Retrieved October 27, 2007, from
http://www.sans.org/reading room
Iase.disa.mil. Information Assurance Support Environment Profile:
Retrieved October
26, 2007, from http://iase.disa.mil/
Information Security Oversight Office [ISOO]. (2005). Report On
Cost Estimates For
Security Classification Activities Background And Methodology.
Retrieved on October
28, 2007, from http://www.archives.gov/isoo/reports/2005-
cost-report.html
Kyle, S. (2003). Biometrics: An In Depth Examination. Retrieved
October 27, 2007, from
http://www.sans.org/reading room
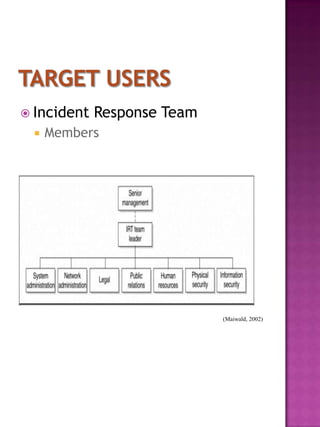
Maiwald, Eric. Security Planning and Disaster Recovery. Blacklick,
OH, USA: McGraw-Hill Professional, 2002.
National Computer Security Center (NCSC).(1987). A Guide to
Understanding Audit in
Trusted Systems. Retrieved October 27, 2007, from
http://csrc,ncsl.nist.gov/publications/secpubs/rainbow/tg001.tx
t](https://image.slidesharecdn.com/databasedevelopmentandsecuritycertificationandaccreditationplan-pitwg-100416193820-phpapp02/85/Database-development-and-security-certification-and-accreditation-plan-pitwg-90-320.jpg)


