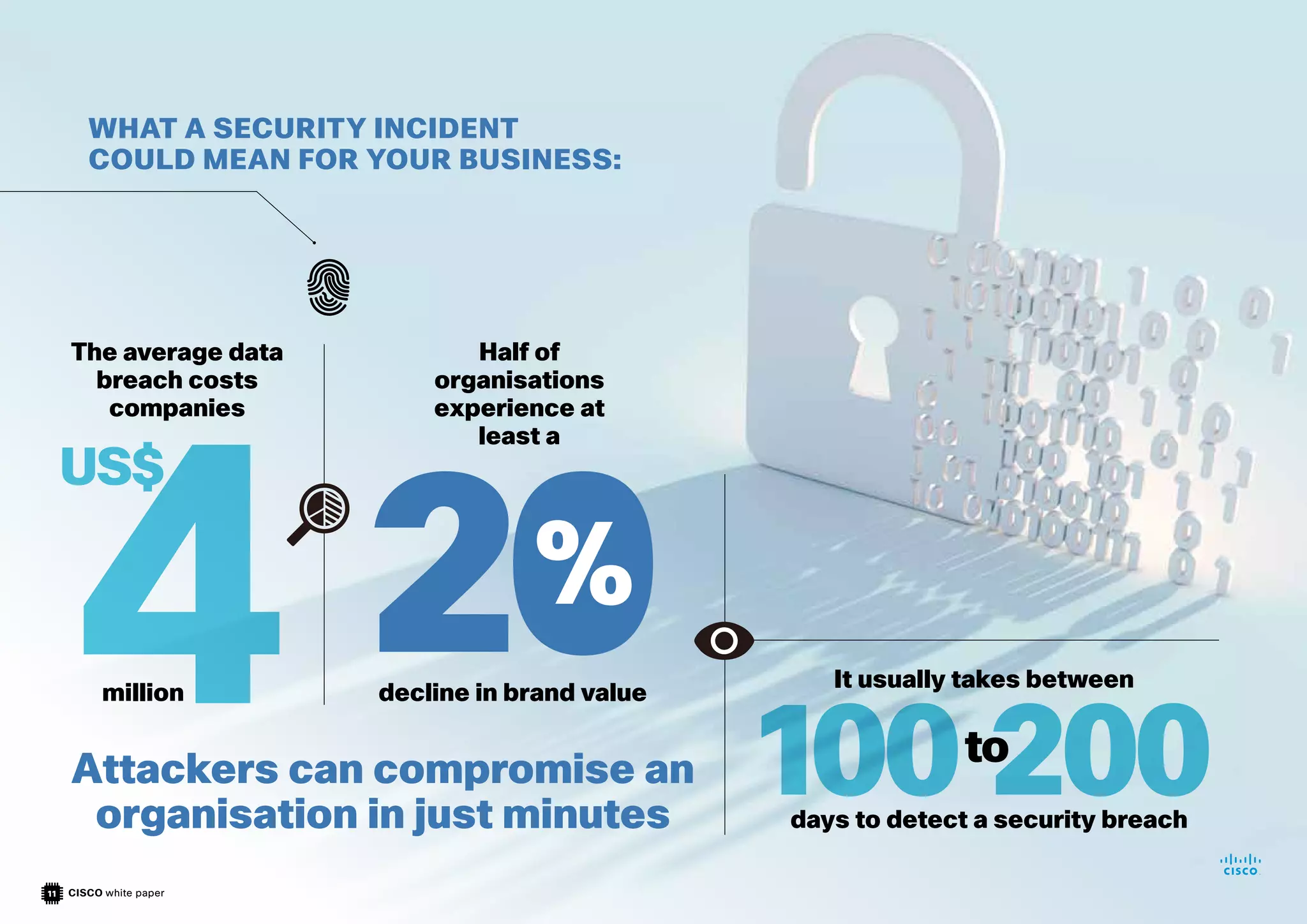
This document discusses how investing in a secure network edge is critical for business success in today's digital world. It argues that the network edge provides opportunities to better understand customer needs, gain business insights from data, and improve operational efficiencies. However, the network edge must be robust and secure to avoid security threats and cyber attacks. The document recommends Cisco's solutions to leverage the network edge for competitive advantages while providing security.