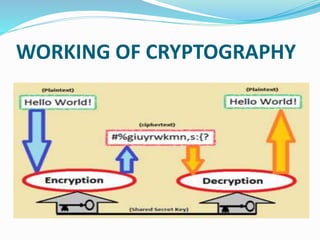
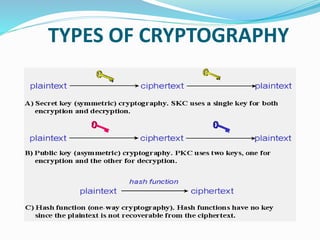
Cryptography is the practice of securing communications and data through encryption techniques. It aims to achieve authentication, privacy, integrity, and non-repudiation. The development of computers allowed for more complex encryption of digital data. There are different types of cryptography including secret key cryptography which uses a single key, and public key cryptography which uses different keys for encryption and decryption. Cryptography provides a secure way to transmit data and is necessary for communications over untrusted networks like the Internet.