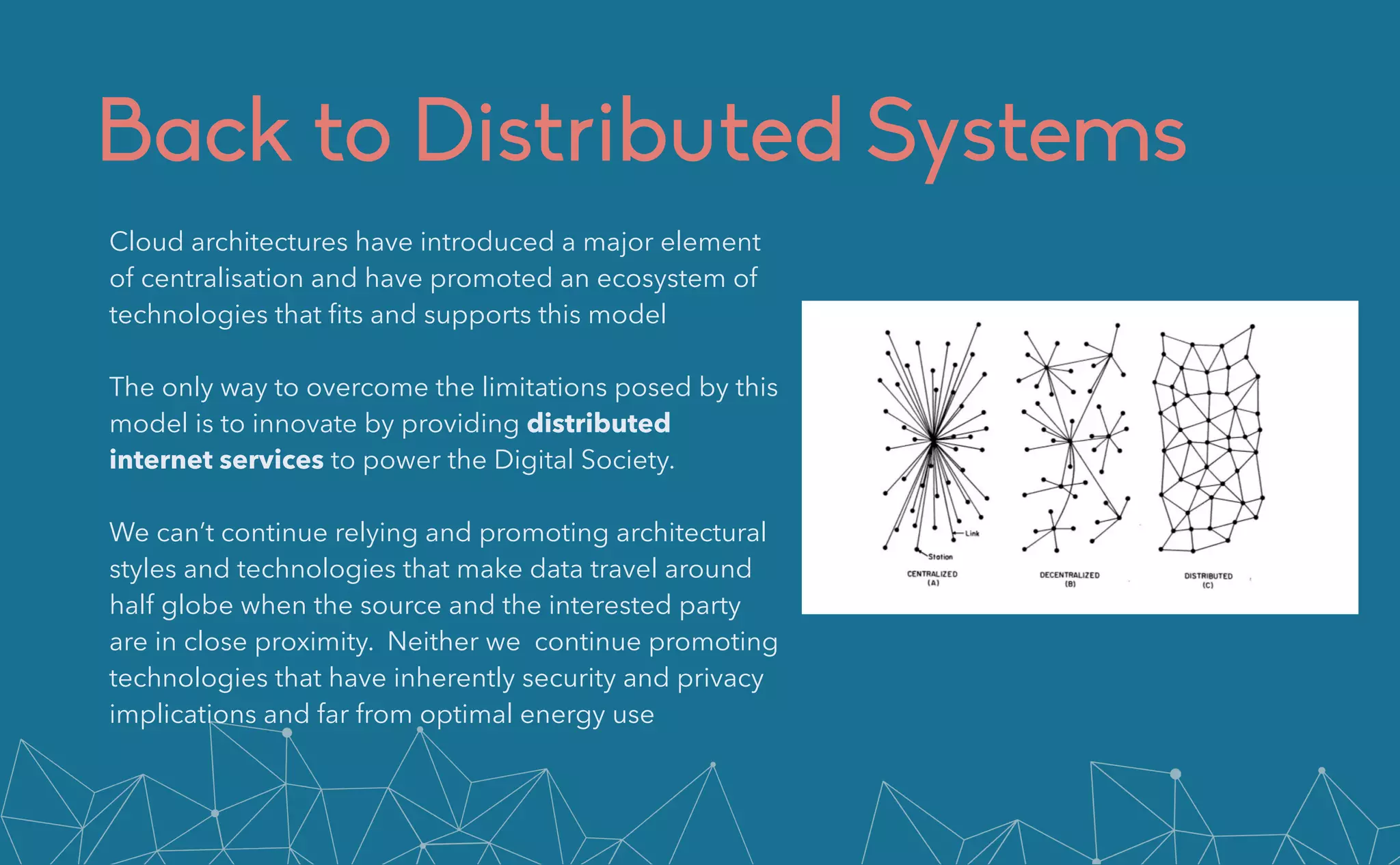
The document discusses the limitations and challenges of cloud computing, including issues related to privacy, data monetization, energy consumption, and the need for edge computing solutions. It emphasizes the importance of innovating distributed internet services, promoting standards, and supporting smaller organizations in adopting edge technology. The text highlights the necessary steps for improving data management and ensuring compliance with regulations to achieve greater digital sovereignty in Europe.

![Cloud Computing Challenges
The privacy abuses revealed by
Snowden have been heavily
covered by the press
What is not so much known, is
that today the vast majority of
servers powering clouds suffer
from MDS and are as a
consequence inherently insecure.
[Security and Privacy]](https://image.slidesharecdn.com/2020-201126144252/75/Data-Decentralisation-Efficiency-Privacy-and-Fair-Monetisation-3-2048.jpg)
![Cloud Computing Challenges
As a consequence of centralisation Cloud vendors
have the lion share on data monetisation
opportunities.
This leads to an extremely biased market in which a
few control too much
If individuals have full ownership and control over
their digital footprint they have higher chance to
monetise it — if desired.
[Monetisation]
Example:
Your browsing history, your electrical consumption, your
running data, etc., is (often) owned, controlled and
monetised by third parties.](https://image.slidesharecdn.com/2020-201126144252/75/Data-Decentralisation-Efficiency-Privacy-and-Fair-Monetisation-4-2048.jpg)
![Cloud Computing Challenges
Cloud computing poses major
energetic challenges not simply
because of data-center but more
importantly for the traf
fi
c it generates.
All data gets in and out of a remote
data center — that consumes energy
[Energy Consumption]](https://image.slidesharecdn.com/2020-201126144252/75/Data-Decentralisation-Efficiency-Privacy-and-Fair-Monetisation-5-2048.jpg)
![The Austerity Dilemma
Whilst there there a growing
community advocating data austerity,
the solution is not simply is being
conscious on our use of precious
resources — such energie — but we
need to realise that the current
architectures, infrastructures and
technologies where not designed for
addressing the data age
The solution relies combining innovation to improve the
ef
fi
ciency of data distribution technologies with the
sensibilisation of European on the value of parsimony
[Energy Consumption]](https://image.slidesharecdn.com/2020-201126144252/75/Data-Decentralisation-Efficiency-Privacy-and-Fair-Monetisation-6-2048.jpg)

![Technology Stack
We have established the
Edge Native Working
Group in Eclipse to incubate
technologies to address the
aforementioned problems
Two key projects in this
context are zenoh which
implements a data plane for
the edge and fogOS which
de
fi
nes the control and
management plane
[Open Infrastructure]](https://image.slidesharecdn.com/2020-201126144252/75/Data-Decentralisation-Efficiency-Privacy-and-Fair-Monetisation-9-2048.jpg)

