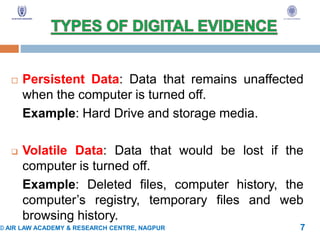
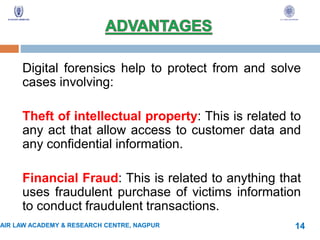
Computer forensic is the process of identifying, preserving, analyzing, and presenting digital evidence in a legally acceptable manner. This involves acquiring evidence from computers and other devices, analyzing the evidence, and reporting the findings. Computer forensic is used to find digital evidence related to cyber crimes, unauthorized disclosure of information, and other offenses. It provides evidence for criminal and civil legal cases by examining both persistent and volatile data stored on devices. Proper procedures and validated tools are used to ensure any evidence collected is admissible in court.