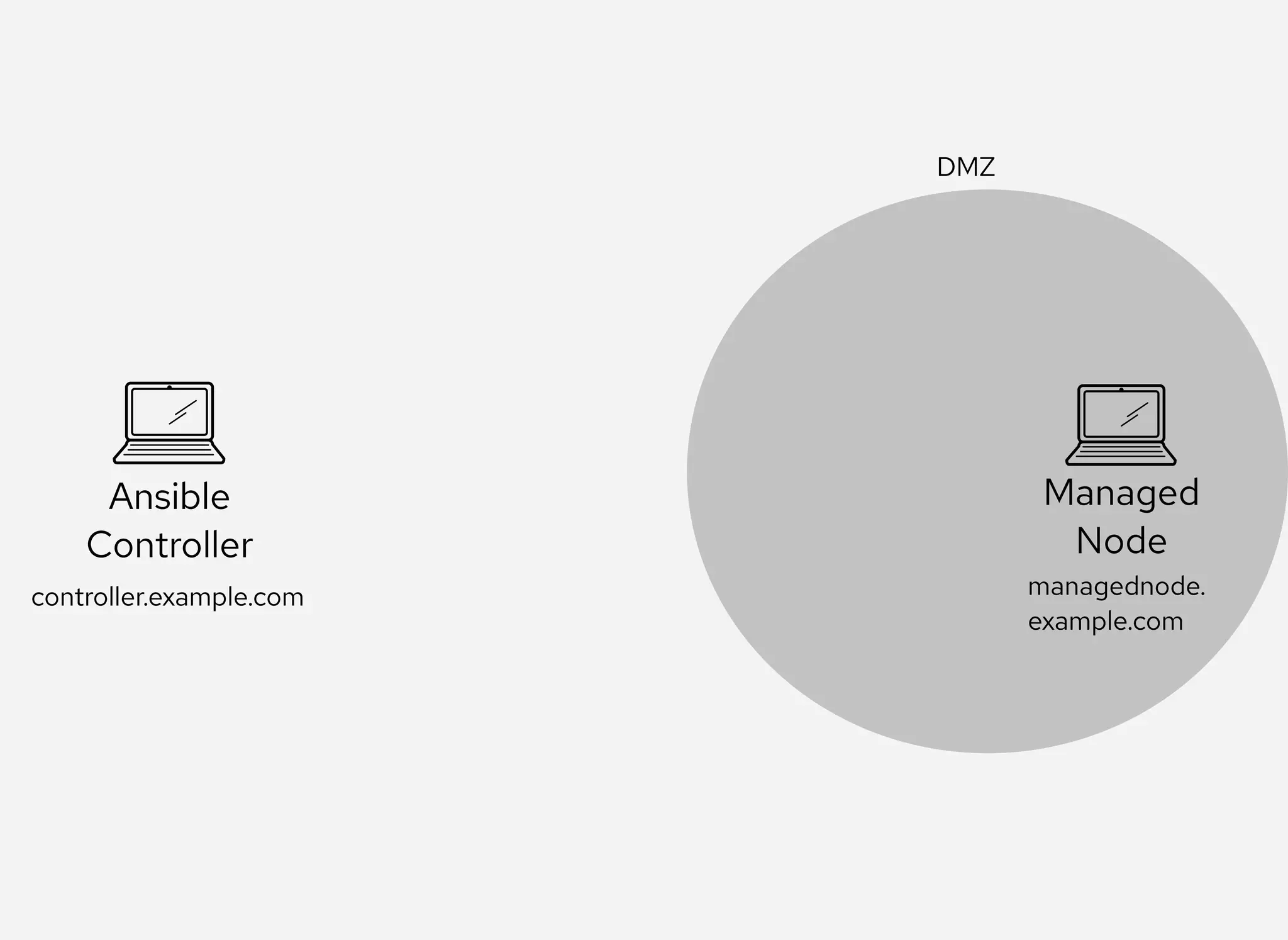
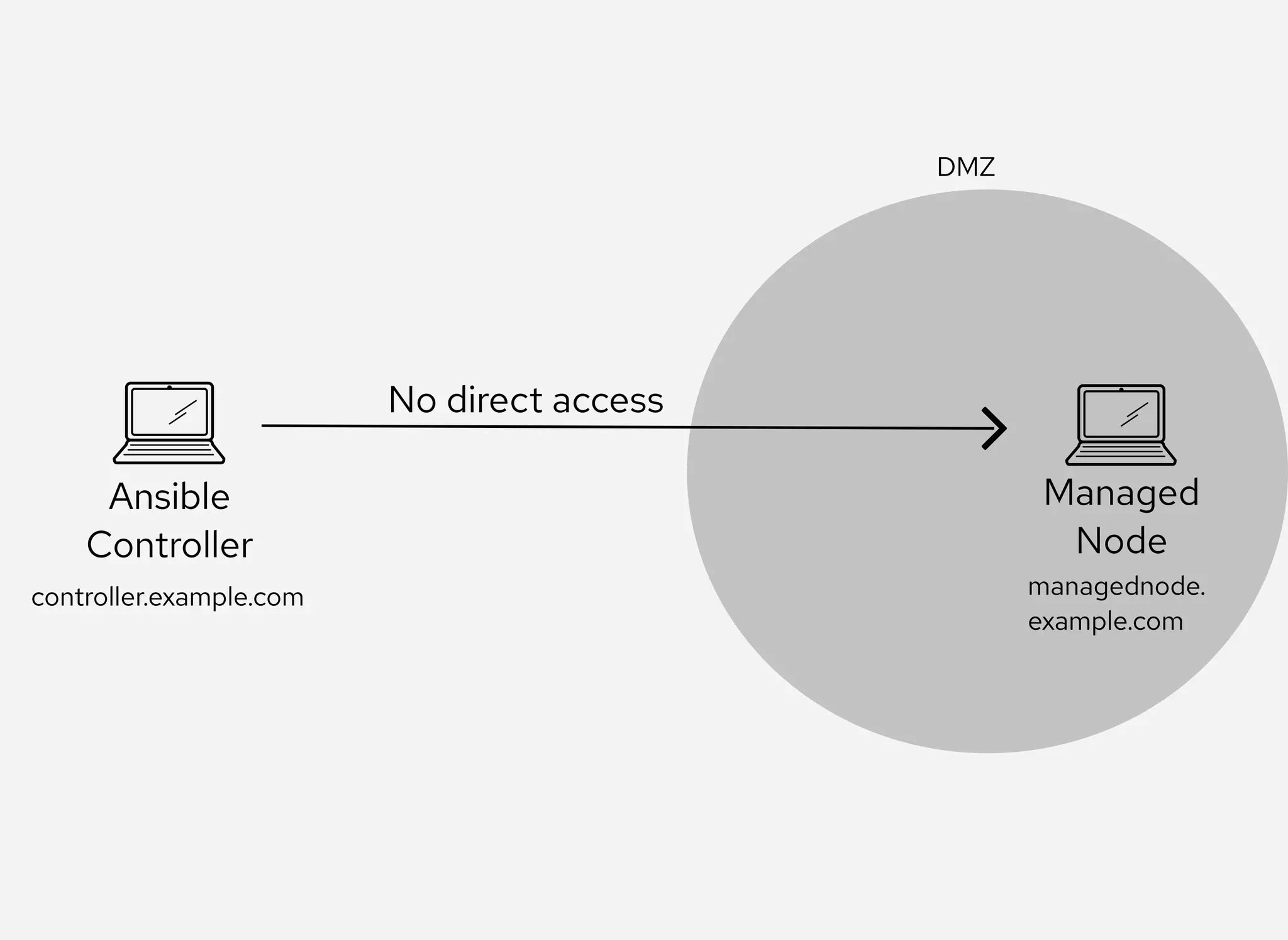
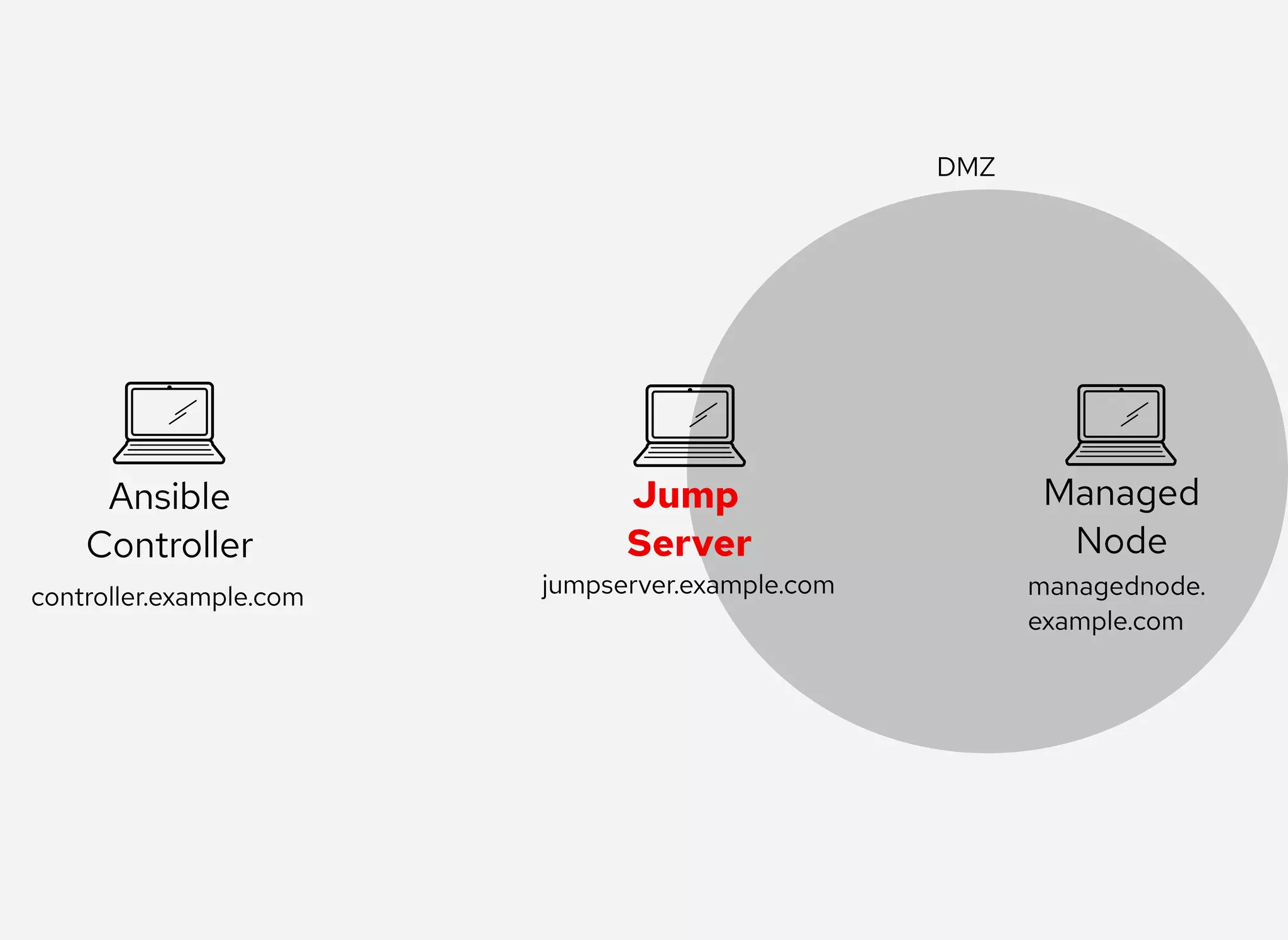
