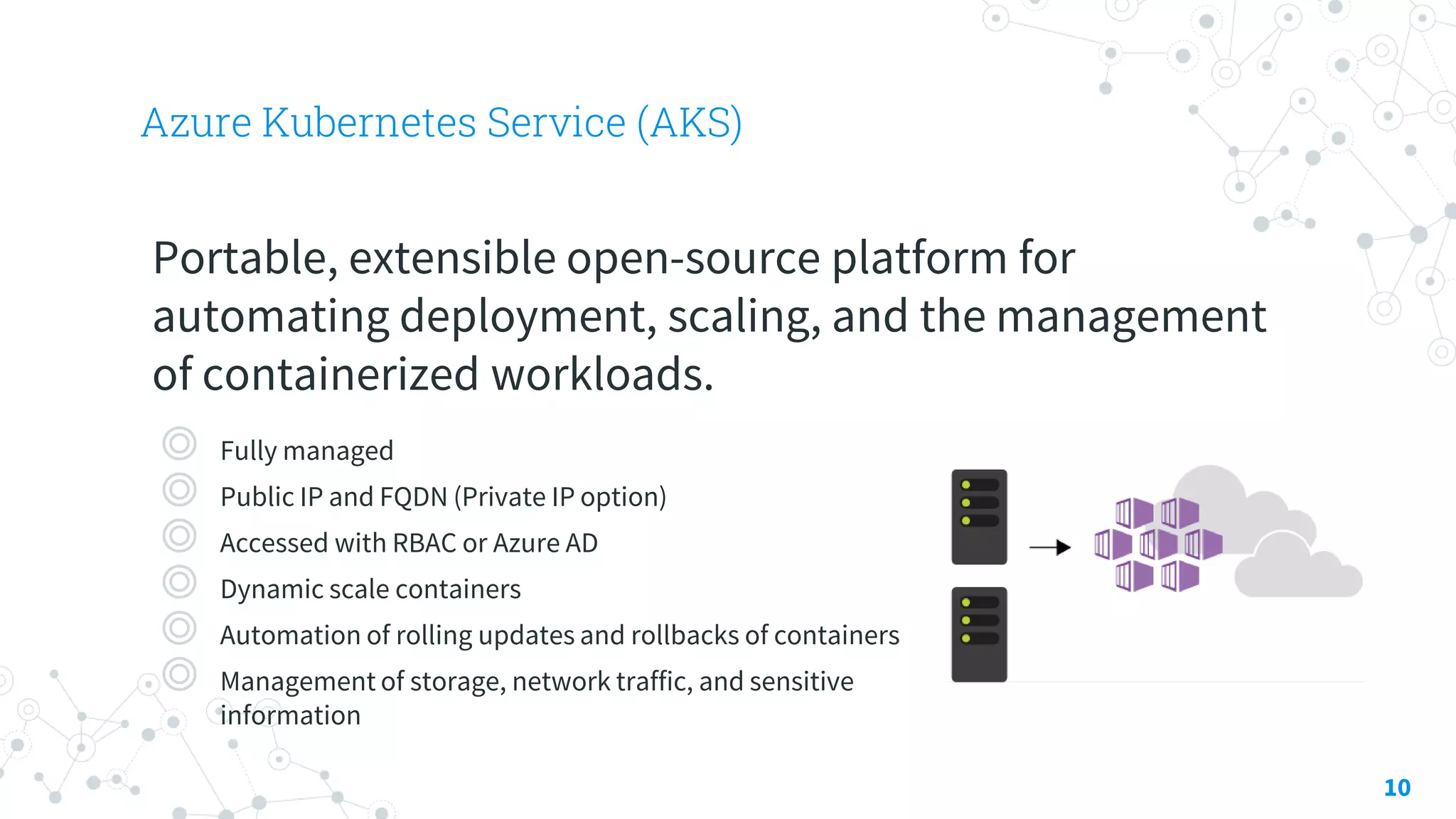
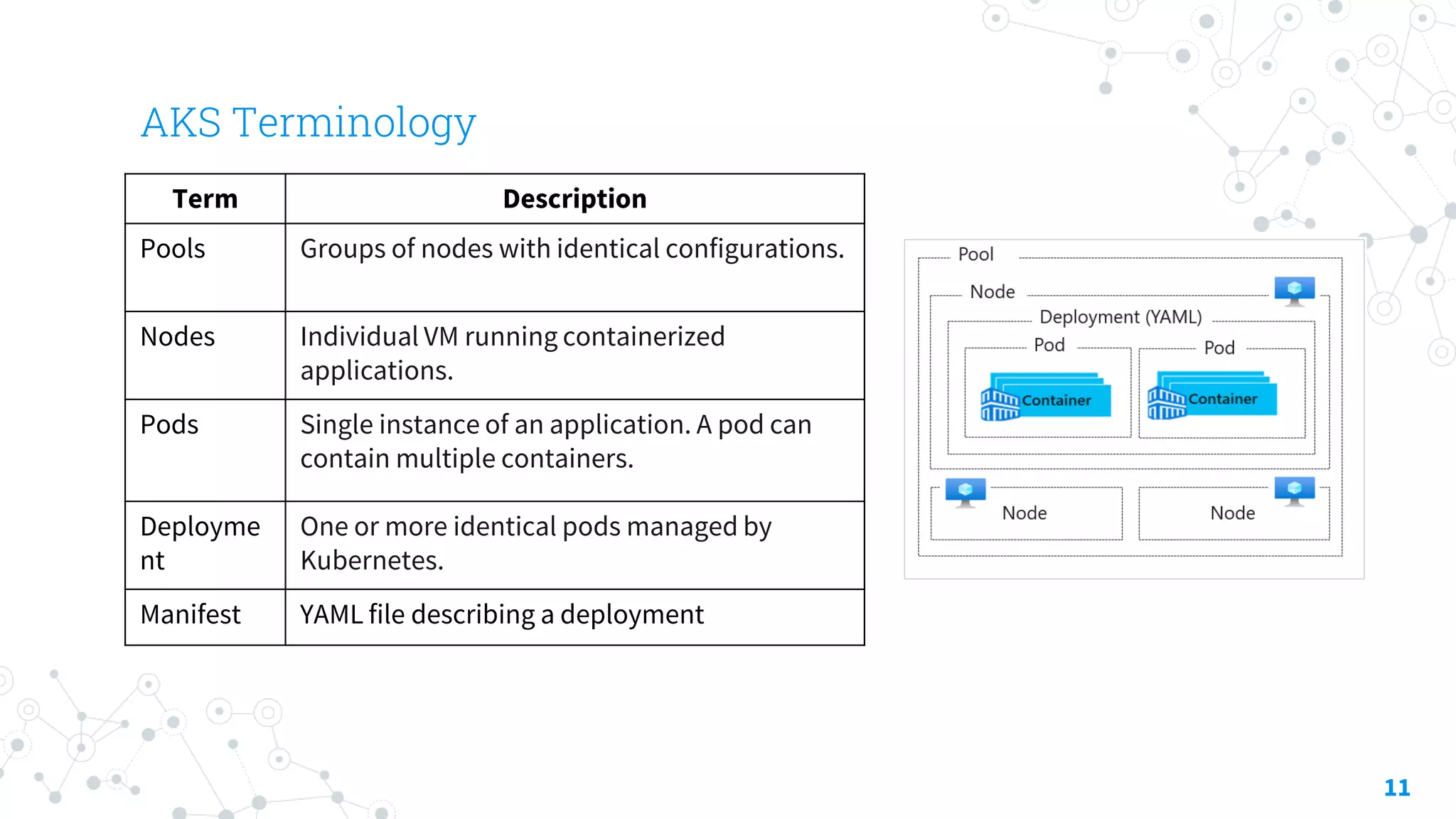
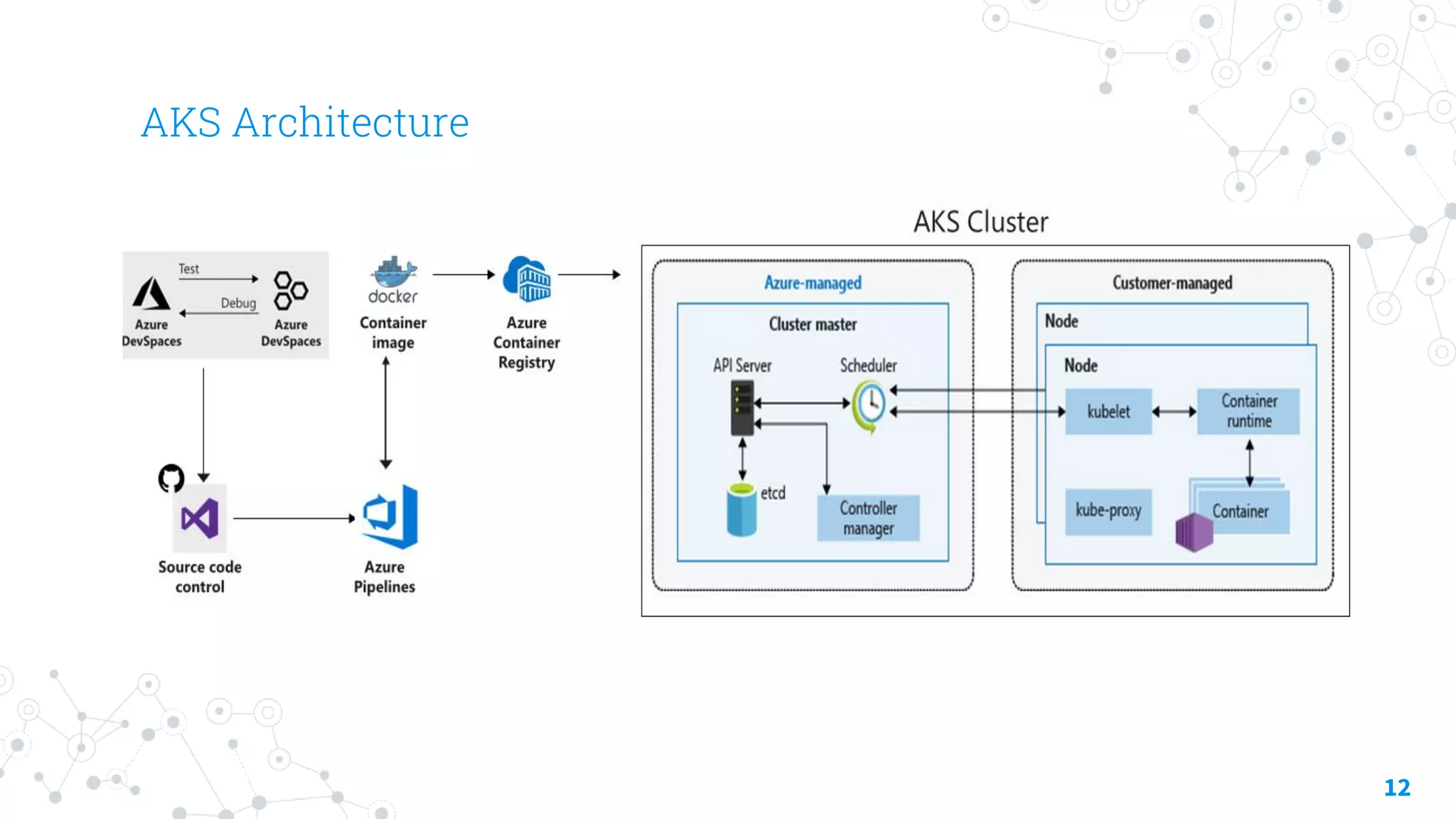
