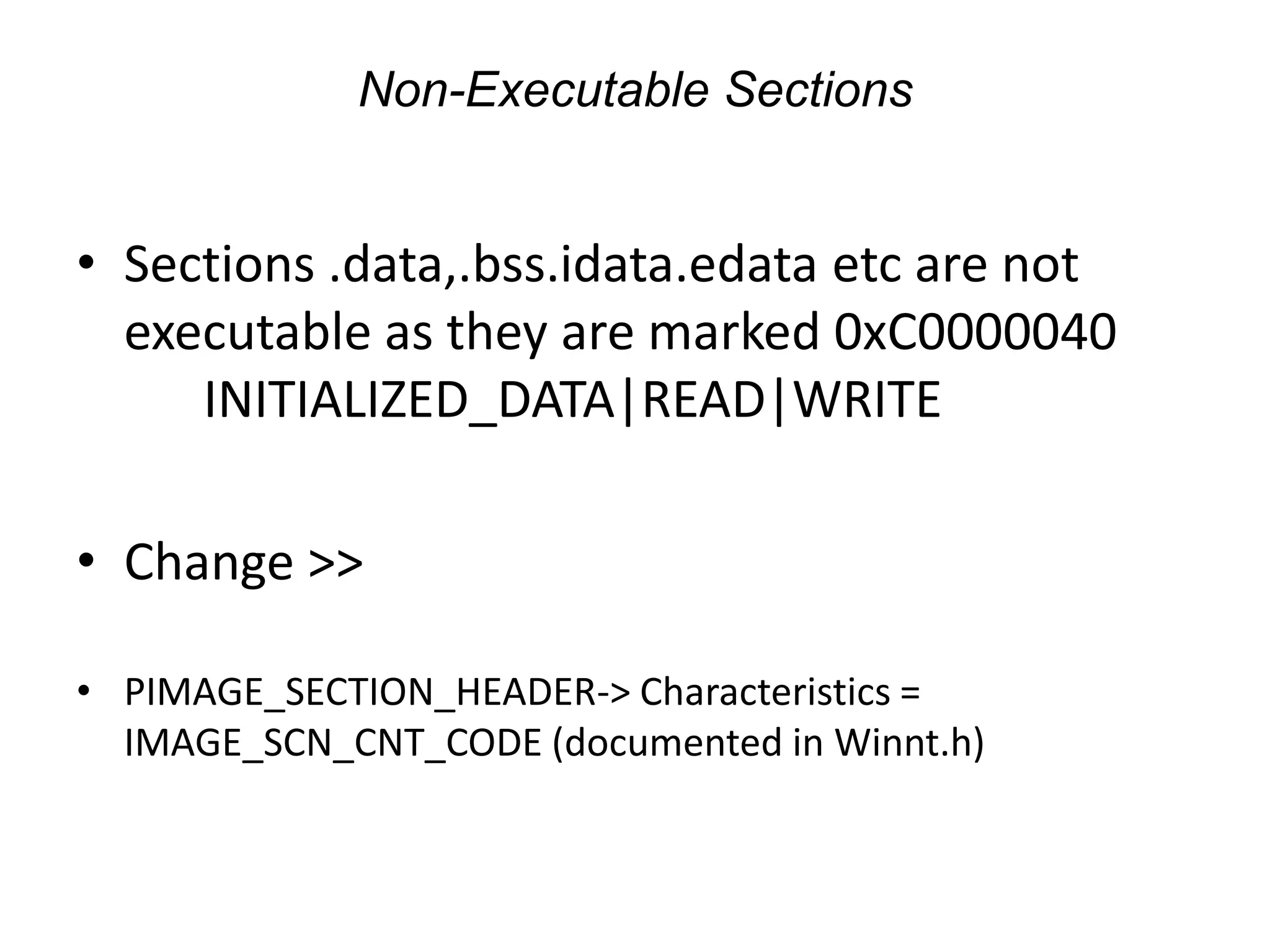
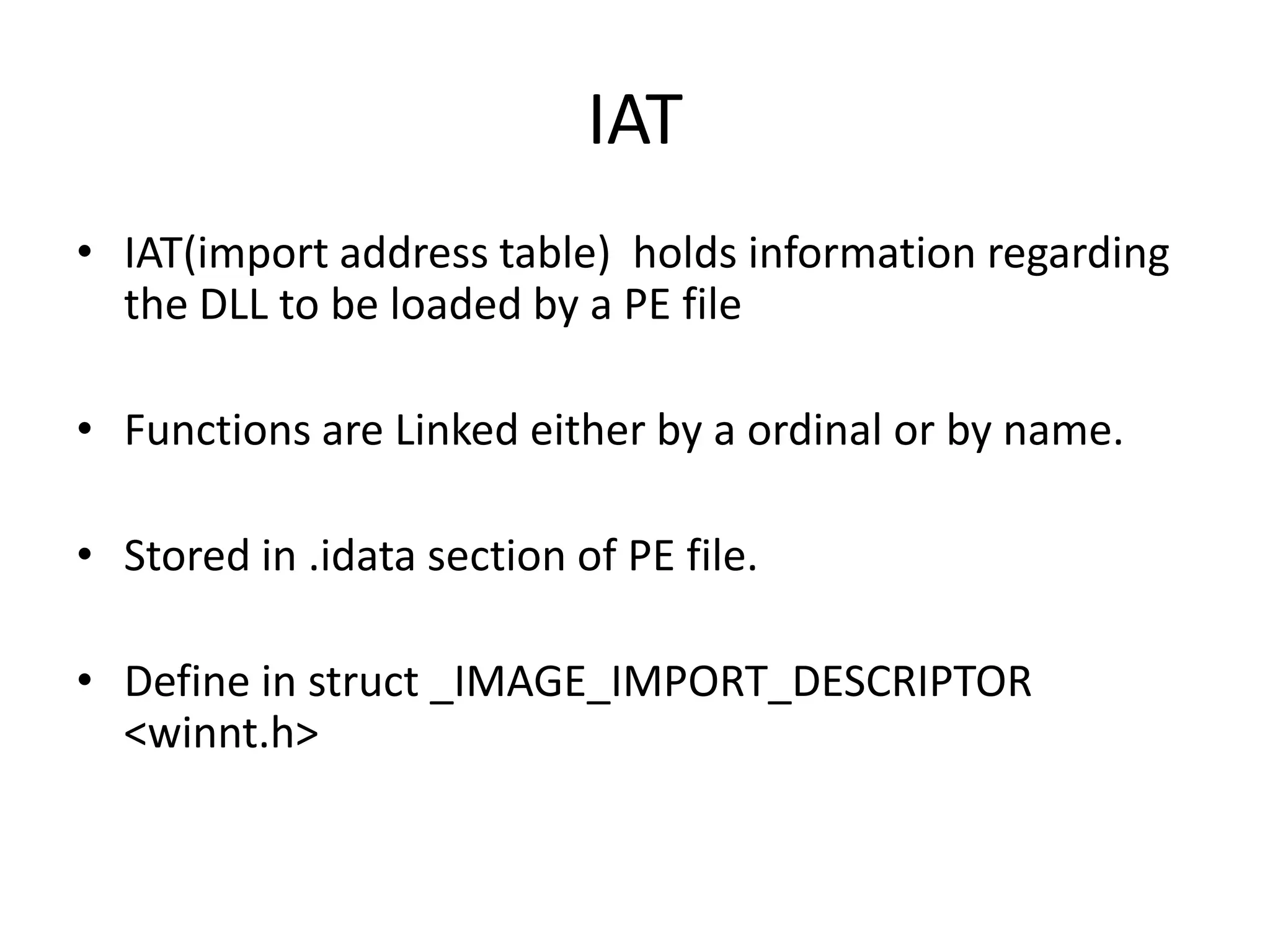
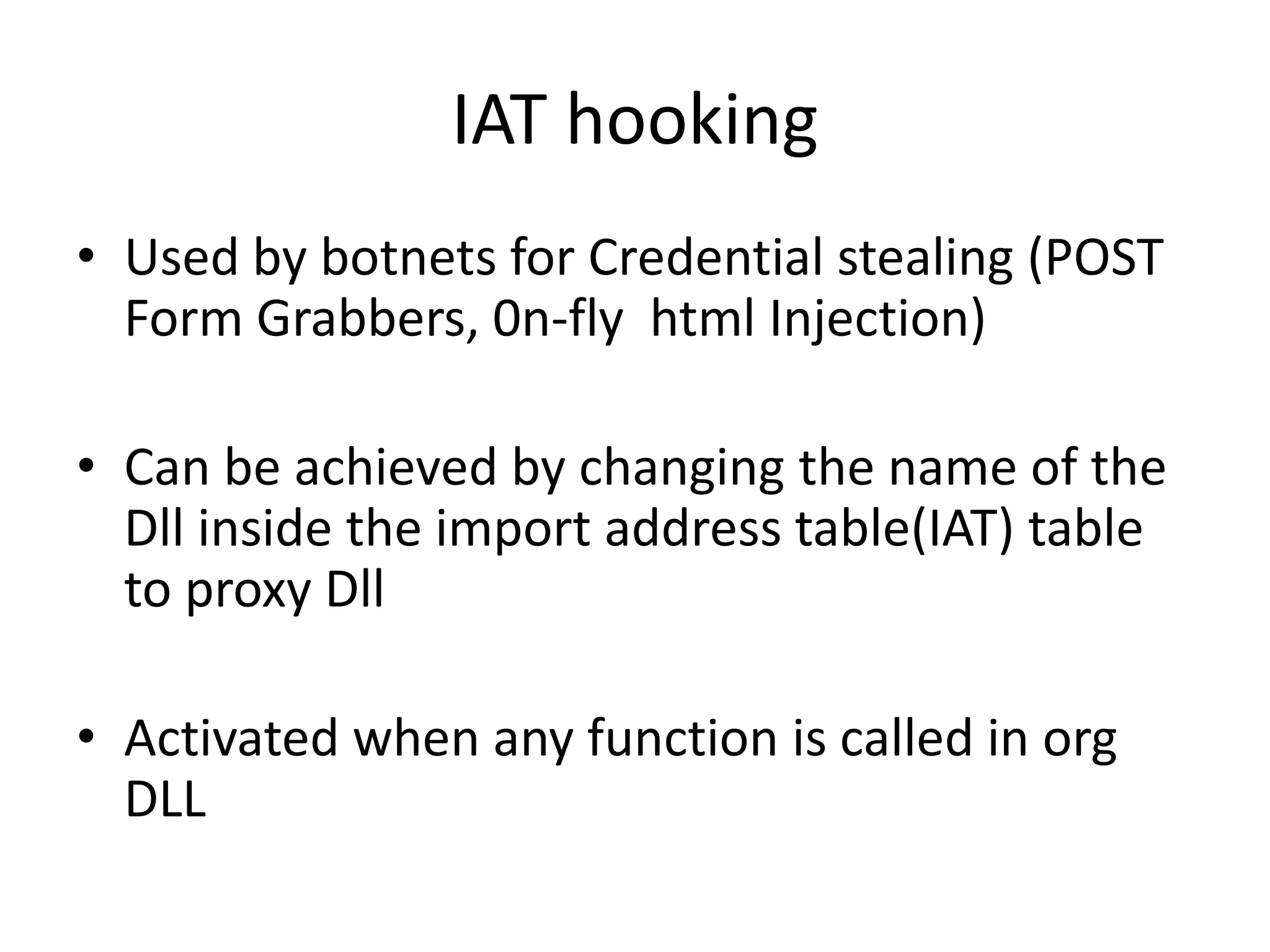
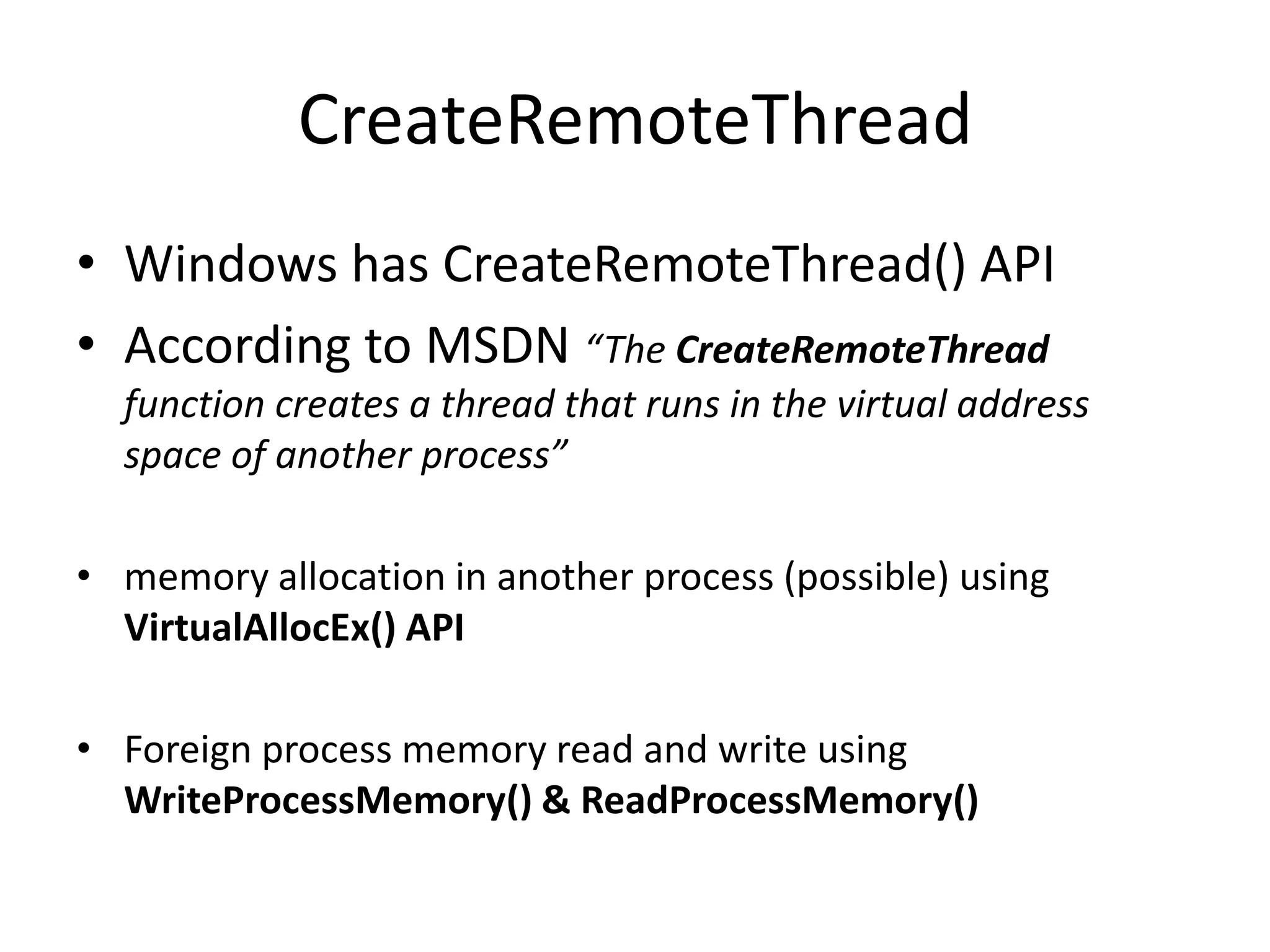