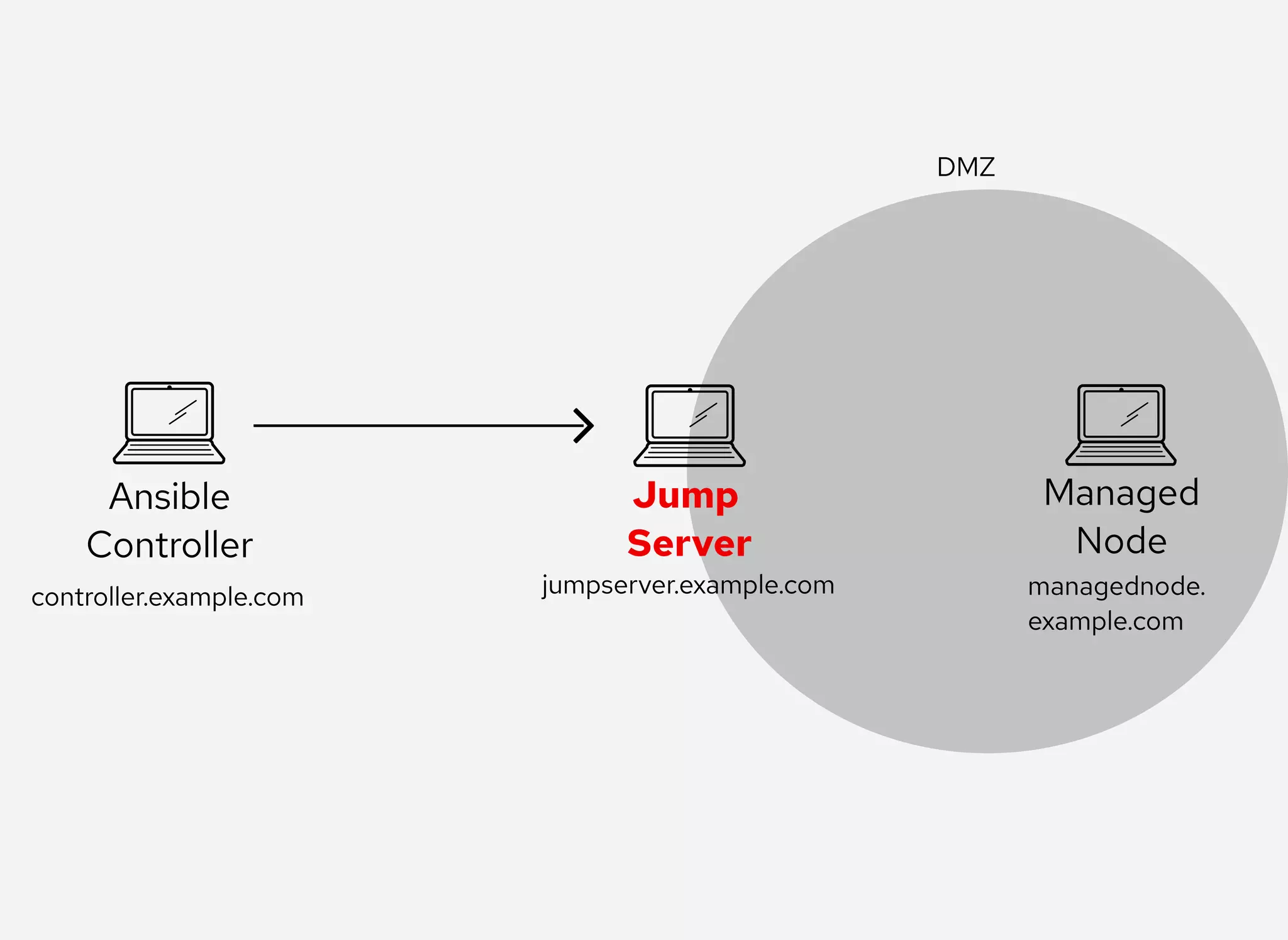
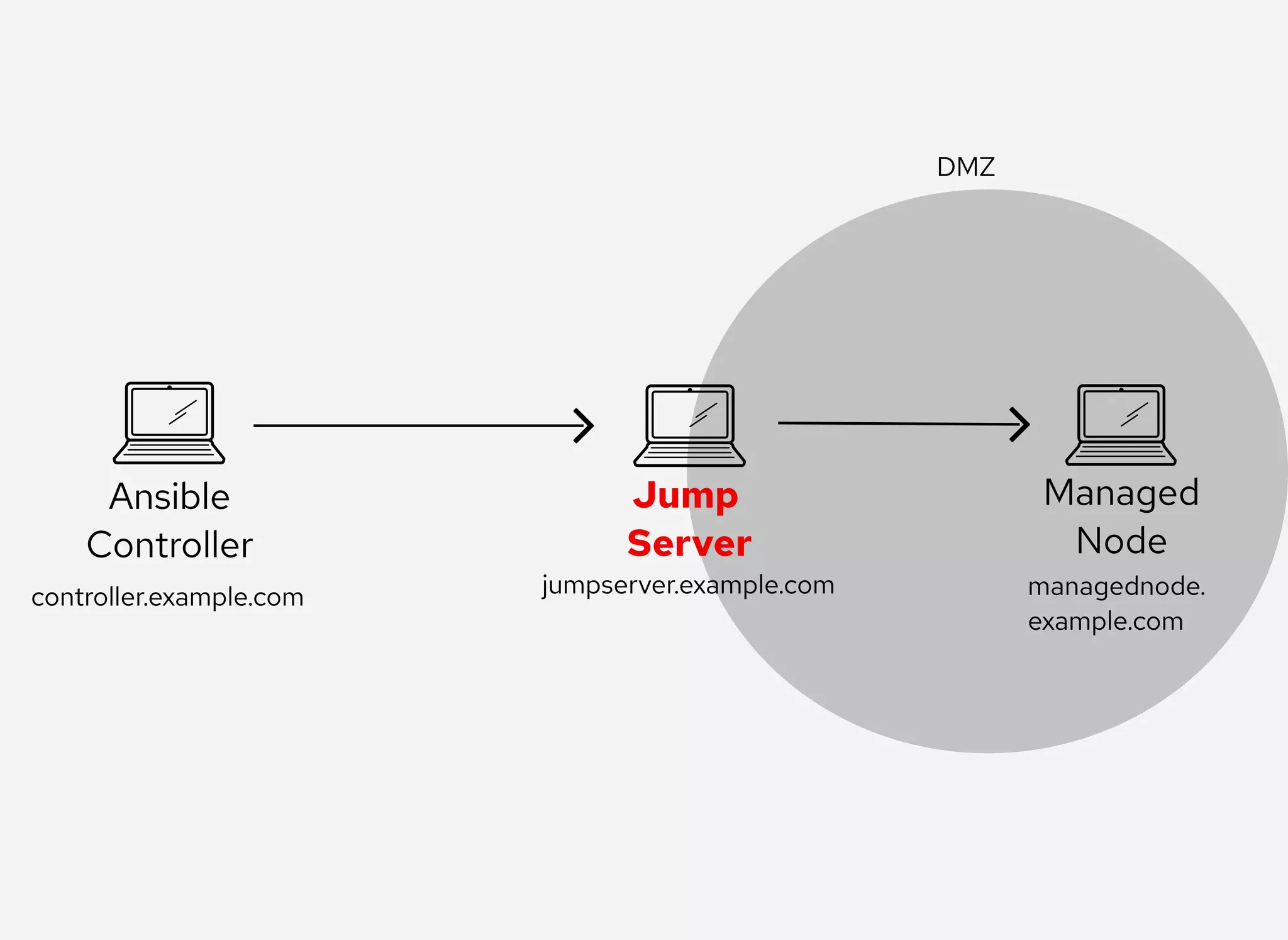
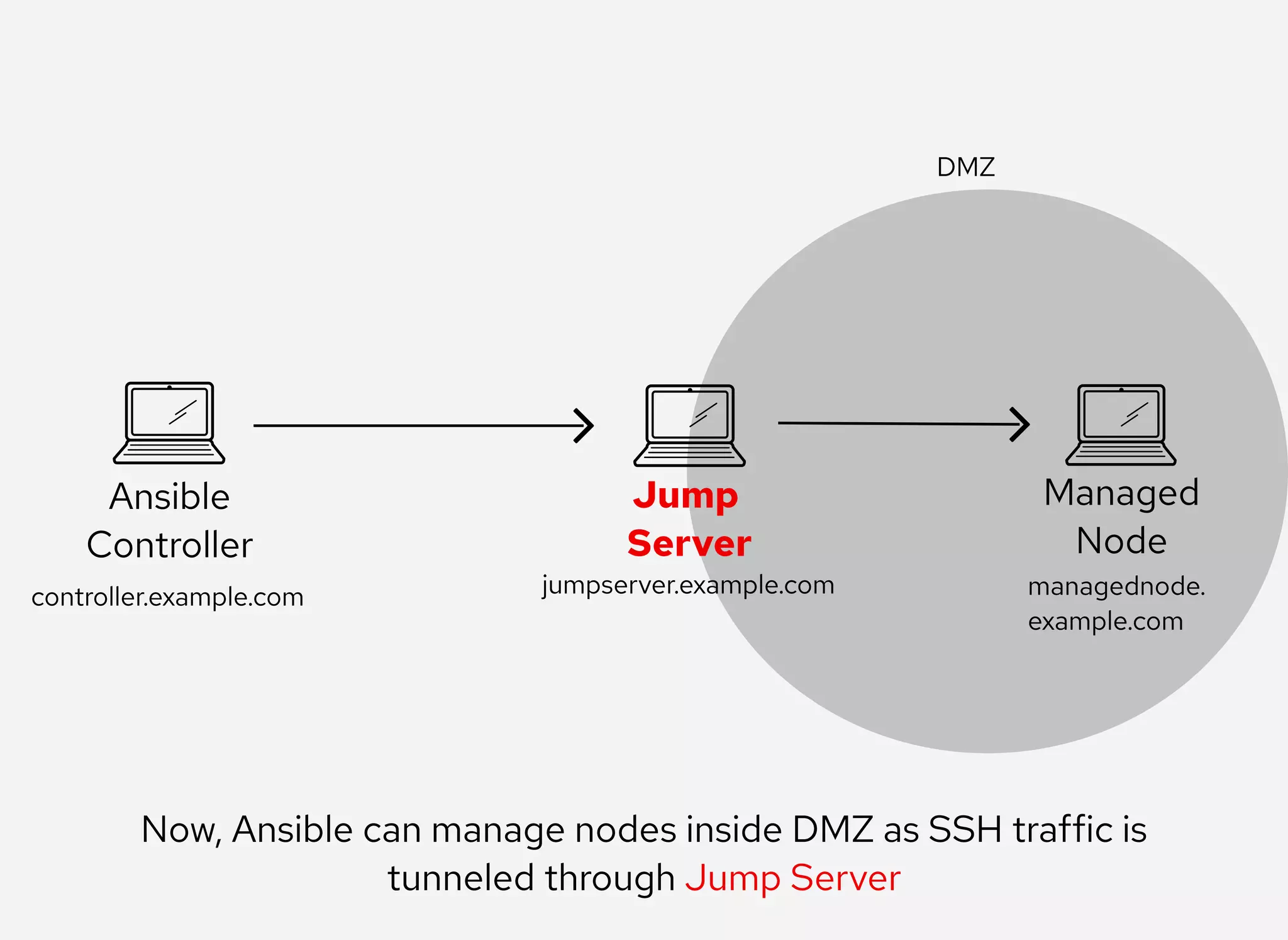
