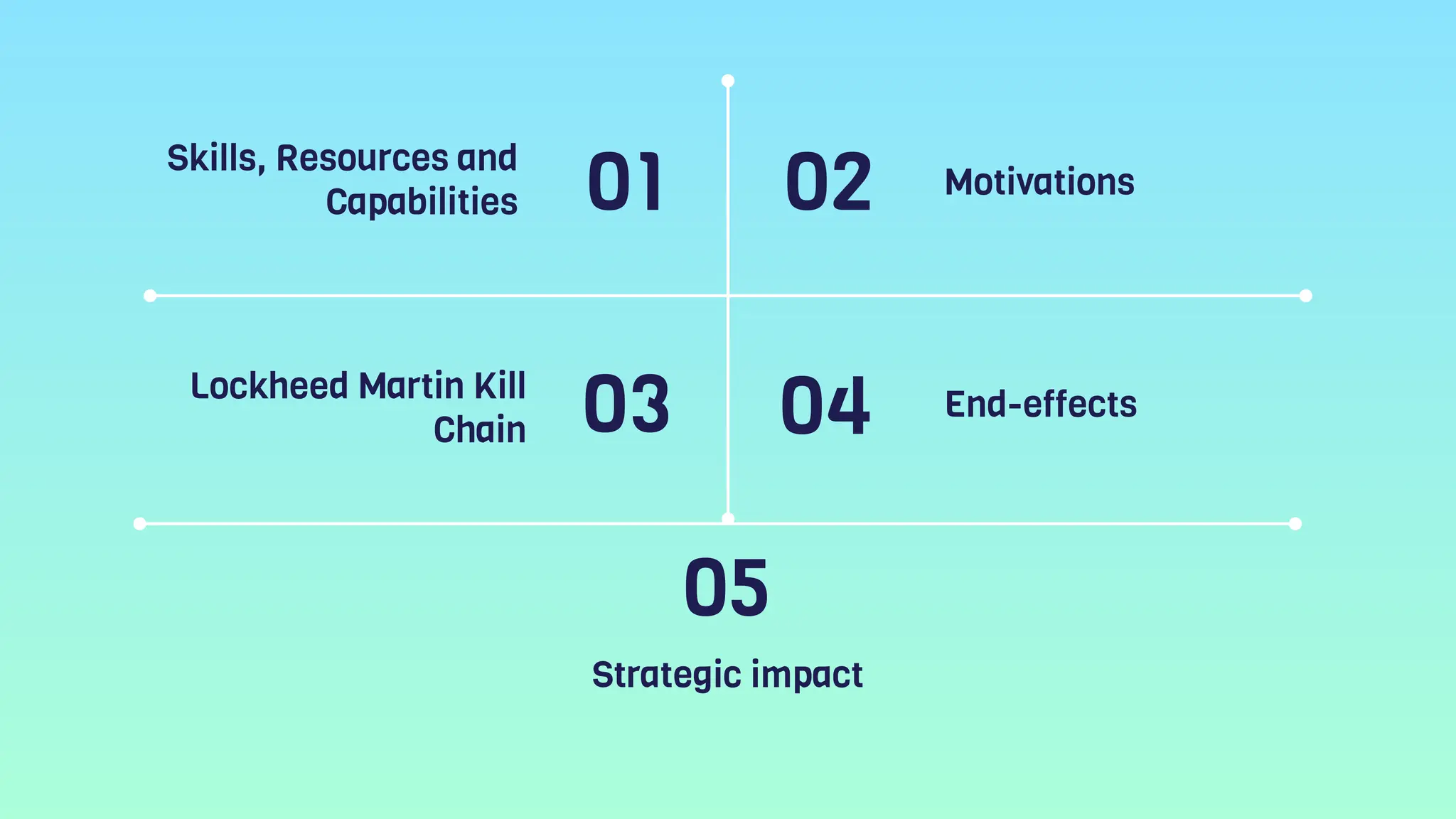
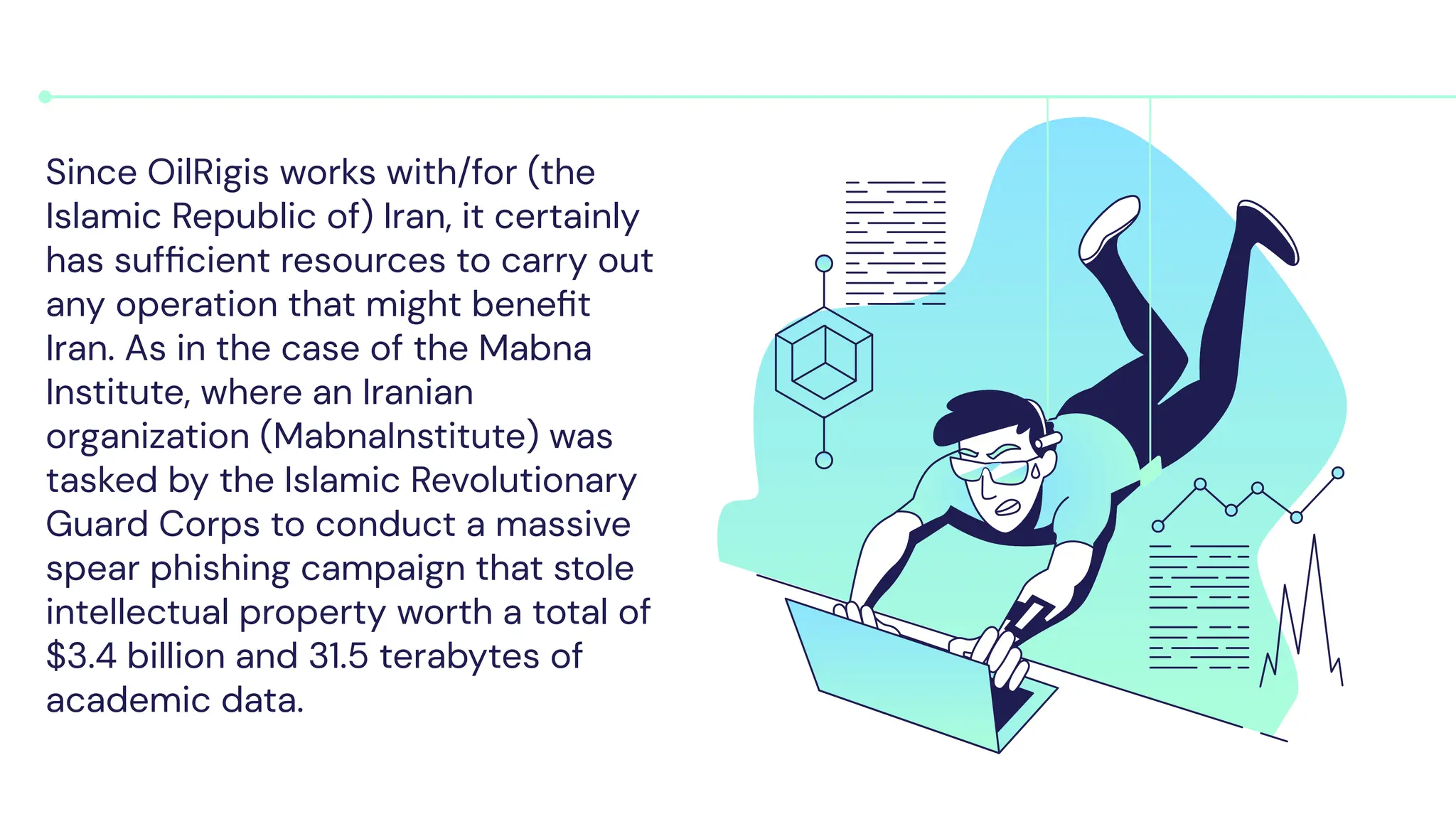
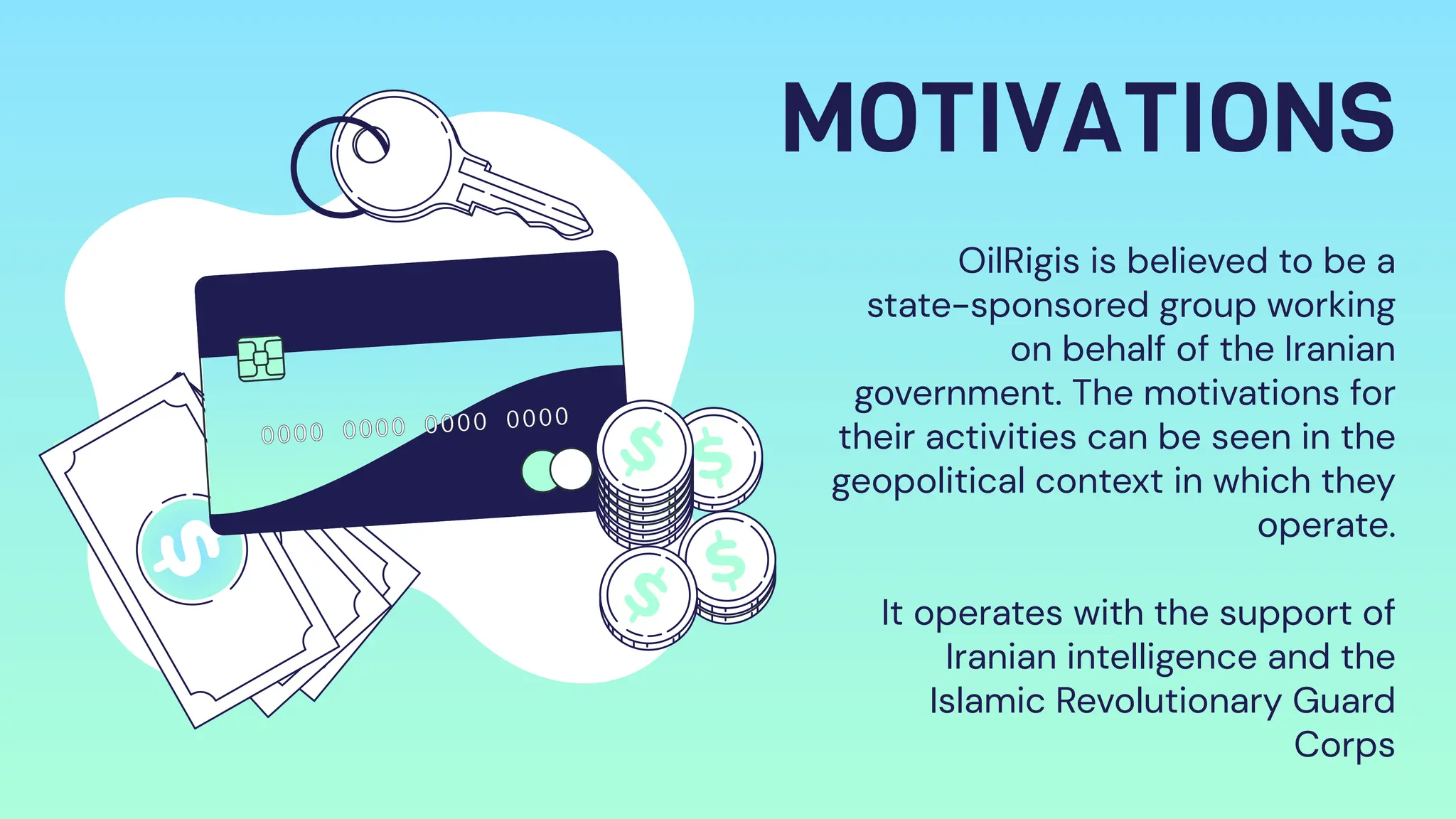
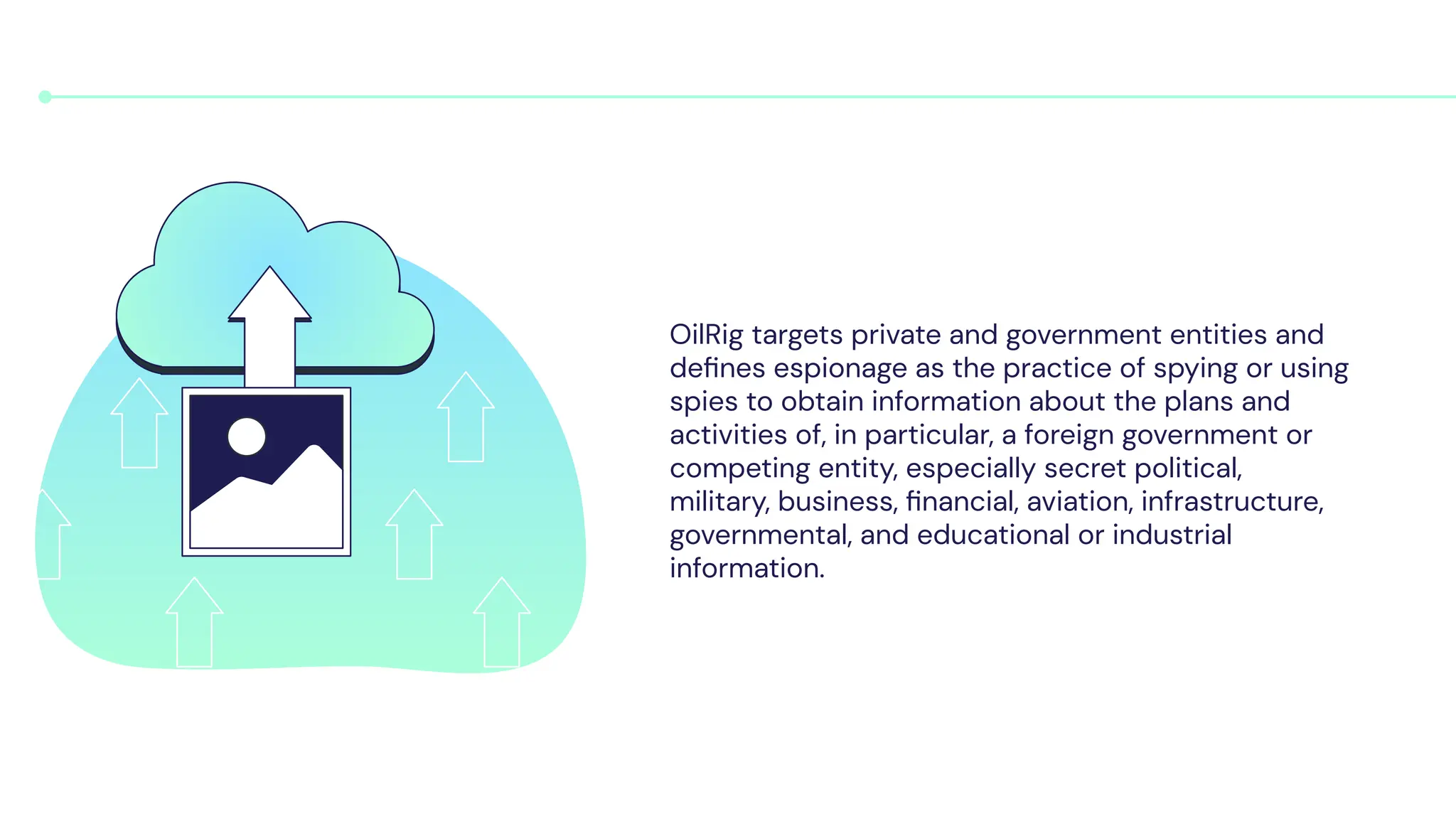
