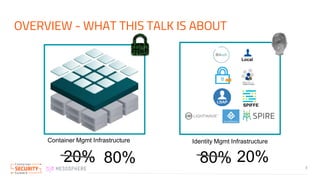
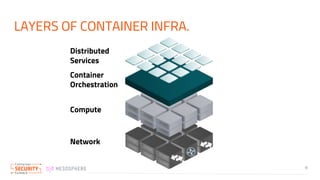
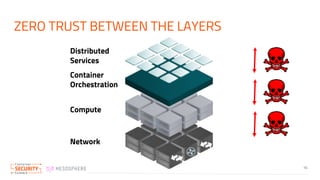
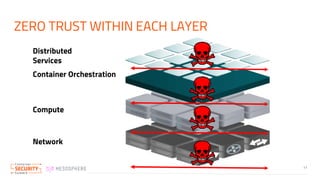
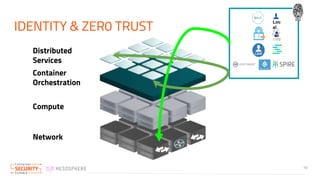
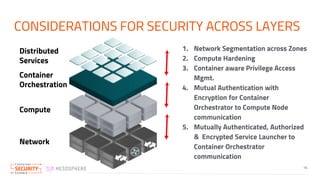
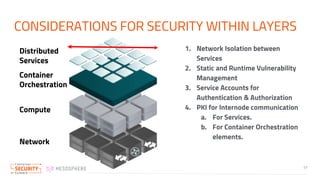
The document discusses the implementation of zero trust security in container infrastructure, emphasizing its importance for secure access and identity management. It outlines various layers of container infrastructure and the need for pluggable local identity systems to support zero trust principles. Key considerations include network segmentation, compute hardening, and mutual authentication to enhance security across and within these layers.