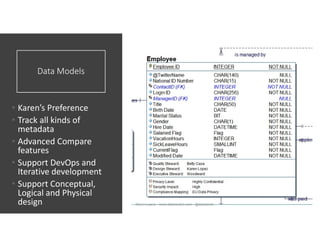
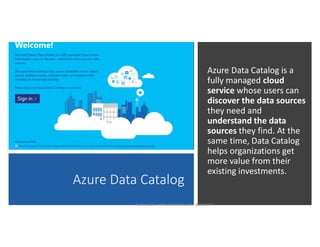
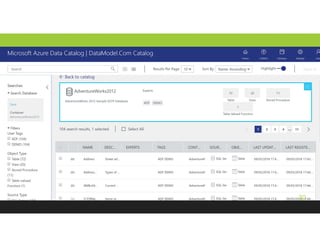
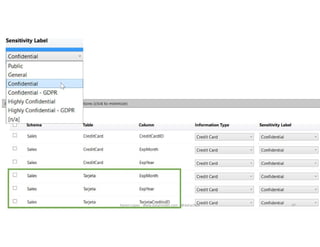
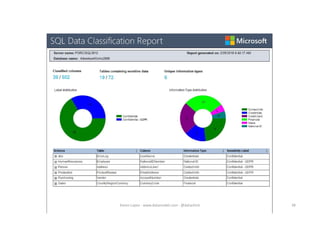
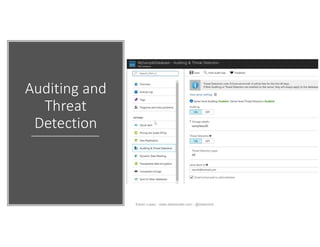
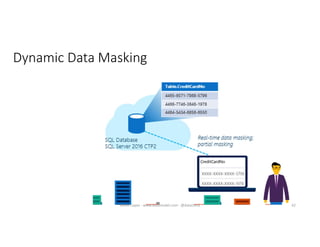
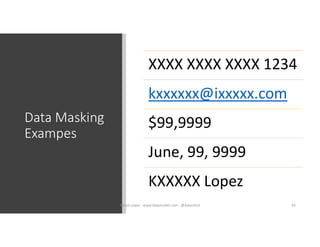
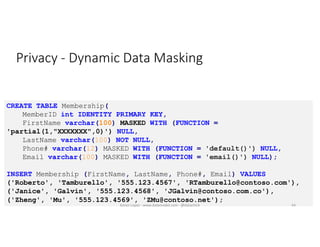
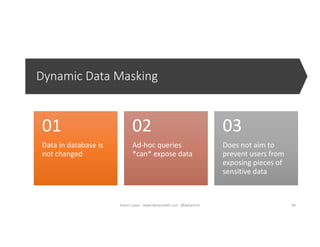
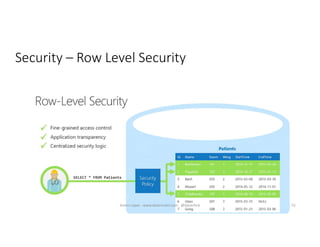
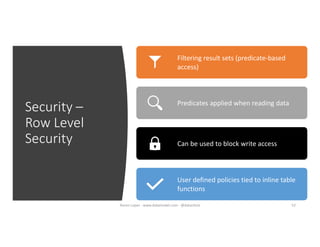
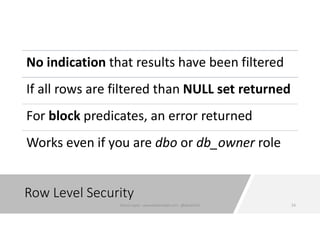
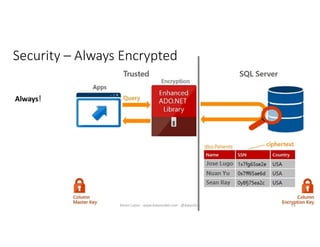
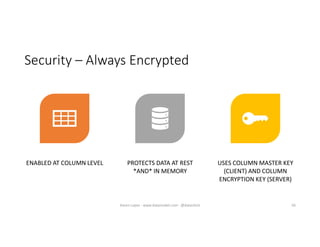
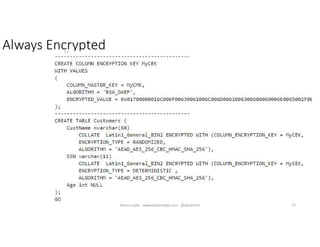
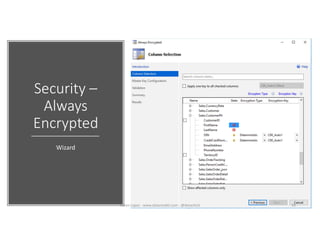
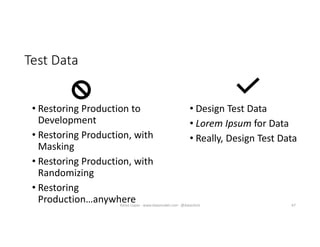
The document discusses securing and protecting data in DevOps environments. It covers topics such as data discovery, classification, curation, cataloging data assets, assessing risks, auditing, dynamic data masking, row-level security, always encrypted columns, and building a culture of data security. The presentation encourages cataloging all data, classifying its sensitivity, designing test data separately from production data, and continually monitoring and testing security practices.