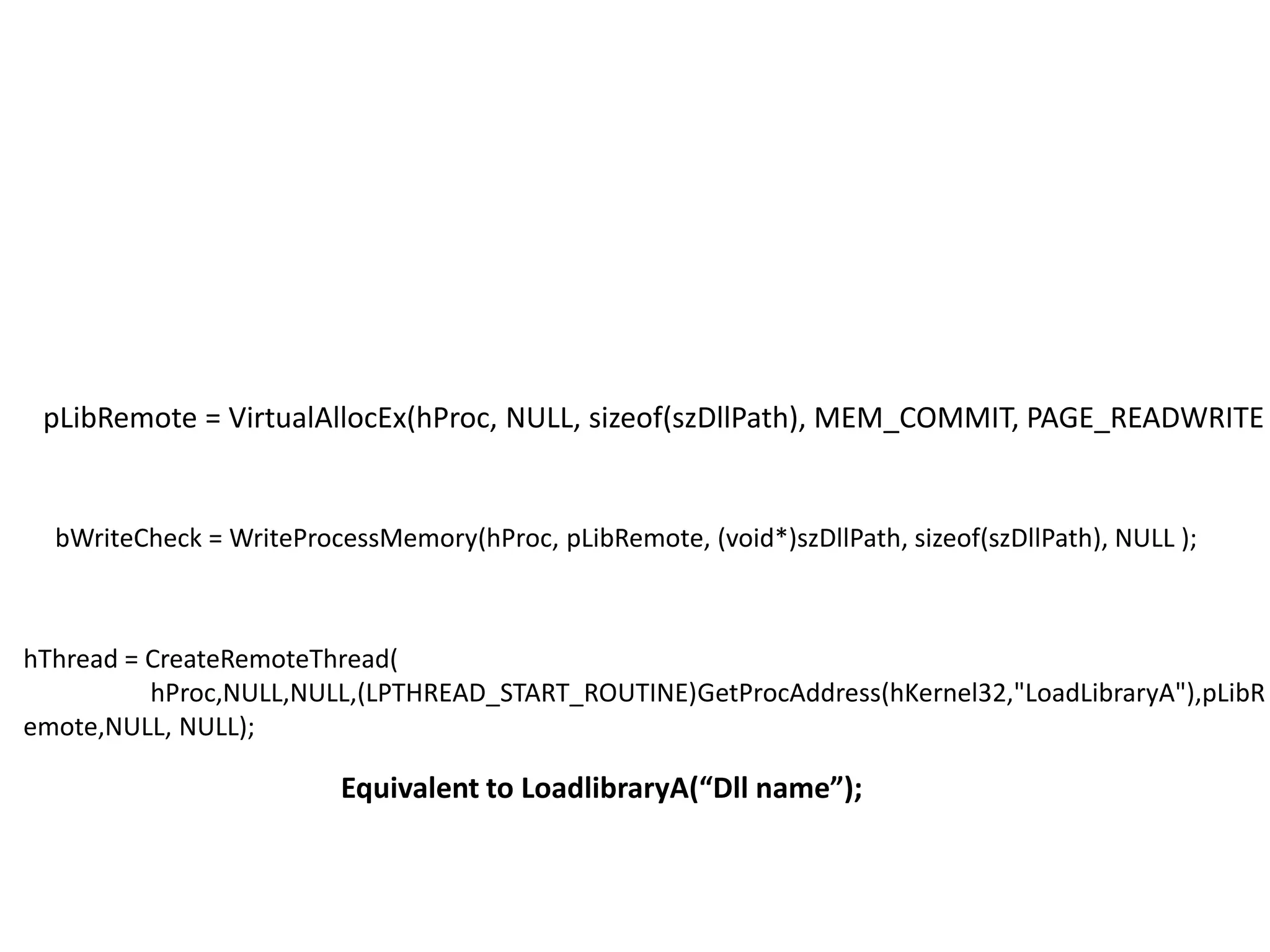
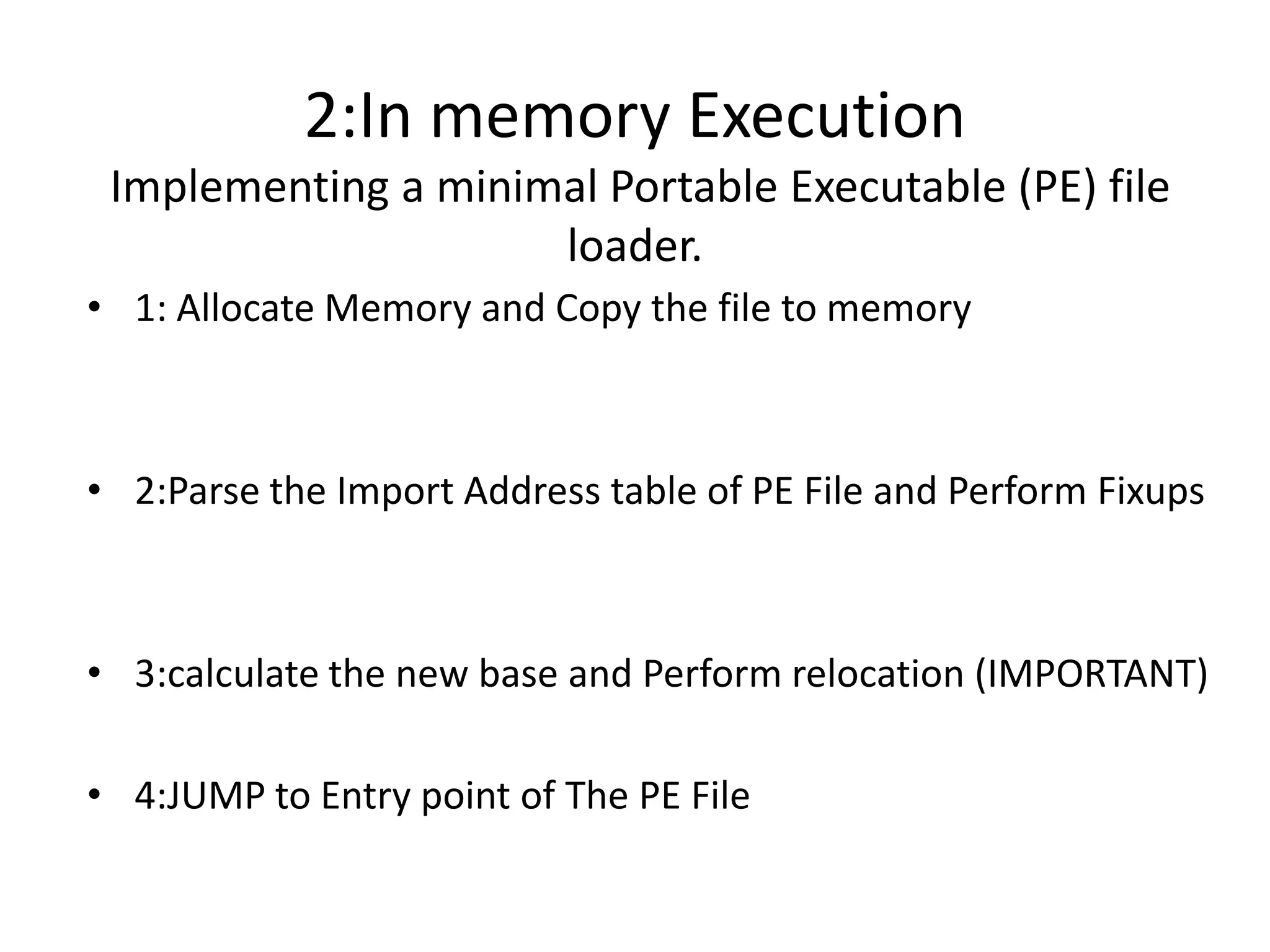
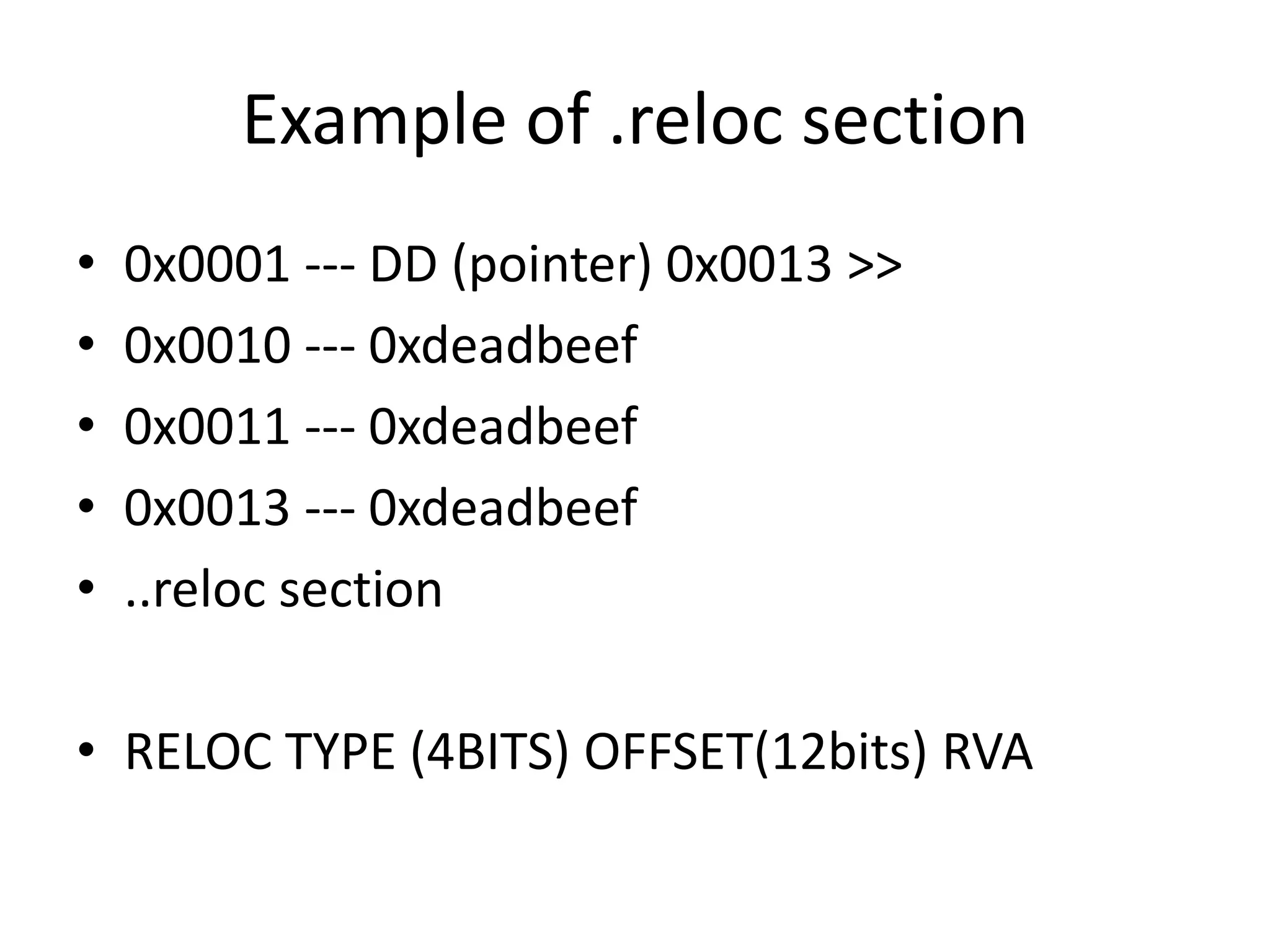
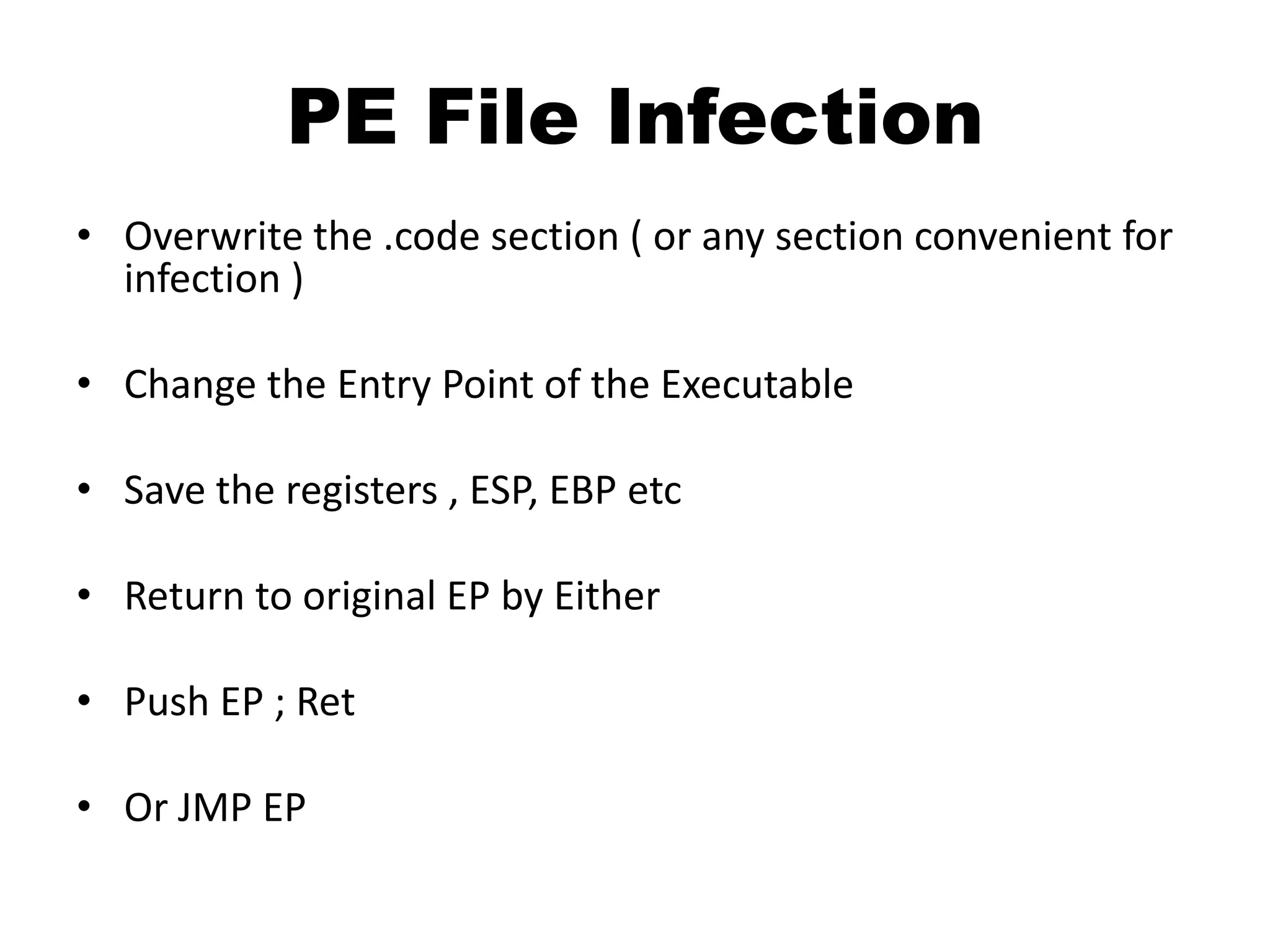
This document discusses different techniques for injecting code on Windows systems, including PE file infection, IAT hooking, and runtime code injection. PE file infection involves overwriting a section like .code and changing the entry point to inject malicious code. IAT hooking changes the DLL name in the import address table to point to a proxy DLL for intercepting function calls. Runtime code injection uses APIs like CreateRemoteThread and WriteProcessMemory to load a DLL or executable into another process's memory and execute it remotely.





![RemedyUse PEB(Process Environment Block) to find kernel32.dll address PEB is located at FS[0x30]Consists heaps, binary information and loaded module information.Further Reading > The Last Stage of DeleriumWin32 Assembly Components. http://www.lsd-pl.net/documents/winasm-1.0.1.pdf;](https://image.slidesharecdn.com/codeinjectiononwindows-110921112922-phpapp01/75/Code-Injection-in-Windows-8-2048.jpg)