- Classical ciphers like the Caesar cipher are simple encryption techniques that are fun to program and understand. The document discusses the Caesar cipher specifically.
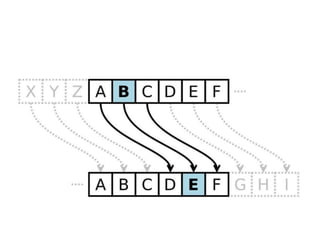
- The Caesar cipher replaces each letter in a message with another letter a fixed number of positions down the alphabet. For example, with a shift of 3, A would be replaced by D, B by E, etc.
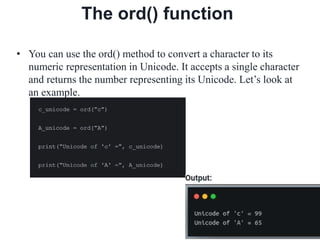
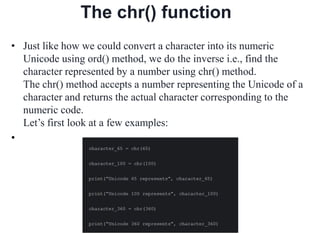
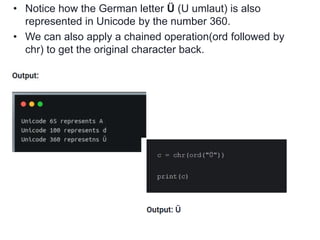
- In Python, the ord() and chr() functions are used to convert between characters and their Unicode numeric codes to perform the encryption and decryption calculations for the Caesar cipher. Mathematical formulas are provided for both the encryption and decryption processes.