Embed presentation
Downloaded 19 times



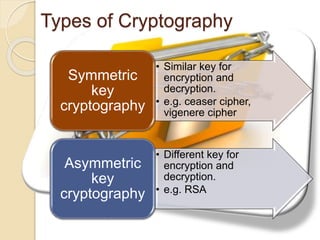



Cryptography is the practice and study of hiding information. It involves encrypting plain text into unintelligible cipher text using an algorithm or key, and decrypting cipher text back into plain text. There are two main types of cryptography: symmetric key cryptography which uses the same key to encrypt and decrypt, and asymmetric key cryptography which uses different keys. Cryptography improves security, keeps communications private, and ensures privacy by encoding messages in a way that can only be read by those possessing the decryption key.






