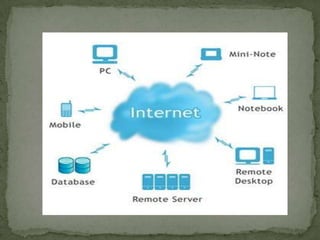
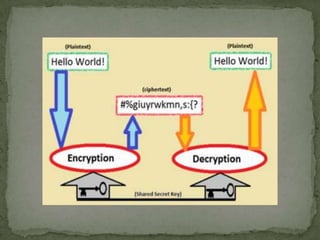
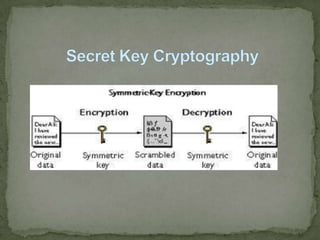
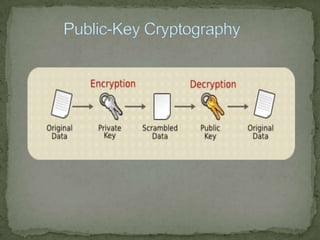
Cryptography is used to protect information by encrypting messages into an unreadable cipher text format. Modern cryptography uses either secret key cryptography, which uses a single key for encryption and decryption, or public key cryptography, which uses two mathematically related keys with one key to encrypt and the other to decrypt. The purpose of cryptography and security is to defend against hackers, industrial espionage, and to secure e-commerce, bank accounts, intellectual property, and avoid liability.