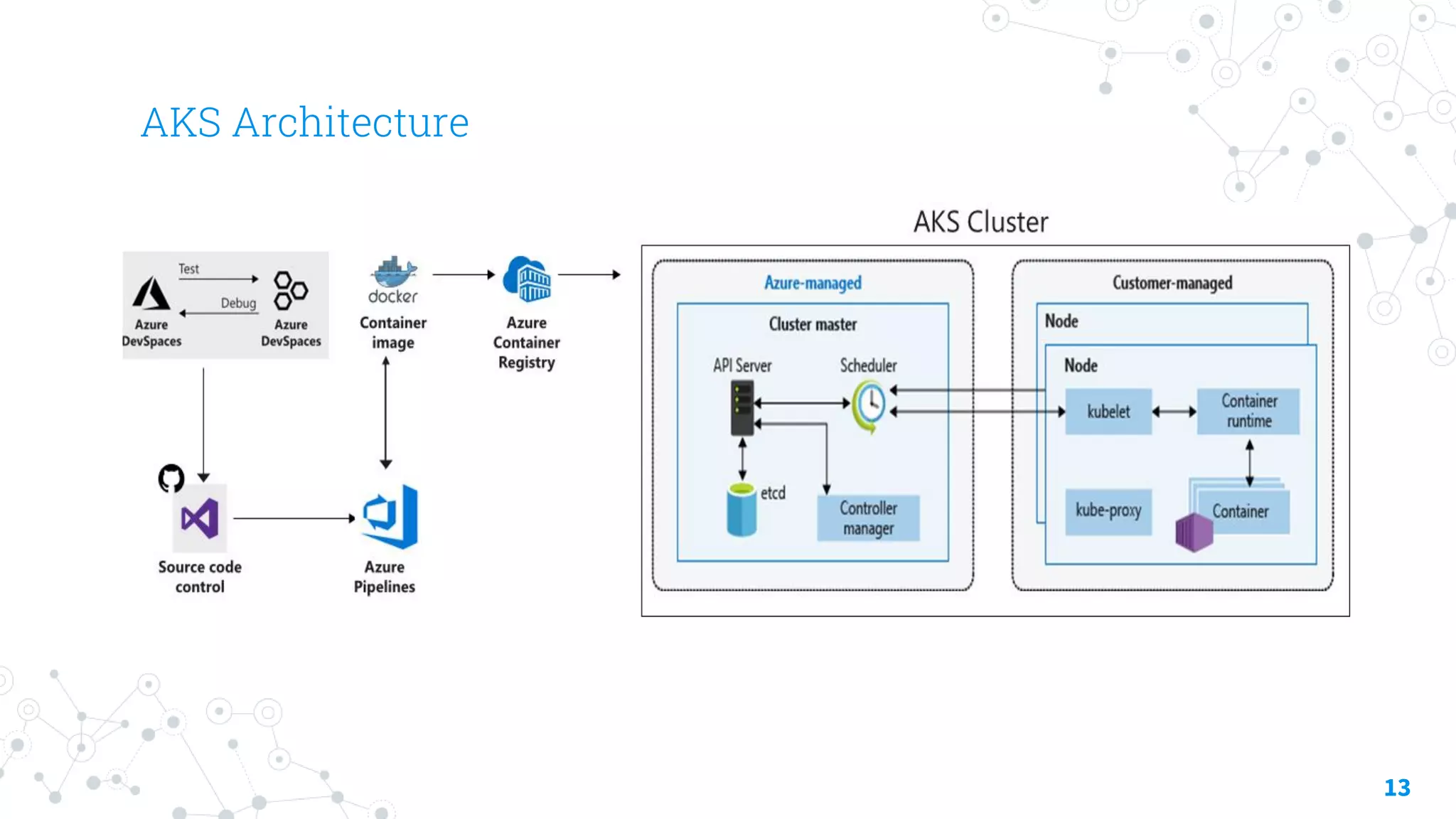
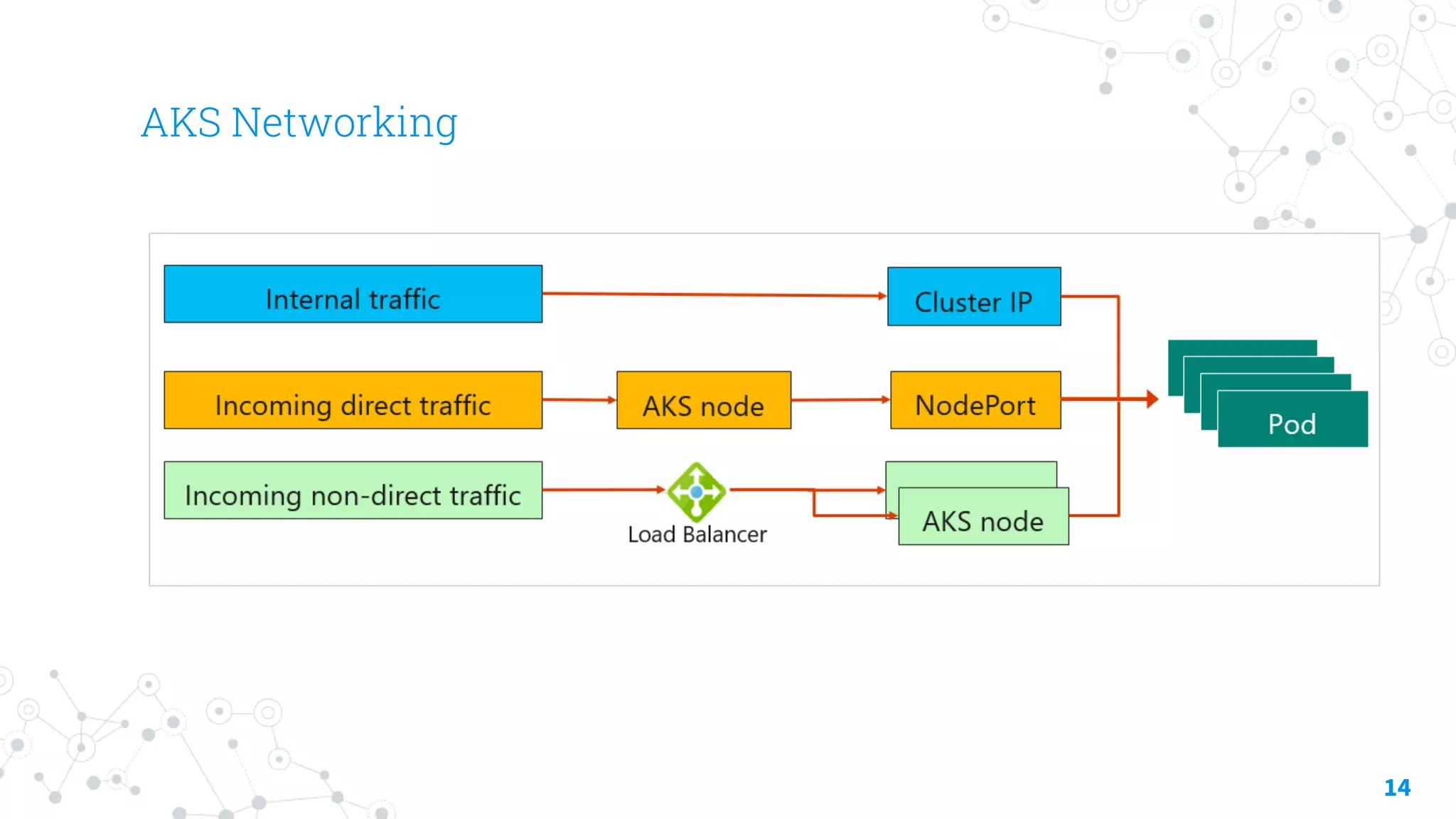
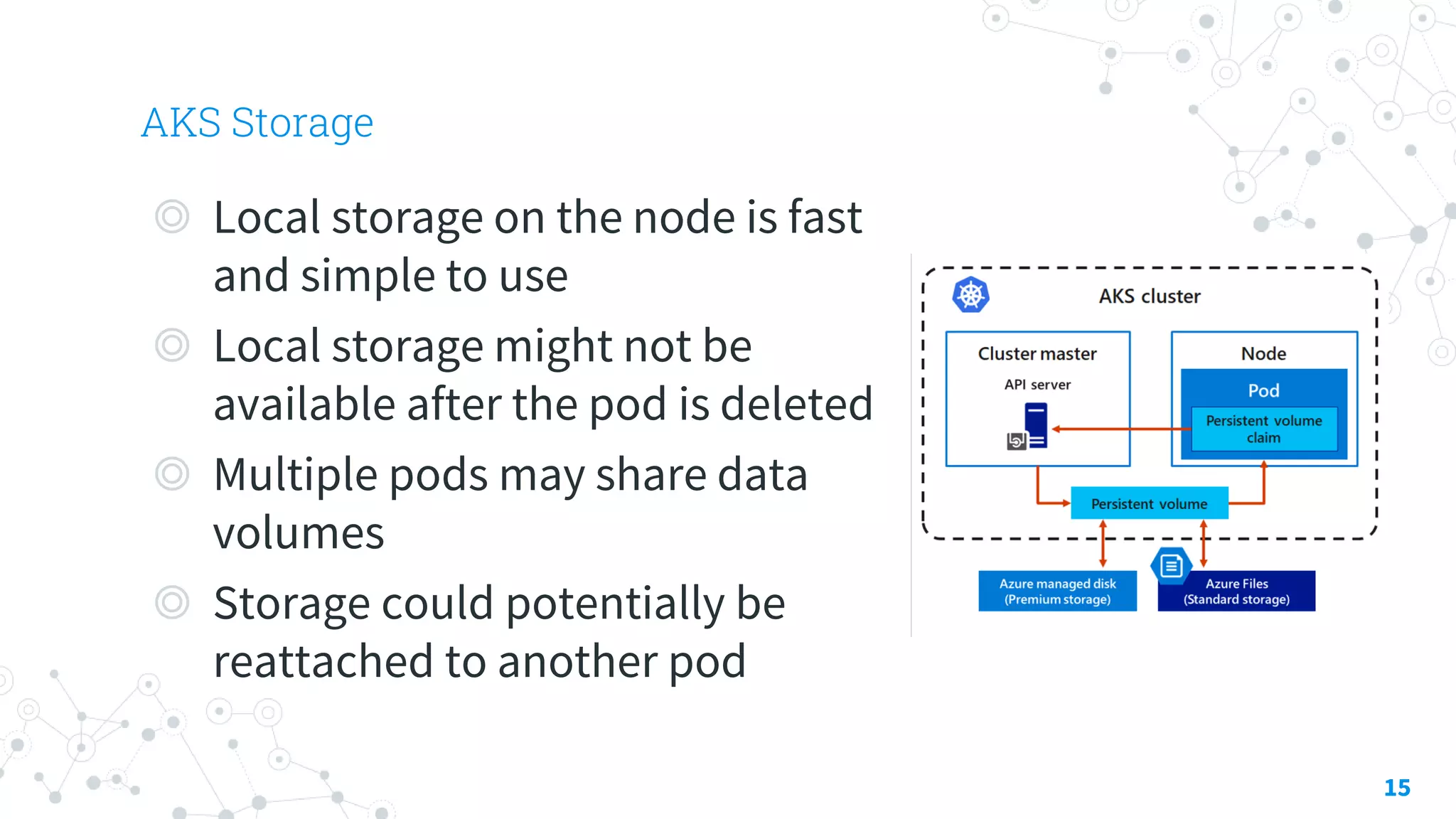
