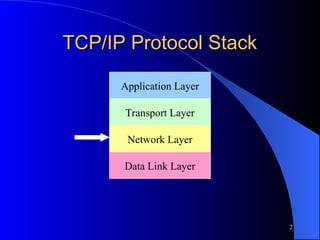
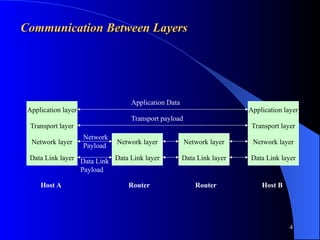
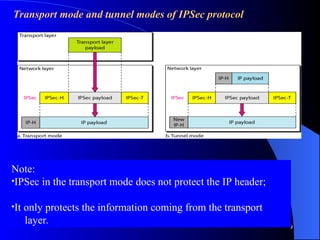
The document provides an overview of internet security, focusing on the IP and TCP/IP protocol stack, and the significance of the network layer in ensuring data integrity and confidentiality. It explains the role of IPsec in securing network communications through methods like authentication headers and encapsulating security payloads, as well as the establishment of security associations. Key elements such as the Internet Key Exchange (IKE) protocol and the function of virtual private networks (VPNs) for secure connections over the internet are also discussed.