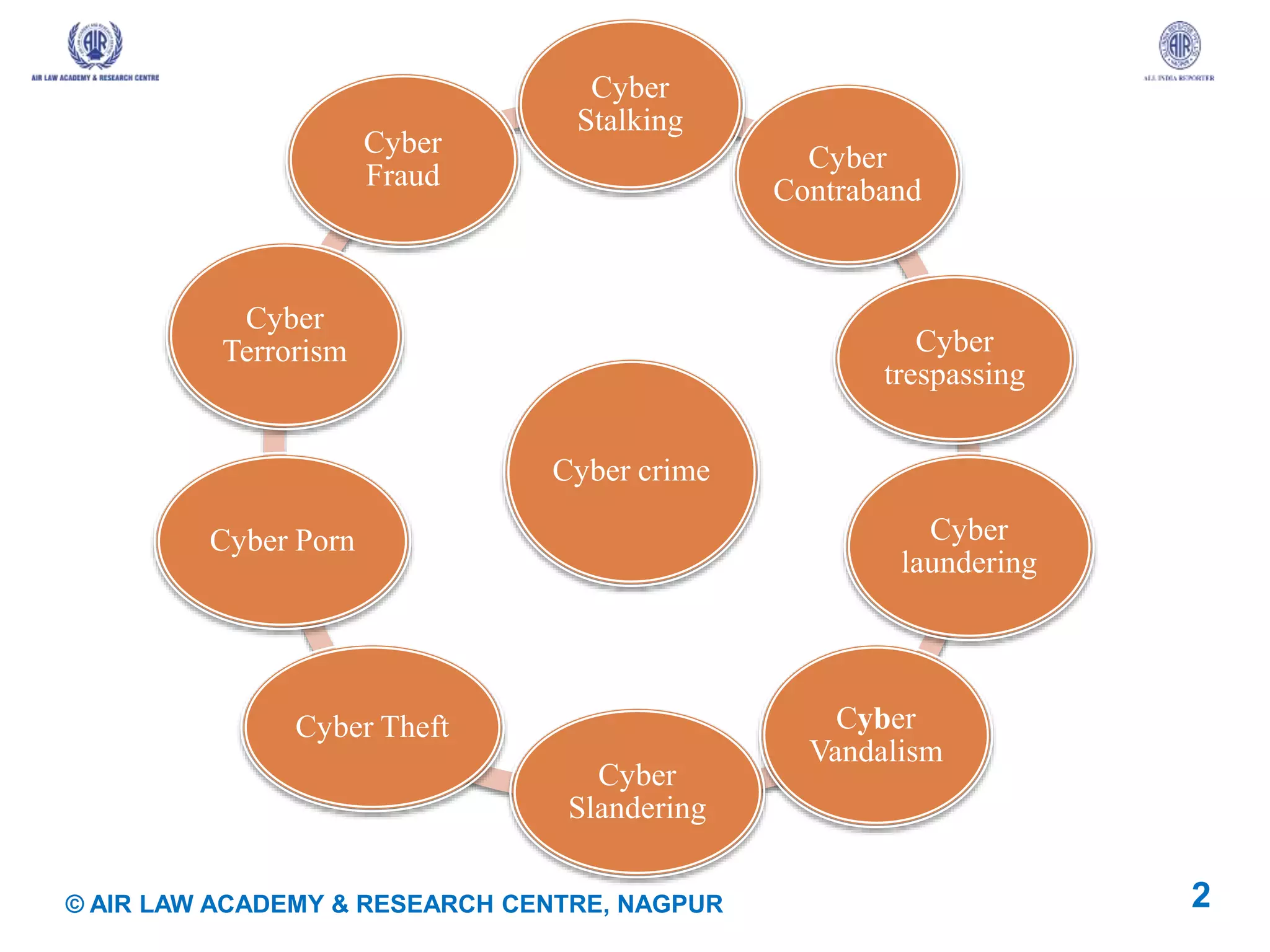
This document discusses various types of cyber crimes. It defines cyber crime as any criminal activity where a computer or technology is used as a tool or target of the crime. The document then lists and provides brief descriptions and examples of 10 common types of cyber crimes: cyber fraud, cyber trespassing, cyber laundering, cyber terrorism, cyber vandalism, cyber theft, cyber pornography, cyber stalking, cyber slandering, and cyber contraband. It concludes by providing some tips to help protect yourself from becoming a victim of cyber crimes, such as using antivirus software, firewalls, maintaining security settings and backups, and staying anonymous online.