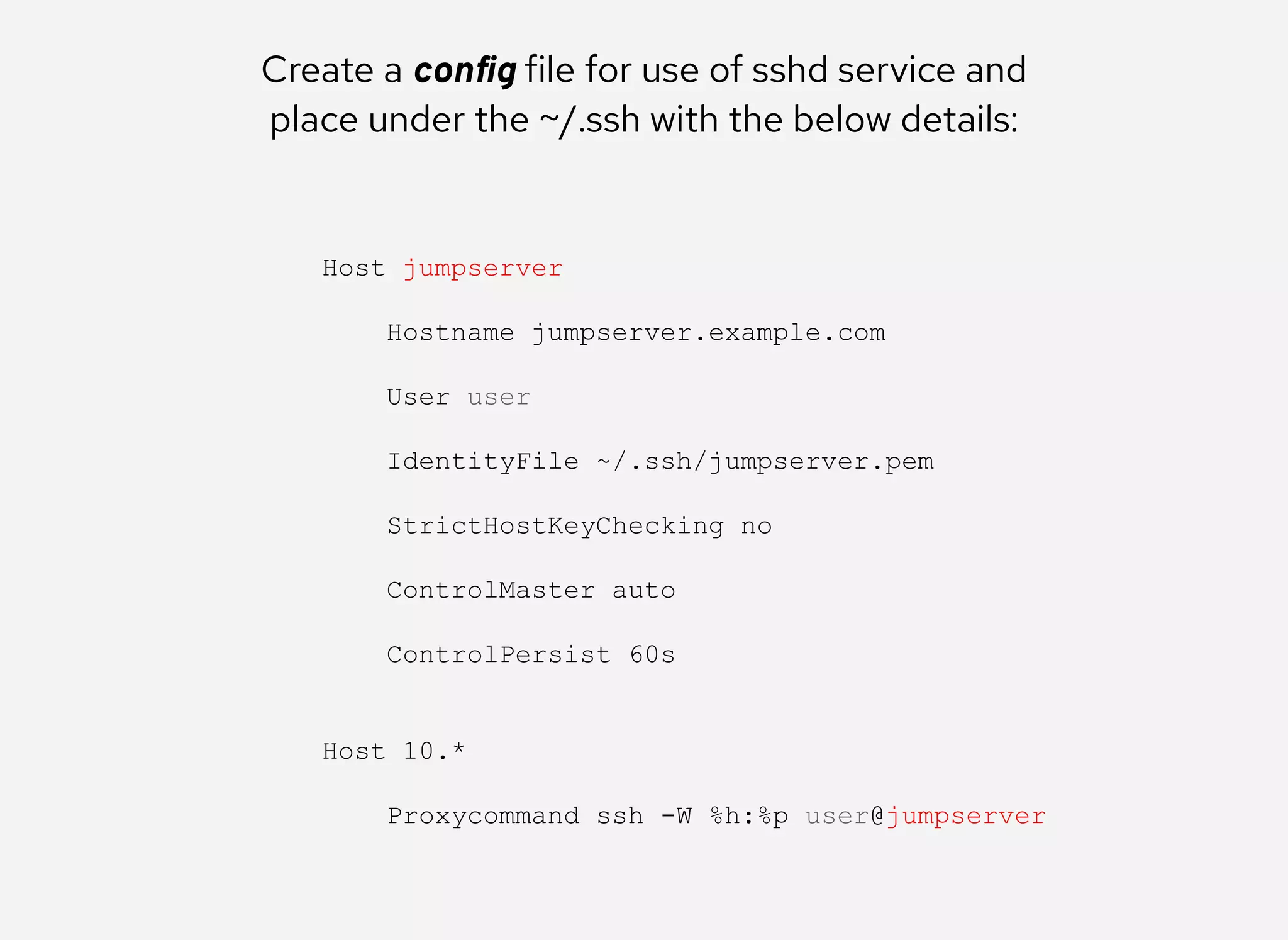
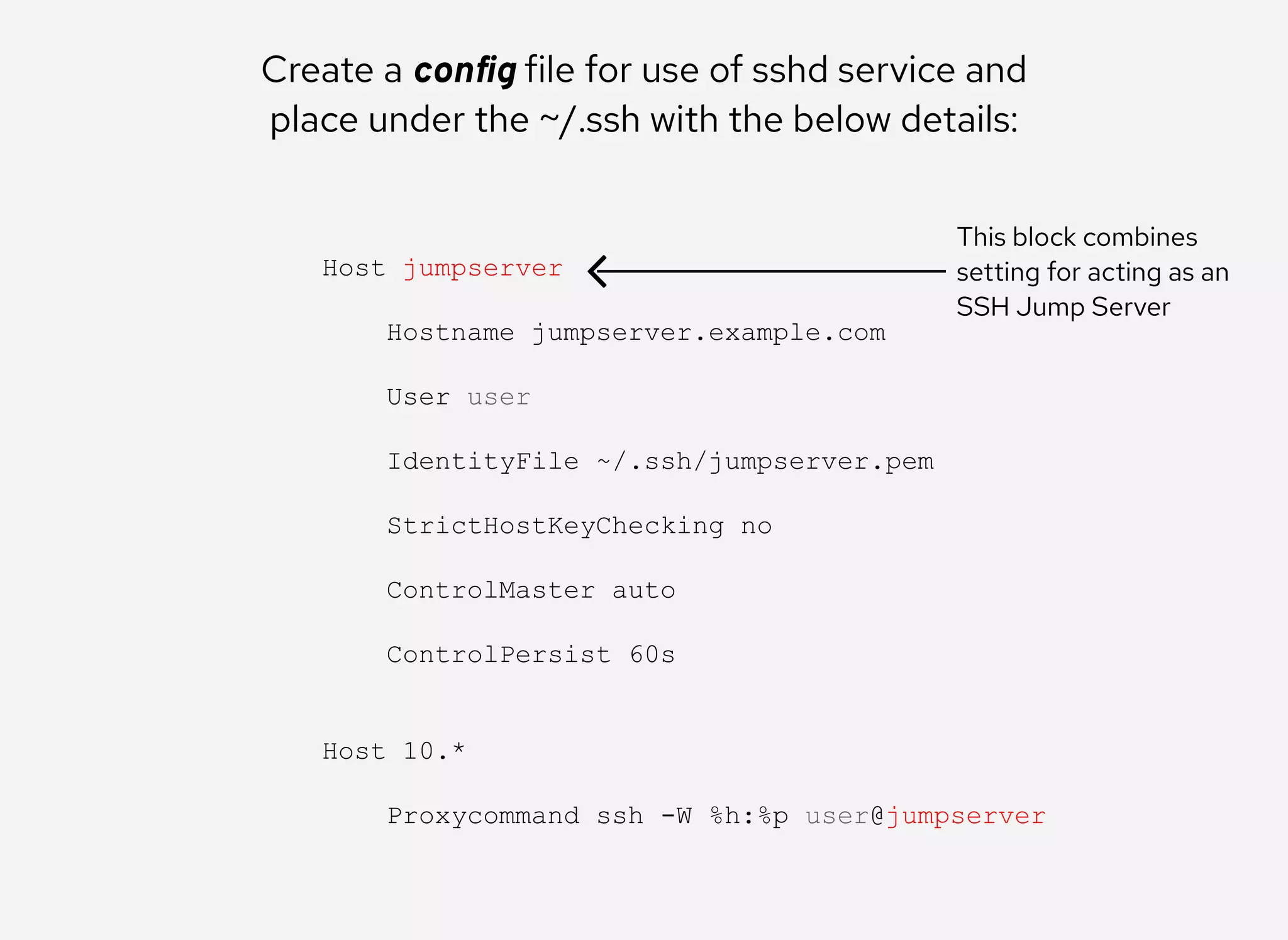
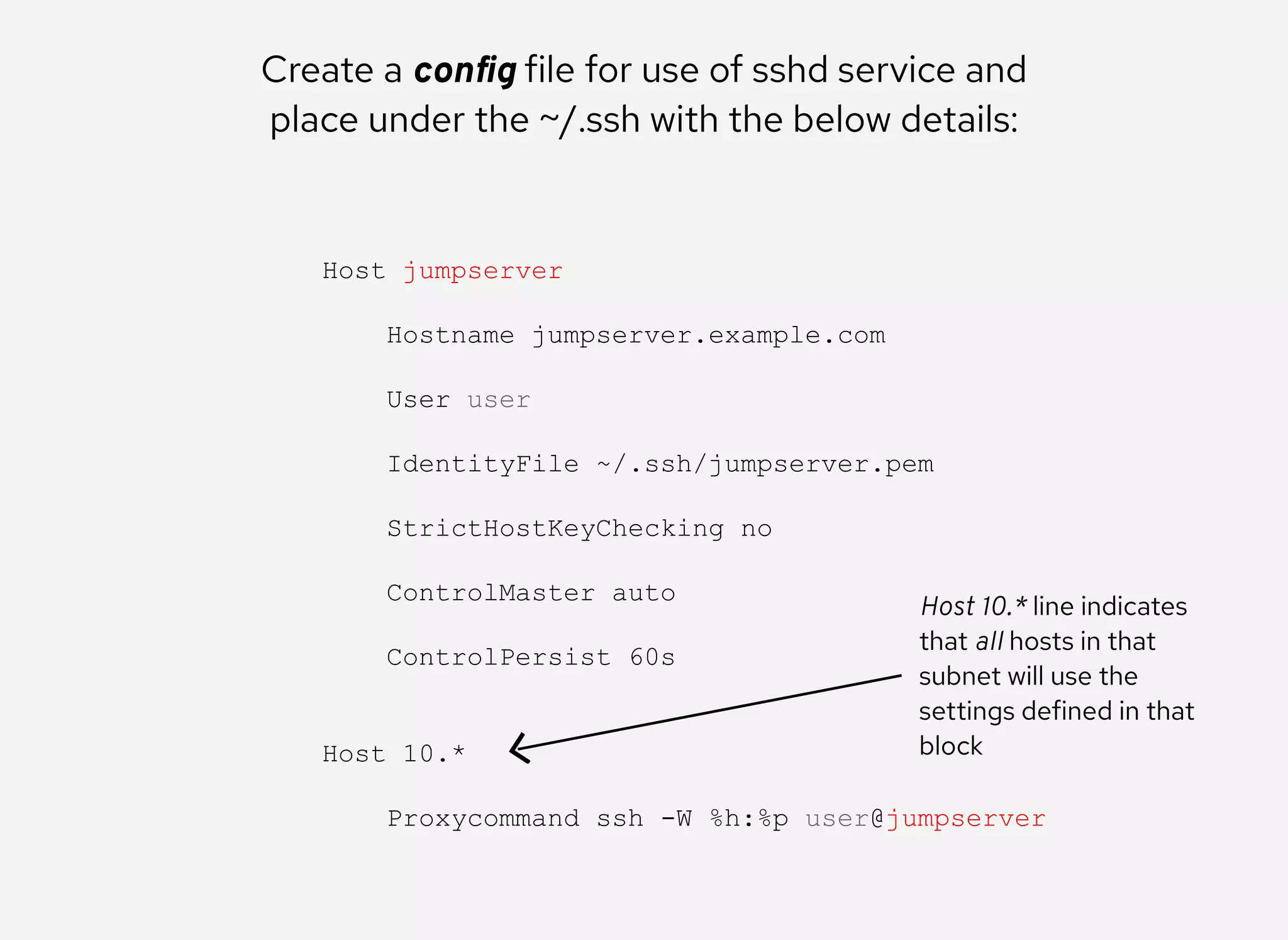