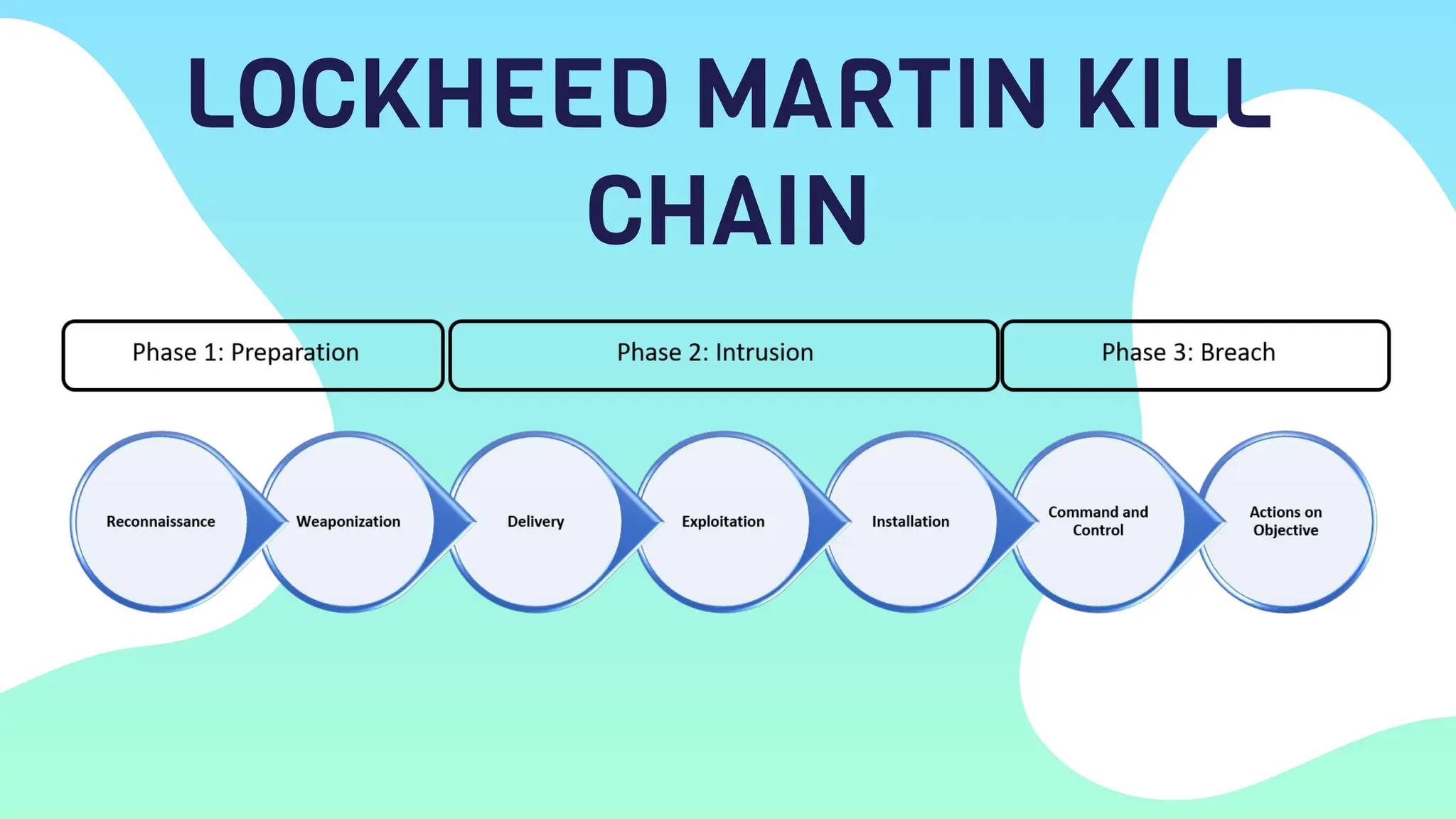
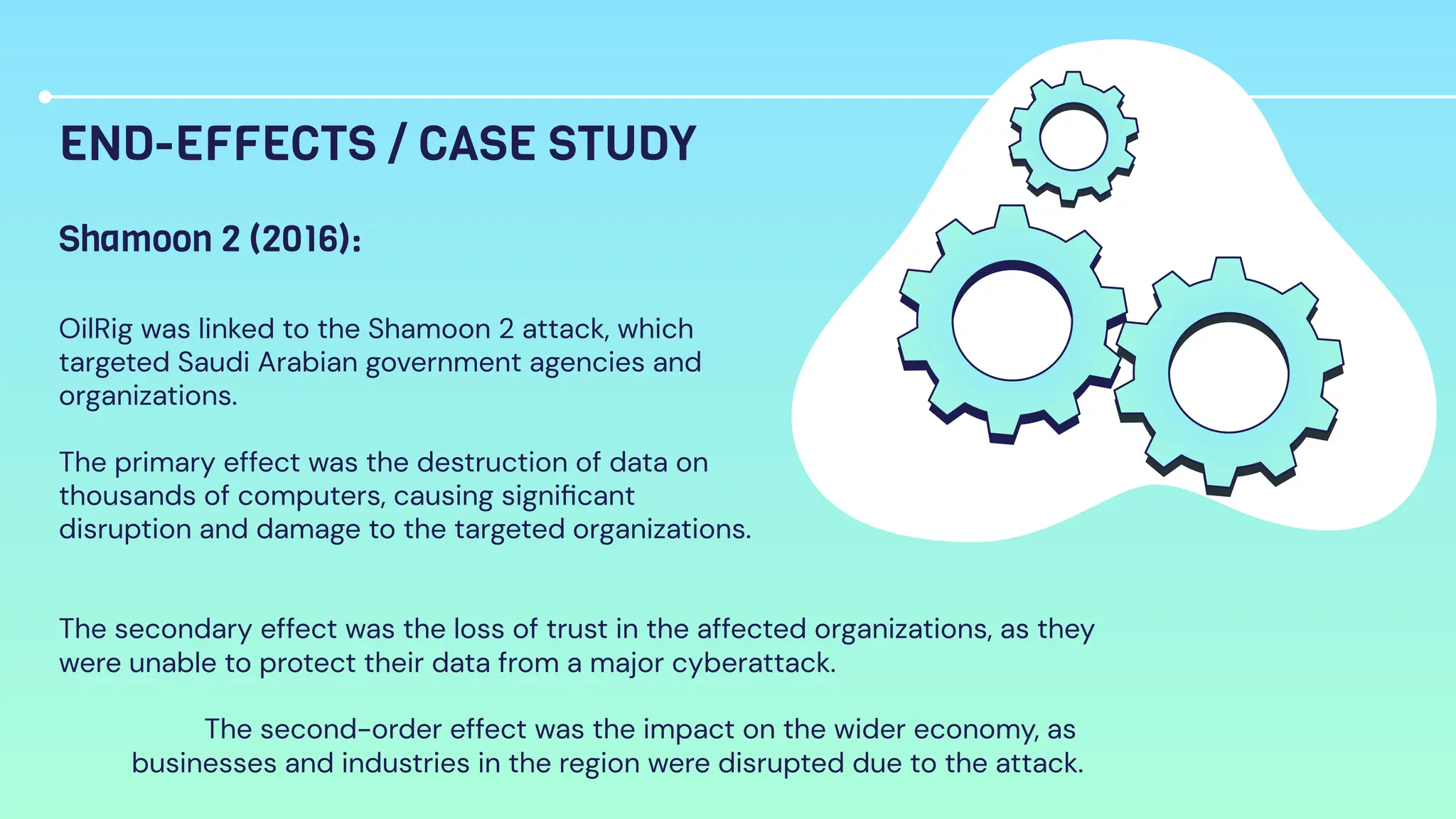
OilRig is an Iranian state-sponsored hacking group with significant cyber capabilities. It has been targeting organizations in the Middle East, Europe, and United States since 2014 through advanced persistent threats and social engineering. OilRig's motivations stem from Iran's geopolitical tensions with its regional neighbors and Western countries. It follows the Lockheed Martin kill chain to conduct espionage and gather intelligence to support Iran's infrastructure and technology development. OilRig poses a strategic threat as its attacks can disrupt critical infrastructure and damage economies through data destruction, as seen in the Shamoon 2 attack against Saudi organizations.