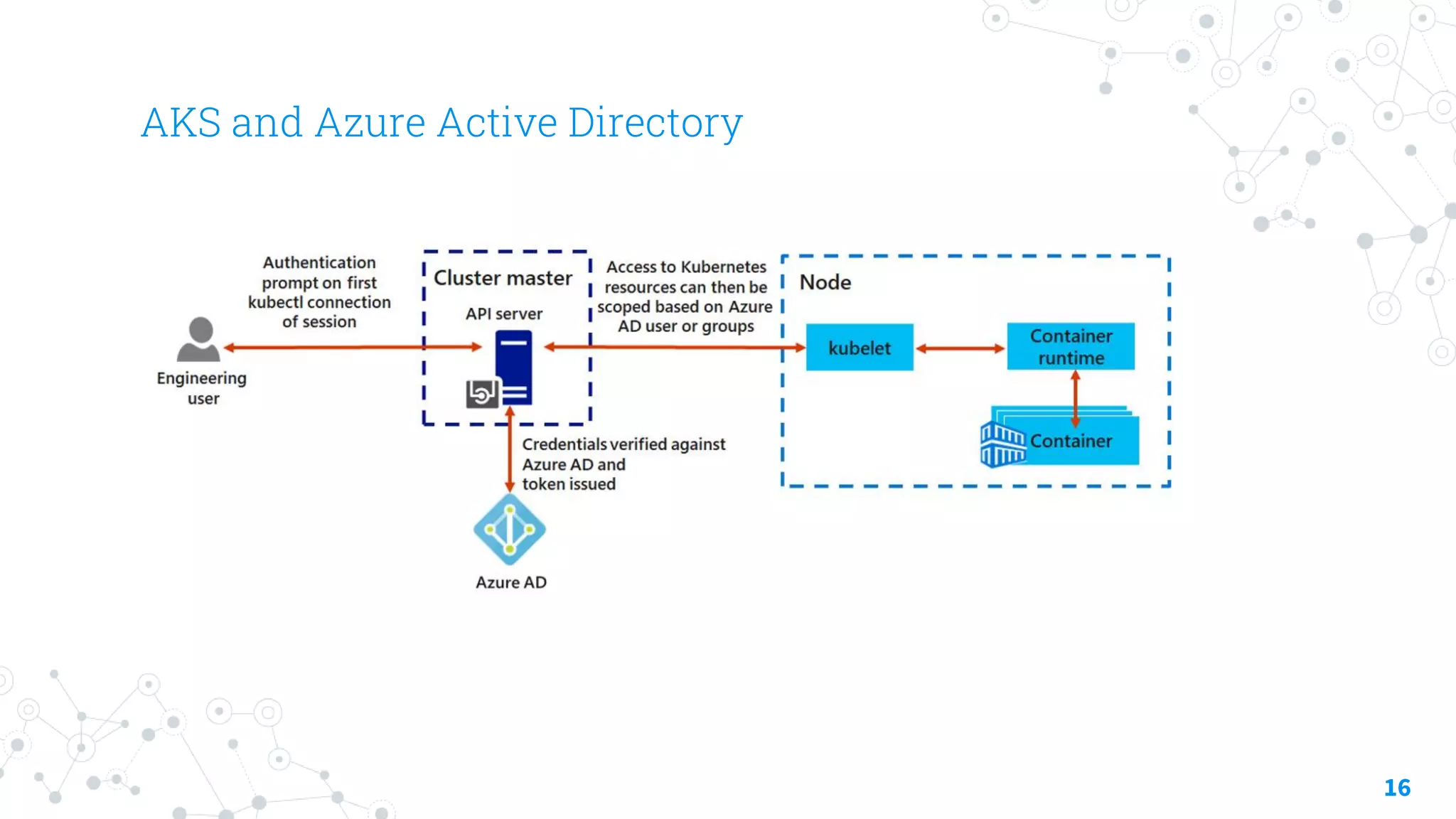
The document discusses container security focusing on Azure services like Azure Container Instances (ACI) and Azure Container Registry (ACR), detailing best practices for securing containers, such as using approved images and role-based access. It further elaborates on Azure Kubernetes Service (AKS) as a platform for managing containerized workloads, featuring automation and scaling capabilities. Key components and terminology related to ACI, ACR, and AKS, as well as their security features, are also outlined.