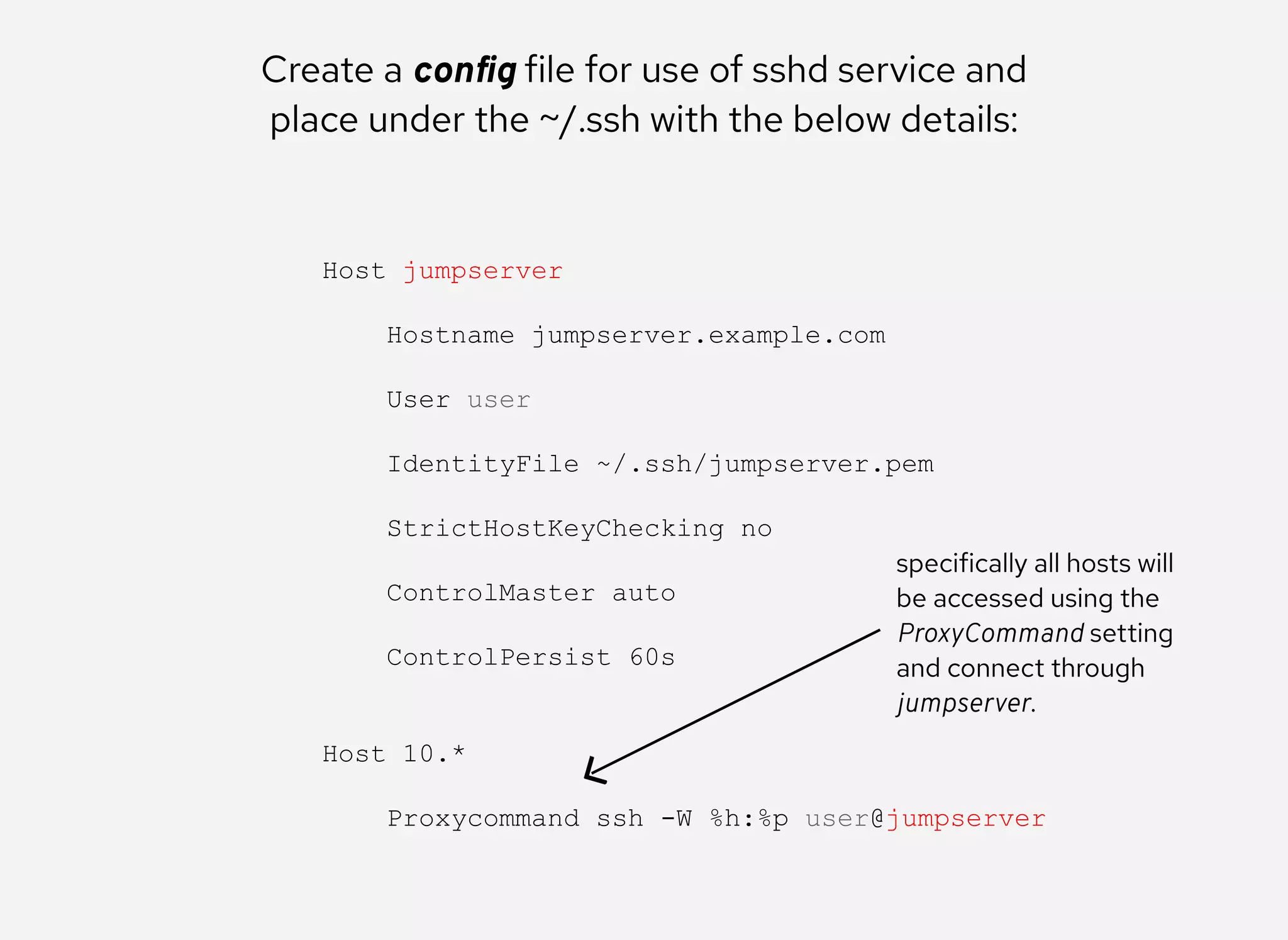
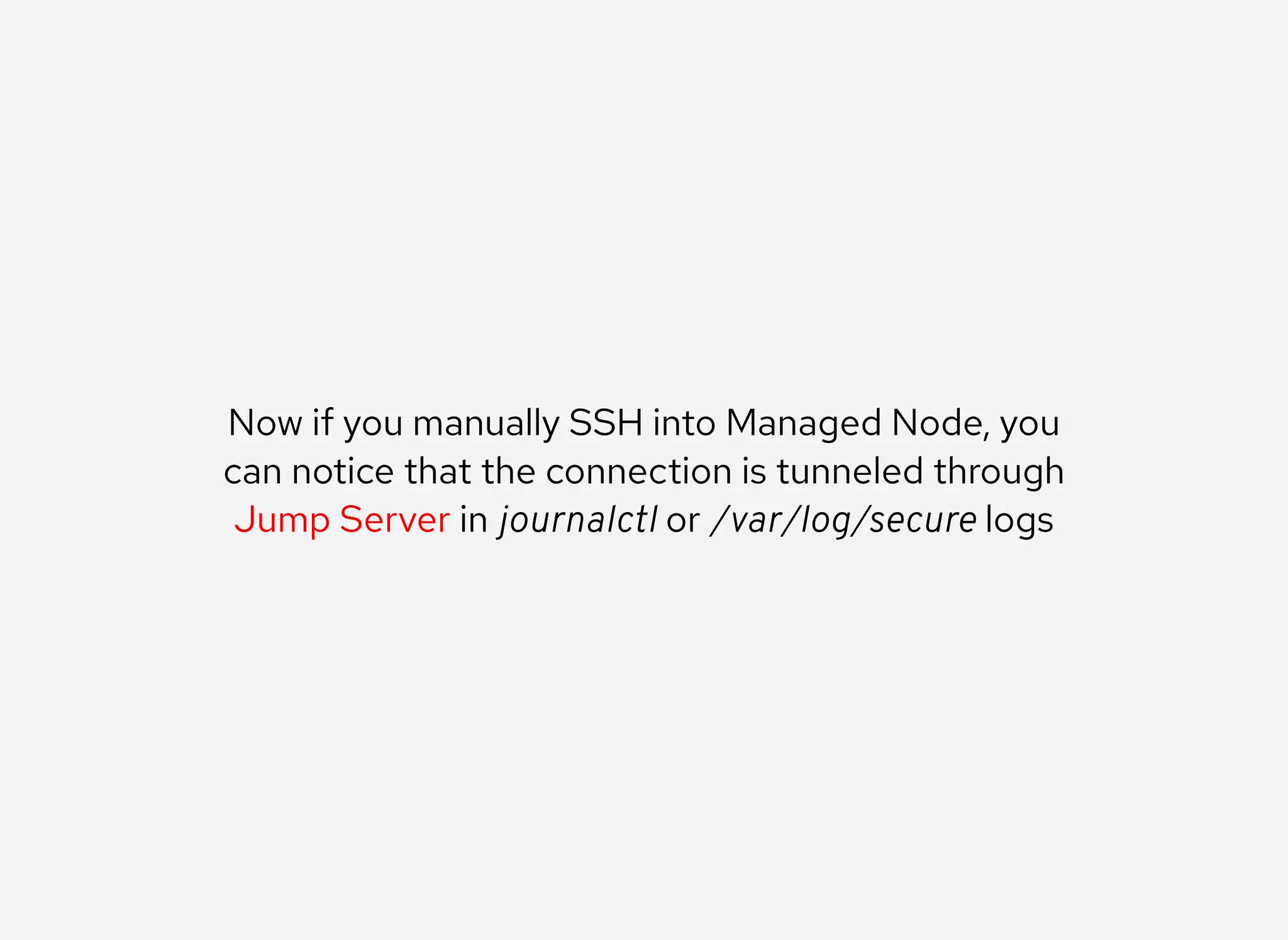
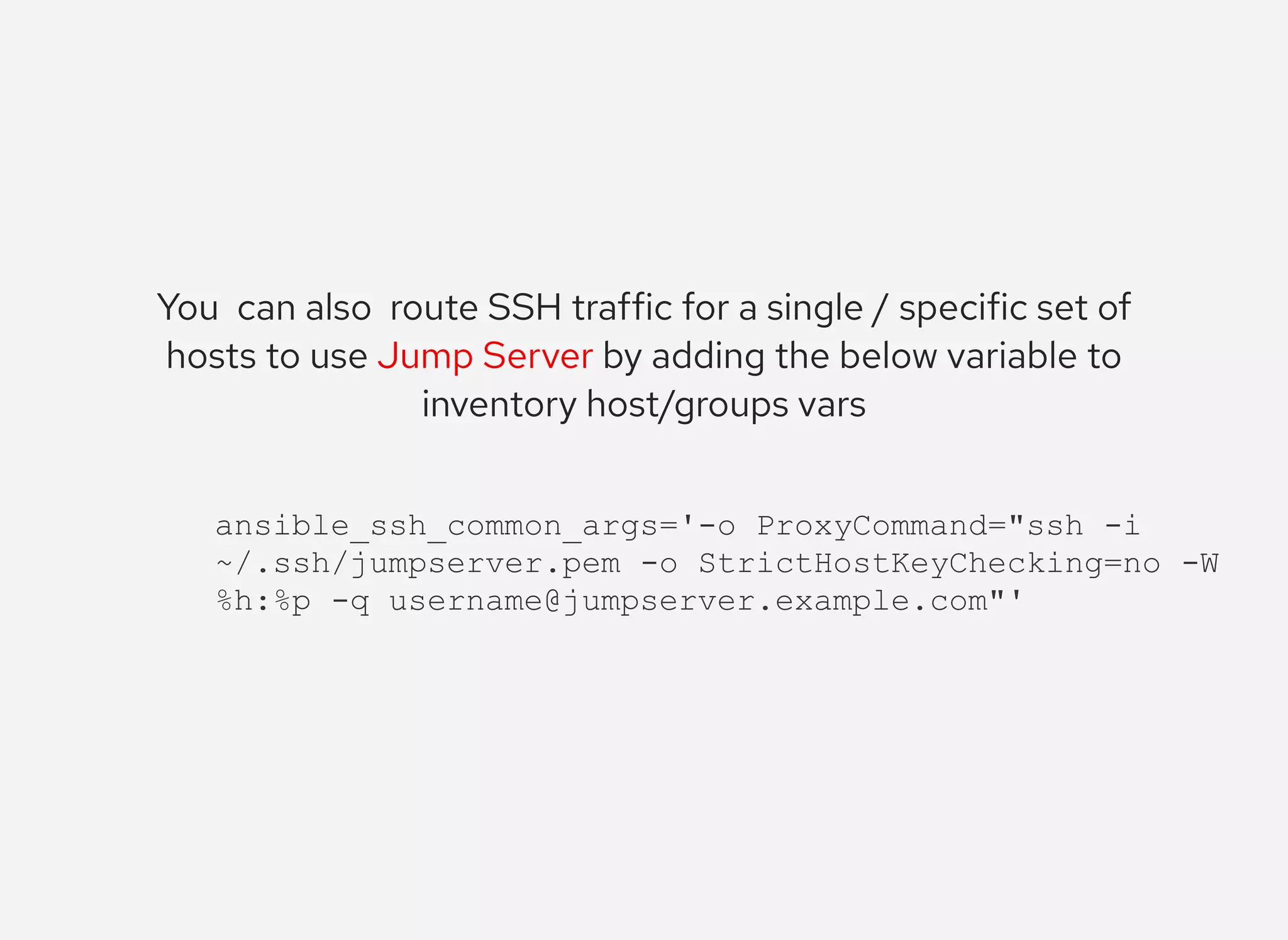
The document details the configuration of Ansible to use a jump server for managing nodes within a DMZ, allowing SSH traffic to be tunneled through the jump server. It provides step-by-step instructions for creating SSH config files and demonstrates how to execute Ansible commands on managed nodes via this setup. Additionally, the document includes information on verifying connectivity and routing SSH traffic for specific hosts through the jump server.